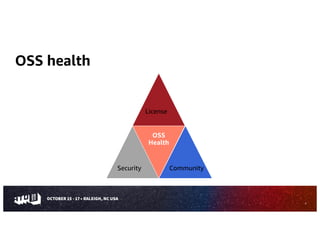
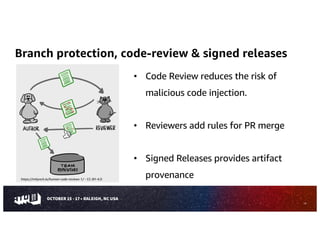
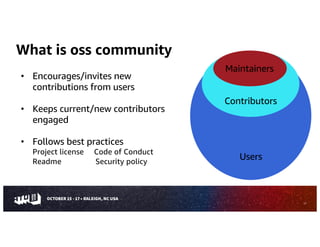
The document is a comprehensive guide on evaluating open source software (OSS), detailing considerations for selecting OSS packages, including licensing, security, and community health. It emphasizes the importance of assessing OSS components to ensure they meet specific needs, while also providing tools like CHAOSS and OpenSSF Scorecard for evaluation. The guide outlines various risks associated with OSS usage and provides resources to mitigate these risks effectively.