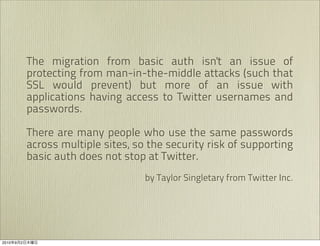
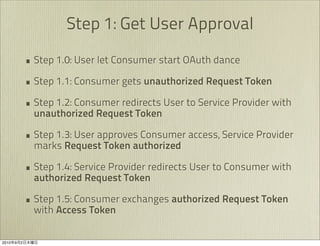
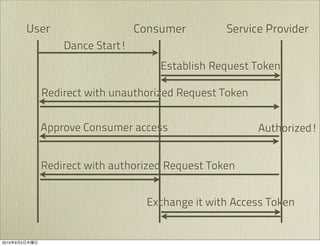
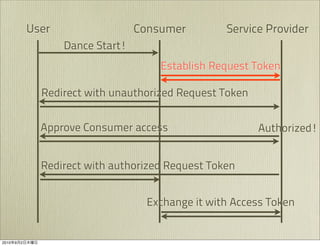
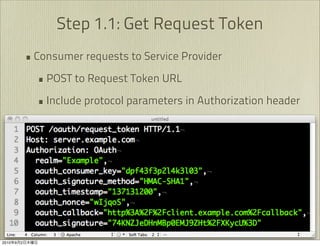
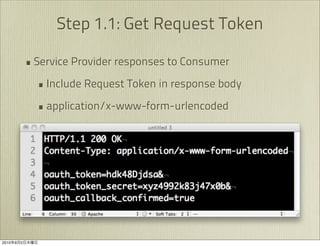
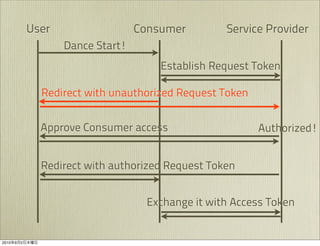
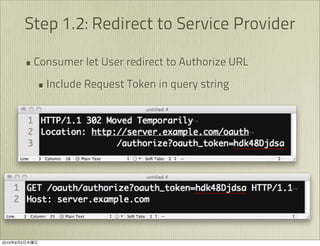
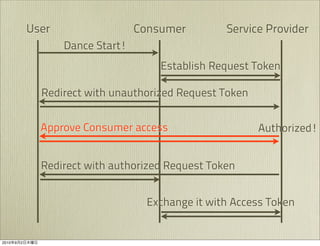
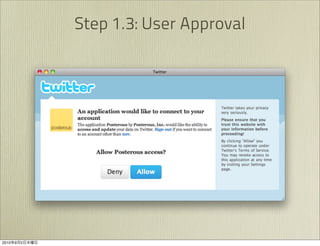
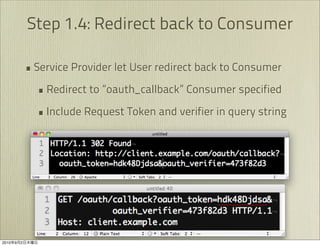
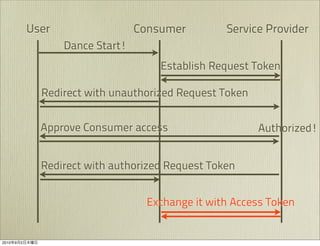
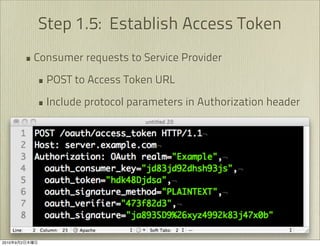
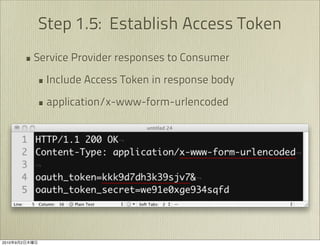
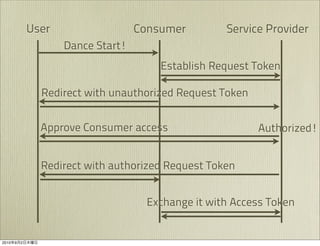
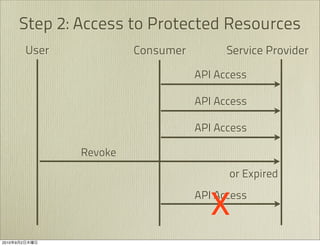
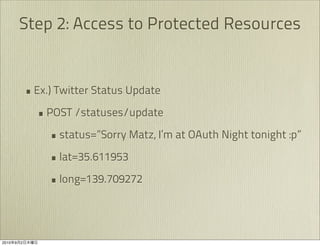
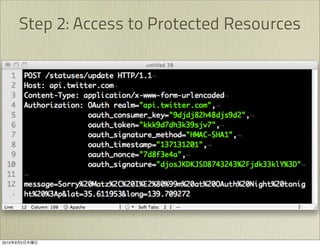
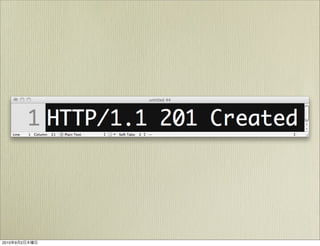
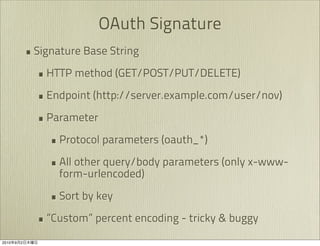
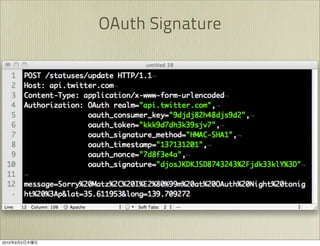
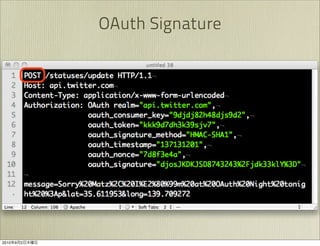
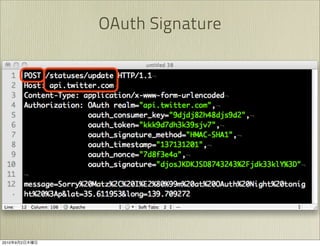
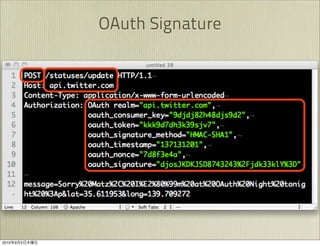
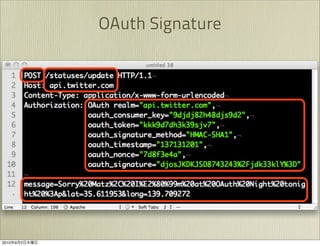
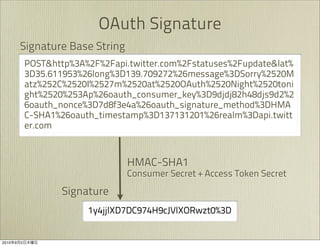
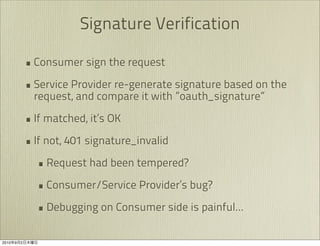
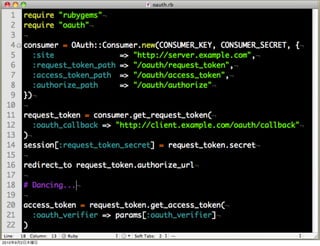
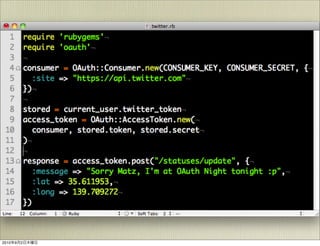
The document discusses OAuth 1.0, an open standard for authorization in API access. It describes the key components of OAuth 1.0 including the three roles of user, consumer, and service provider. It outlines the three step authorization process of obtaining a request token, user authorization, and exchanging for an access token. The document provides details on OAuth signatures and parameters used to securely authorize API access on behalf of the user.