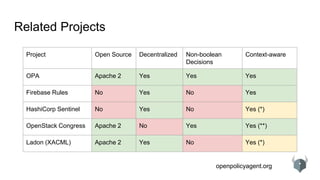
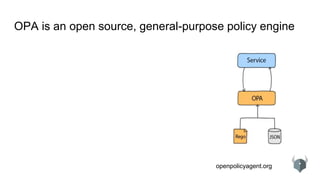
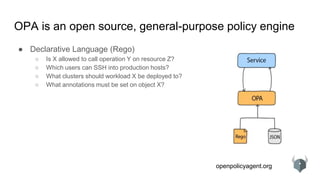
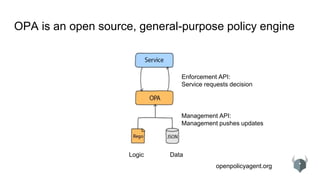
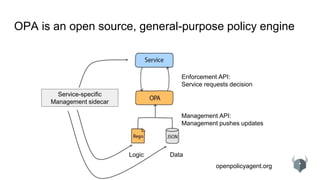
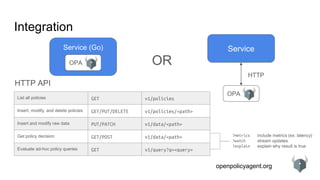
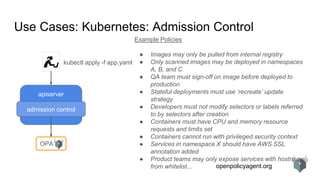
The document provides an overview of the Open Policy Agent (OPA), an open-source policy engine that allows for policy management in various domains, including Kubernetes and microservices. It describes its architecture, use cases, and the declarative language 'rego' used for defining policies, highlighting features such as zero runtime dependencies and easy integration. It also discusses various integration scenarios, management APIs, and performance requirements, alongside future use cases and lessons learned from implementing OPA.


![openpolicyagent.org
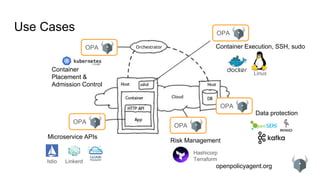
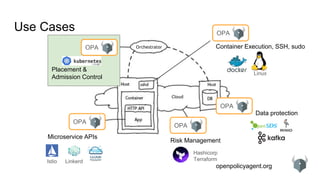
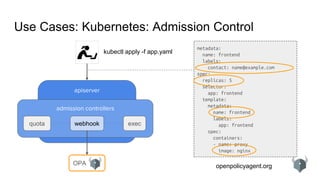
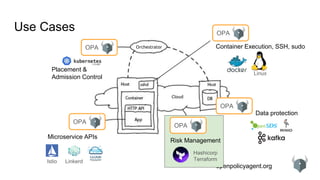
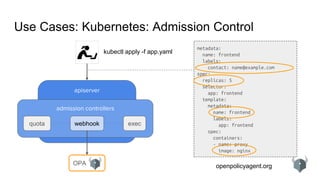
Use Cases: Kubernetes: Admission Control Policy
kind: Pod
metadata:
labels:
app: nginx
name: nginx-1493591563-bvl8q
namespace: production
spec:
containers:
- image: nginx
name: nginx
securityContext:
privileged: true
dnsPolicy: ClusterFirst
nodeName: minikube
restartPolicy: Always
status:
containerStatuses:
- name: nginx
ready: true
hostIP: 192.168.99.100
phase: Running
podIP: 172.17.0.4
# references
spec.containers[0].image
# variables and iteration
container := spec.containers[index]
# expressions
container.securityContext.privileged == true
# functions
is_privileged(container) {
container.securityContext.privileged == true
}
# rules
deny {
review.user == “bob”
review.operation == “CREATE”
review.namespace == “production”
is_privileged(spec.containers[_])
}](https://image.slidesharecdn.com/opaapiandusecases-180223184200/85/OPA-APIs-and-Use-Case-Survey-16-320.jpg)



![openpolicyagent.org
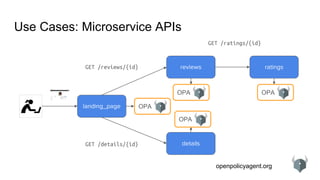
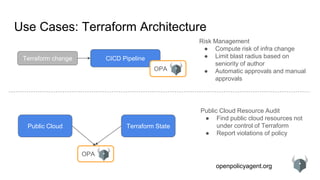
Use Cases: Microservice APIs
details
ratings
Policy Query
POST opa:8181/v1/data/example/allow
{
“input”: {
“path”: [“details”, “bob”],
“method”: “GET”,
“source”: “landing_page”,
“target”: “details”,
“query_params”: {},
“user”: “alice”,
“body”: null
}
}
Policy Decision
200 OK
{
“result”: true
}
detailsdetails
reviews
landing_page OPA
OPA
OPA
OPA](https://image.slidesharecdn.com/opaapiandusecases-180223184200/85/OPA-APIs-and-Use-Case-Survey-22-320.jpg)







![openpolicyagent.org
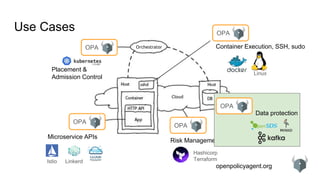
Use Cases: Kubernetes: Admission Control
kind: Pod
metadata:
labels:
app: nginx
name: nginx-1493591563-bvl8q
namespace: production
spec:
containers:
- image: nginx
name: nginx
securityContext:
privileged: true
dnsPolicy: ClusterFirst
nodeName: minikube
restartPolicy: Always
status:
containerStatuses:
- name: nginx
ready: true
hostIP: 192.168.99.100
phase: Running
podIP: 172.17.0.4
# references
spec.containers[0].image](https://image.slidesharecdn.com/opaapiandusecases-180223184200/85/OPA-APIs-and-Use-Case-Survey-34-320.jpg)
![openpolicyagent.org
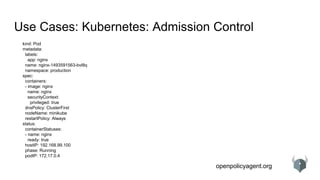
Use Cases: Kubernetes: Admission Control
kind: Pod
metadata:
labels:
app: nginx
name: nginx-1493591563-bvl8q
namespace: production
spec:
containers:
- image: nginx
name: nginx
securityContext:
privileged: true
dnsPolicy: ClusterFirst
nodeName: minikube
restartPolicy: Always
status:
containerStatuses:
- name: nginx
ready: true
hostIP: 192.168.99.100
phase: Running
podIP: 172.17.0.4
# references
spec.containers[0].image
# variables and iteration
container = spec.containers[index]](https://image.slidesharecdn.com/opaapiandusecases-180223184200/85/OPA-APIs-and-Use-Case-Survey-35-320.jpg)
![openpolicyagent.org
Use Cases: Kubernetes: Admission Control
kind: Pod
metadata:
labels:
app: nginx
name: nginx-1493591563-bvl8q
namespace: production
spec:
containers:
- image: nginx
name: nginx
securityContext:
privileged: true
dnsPolicy: ClusterFirst
nodeName: minikube
restartPolicy: Always
status:
containerStatuses:
- name: nginx
ready: true
hostIP: 192.168.99.100
phase: Running
podIP: 172.17.0.4
# references
spec.containers[0].image
# variables and iteration
container = spec.containers[index]
# expressions
container.securityContext.privileged = true](https://image.slidesharecdn.com/opaapiandusecases-180223184200/85/OPA-APIs-and-Use-Case-Survey-36-320.jpg)
![openpolicyagent.org
Use Cases: Kubernetes: Admission Control
kind: Pod
metadata:
labels:
app: nginx
name: nginx-1493591563-bvl8q
namespace: production
spec:
containers:
- image: nginx
name: nginx
securityContext:
privileged: true
dnsPolicy: ClusterFirst
nodeName: minikube
restartPolicy: Always
status:
containerStatuses:
- name: nginx
ready: true
hostIP: 192.168.99.100
phase: Running
podIP: 172.17.0.4
# references
spec.containers[0].image
# variables and iteration
container = spec.containers[index]
# expressions
container.securityContext.privileged = true
# functions
is_privileged(container) {
container.securityContext.privileged = true
}](https://image.slidesharecdn.com/opaapiandusecases-180223184200/85/OPA-APIs-and-Use-Case-Survey-37-320.jpg)
![openpolicyagent.org
Use Cases: Kubernetes: Admission Control
kind: Pod
metadata:
labels:
app: nginx
name: nginx-1493591563-bvl8q
namespace: production
spec:
containers:
- image: nginx
name: nginx
securityContext:
privileged: true
dnsPolicy: ClusterFirst
nodeName: minikube
restartPolicy: Always
status:
containerStatuses:
- name: nginx
ready: true
hostIP: 192.168.99.100
phase: Running
podIP: 172.17.0.4
# references
spec.containers[0].image
# variables and iteration
container = spec.containers[index]
# expressions
container.securityContext.privileged = true
# functions
is_privileged(container) {
container.securityContext.privileged = true
}
# rules
deny {
review.user = “bob”
review.operation = “CREATE”
review.namespace = “production”
is_privileged(spec.containers[_])
}](https://image.slidesharecdn.com/opaapiandusecases-180223184200/85/OPA-APIs-and-Use-Case-Survey-38-320.jpg)
![openpolicyagent.org
Performance: Microservice APIs
Benchmarks run on every release, e.g. https://gist.github.com/tsandall/97729bef8ee804a75b9e20e81508782d#file-_results_
+----------------+--------------------+--------------+------------+--------------+-----------+-----------------+
| Percentile (%) | Serialization (µs) | Request (µs) | Parse (µs) | Compile (µs) | Eval (µs) | Processing (µs) |
+----------------+--------------------+--------------+------------+--------------+-----------+-----------------+
| 50 | 2 | 358 | 11 | 43 | 180 | 14 |
| 75 | 3 | 389 | 12 | 45 | 186 | 16 |
| 90 | 3 | 437 | 13 | 49 | 200 | 19 |
| 95 | 4 | 495 | 15 | 56 | 234 | 23 |
| 99 | 8 | 1886 | 29 | 87 | 736 | 35 |
| 99.9 | 23 | 2583 | 221 | 205 | 2215 | 69 |
| 99.99 | 72 | 3357 | 1920 | 264 | 2617 | 161 |
+----------------+--------------------+--------------+------------+--------------+-----------+-----------------+
HTTP Latency
allow {
input.method = "GET"
input.path = ["finance", "salary", account_id]
input.user_id = account_id
}
1000 rules with 10 hits
Note: v0.6 will reduce eval
latency by 2-orders of
magnitude](https://image.slidesharecdn.com/opaapiandusecases-180223184200/85/OPA-APIs-and-Use-Case-Survey-42-320.jpg)
![openpolicyagent.org
Integration: Python
def check_request(request):
body = { # prepare body for OPA query by...
"input": { # supplying input data containing...
"auth_user": request.token.username, # authenticated username/identity (e.g., bob)
"path": request.path.split("/"), # HTTP URL path (e.g., /widgets/12345)
"method": request.method, # HTTP method (e.g., POST, GET, DELETE, etc.)
}
}
# query authorization policy in OPA for ‘allow’ decision
response = requests.post(“http://opa:8181/v1/data/acmecorp/api/authz/allow”, data=body)
# check OPA response for ‘allow’ decision
if not response.json()[“result”][“allow”]:
raise Exception(“request rejected by administrative policy”)](https://image.slidesharecdn.com/opaapiandusecases-180223184200/85/OPA-APIs-and-Use-Case-Survey-43-320.jpg)