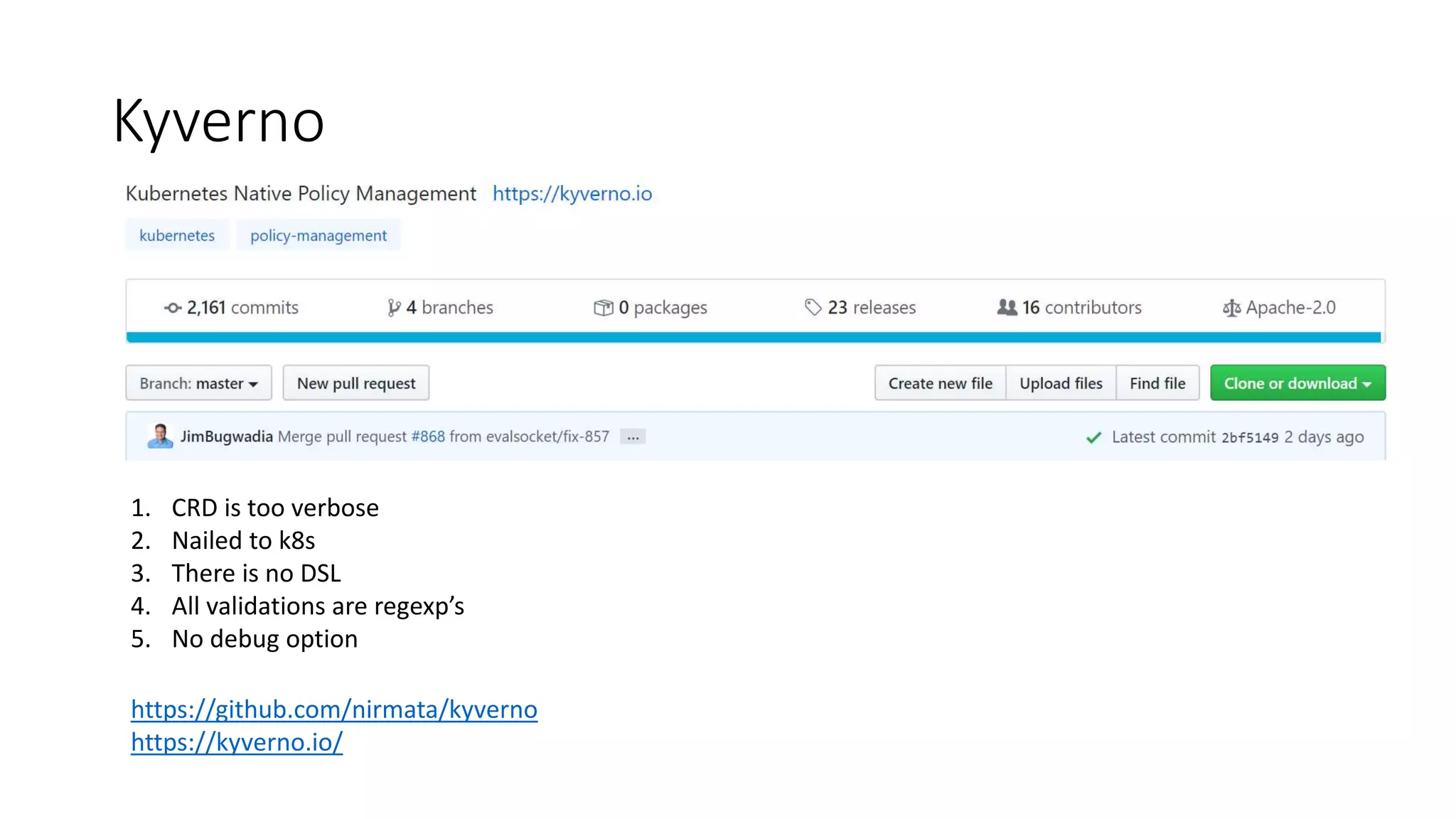
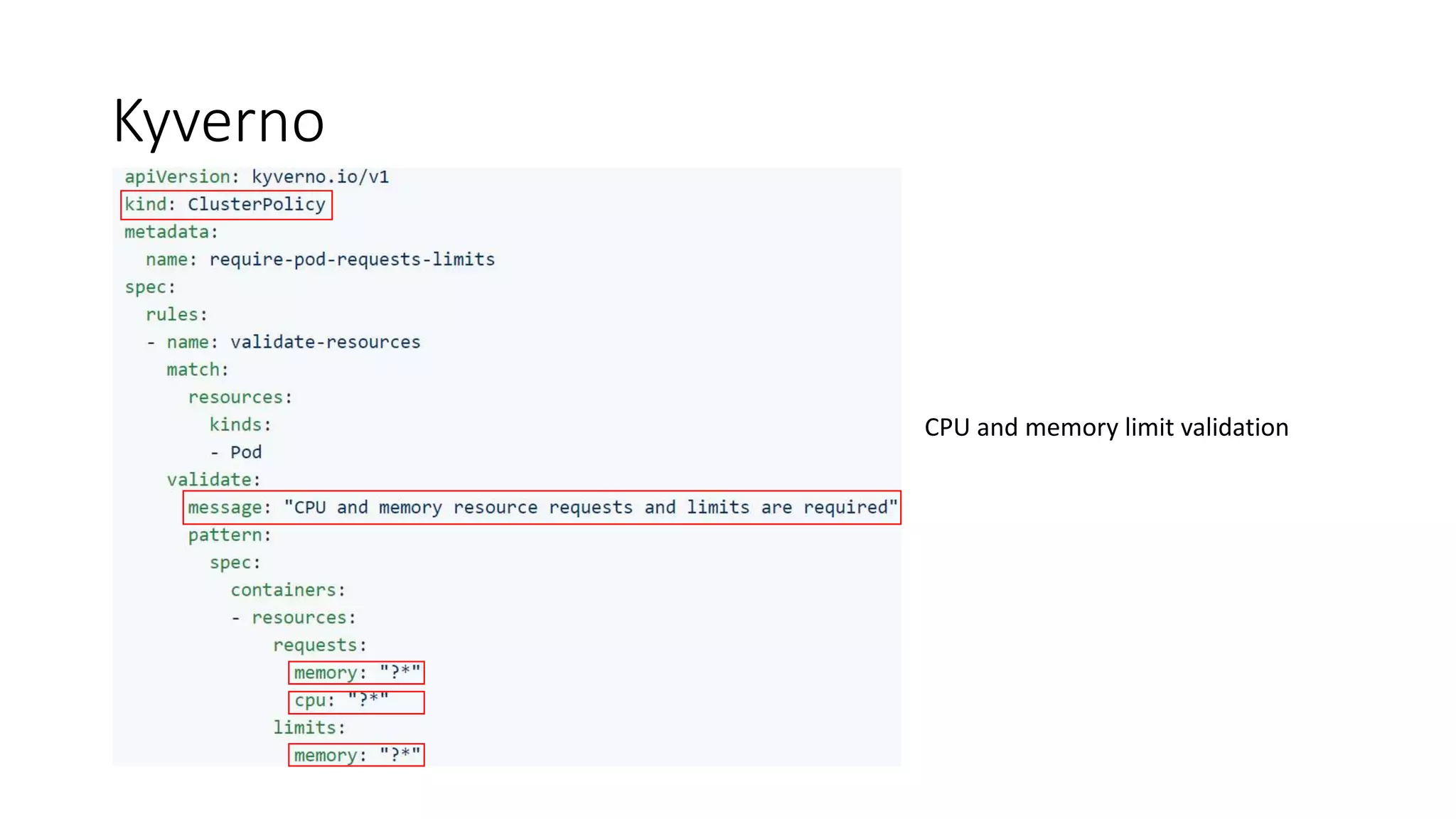
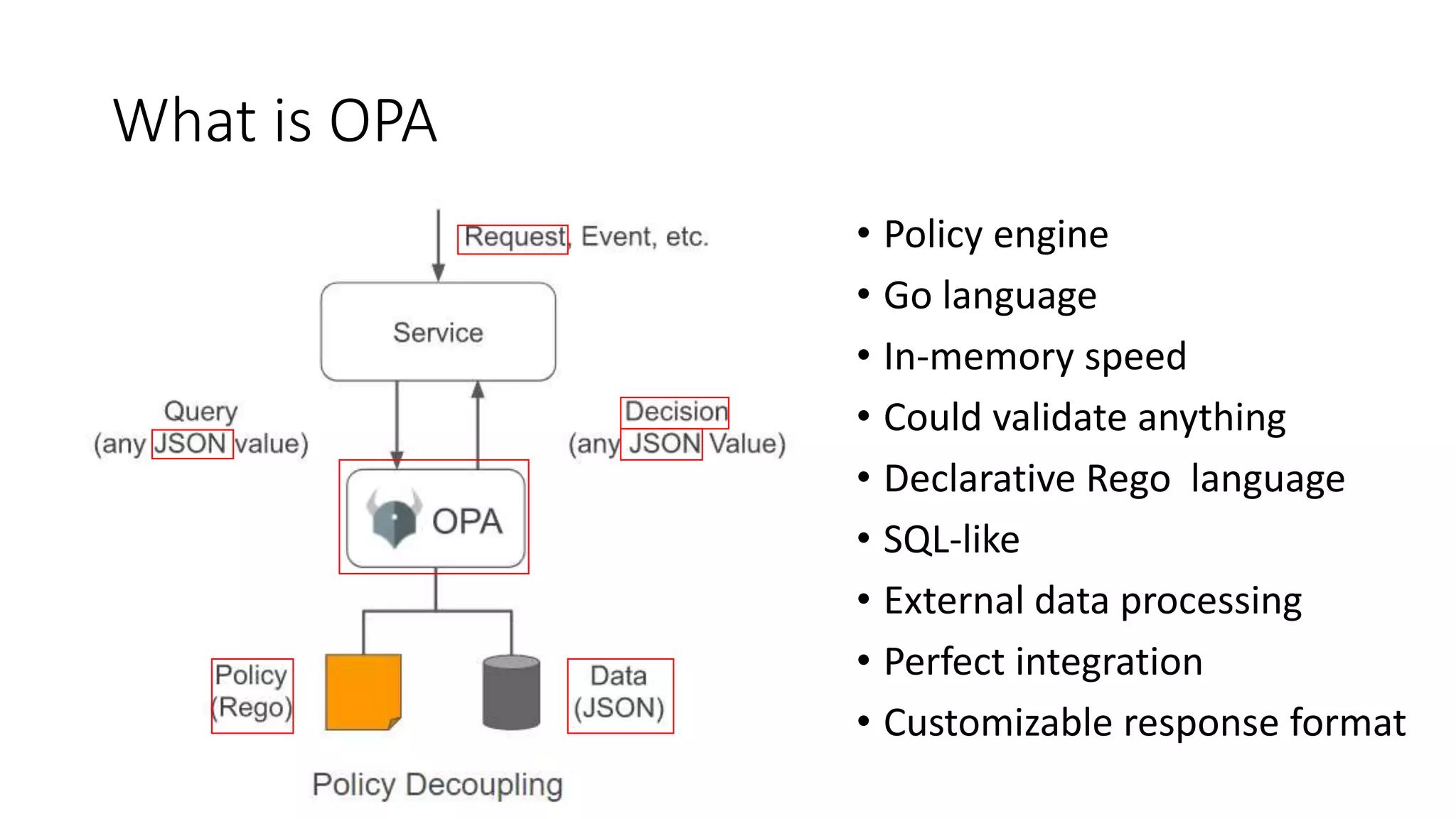
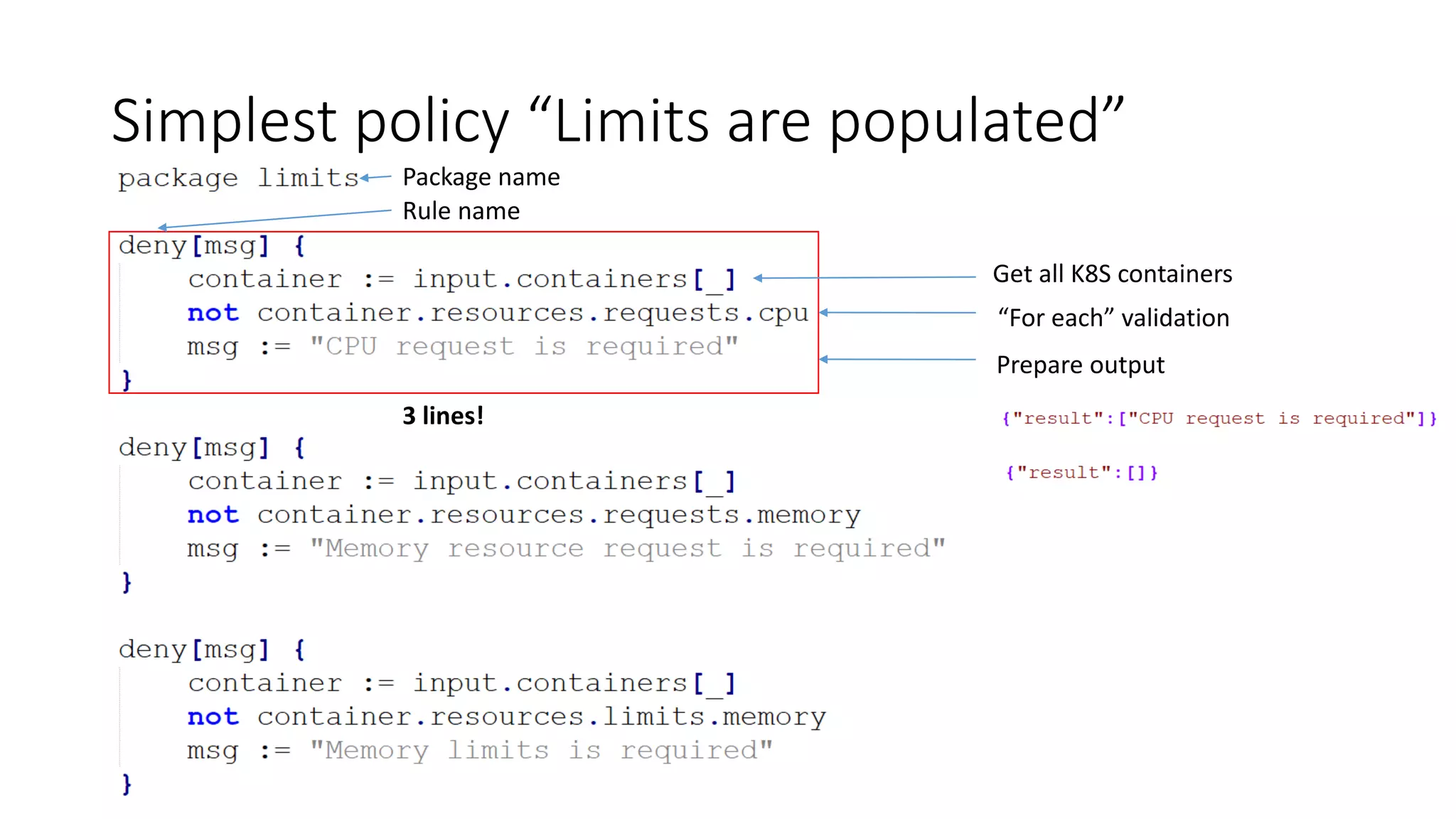
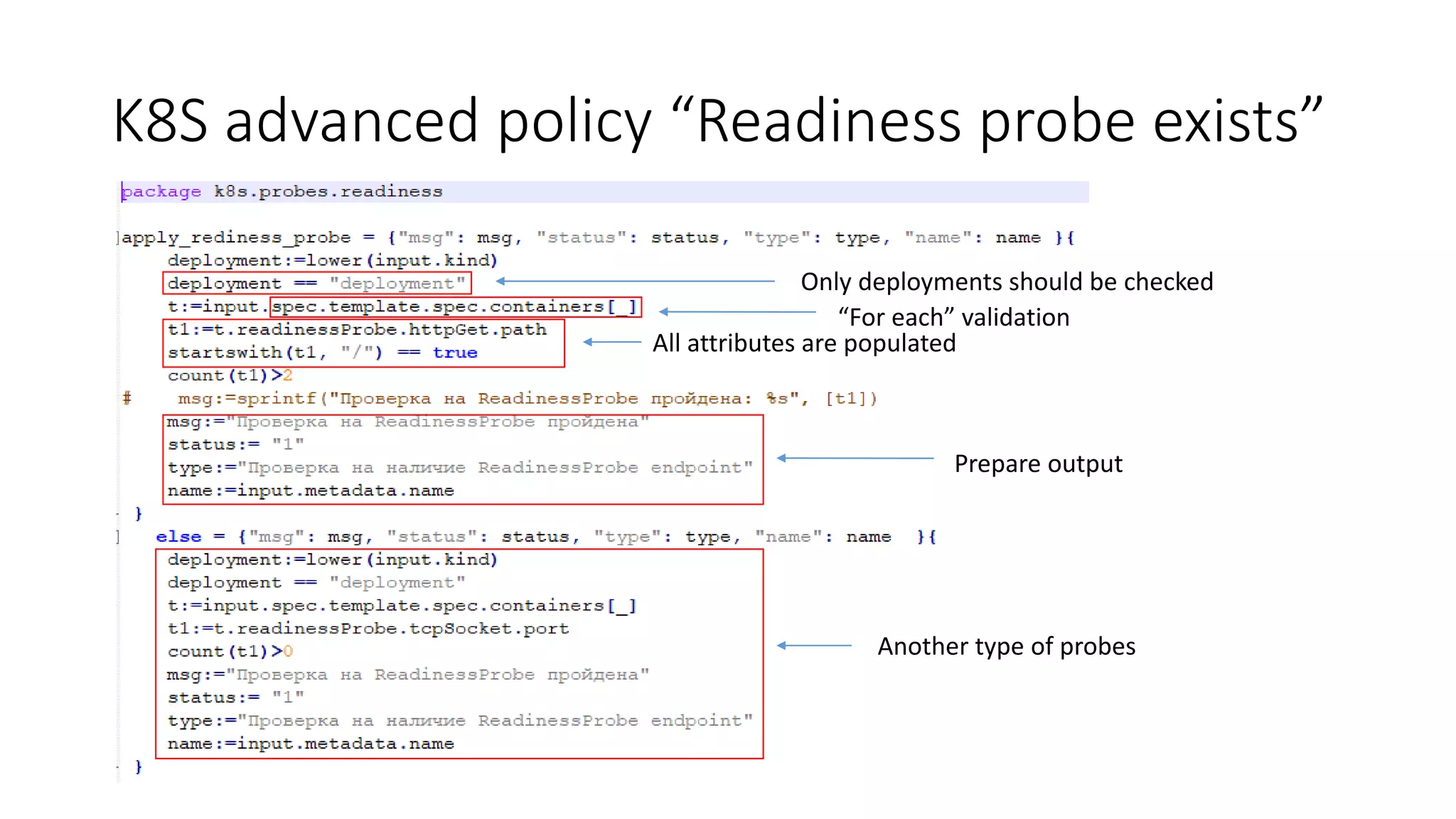
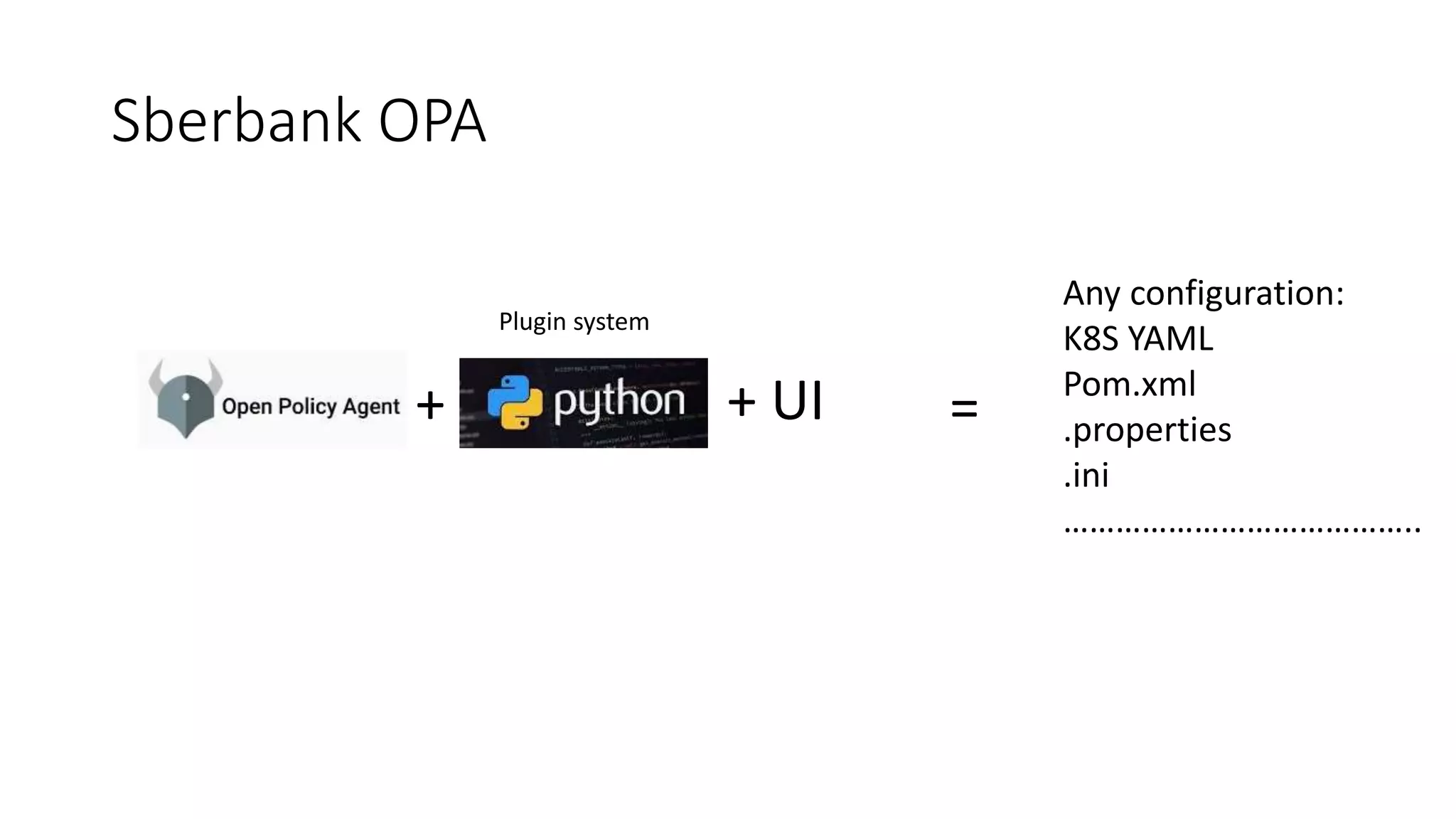
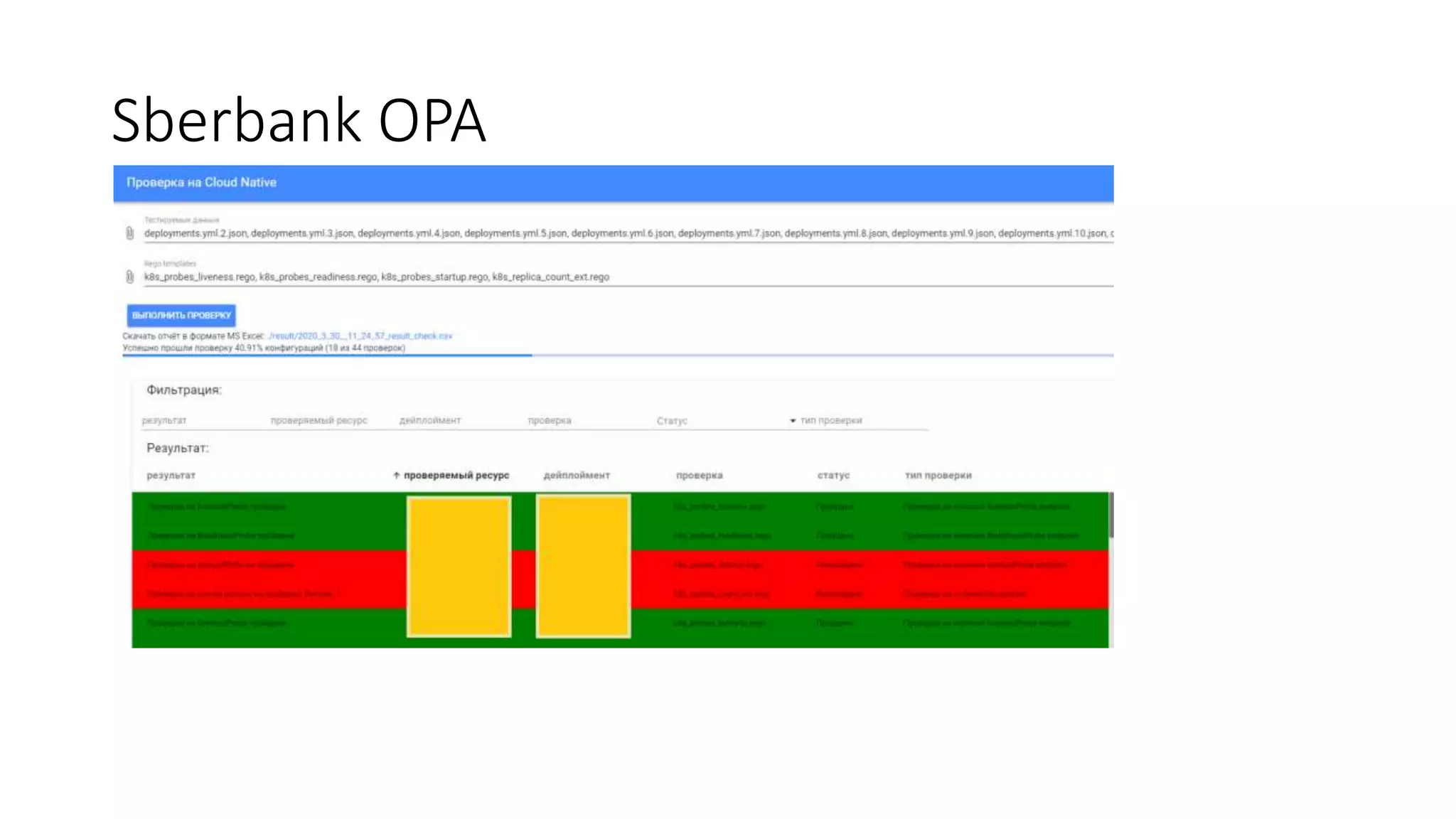
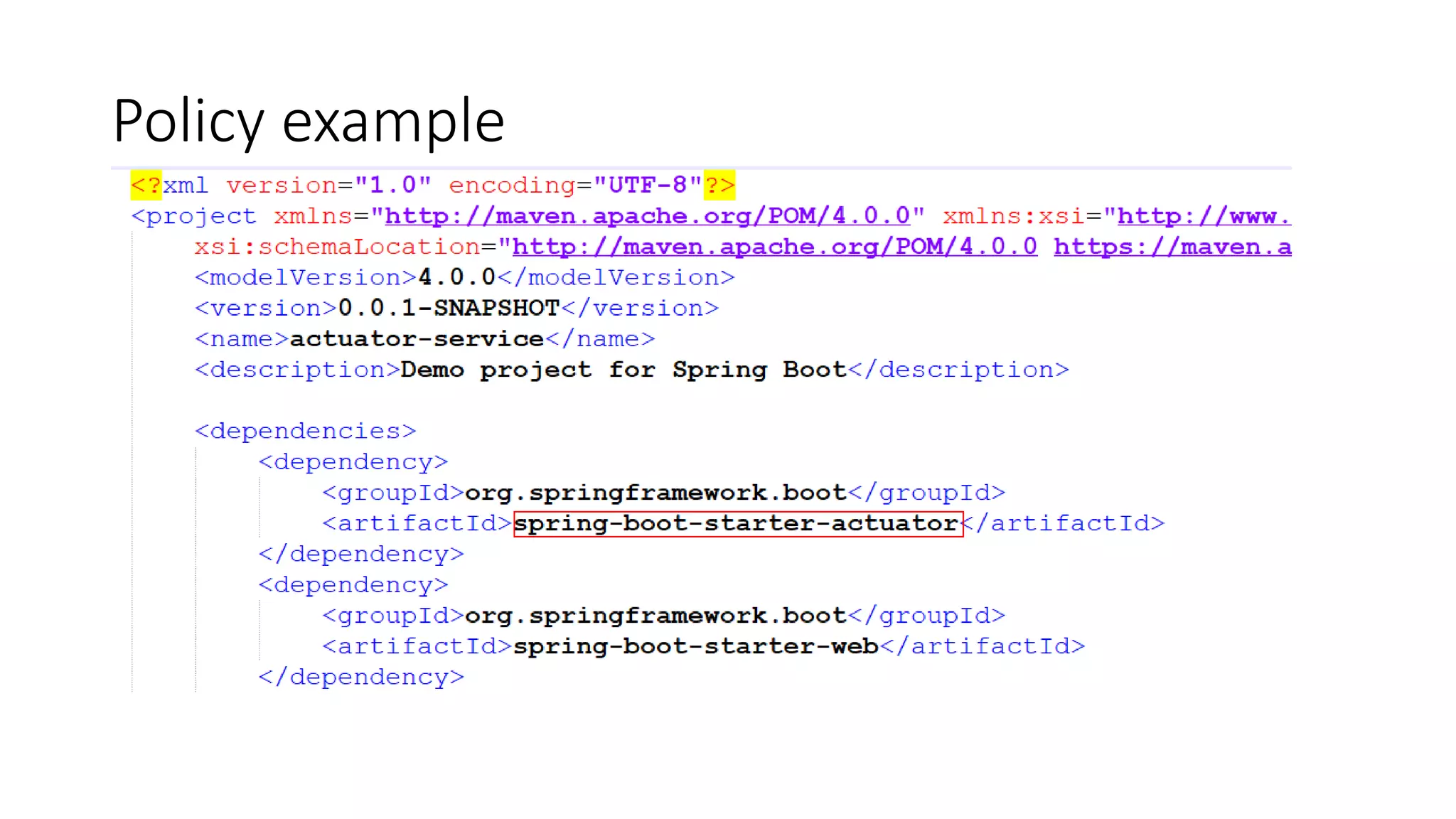
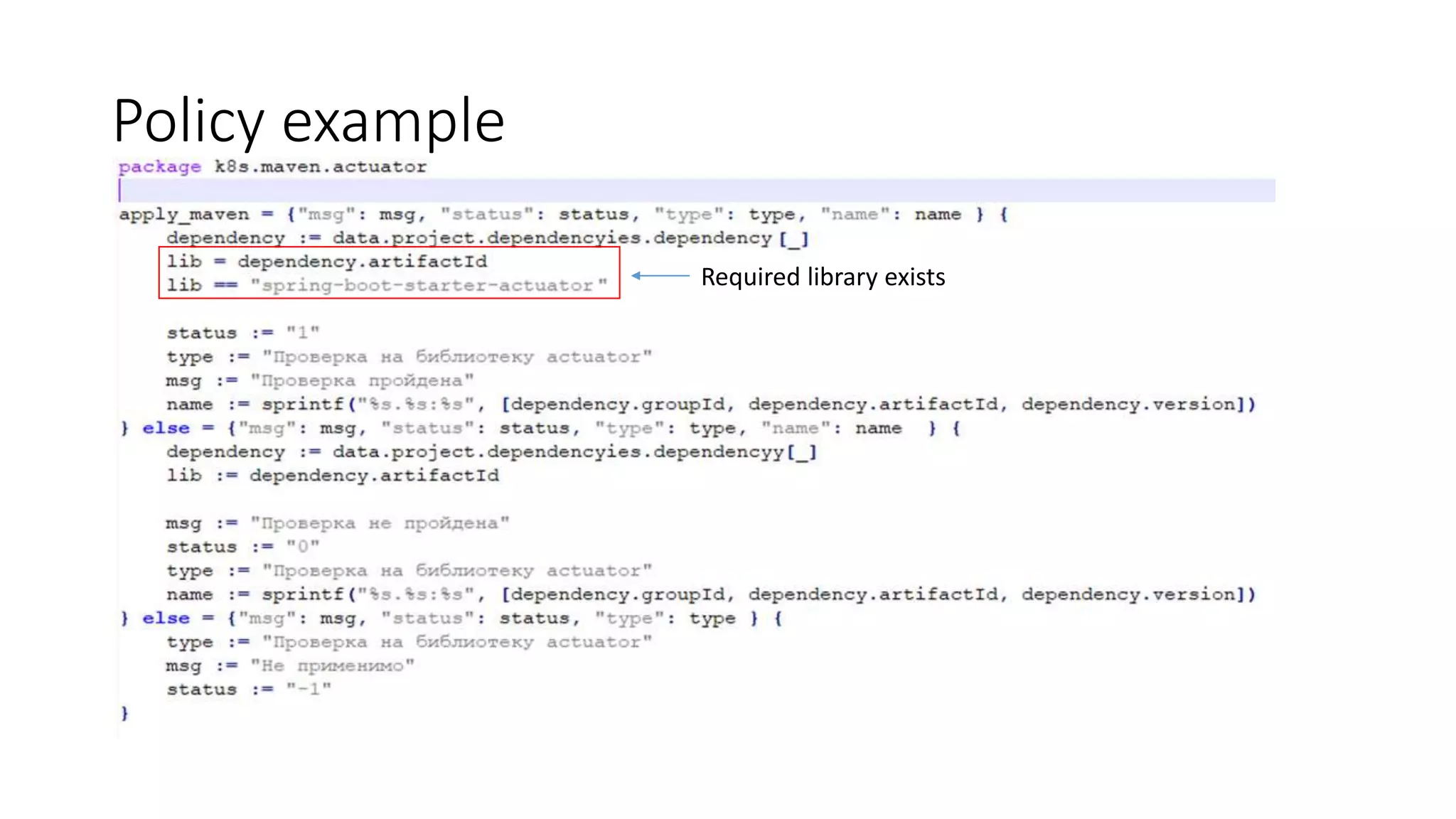
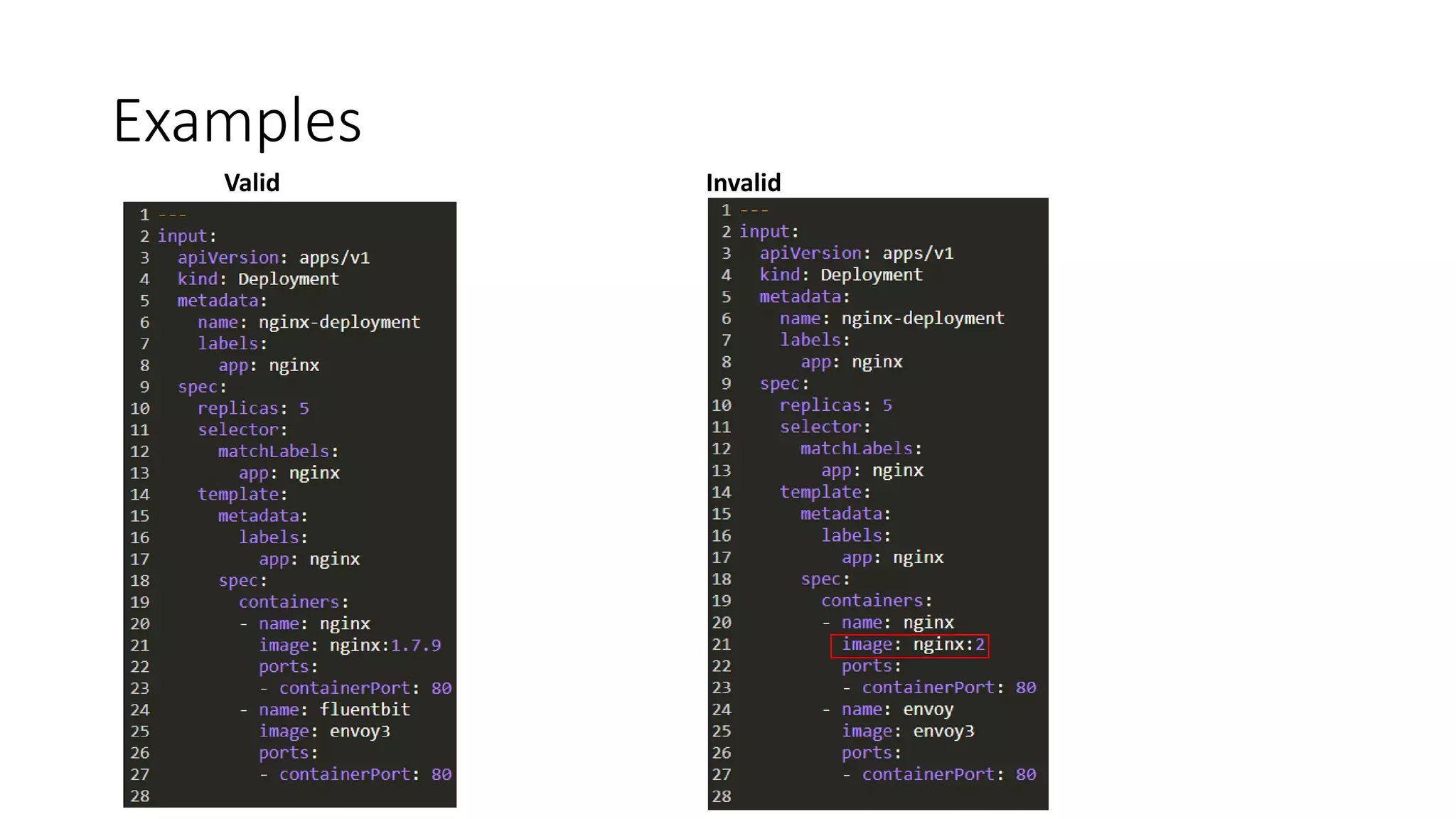
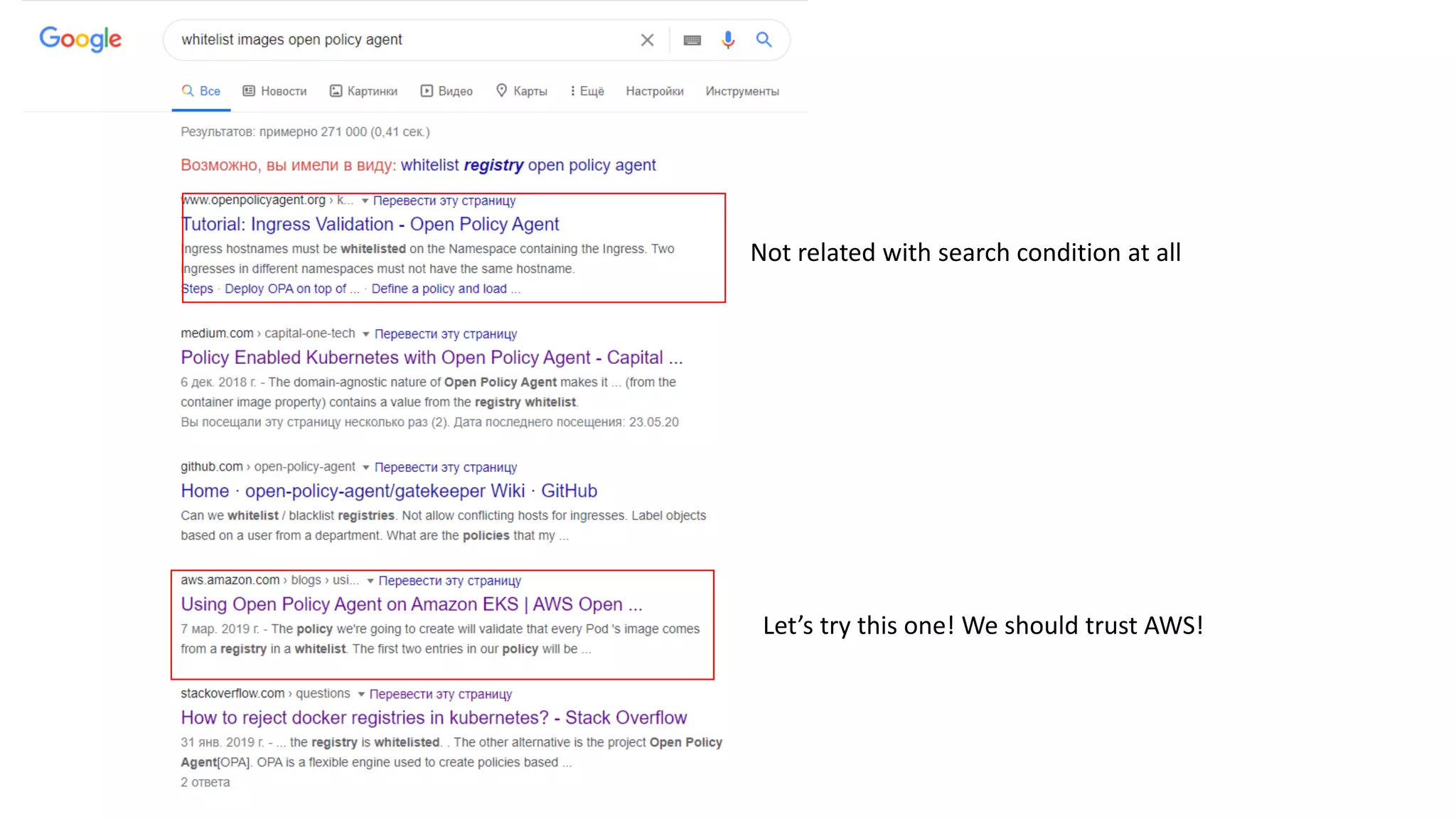
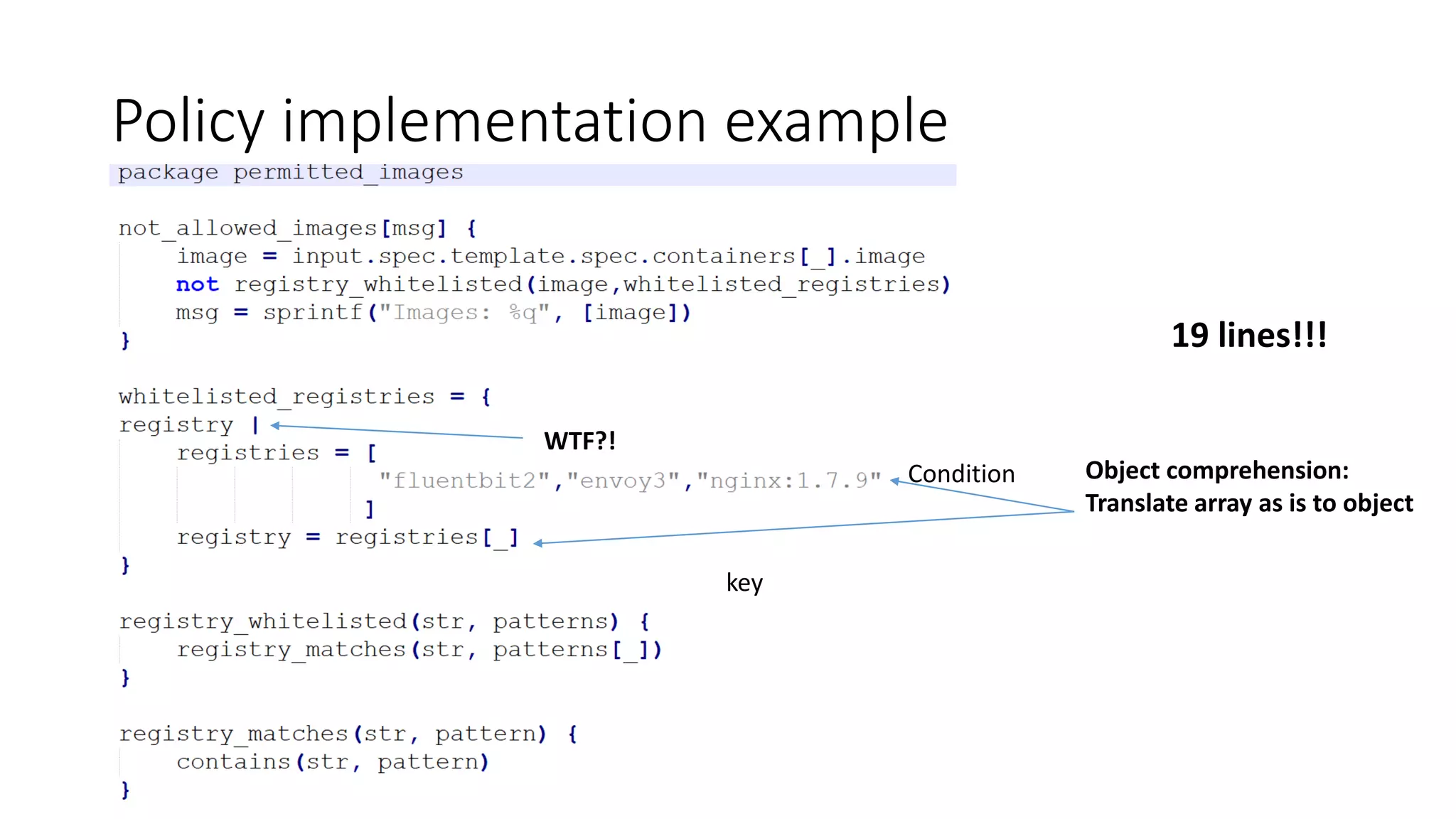
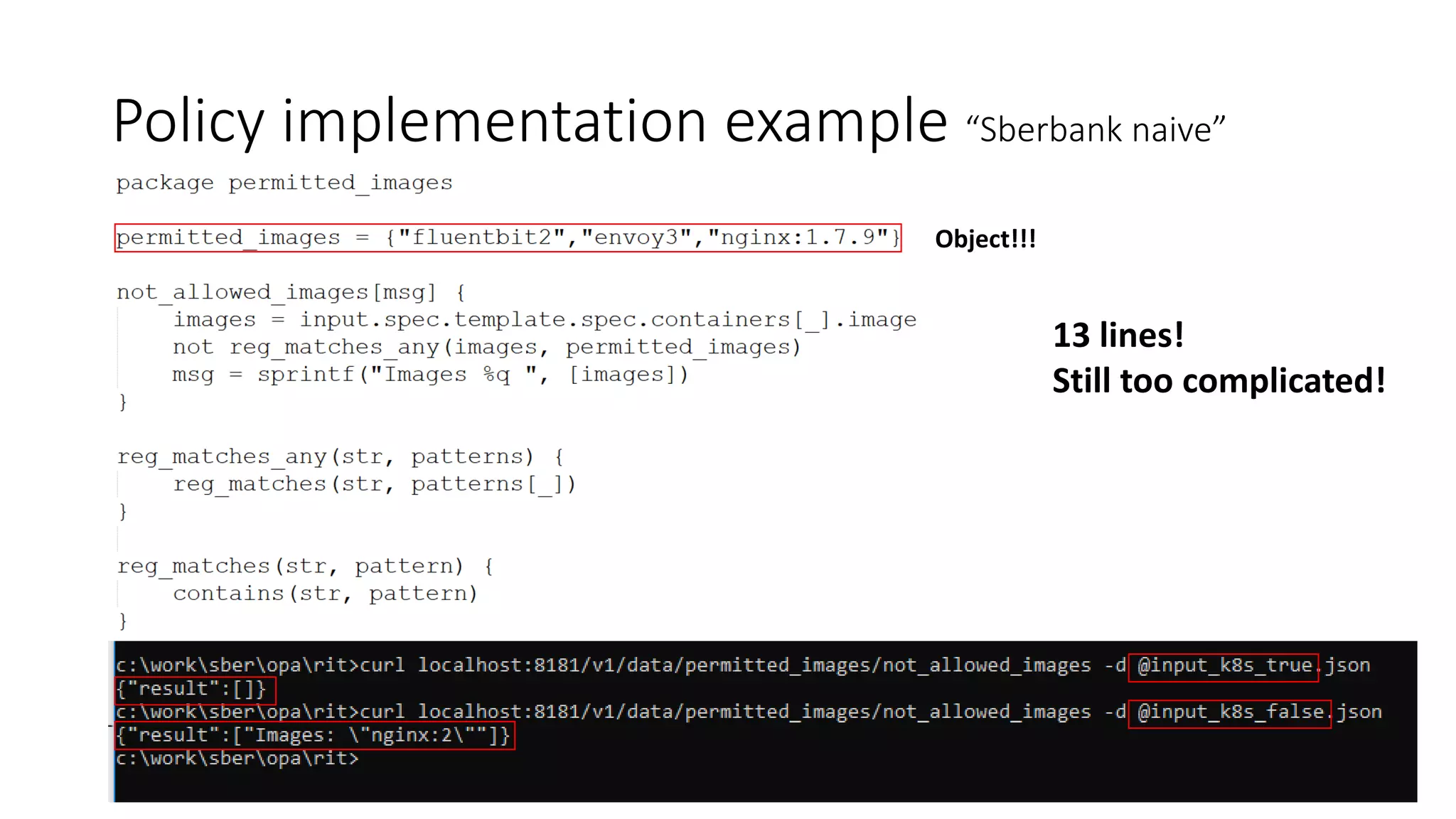
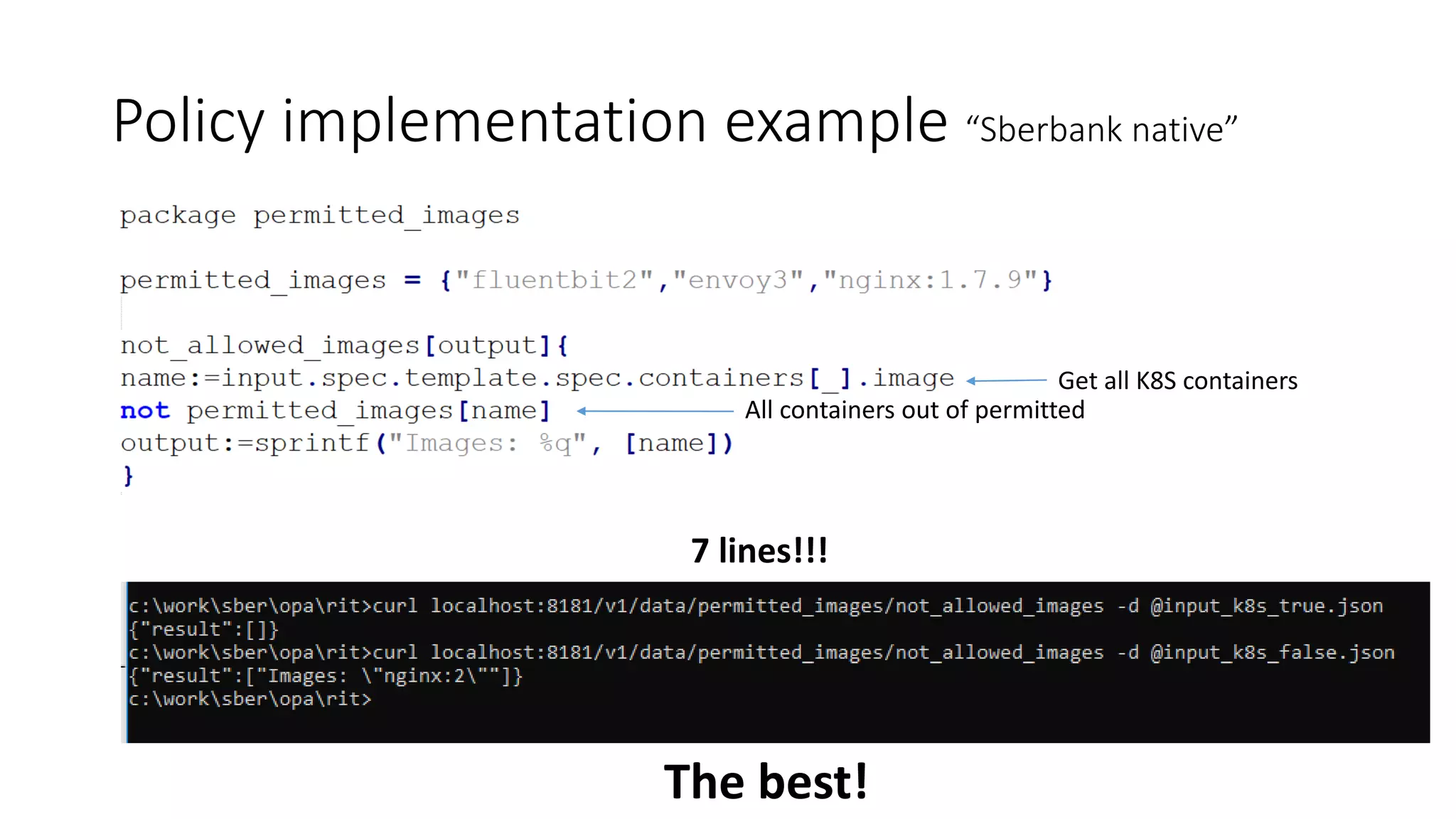
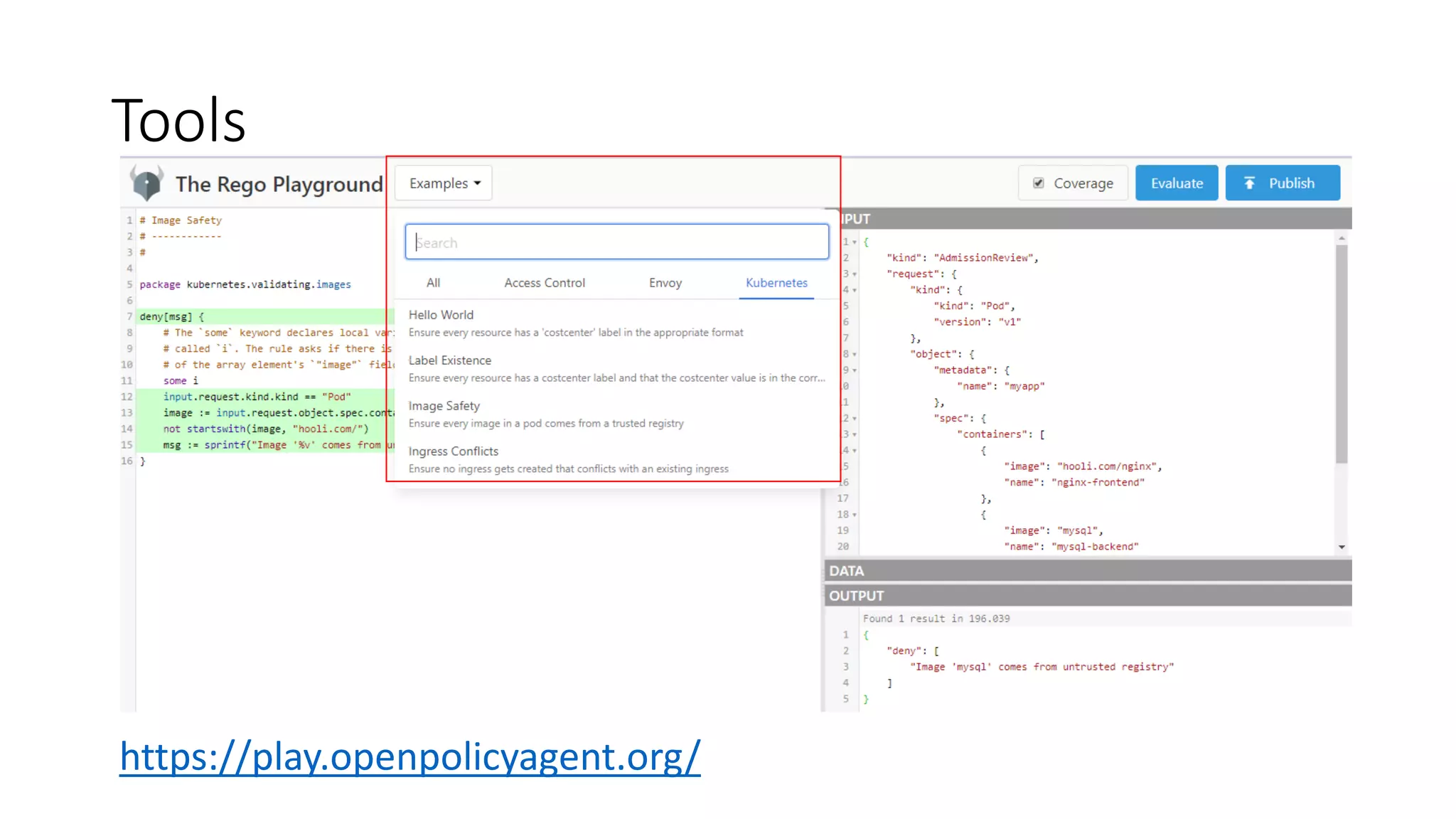
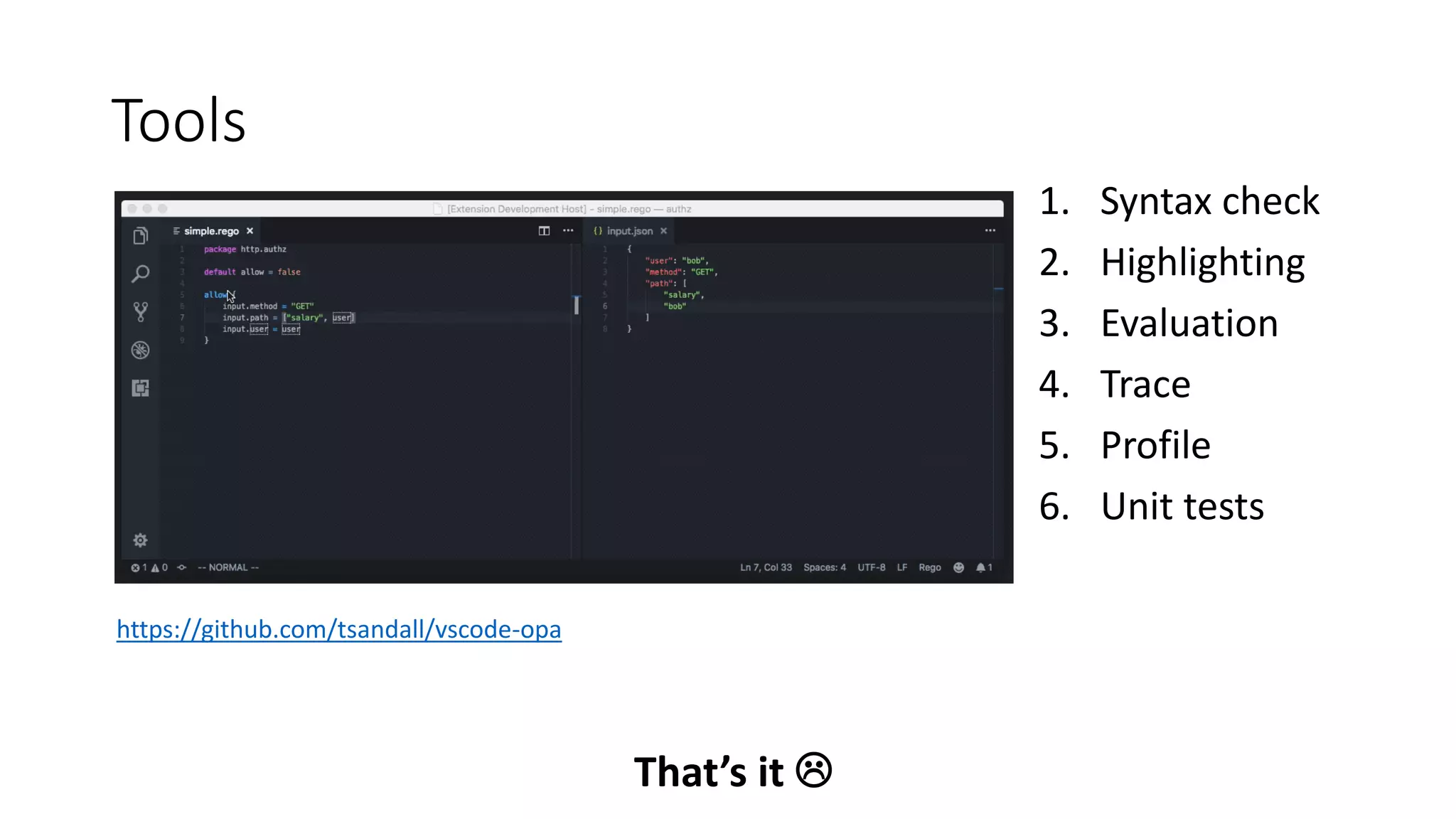
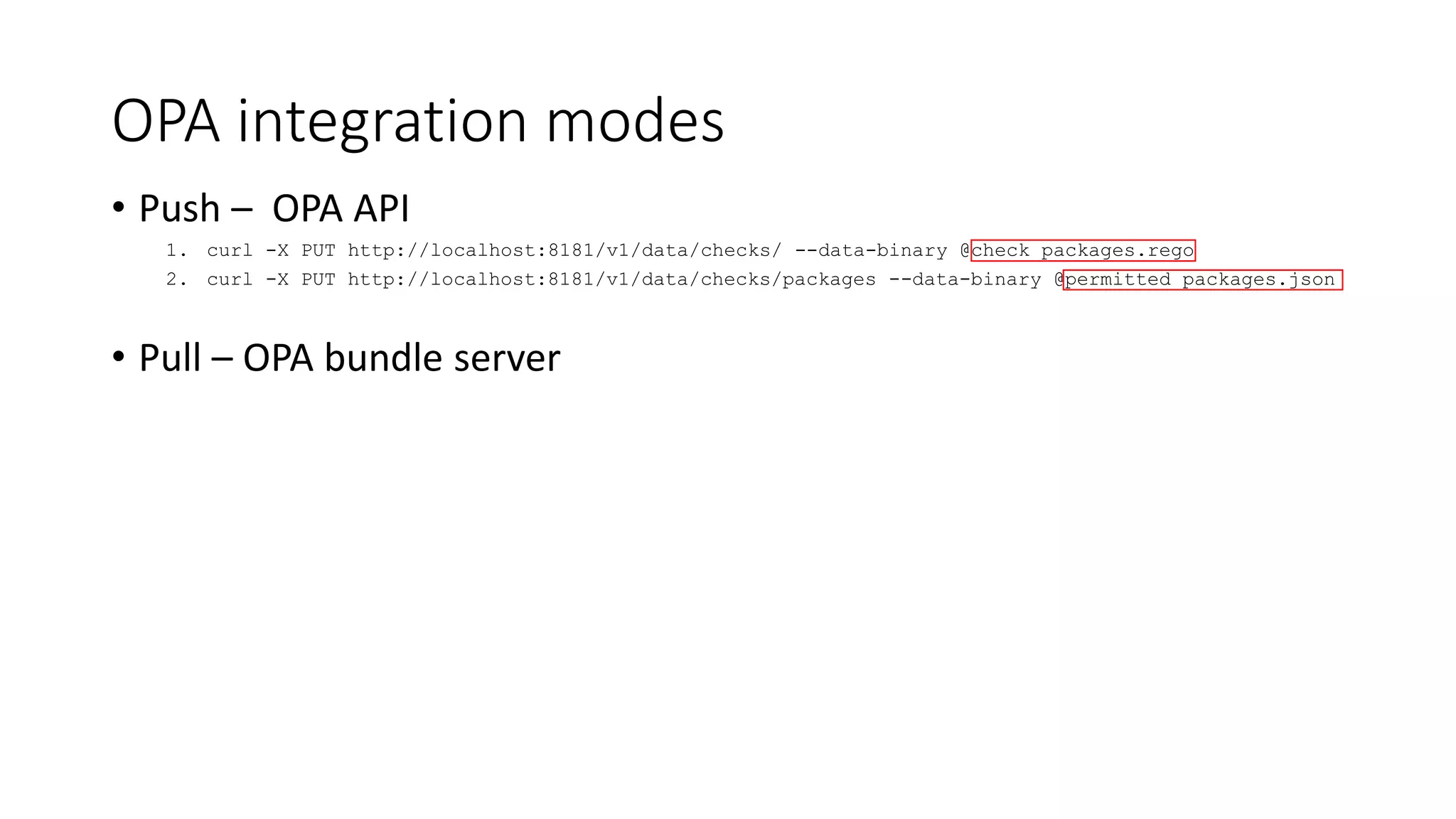
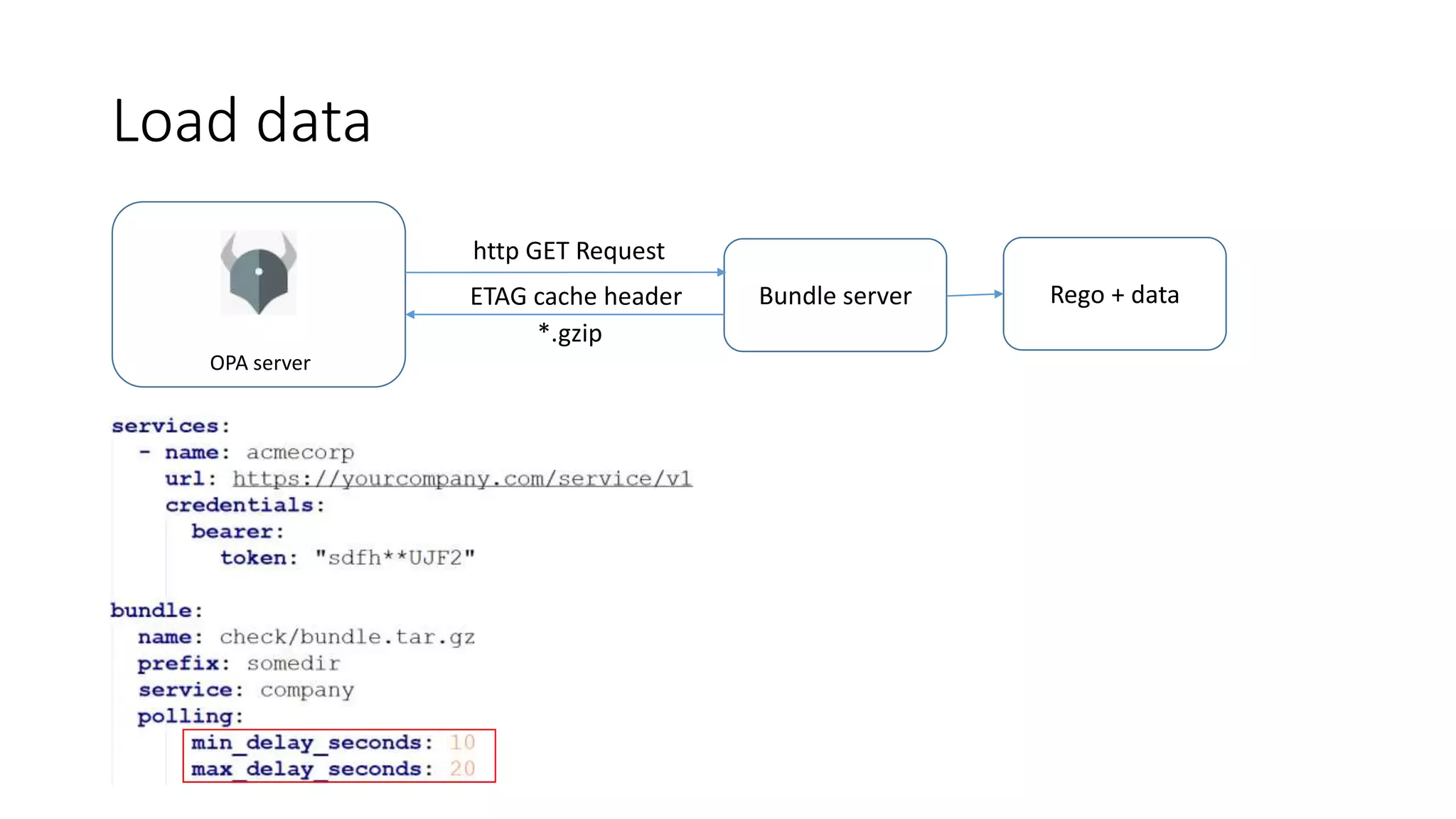
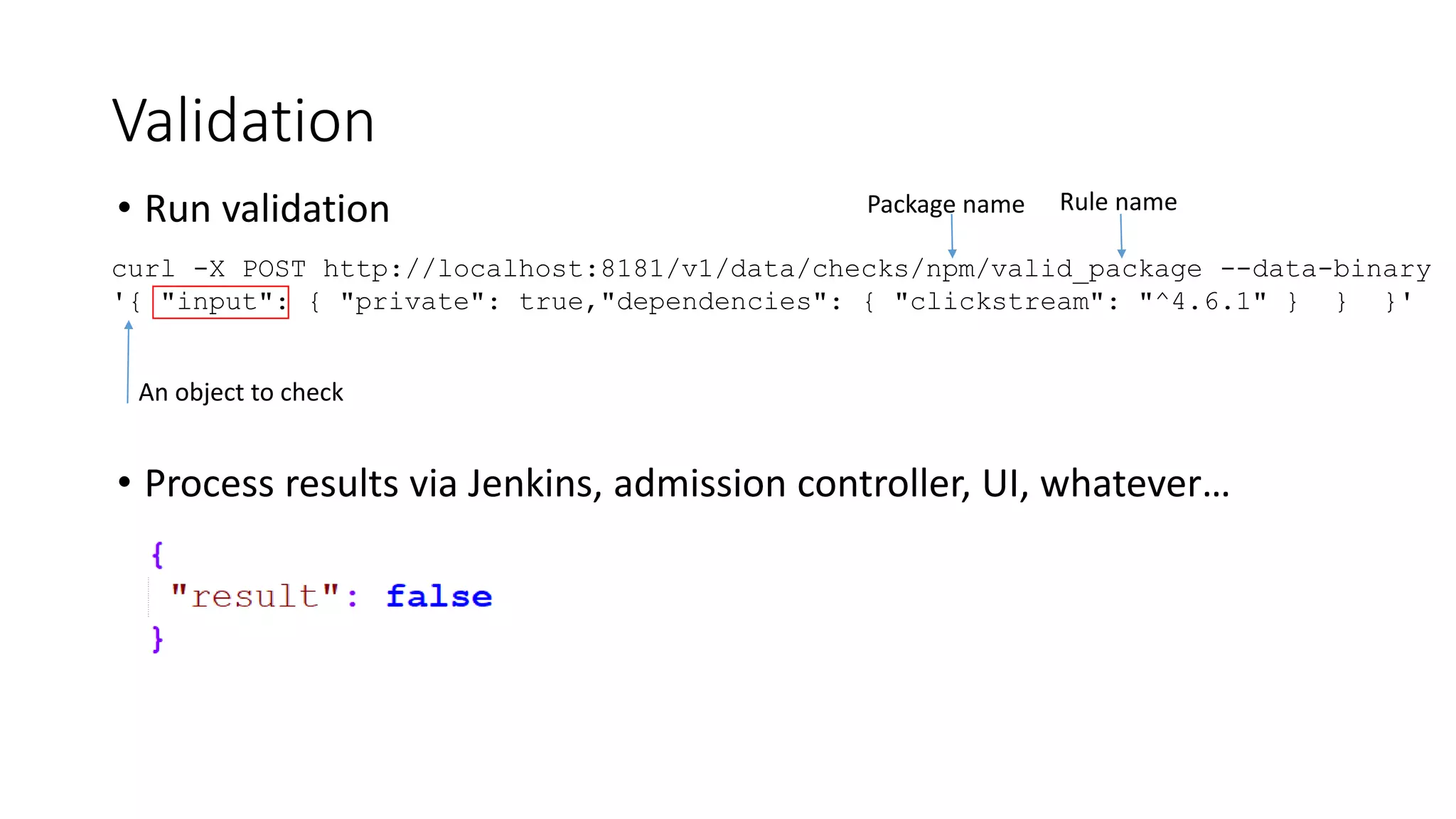
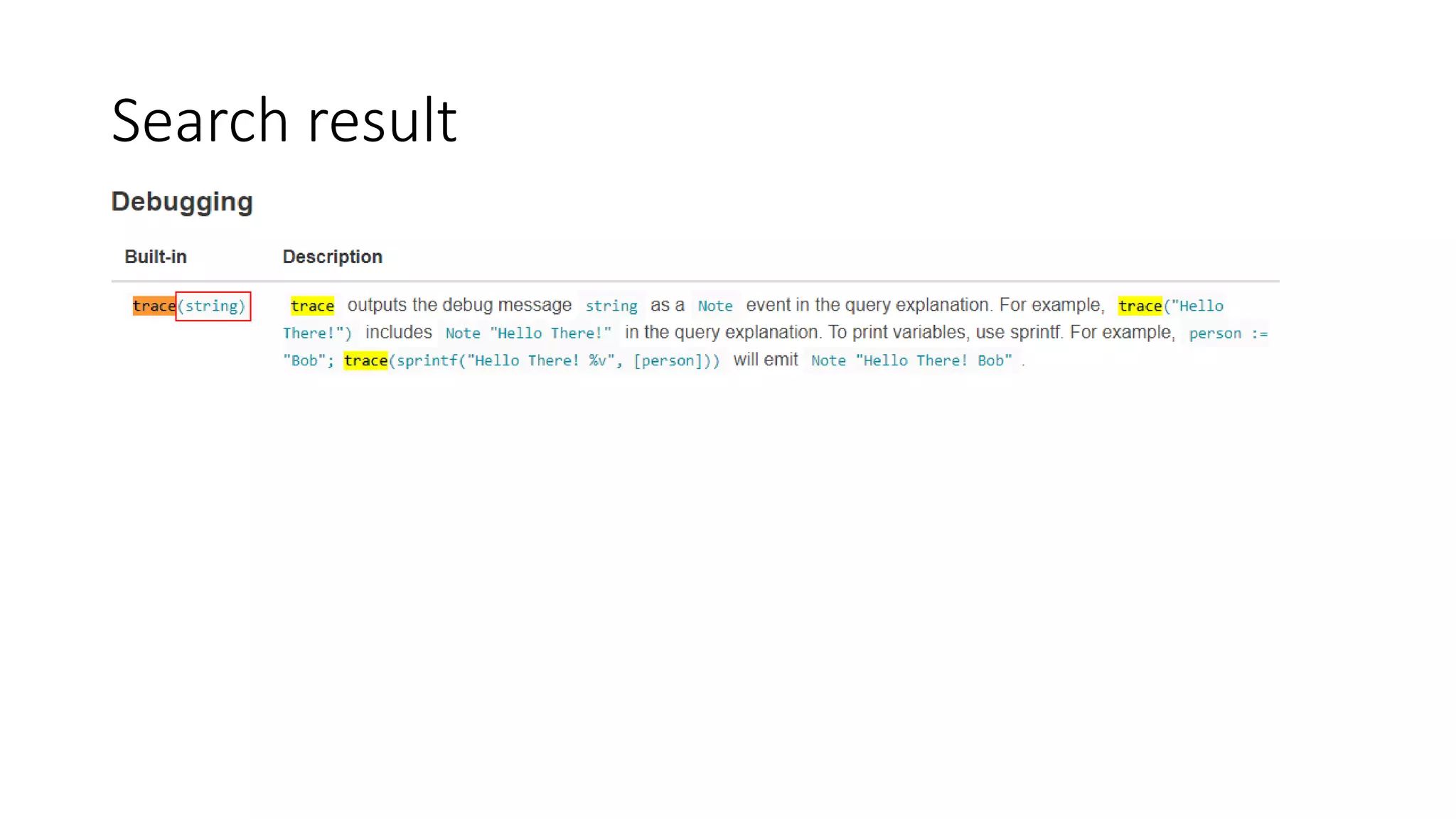
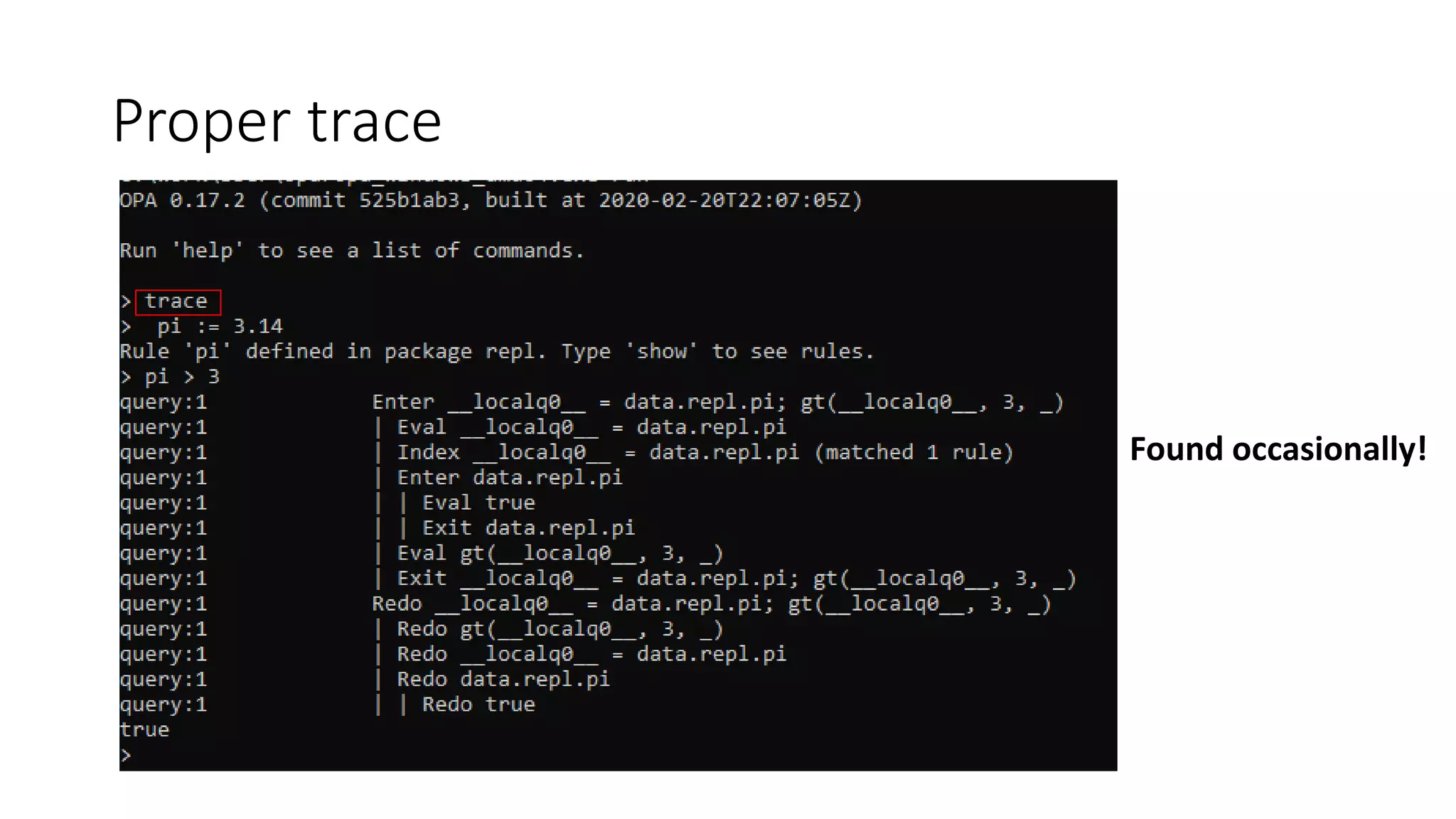
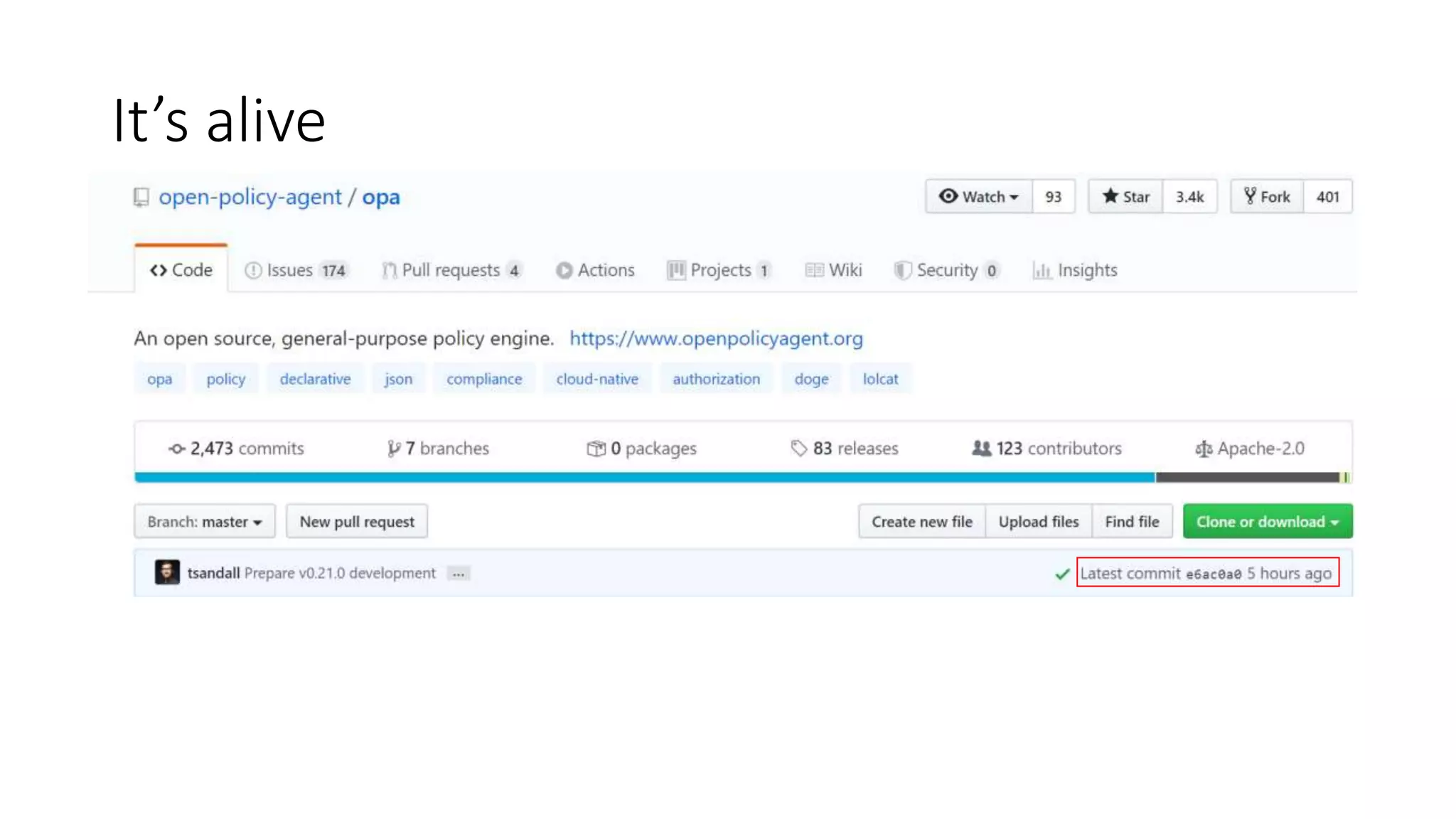
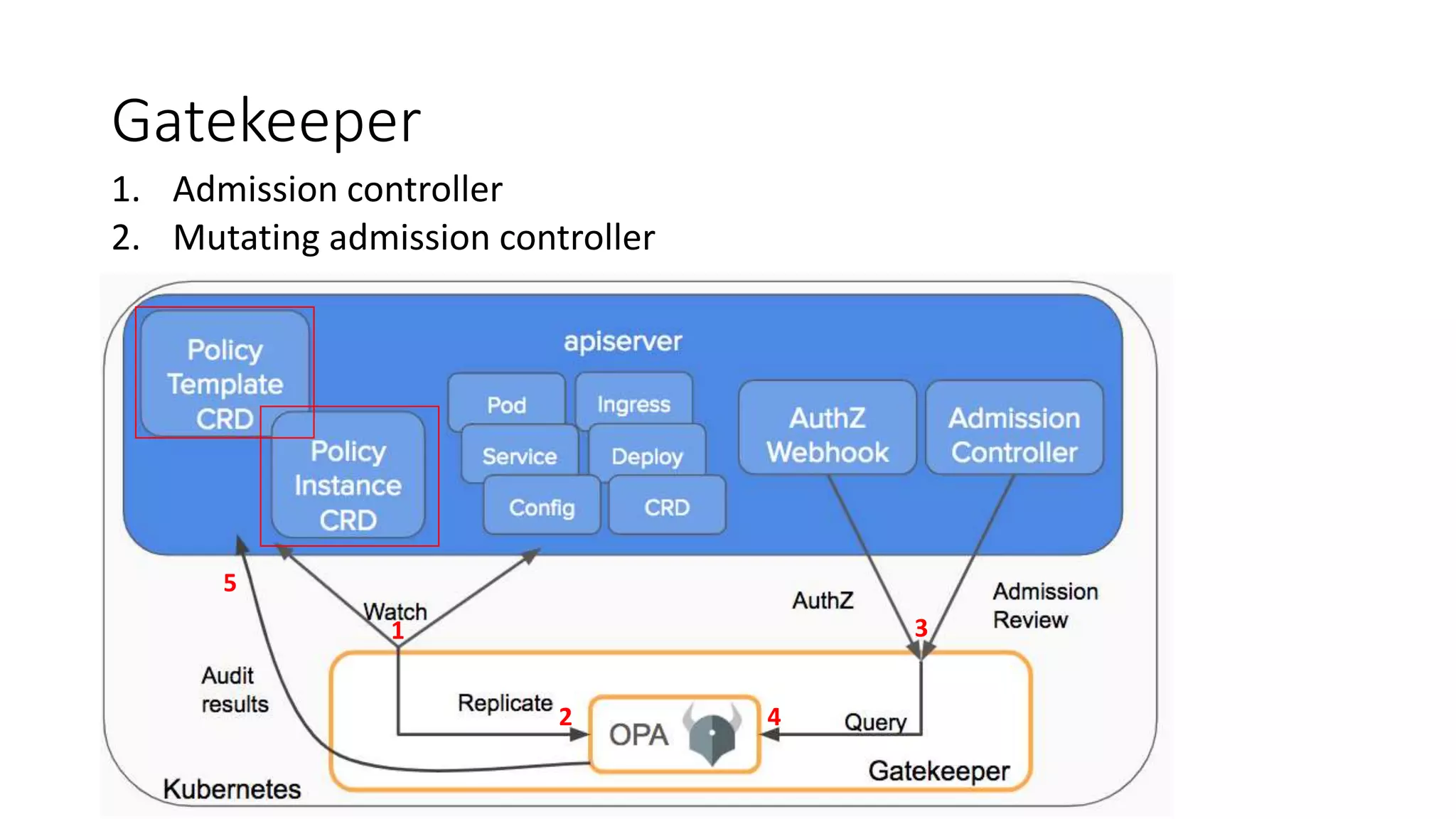
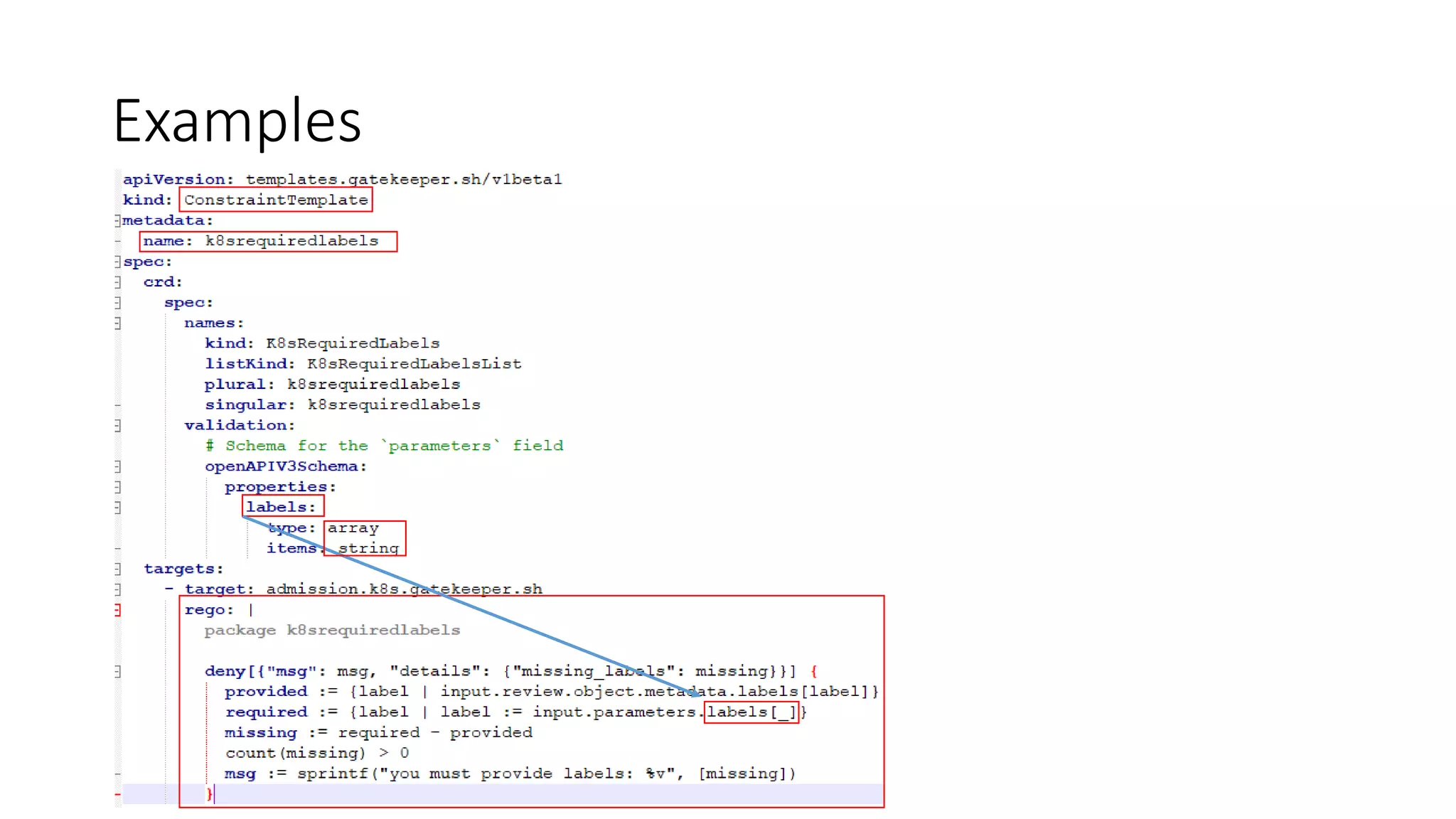
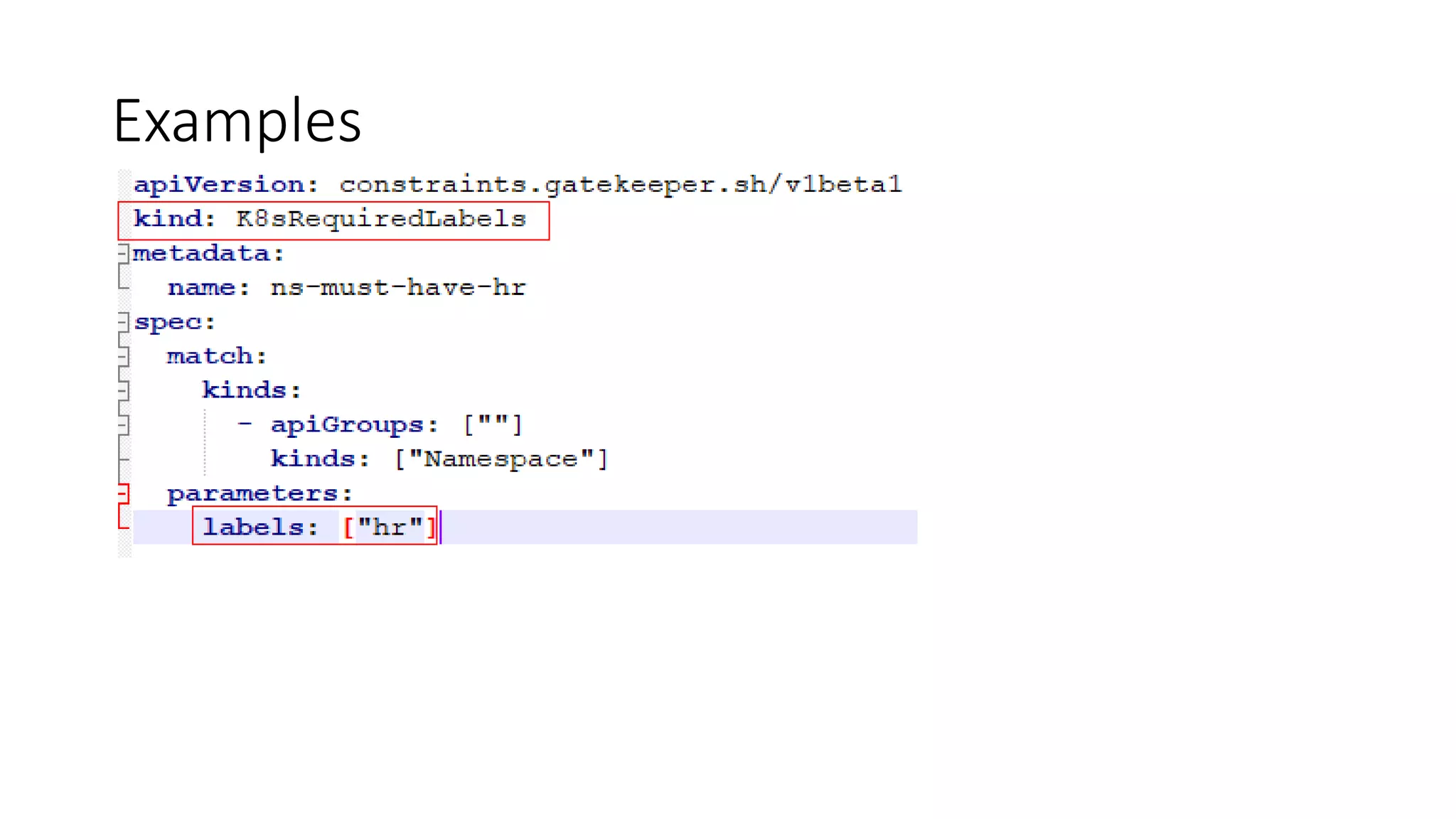
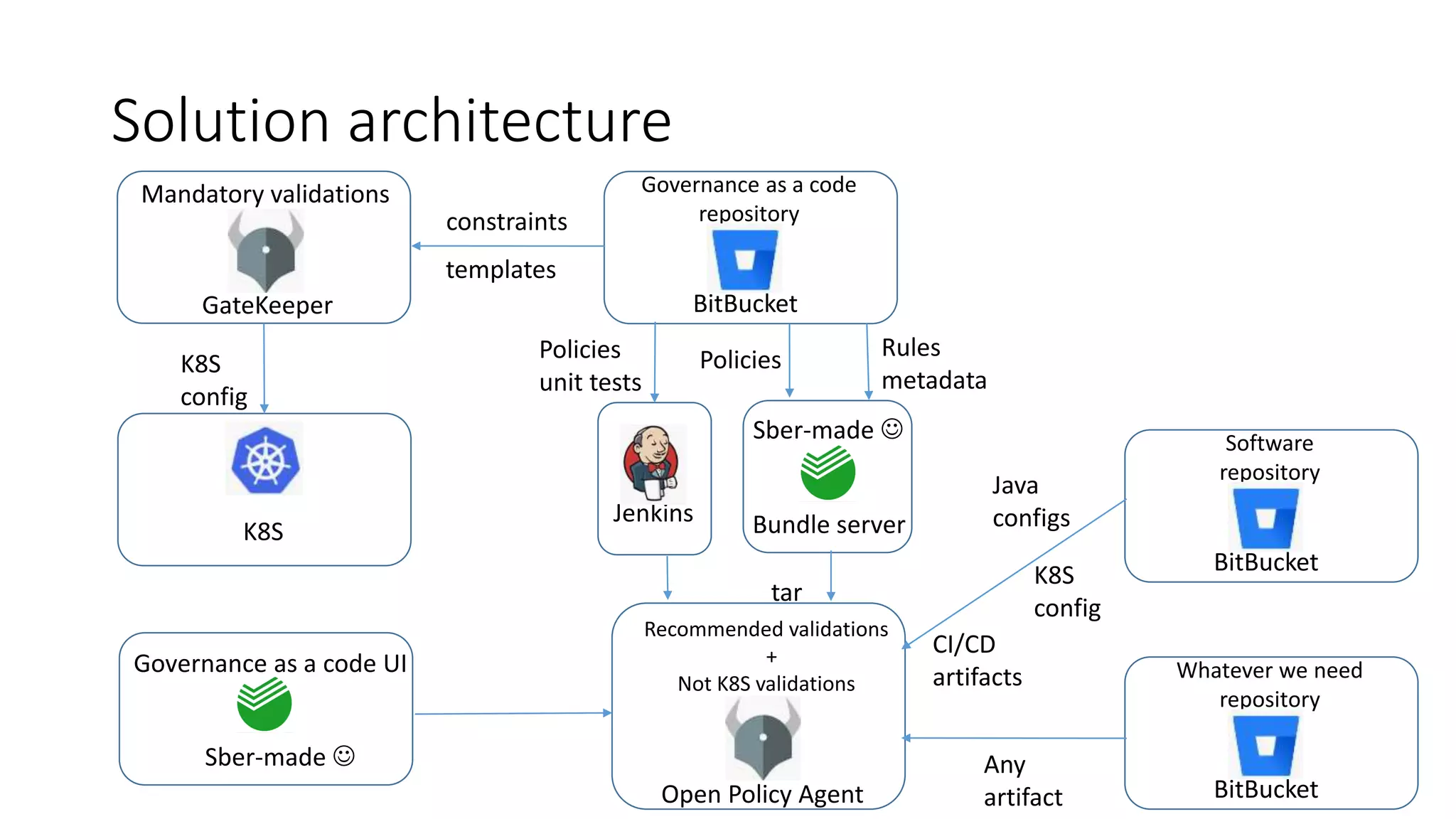
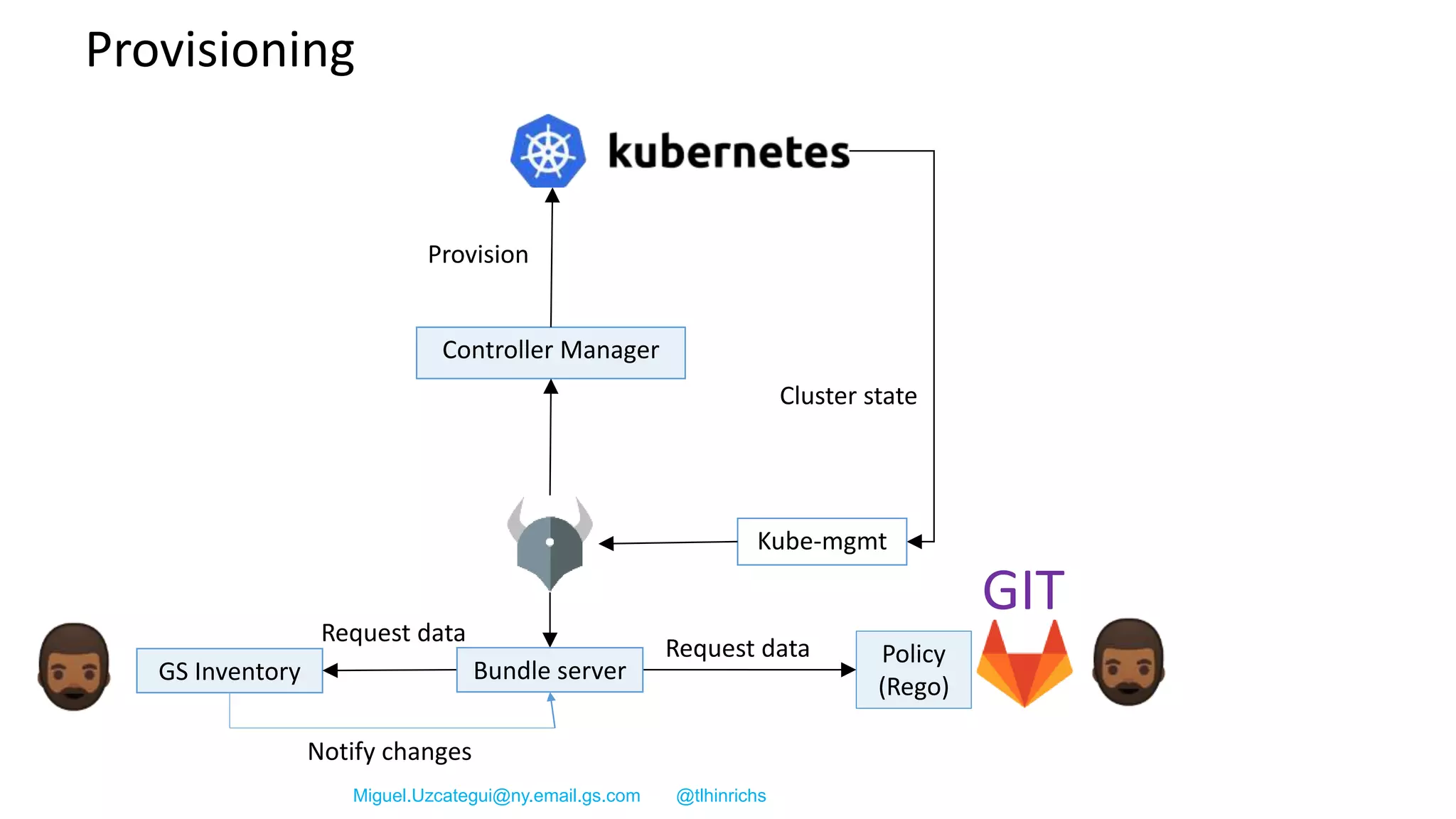
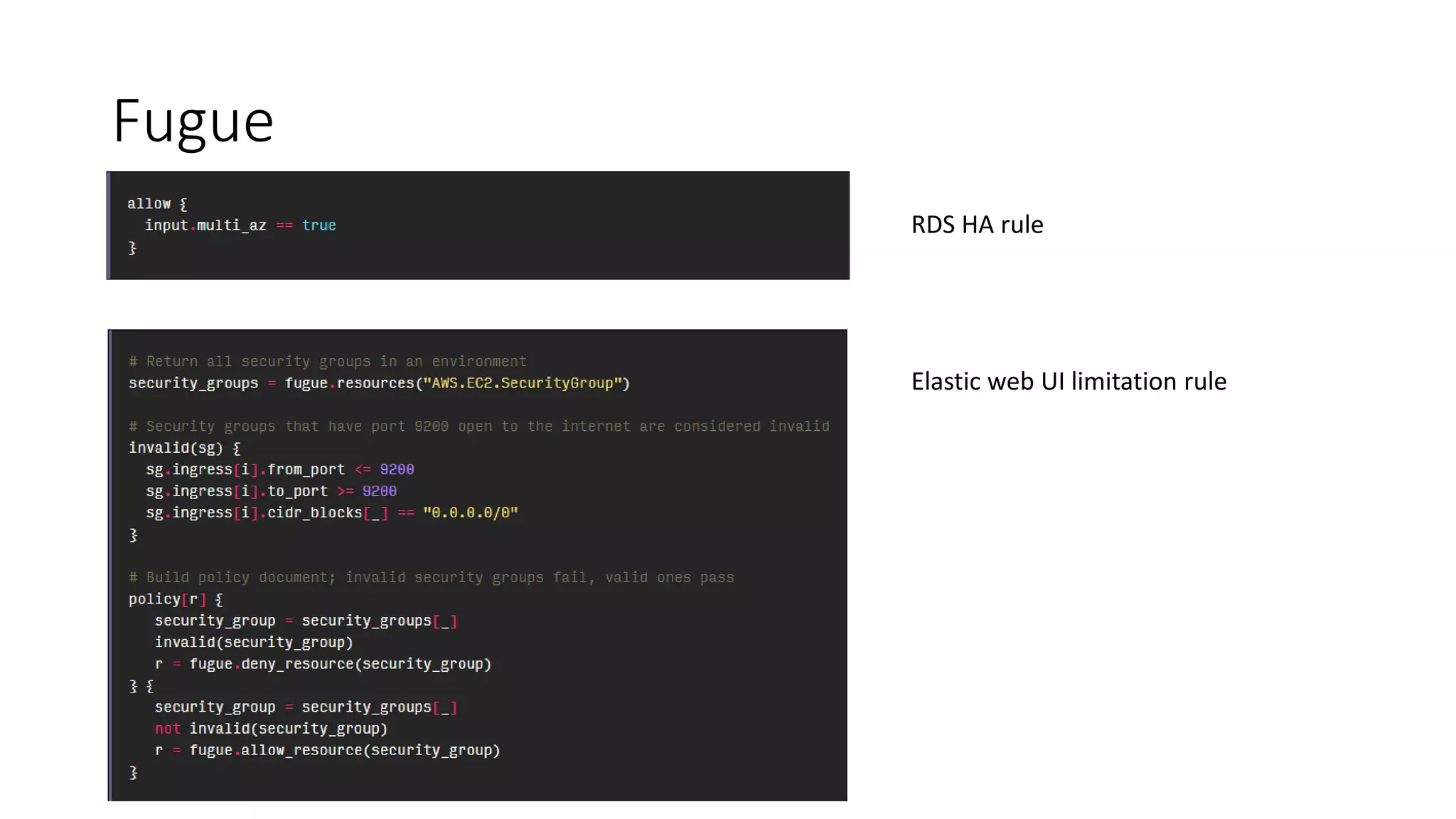
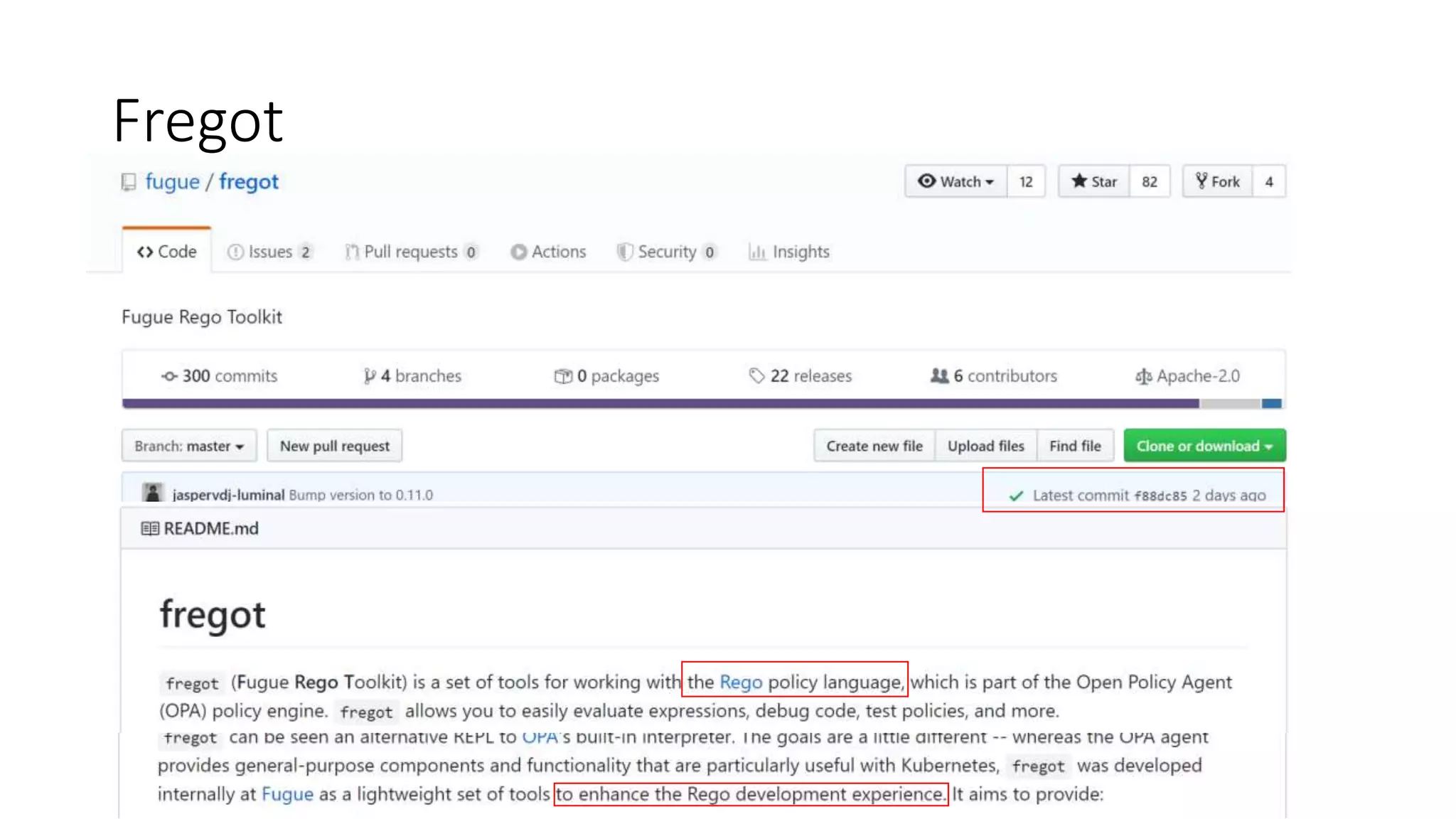
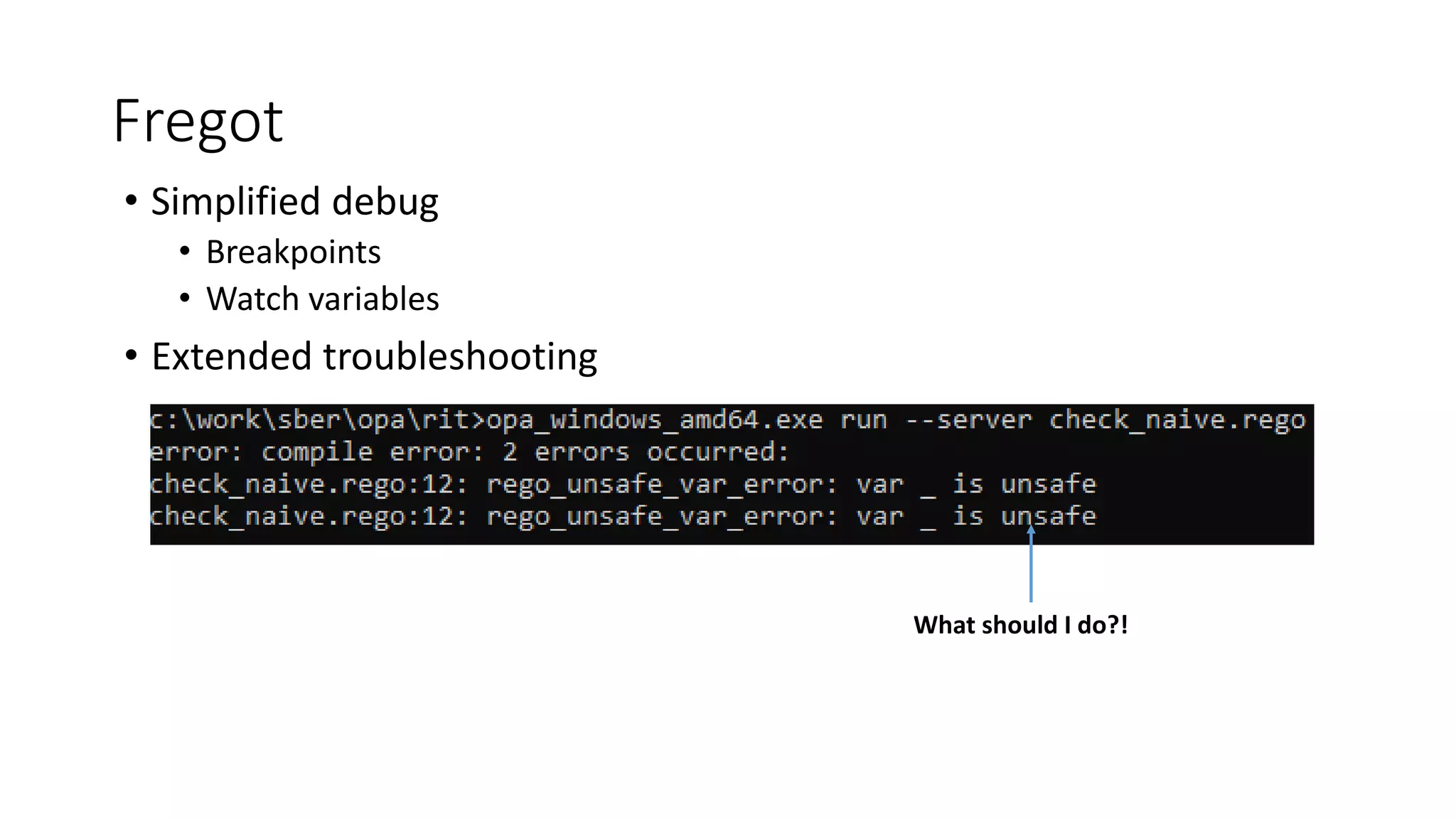
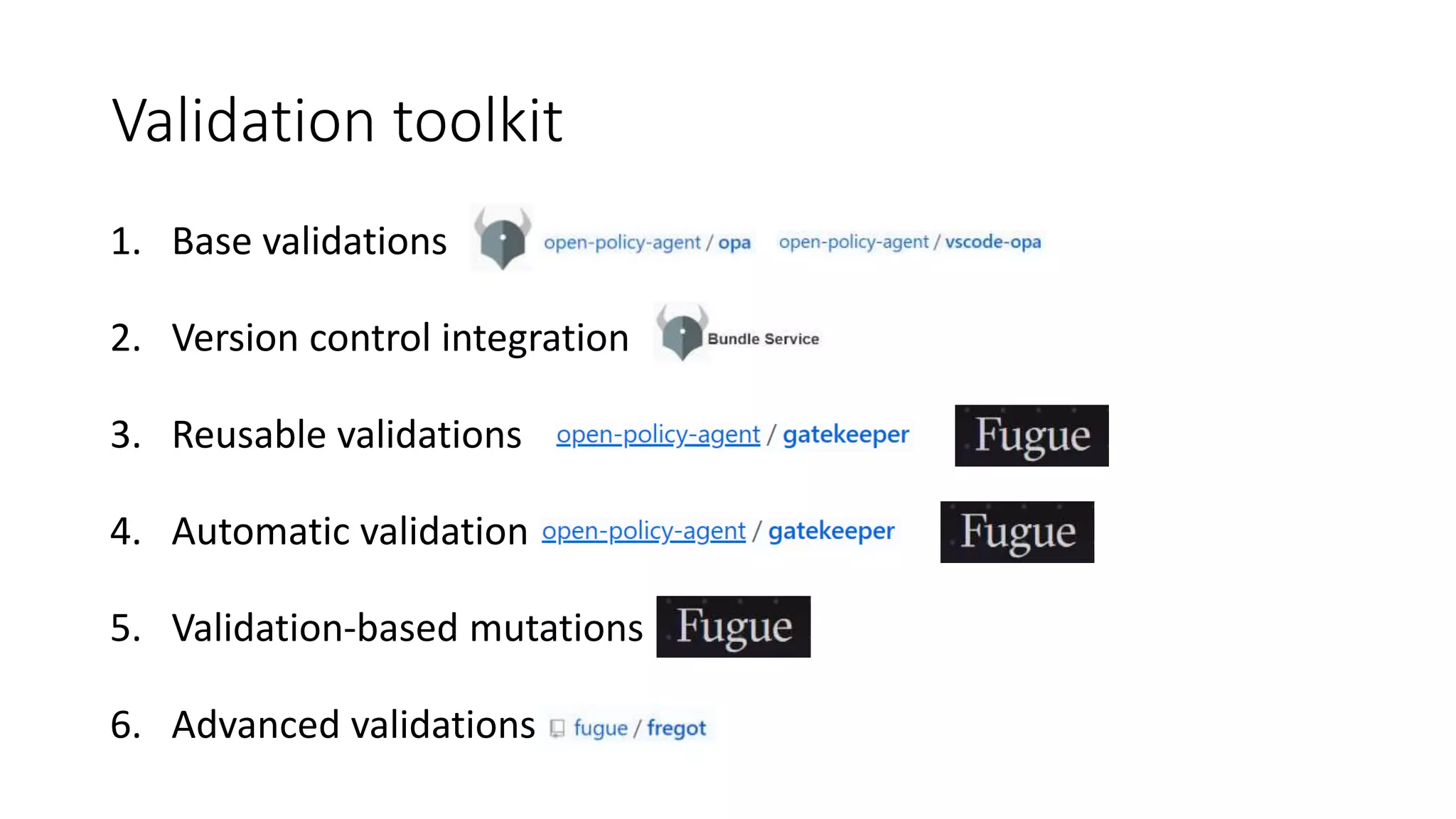
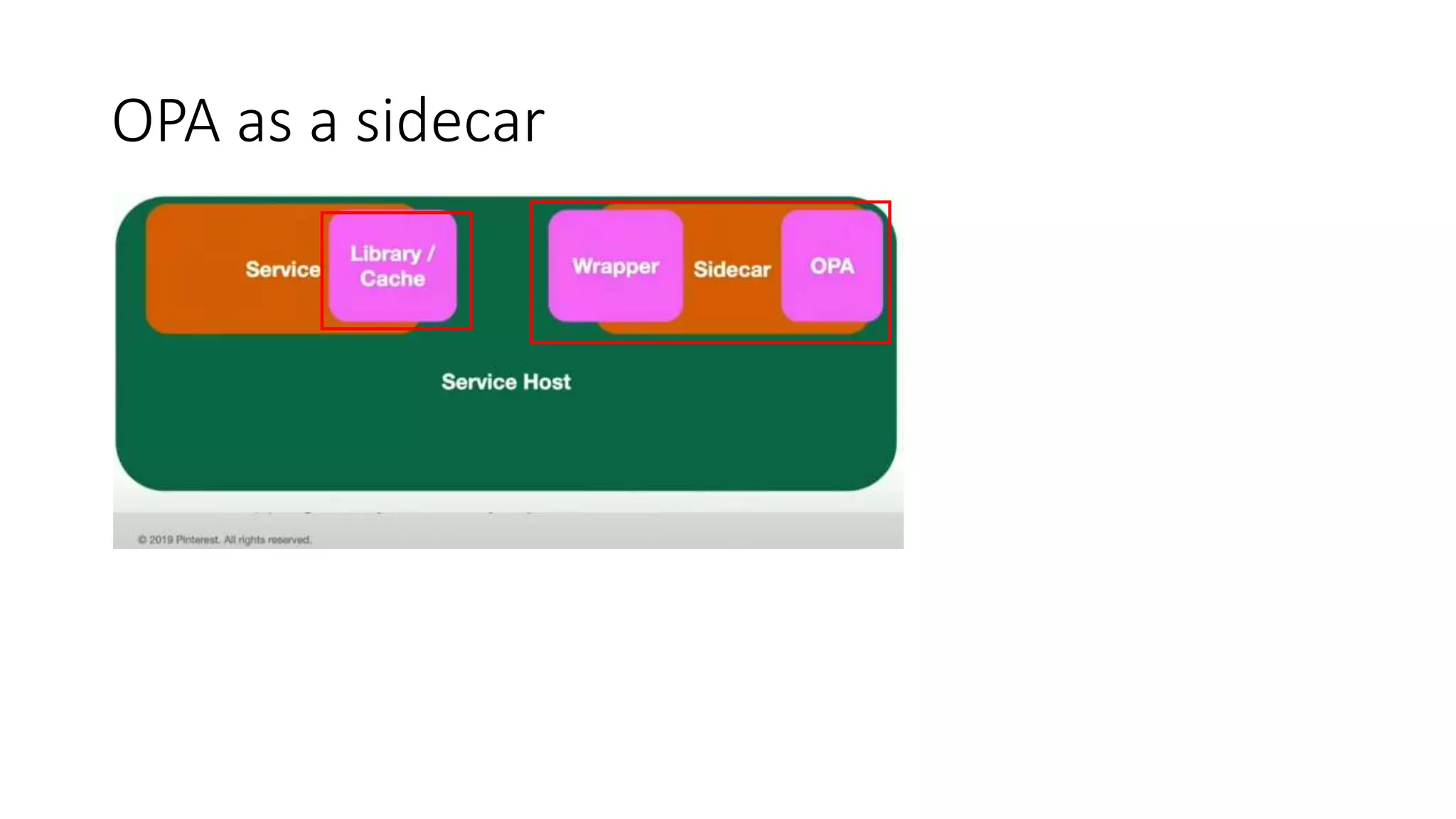
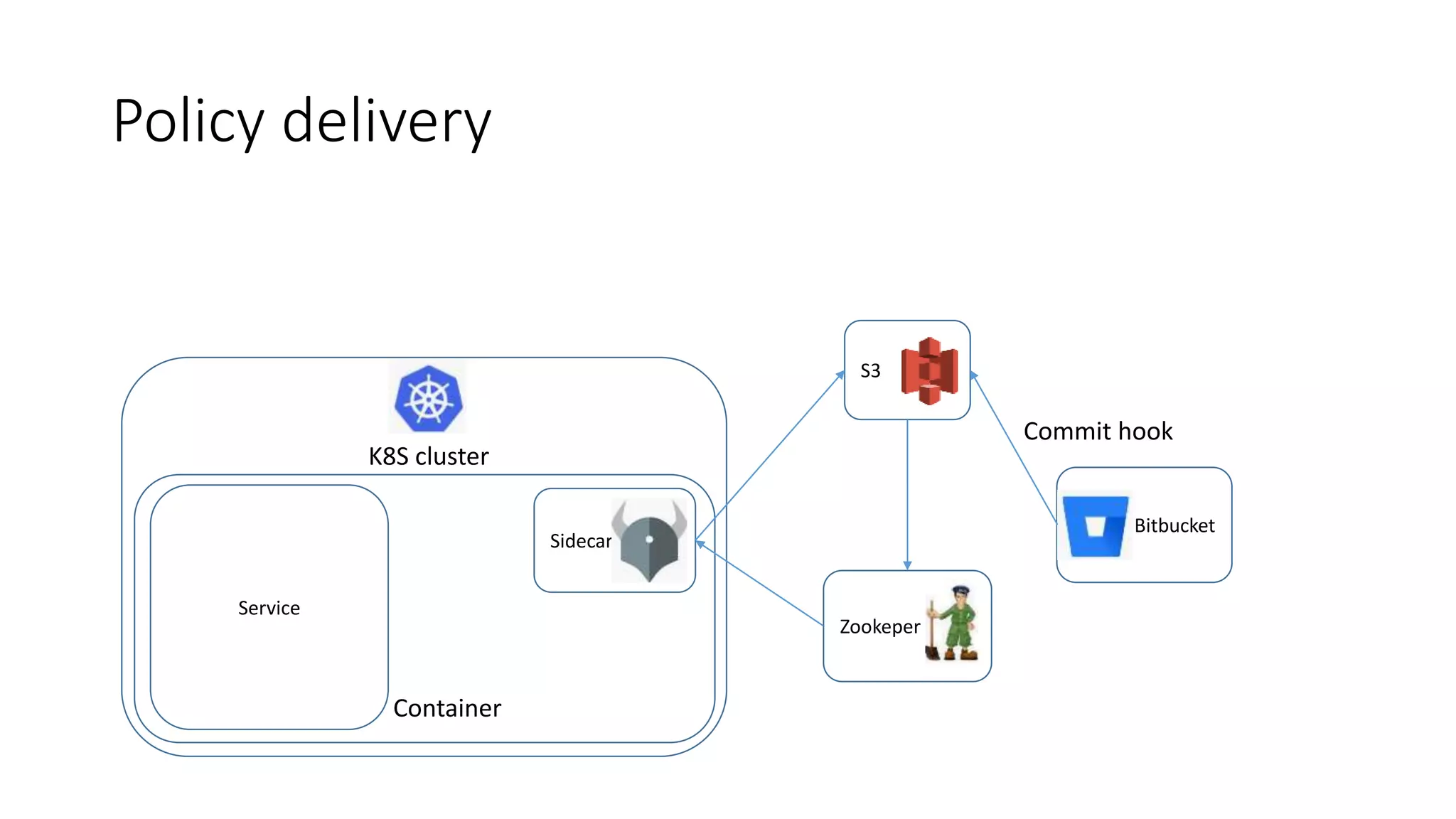
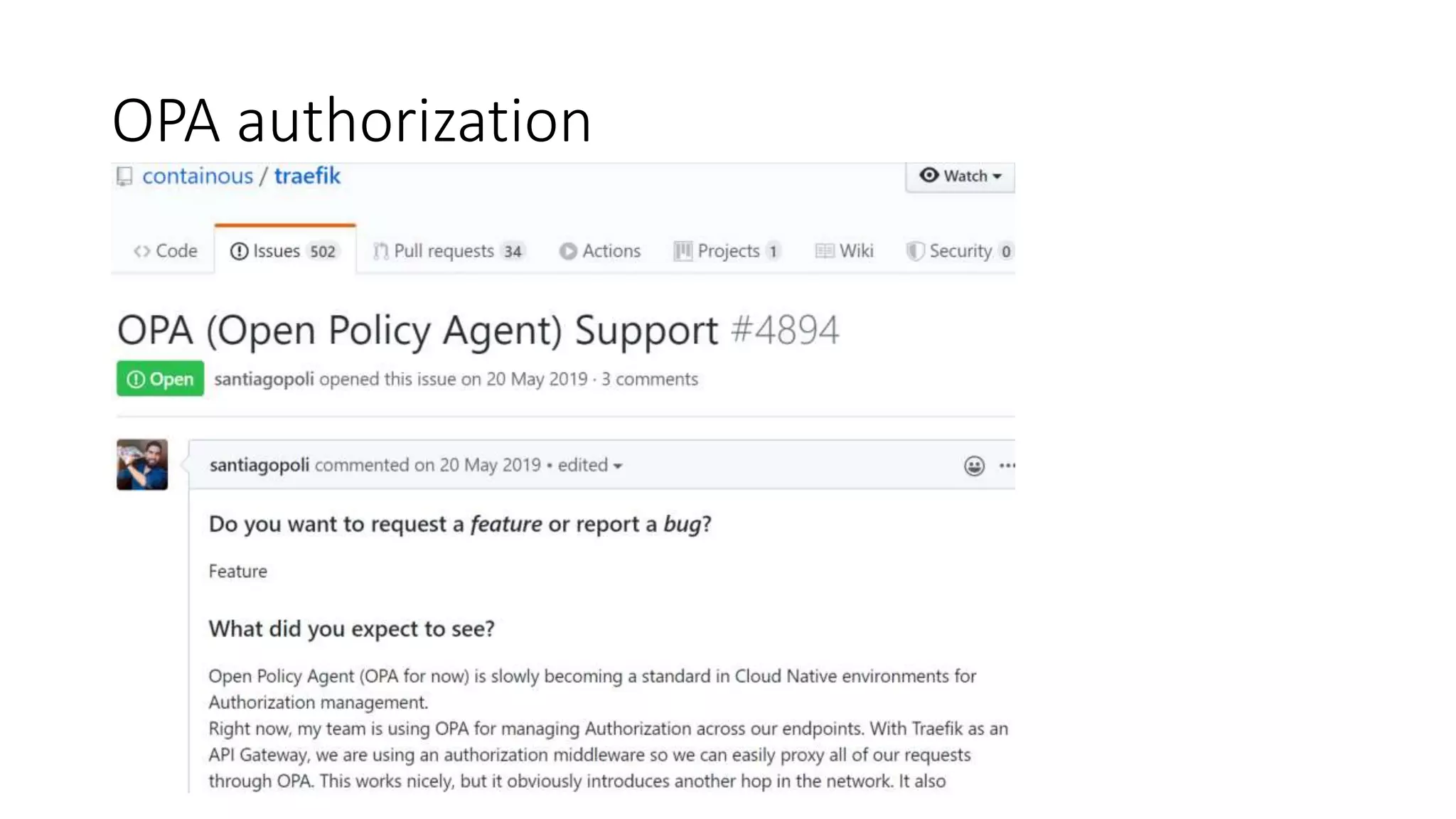
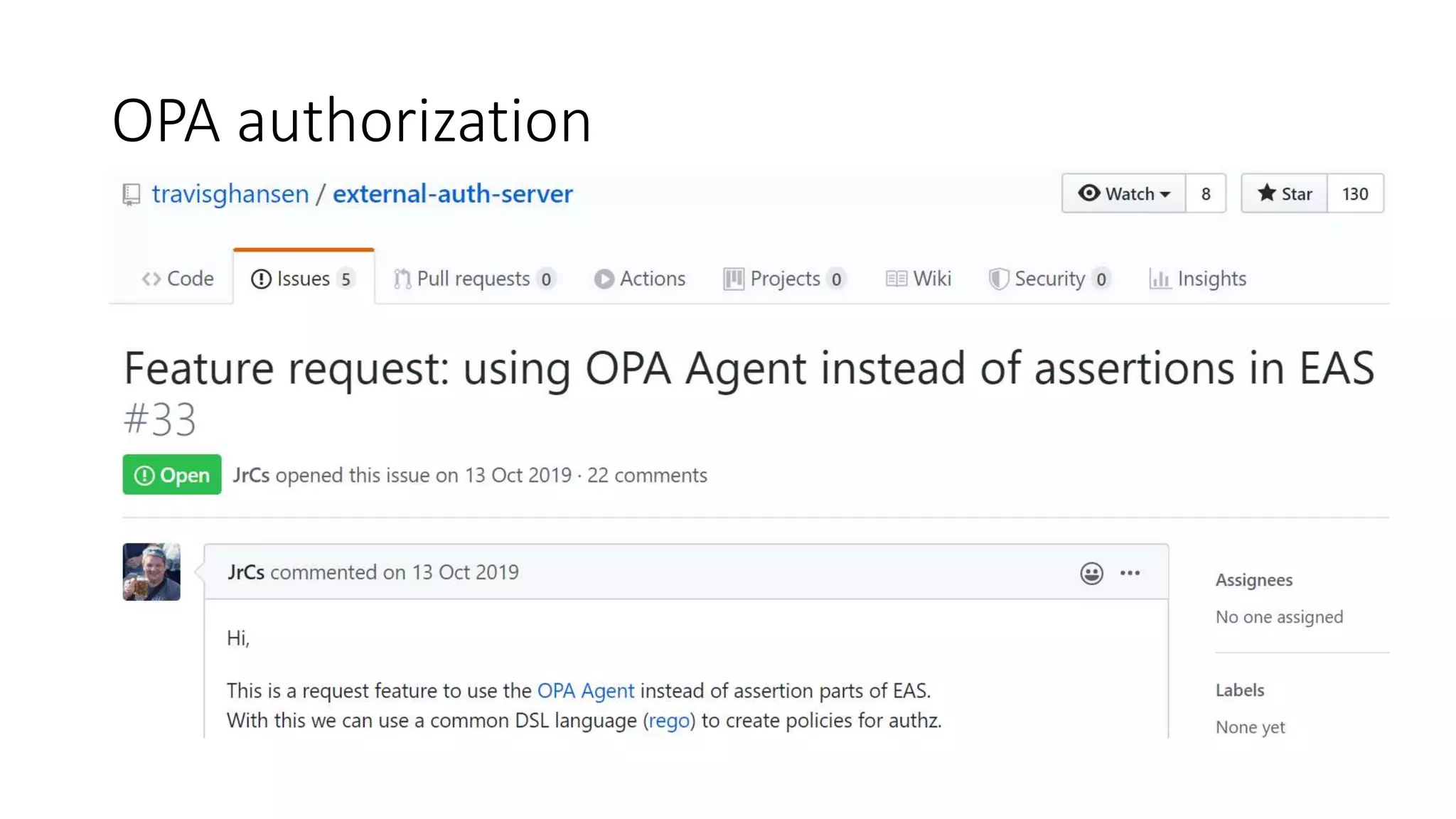
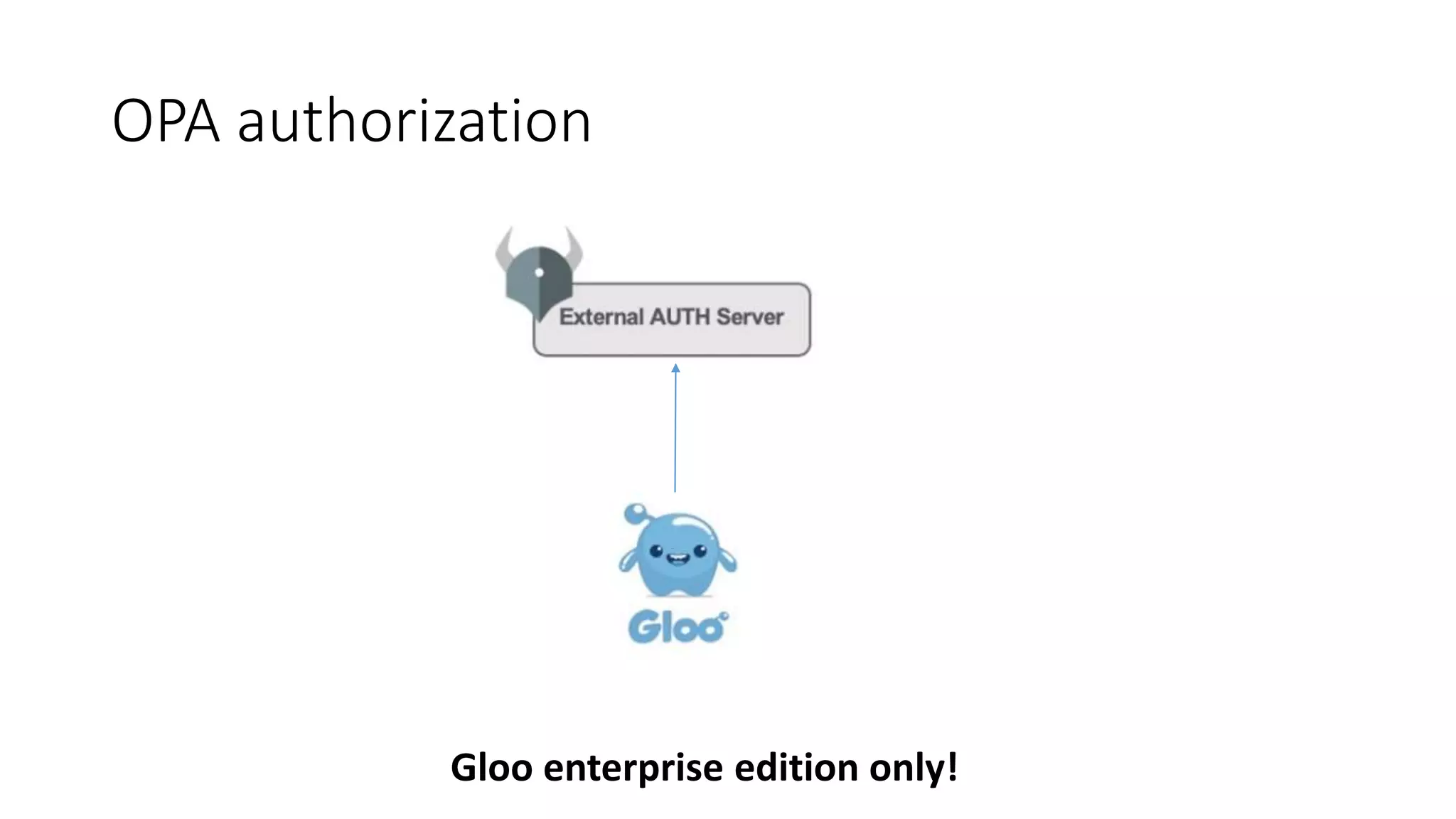
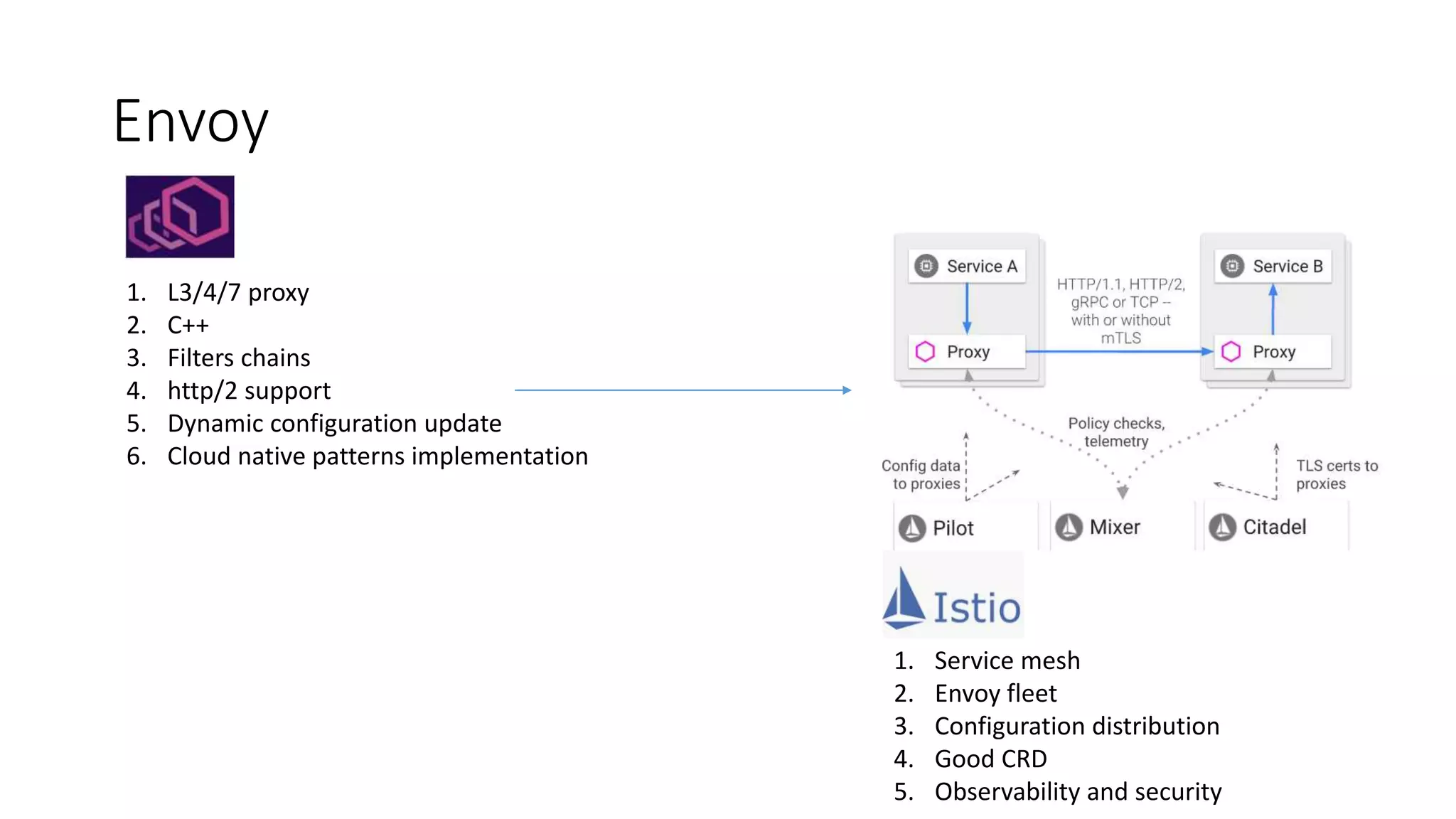
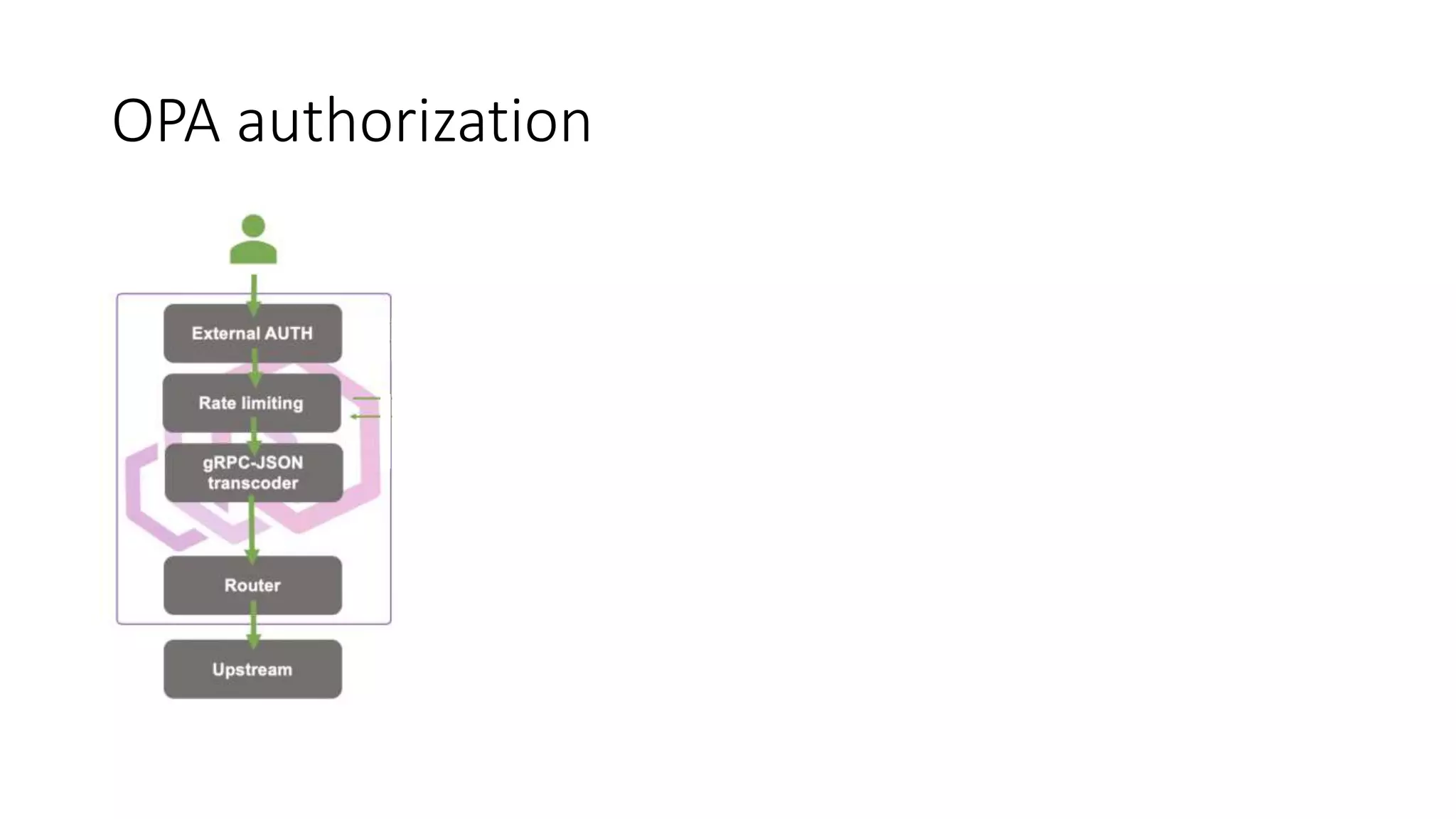
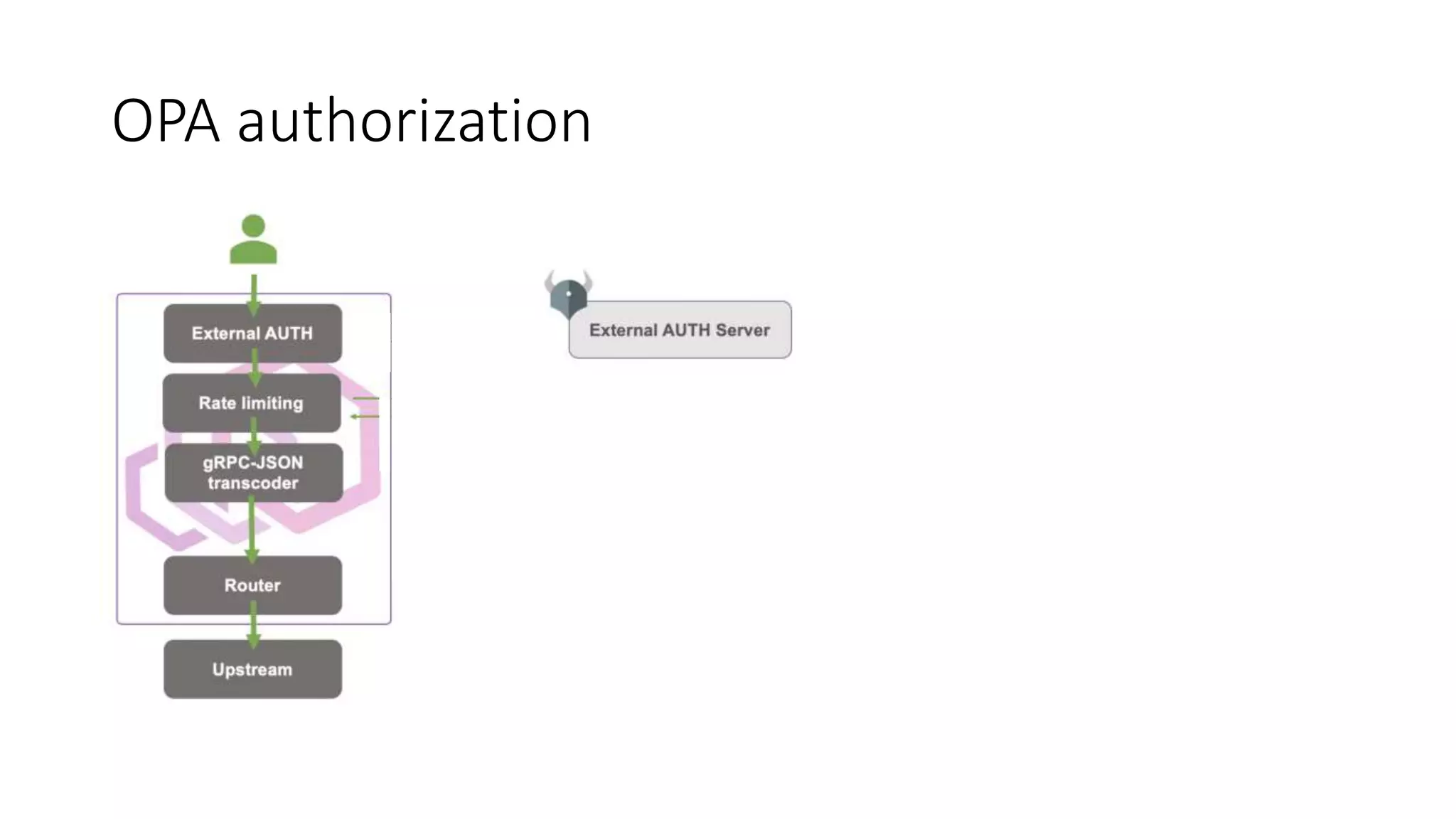
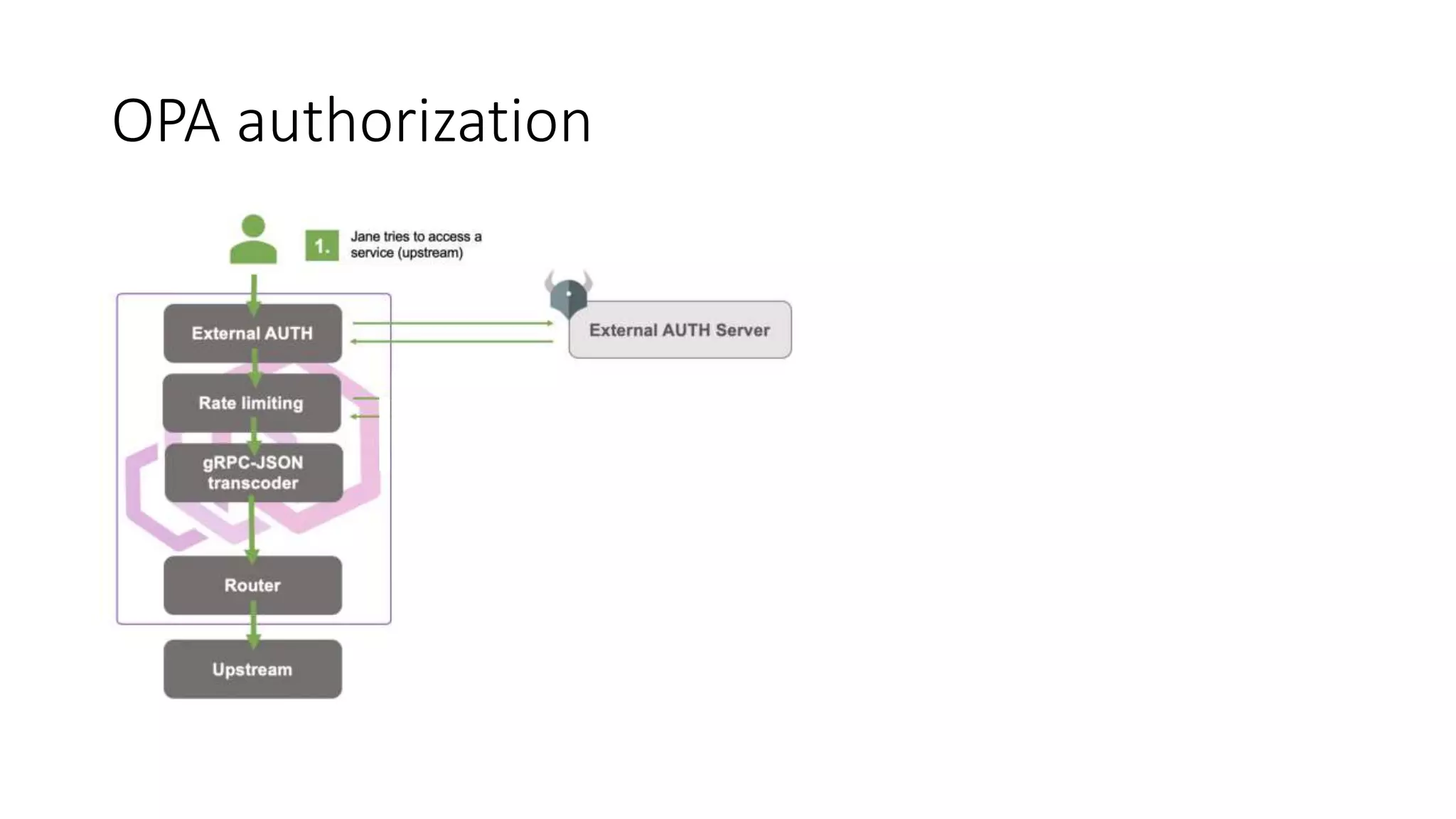
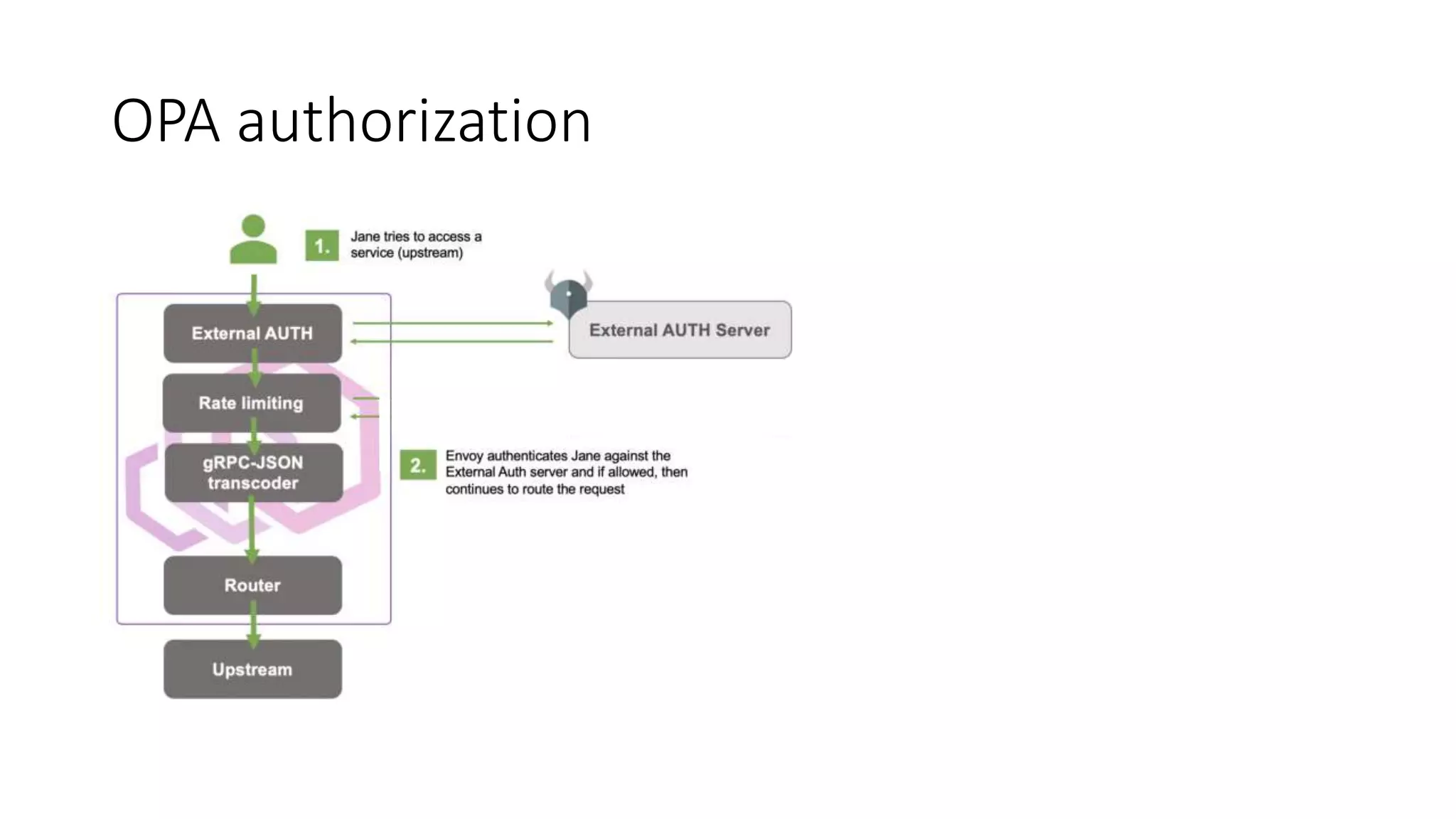
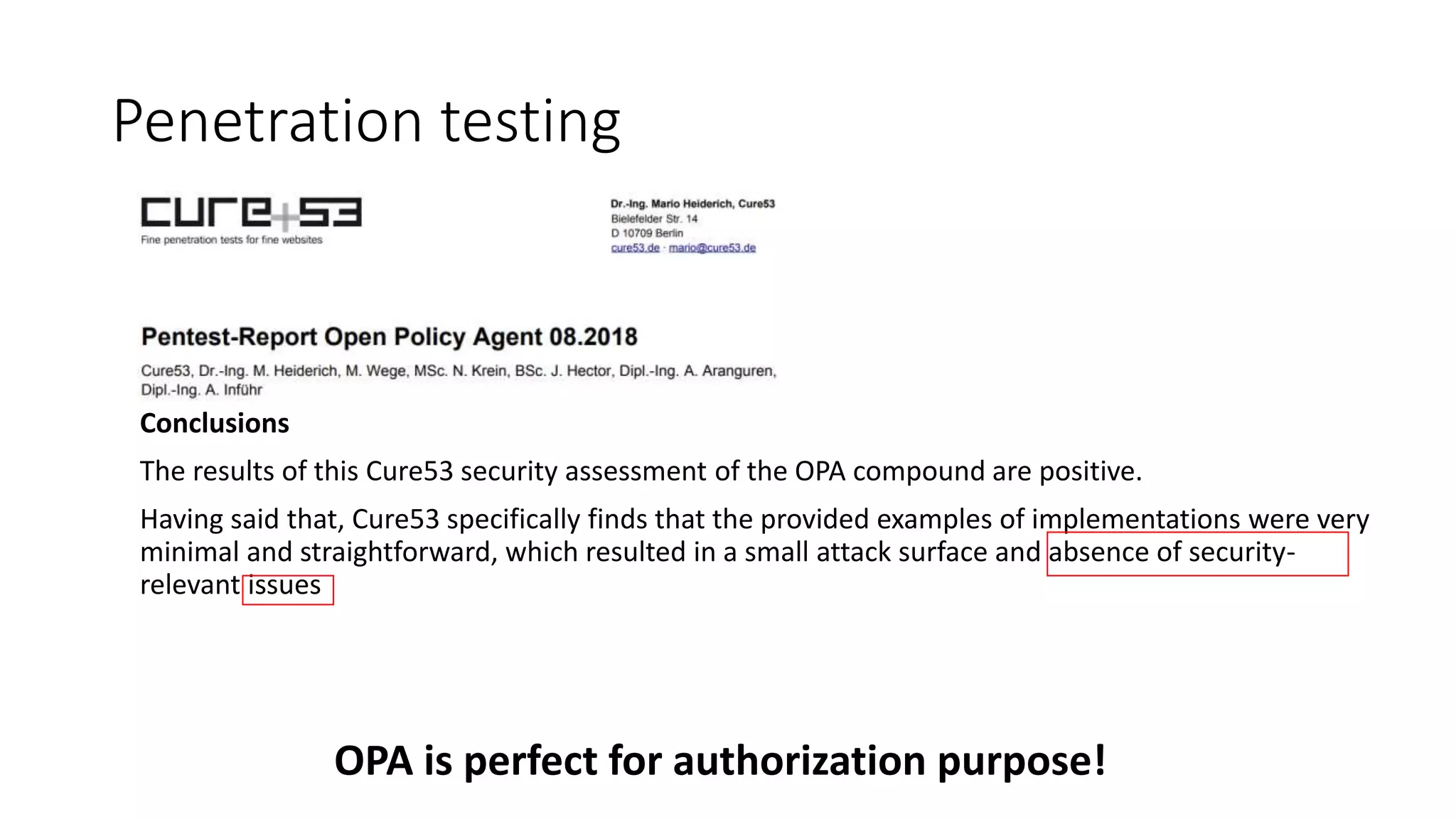
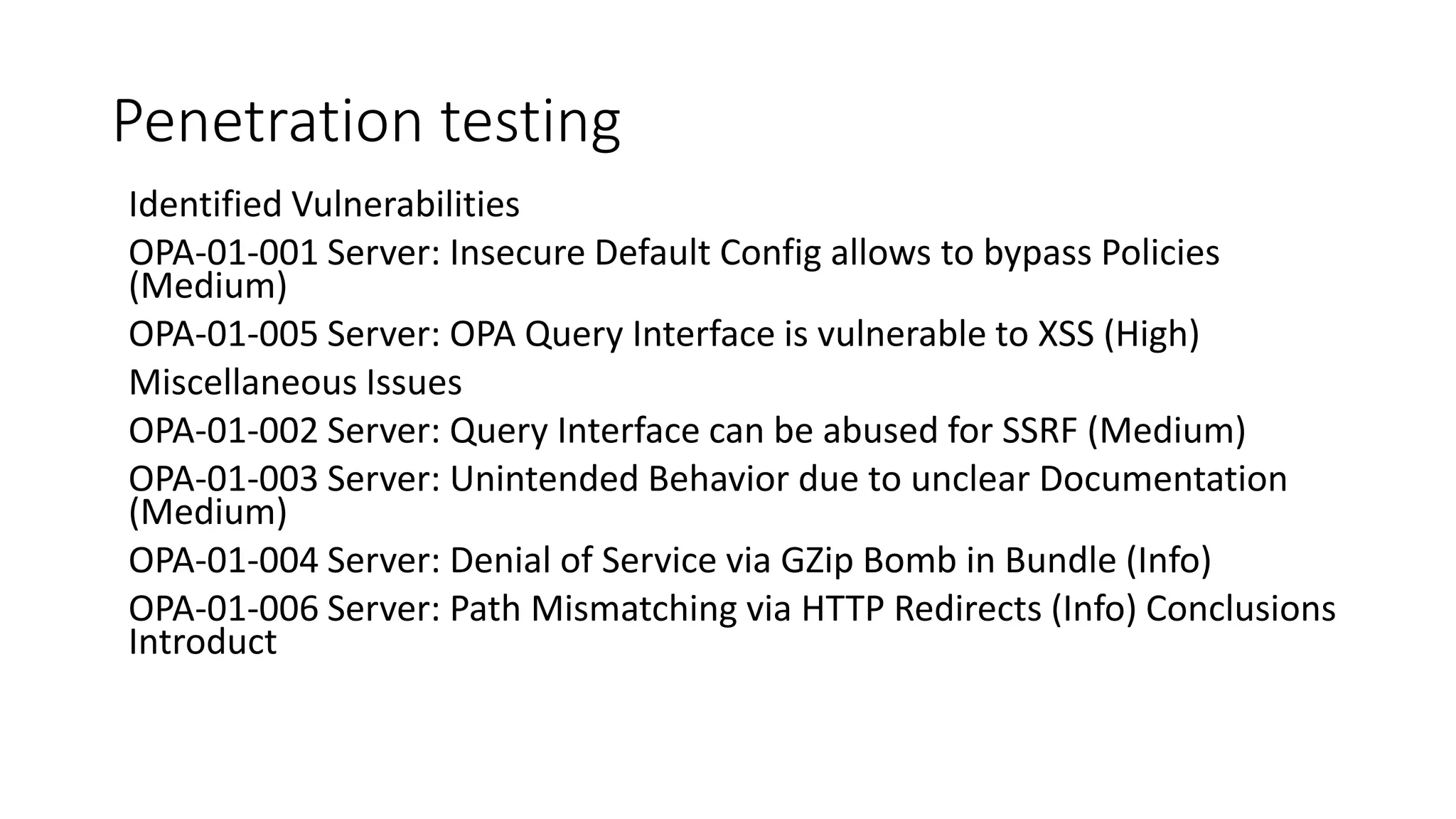
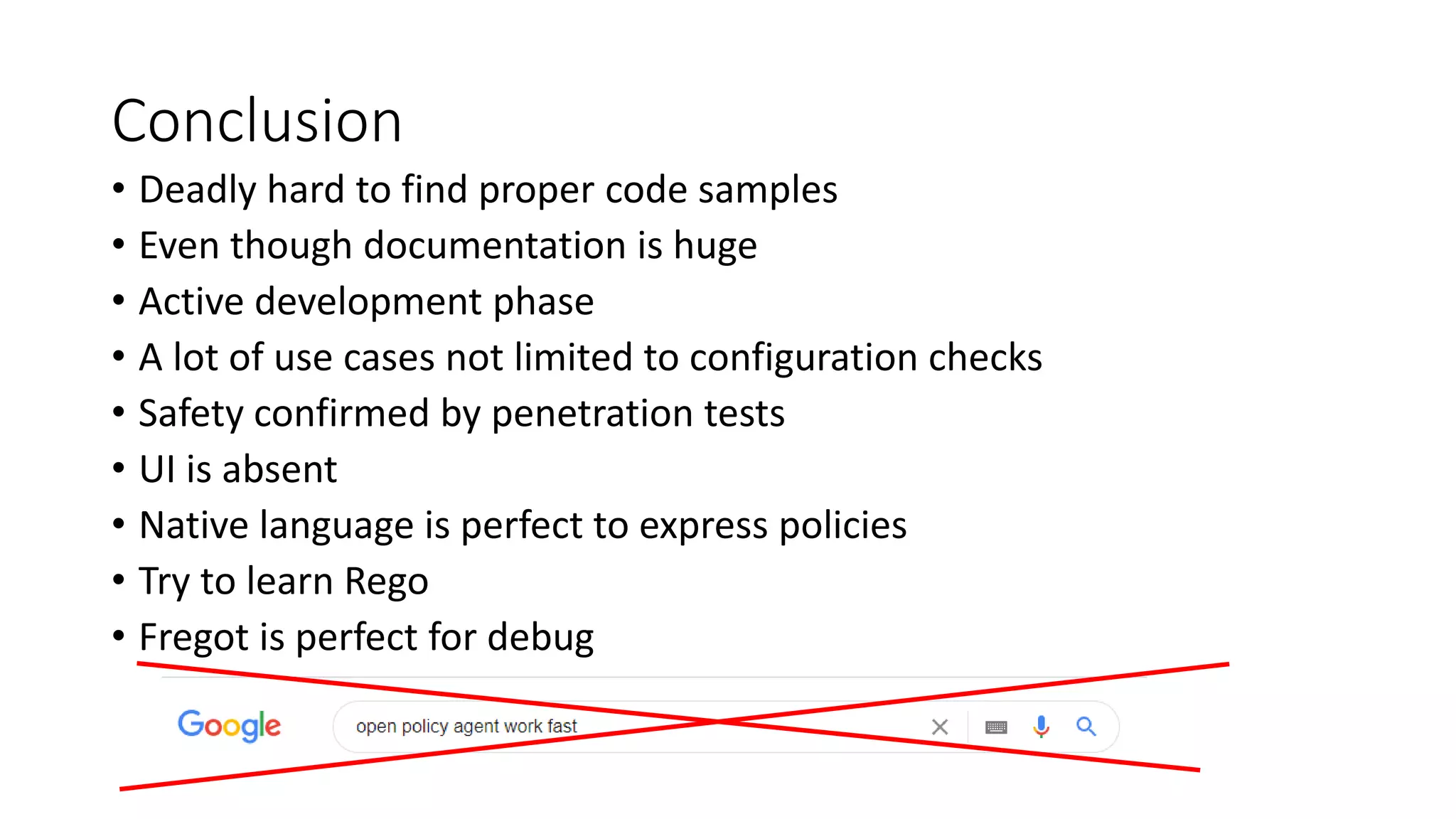
The document discusses the implementation and promotion of standards in software engineering, focusing on tools like Open Policy Agent (OPA) for policy-based control and validation processes. It outlines compliance maturity levels, key use cases of OPA, and various integrations with Kubernetes and other technologies. The document also highlights challenges, examples of policy implementation, and the importance of automated validations in ensuring software delivery efficiency.