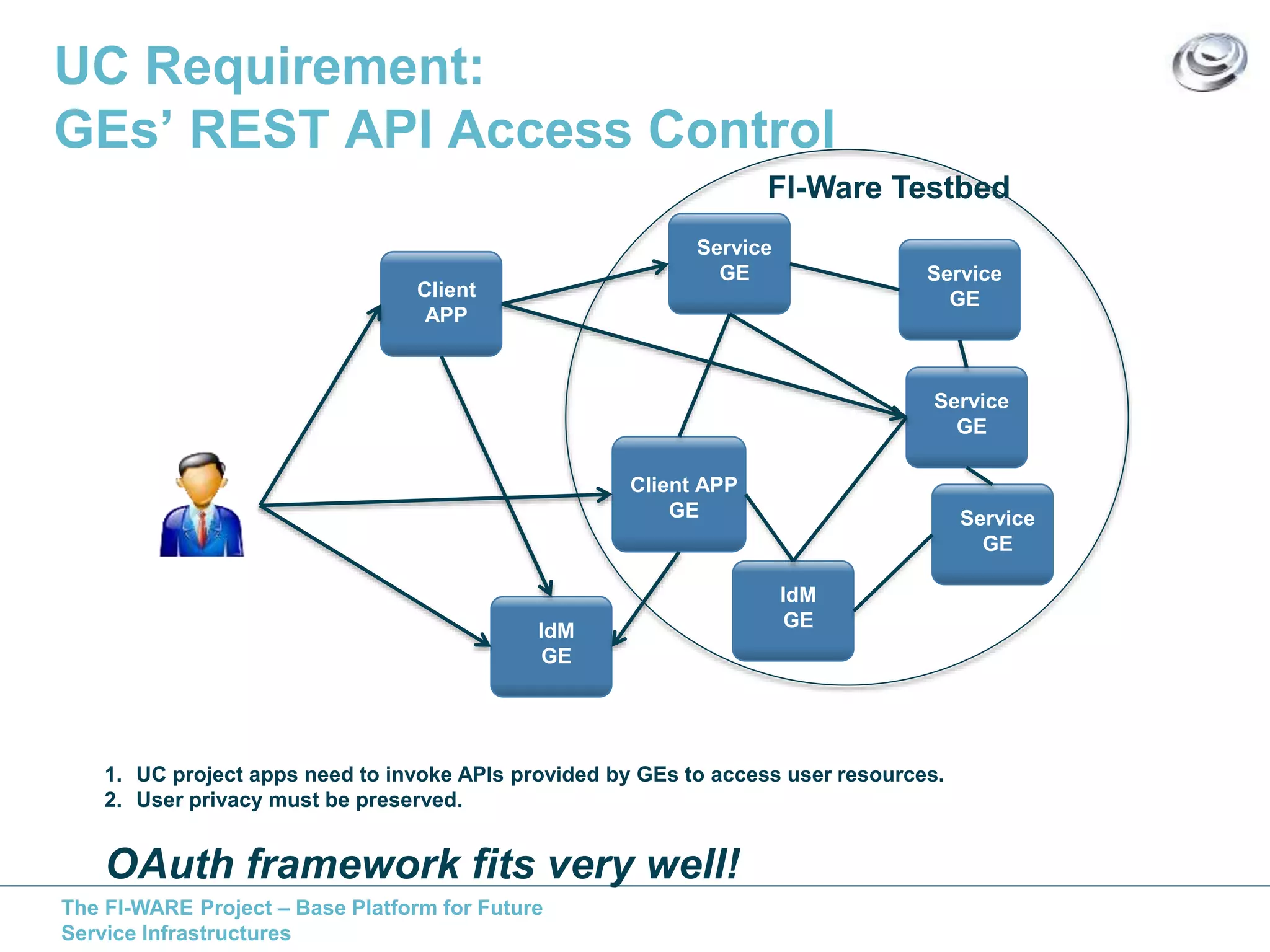
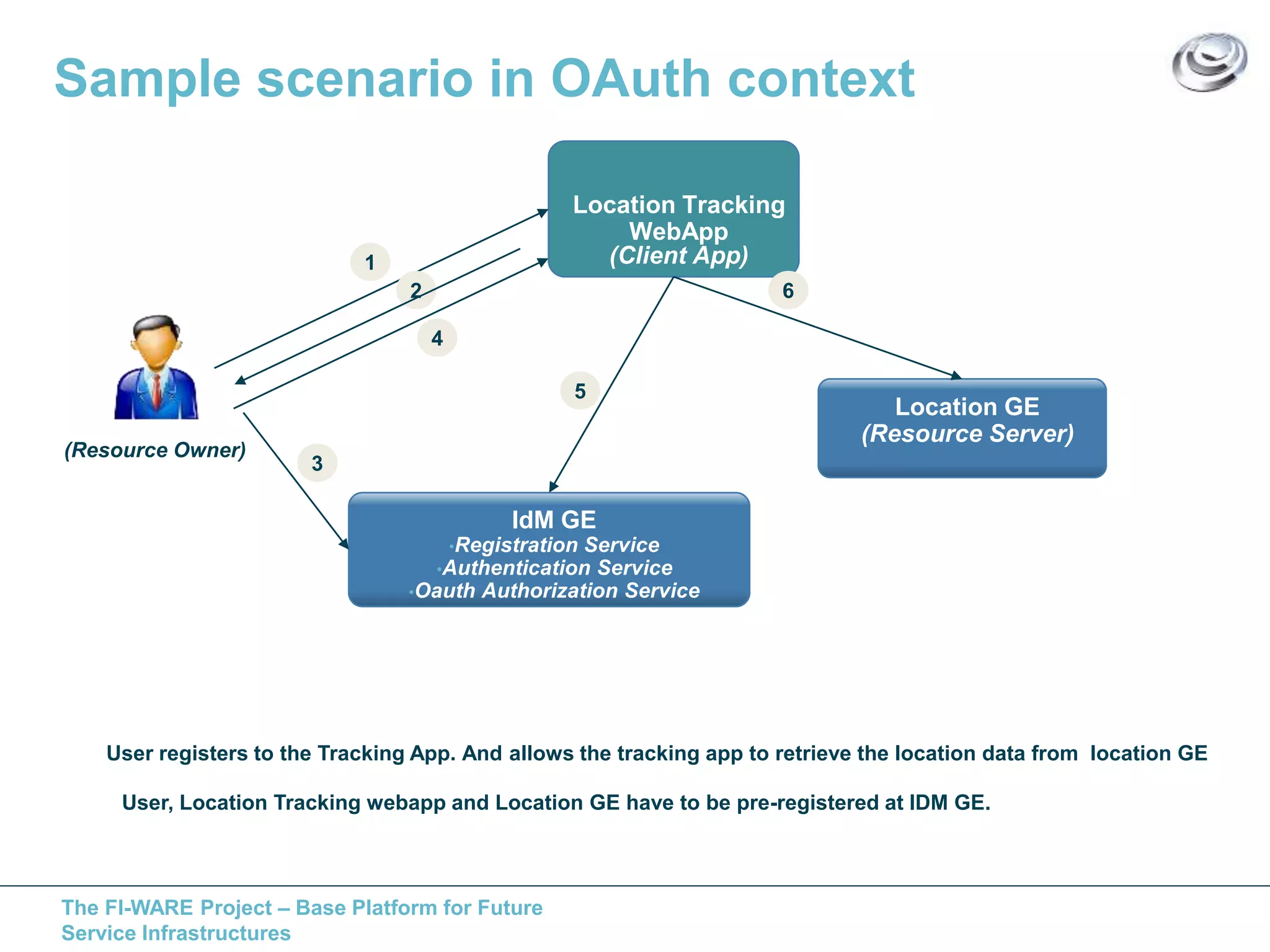
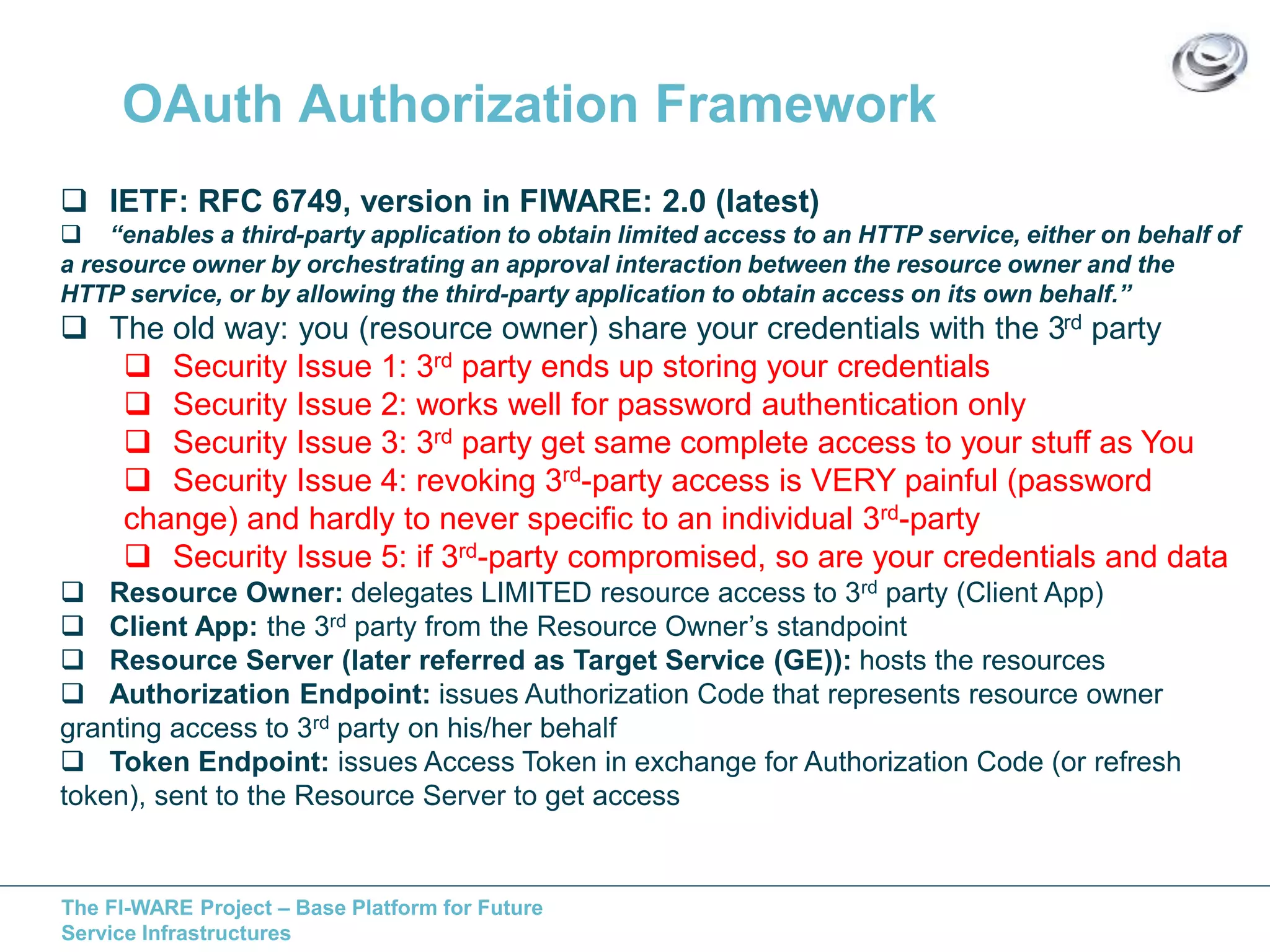
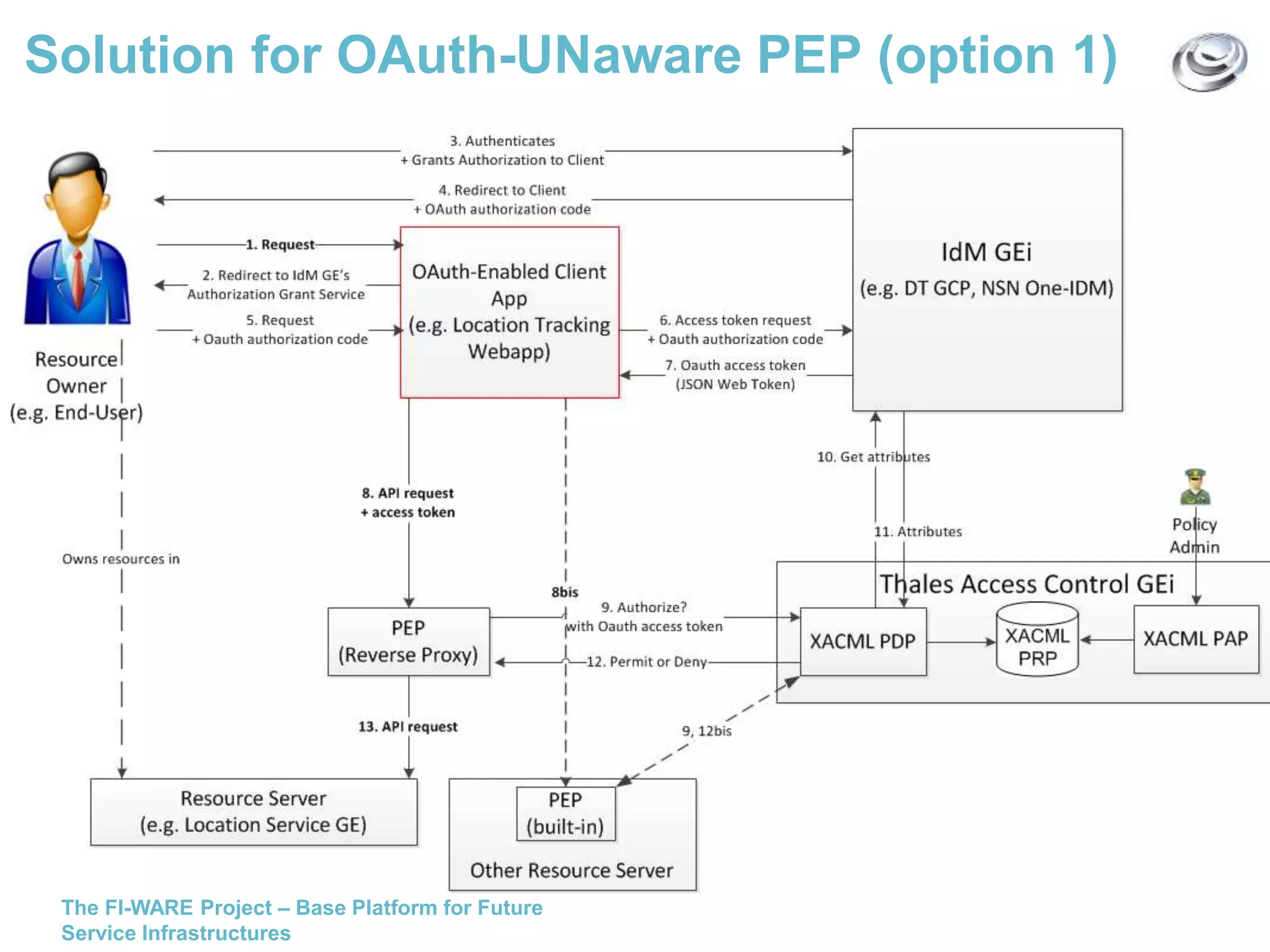
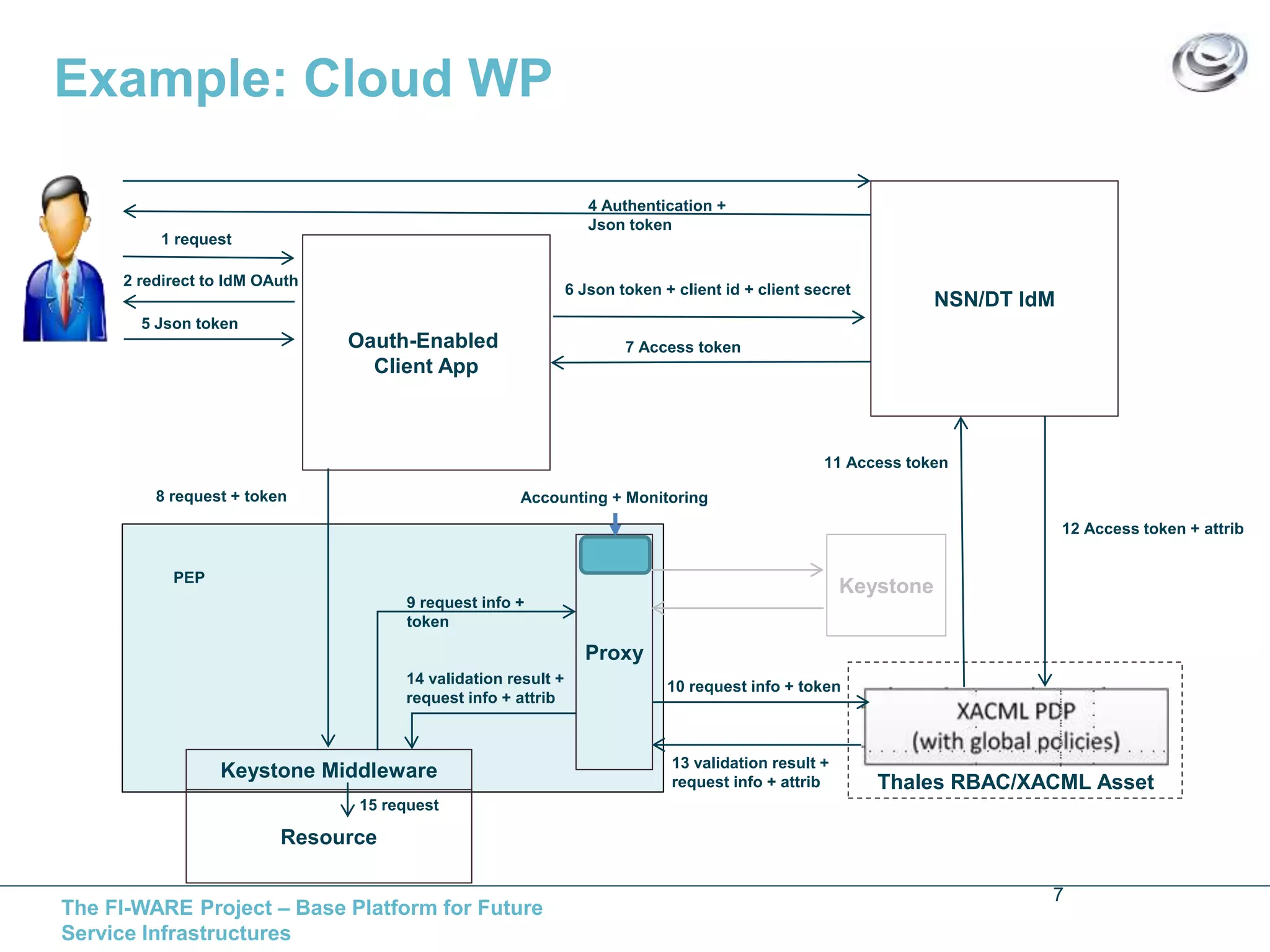
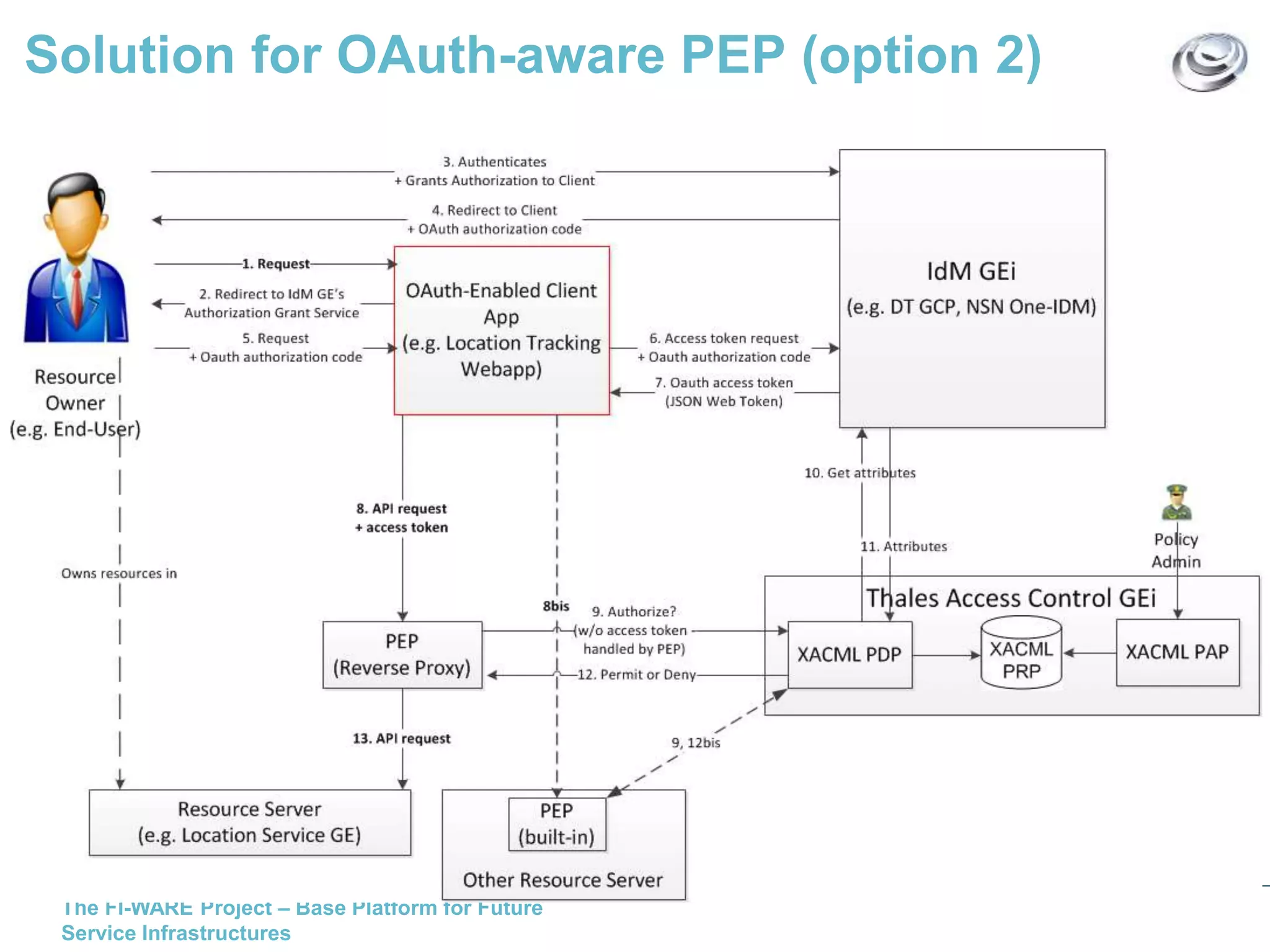
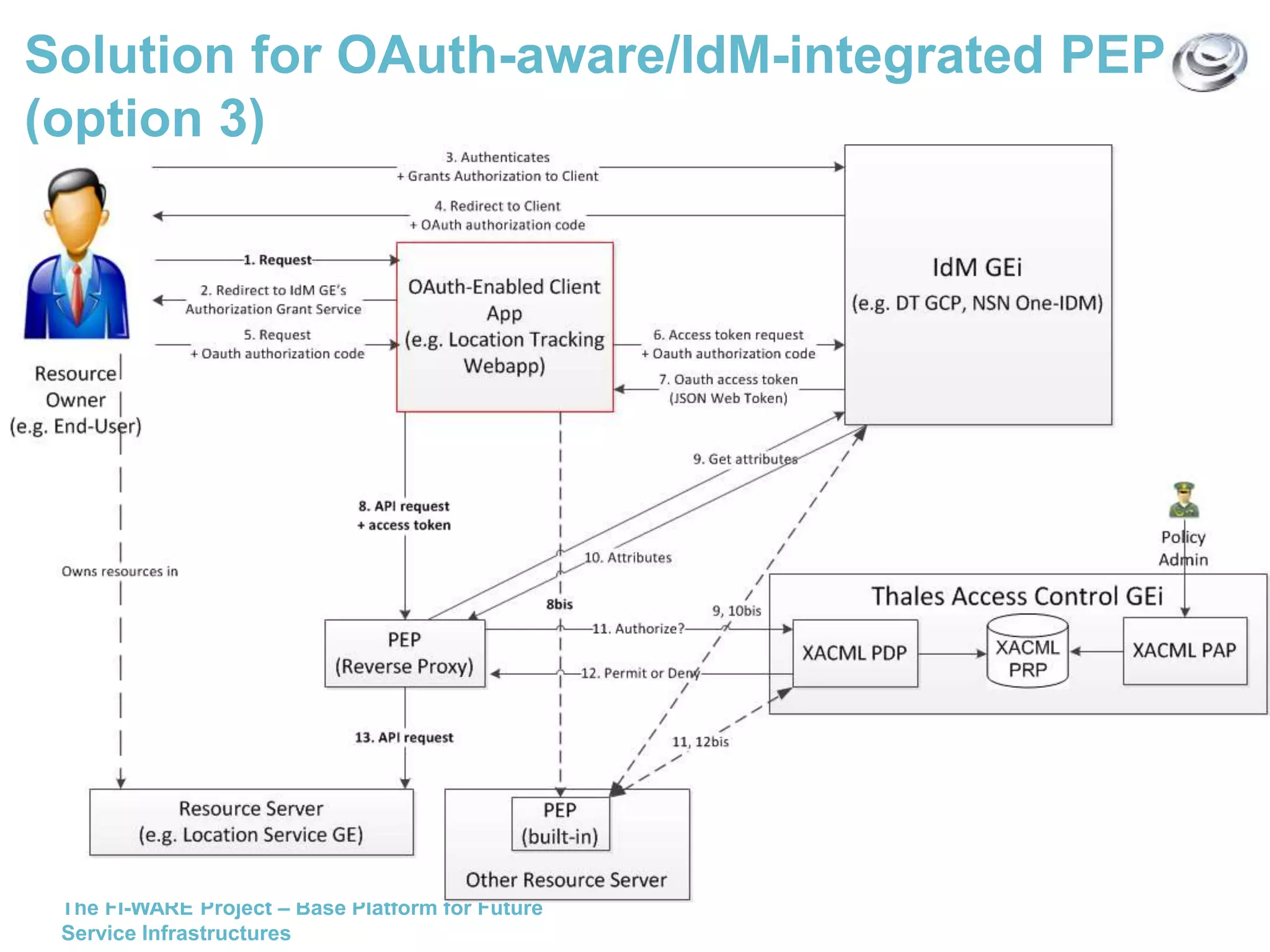
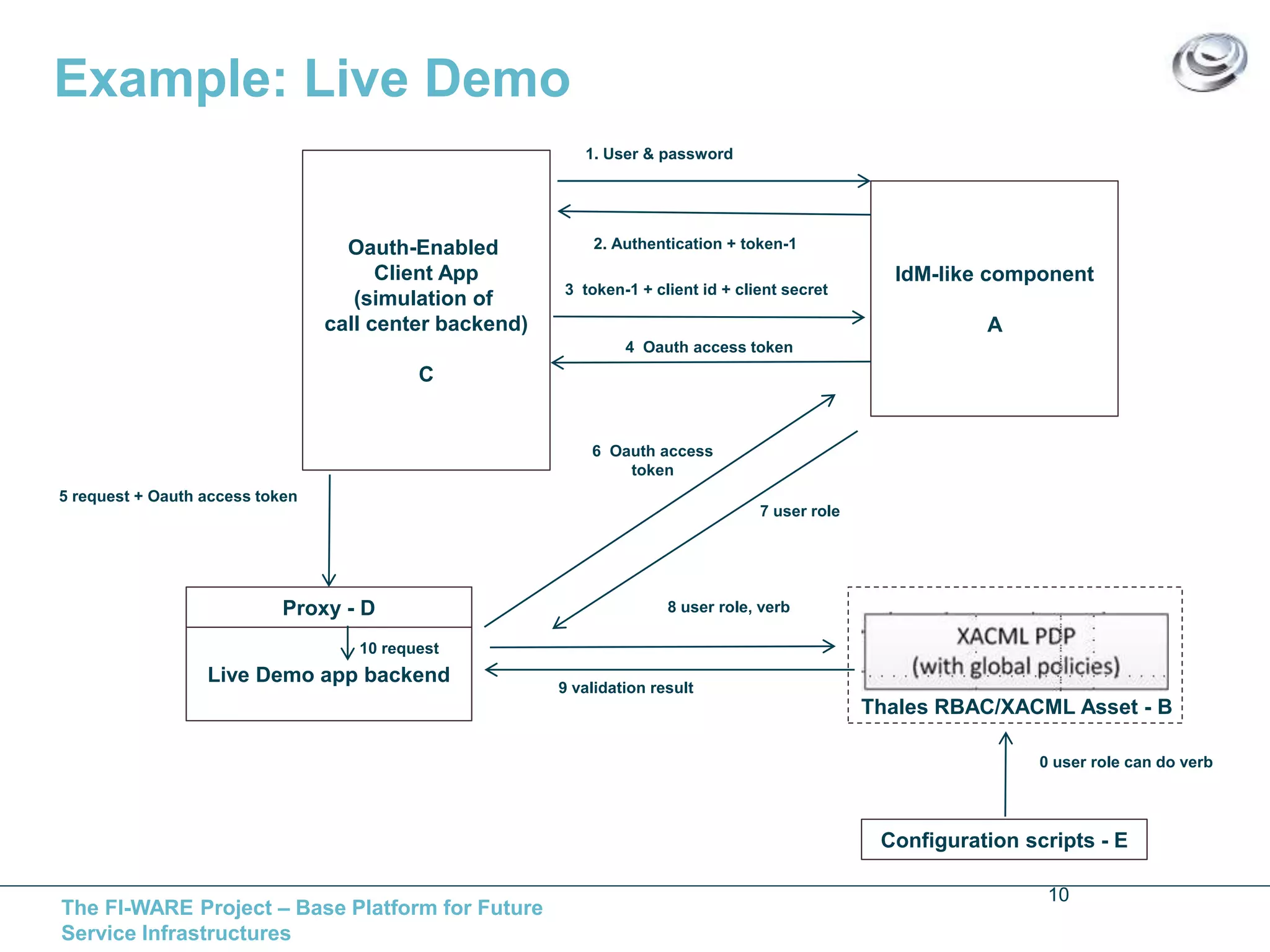
This document discusses API access control for FIWARE GEs using OAuth and XACML. It describes how the IdM GE can provide OAuth authorization services while the Access Control GE can enforce access control policies set in XACML. The Access Control GE includes a Policy Decision Point and can validate OAuth access tokens to control access to protected resources according to policies. Several solutions are provided for OAuth-aware and unaware policy enforcement points.