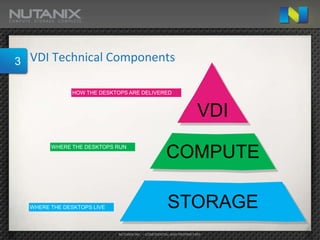
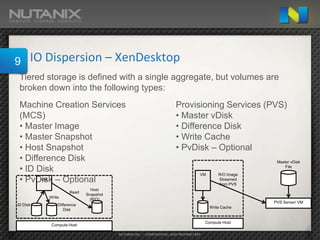
This document summarizes an interactive workshop on virtual desktop infrastructure (VDI) design. It discusses technical components of VDI like where desktops are delivered from and run, as well as storage considerations. Key topics covered include IO dispersion across different types of storage, squeezing virtual machines onto hardware, and balancing persistent versus non-persistent desktops. The document also outlines several important considerations for a successful VDI implementation like whether to use a traditional or converged infrastructure, how to pilot VDI, scaling out cost effectively, and where to focus efforts.