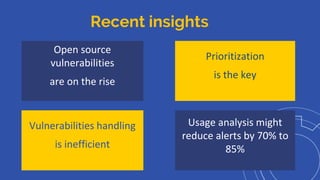
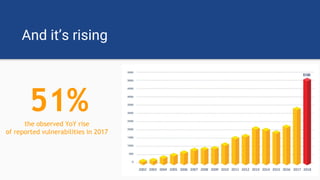
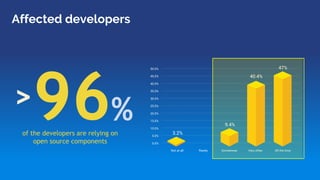
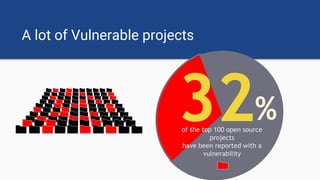
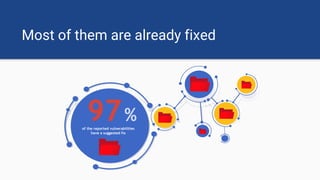
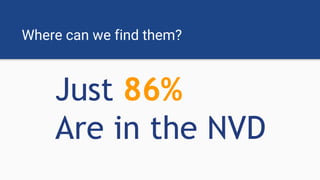
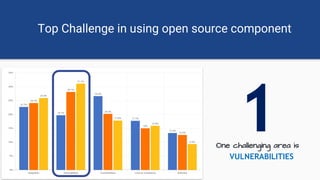
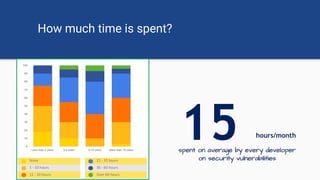
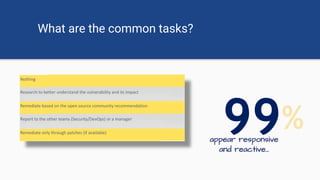
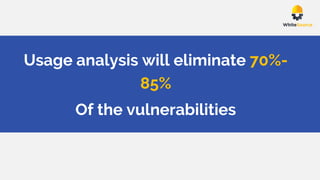
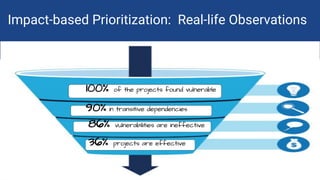
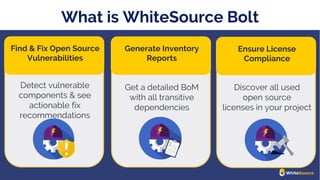
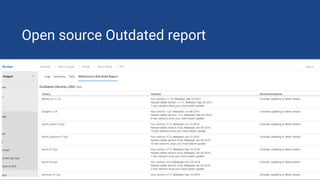
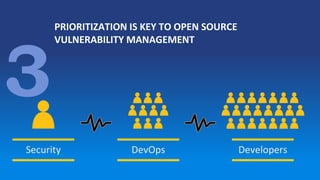
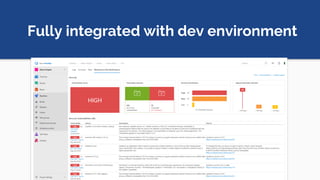
The document discusses the rise of open source vulnerabilities and the inefficiency of their handling, emphasizing the need for prioritization in managing these risks. It highlights that 30% of the top 100 open source projects have reported vulnerabilities and suggests that effective usage analysis can reduce alerts by 70% to 85%. Additionally, it introduces Whitesource Bolt as a practical tool for detecting and fixing open source vulnerabilities while ensuring license compliance.