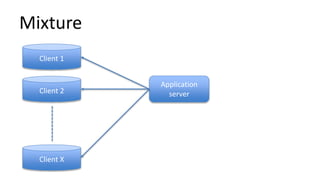
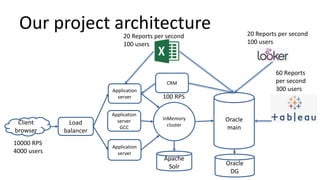
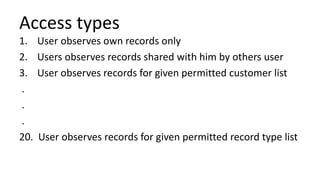
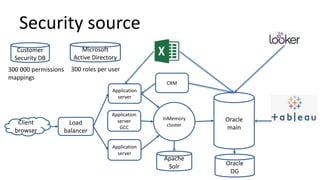
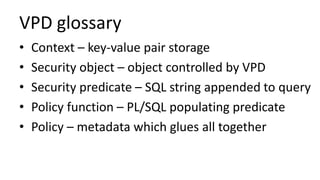
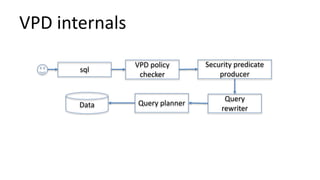
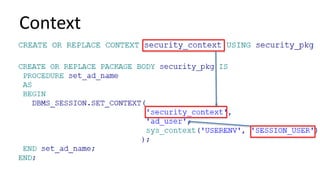
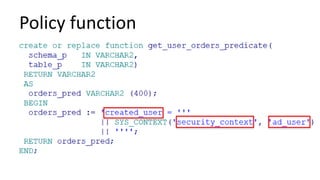
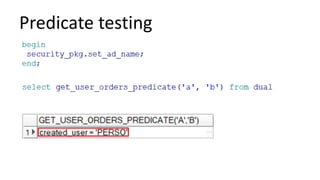
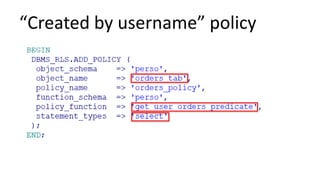
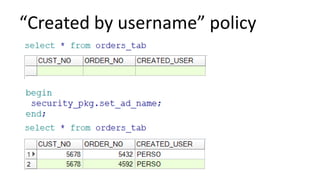
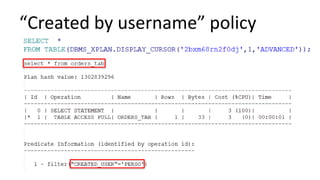
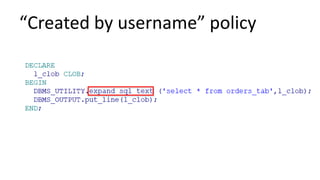
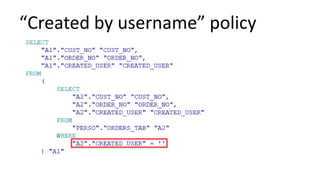
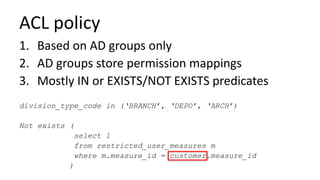
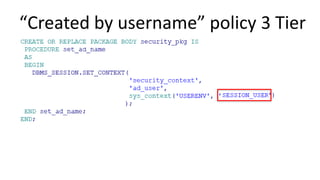
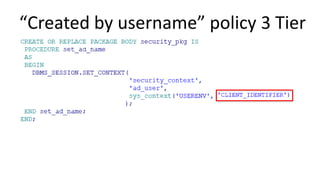
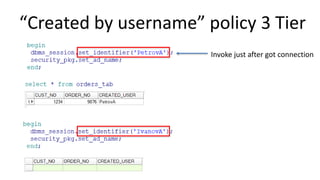
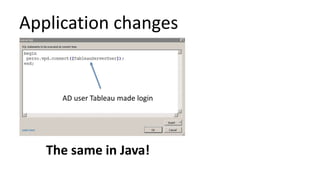
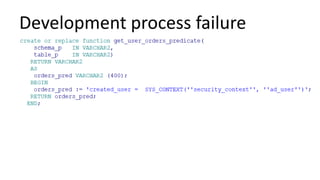
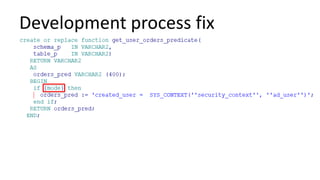
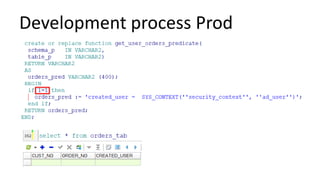
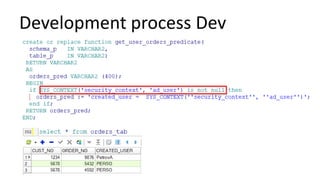
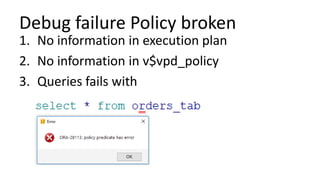
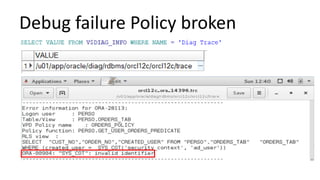
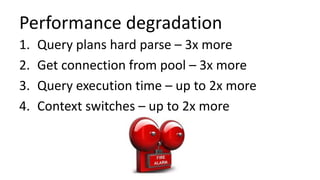
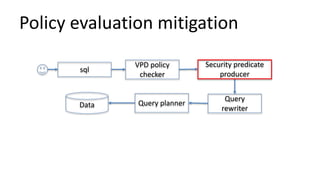
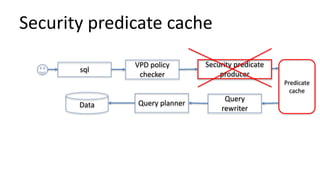
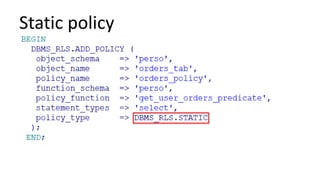
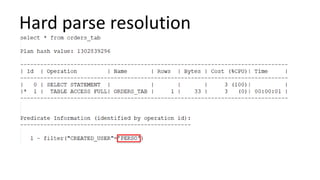
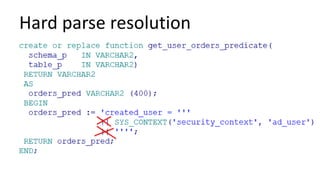
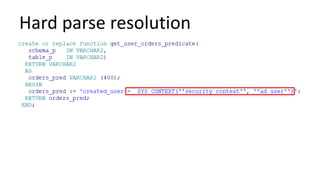
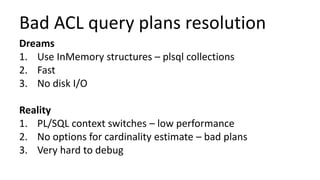
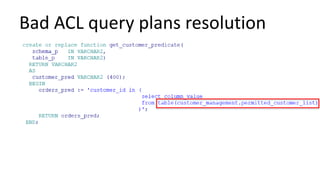
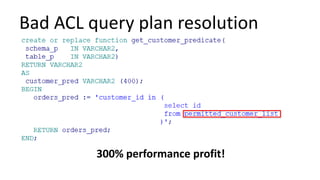
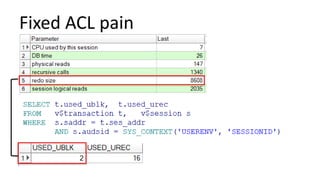
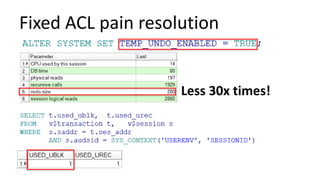
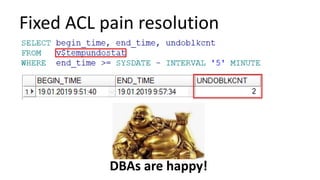
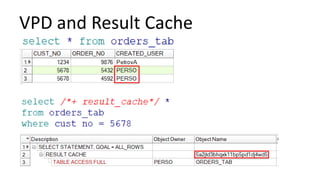
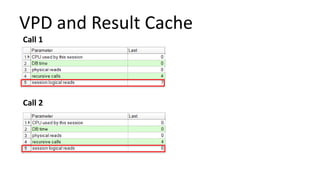
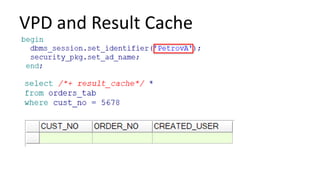
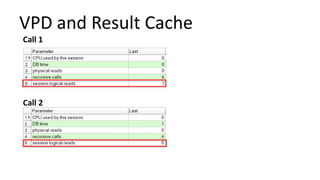
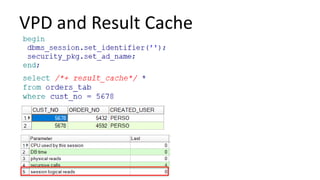
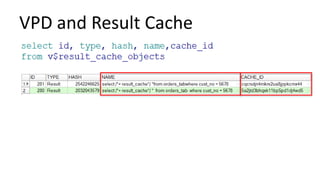
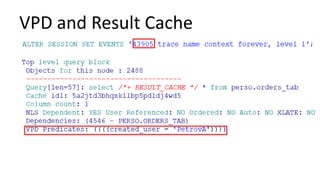
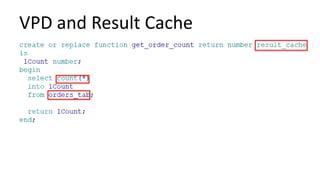
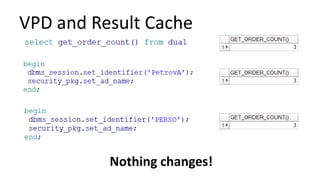
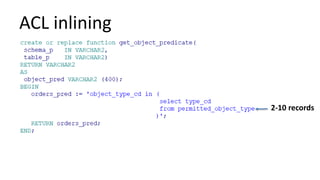
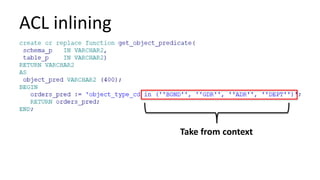
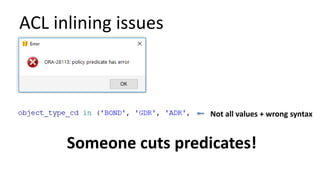
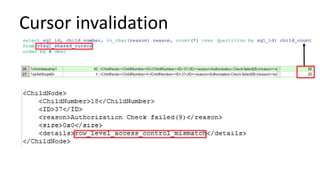
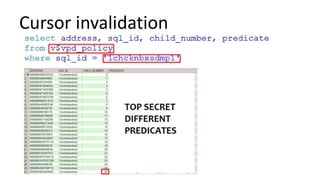
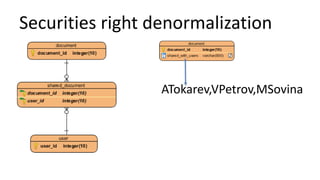
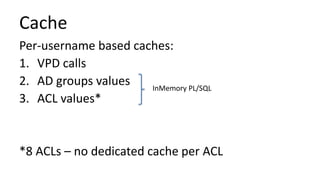
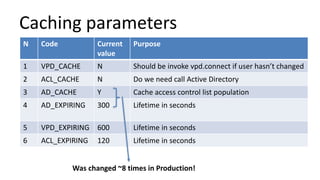
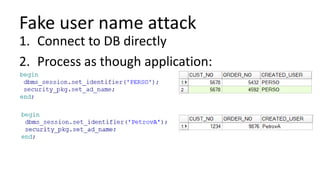
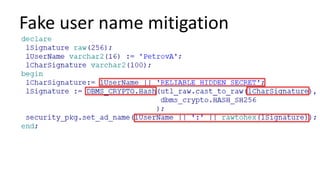
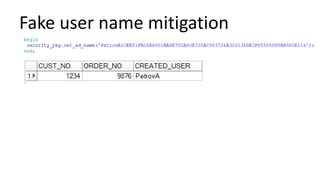
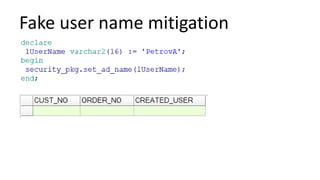
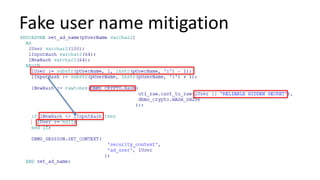
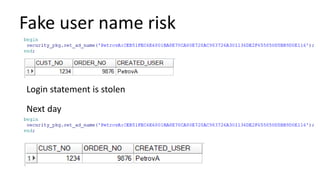
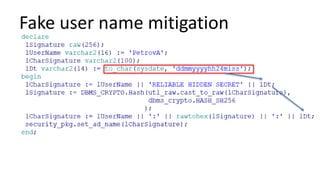
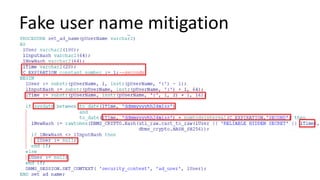
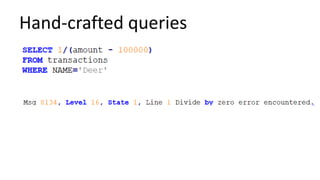
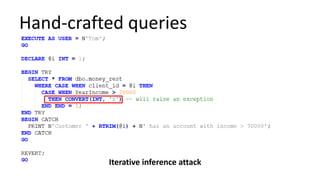
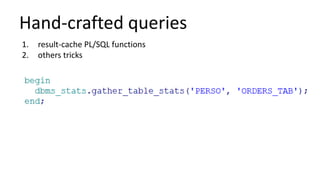
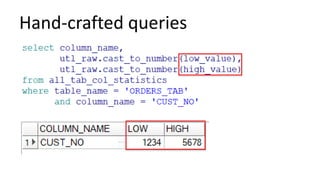
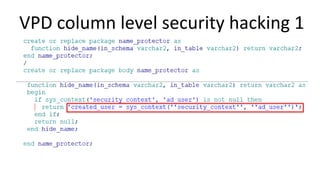
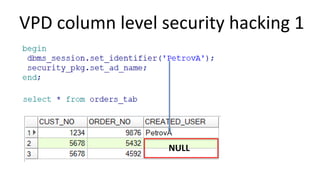
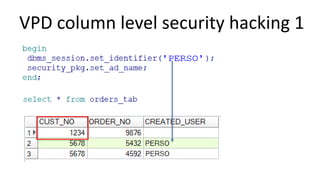
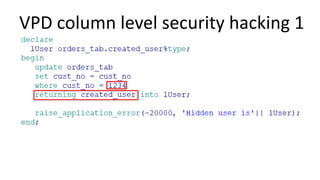
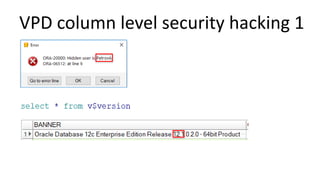
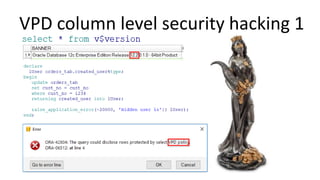
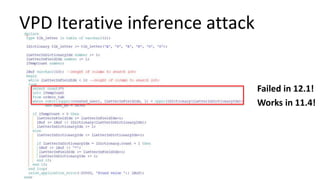
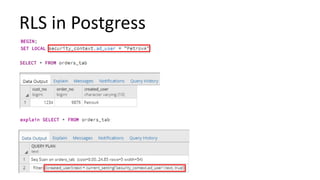
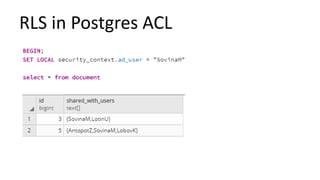
The document discusses the implementation and challenges of row-level security (RLS) in a high-load project, highlighting security myths, performance issues, and various architectural approaches. It outlines the requirements necessary for an effective RLS system, such as minimal application changes and centralized management, while also detailing lessons learned and strategies for overcoming development and performance obstacles. Finally, it emphasizes the importance of planning, data-driven approaches, and keeping security proactive to prevent potential hacks.