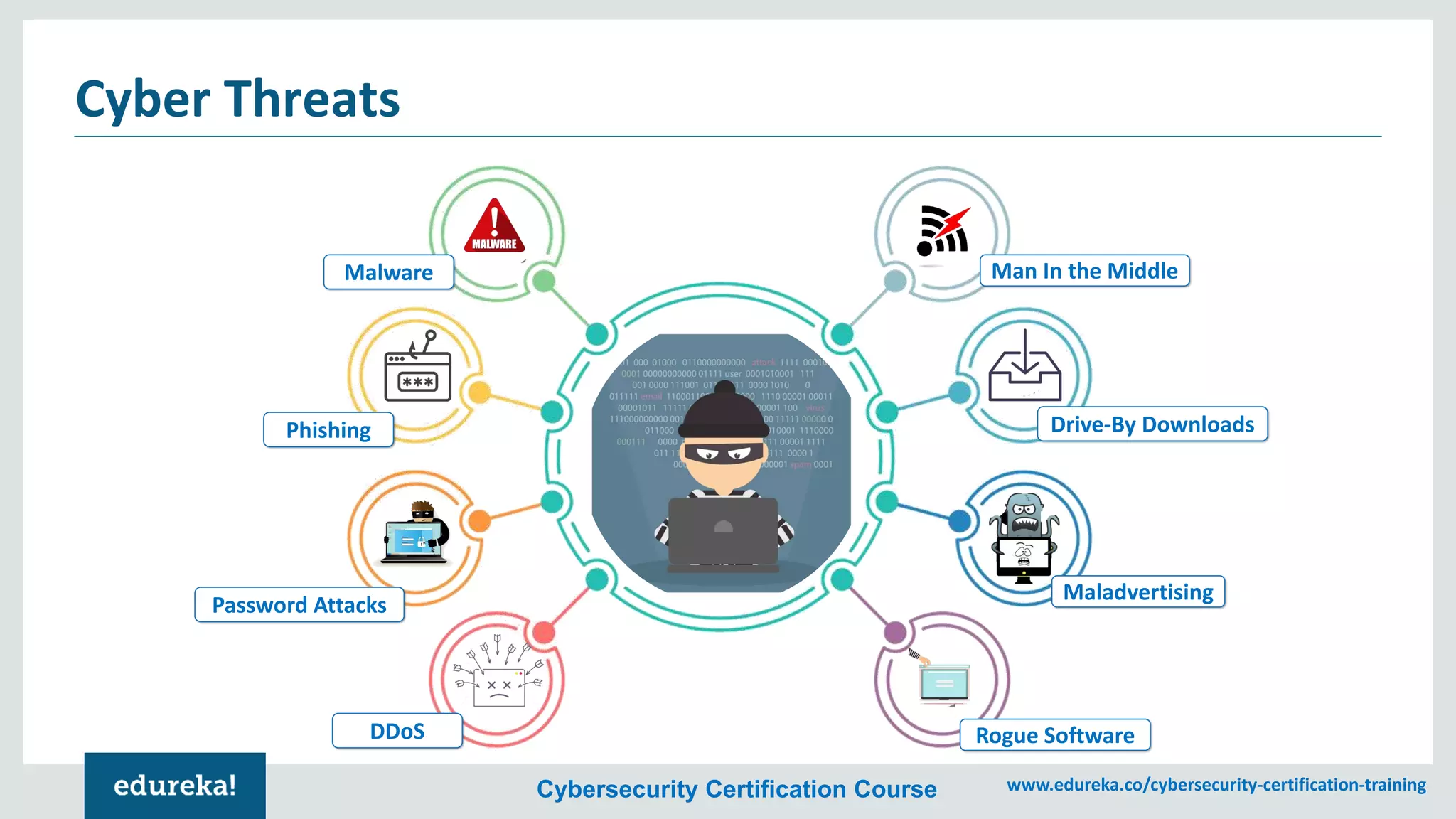
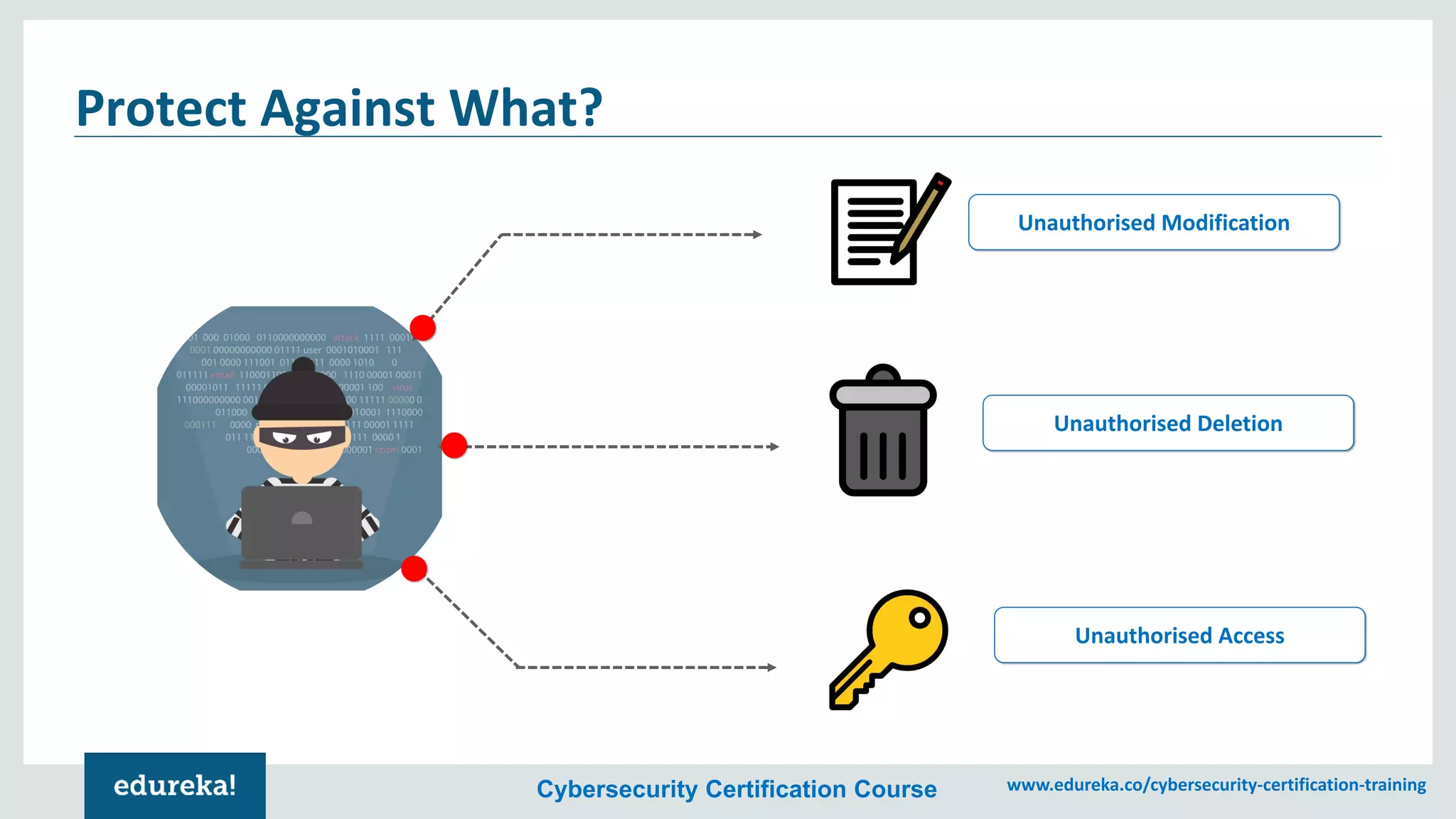
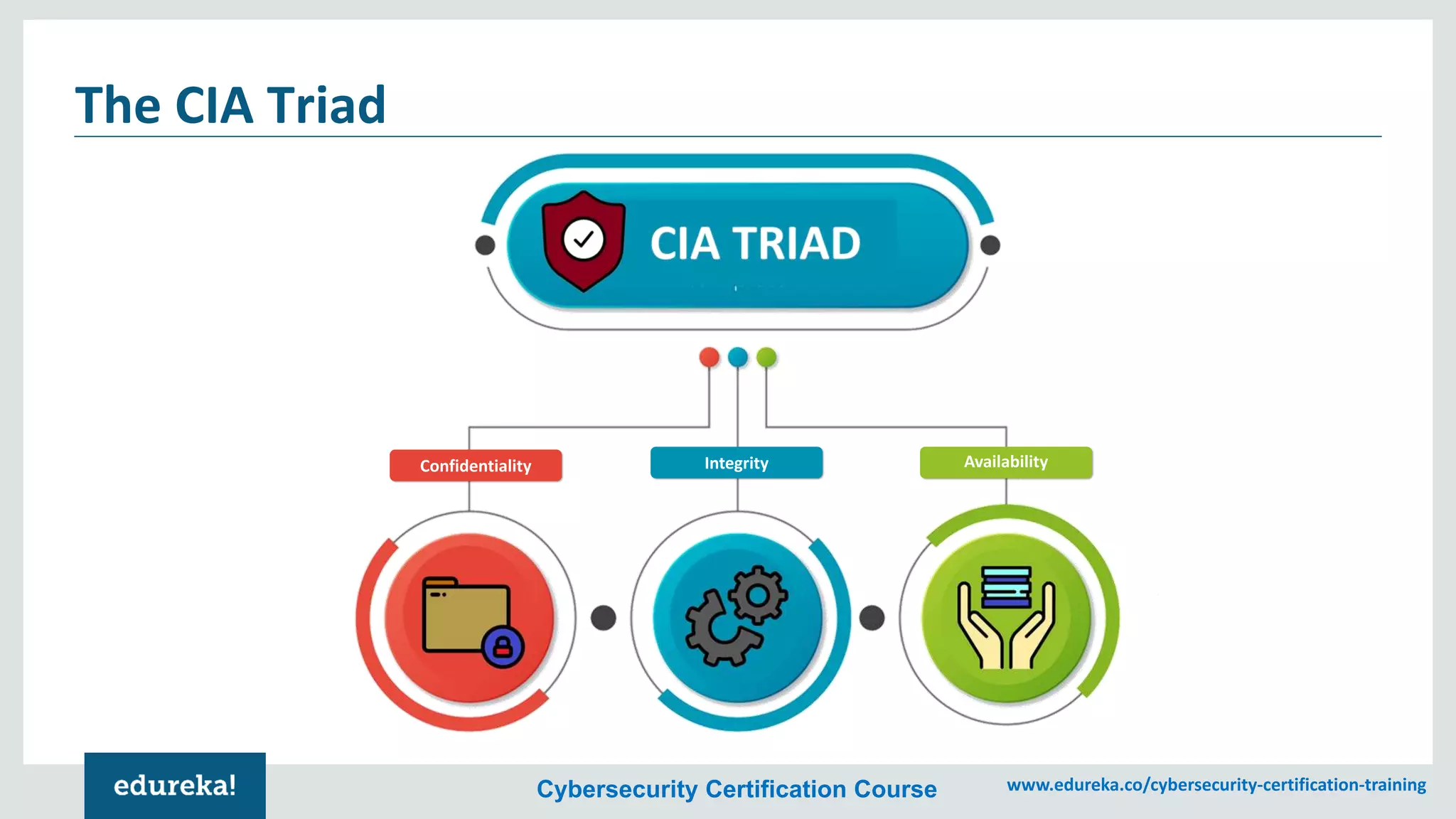
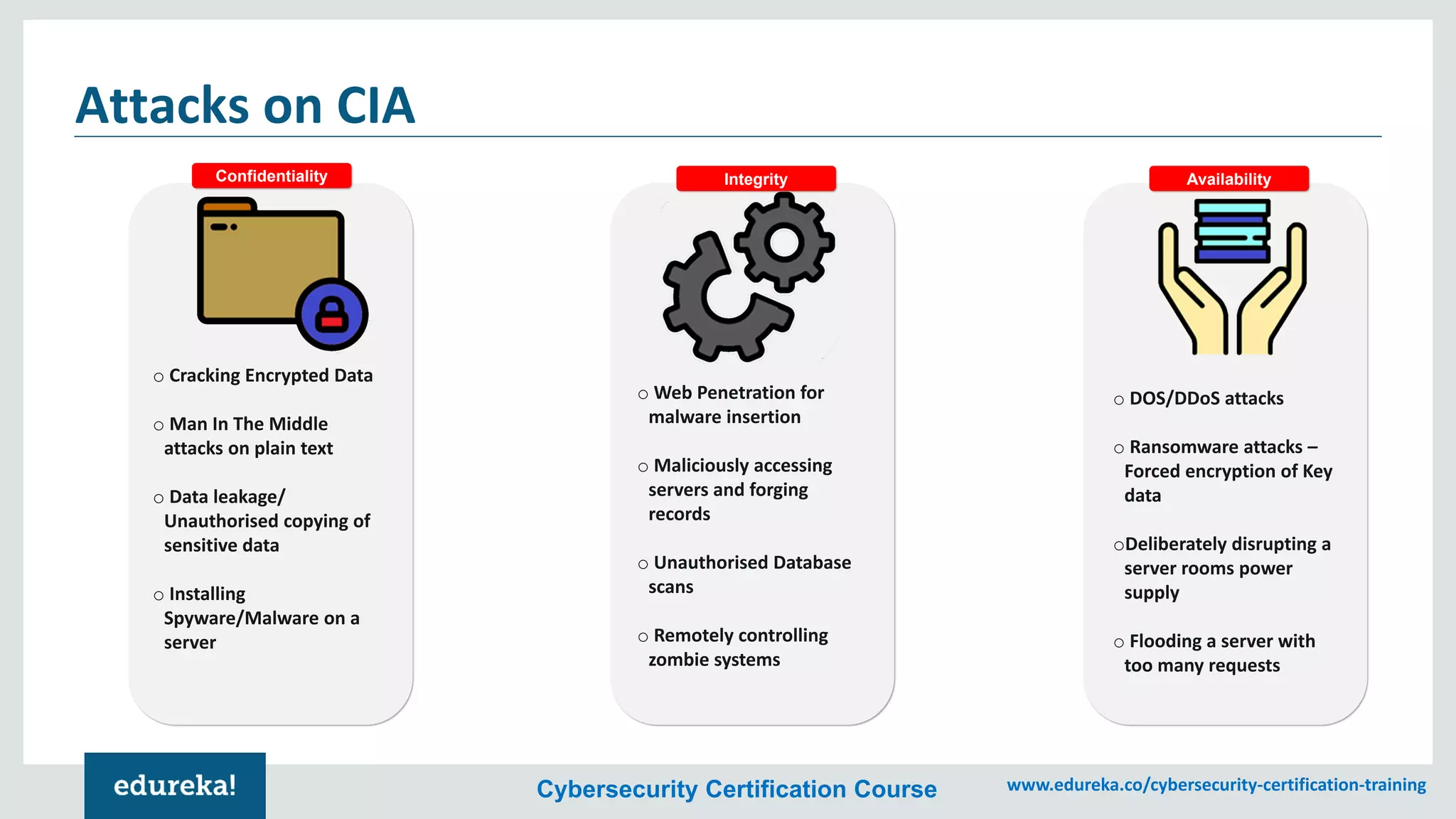
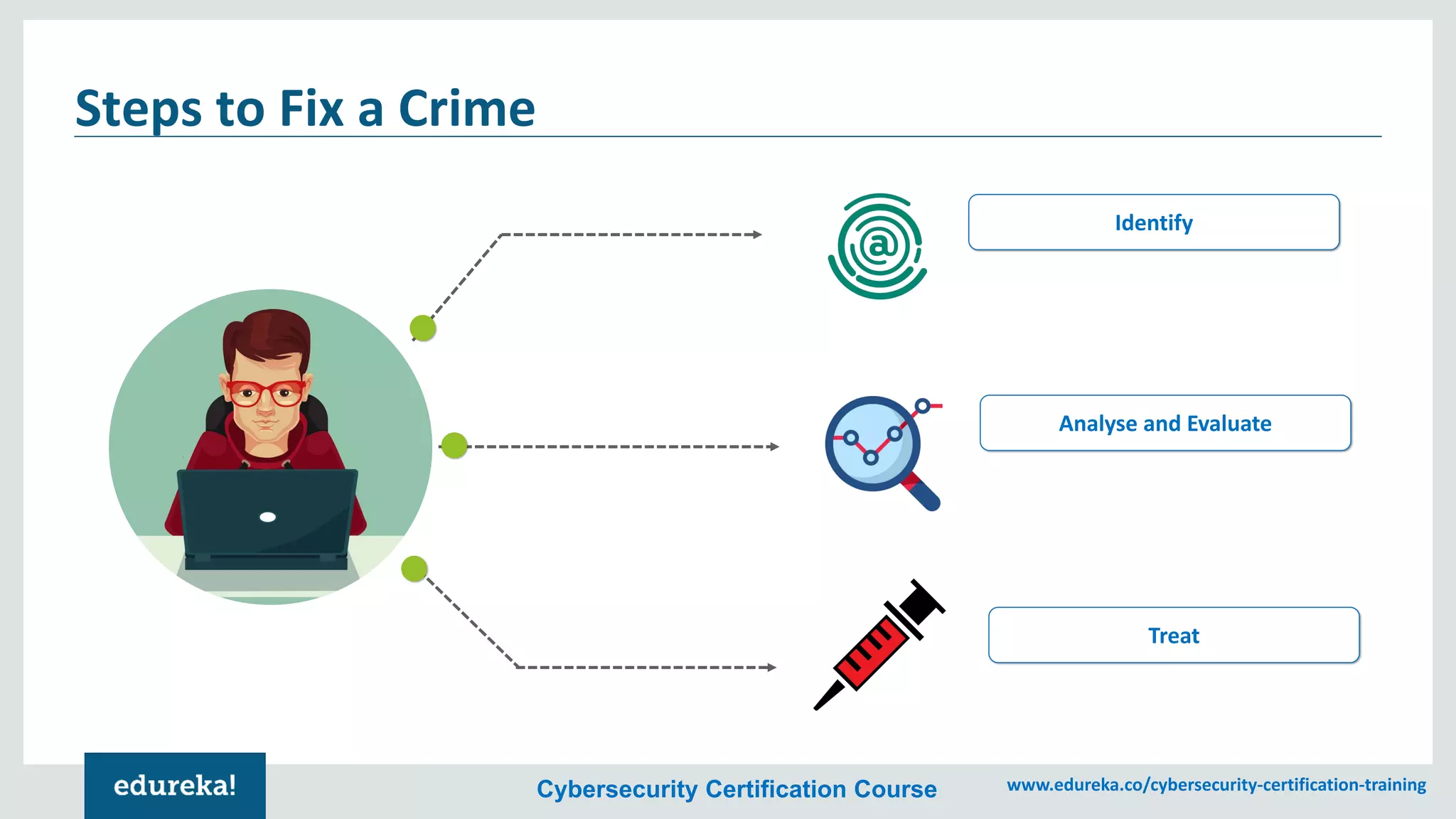
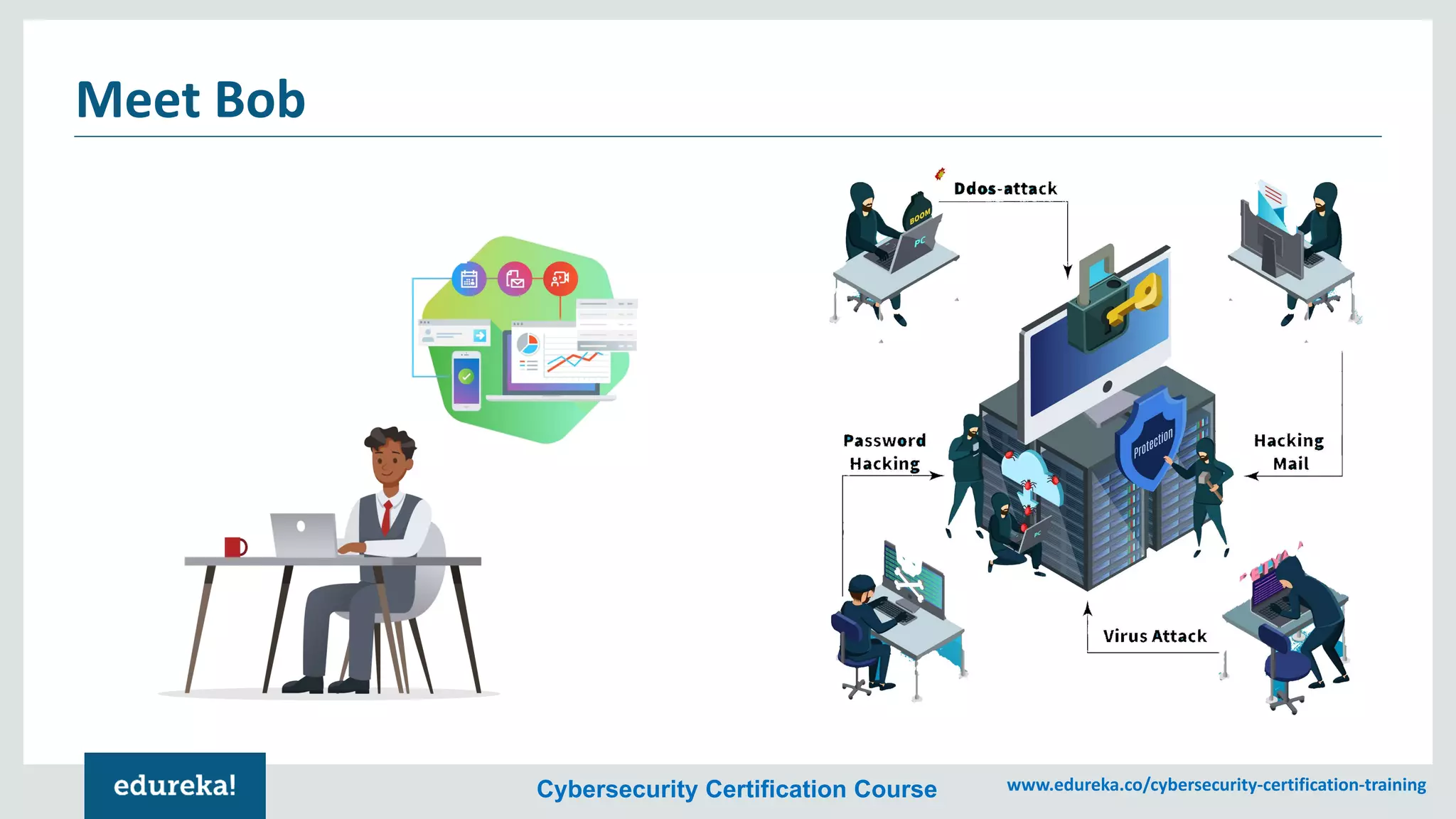
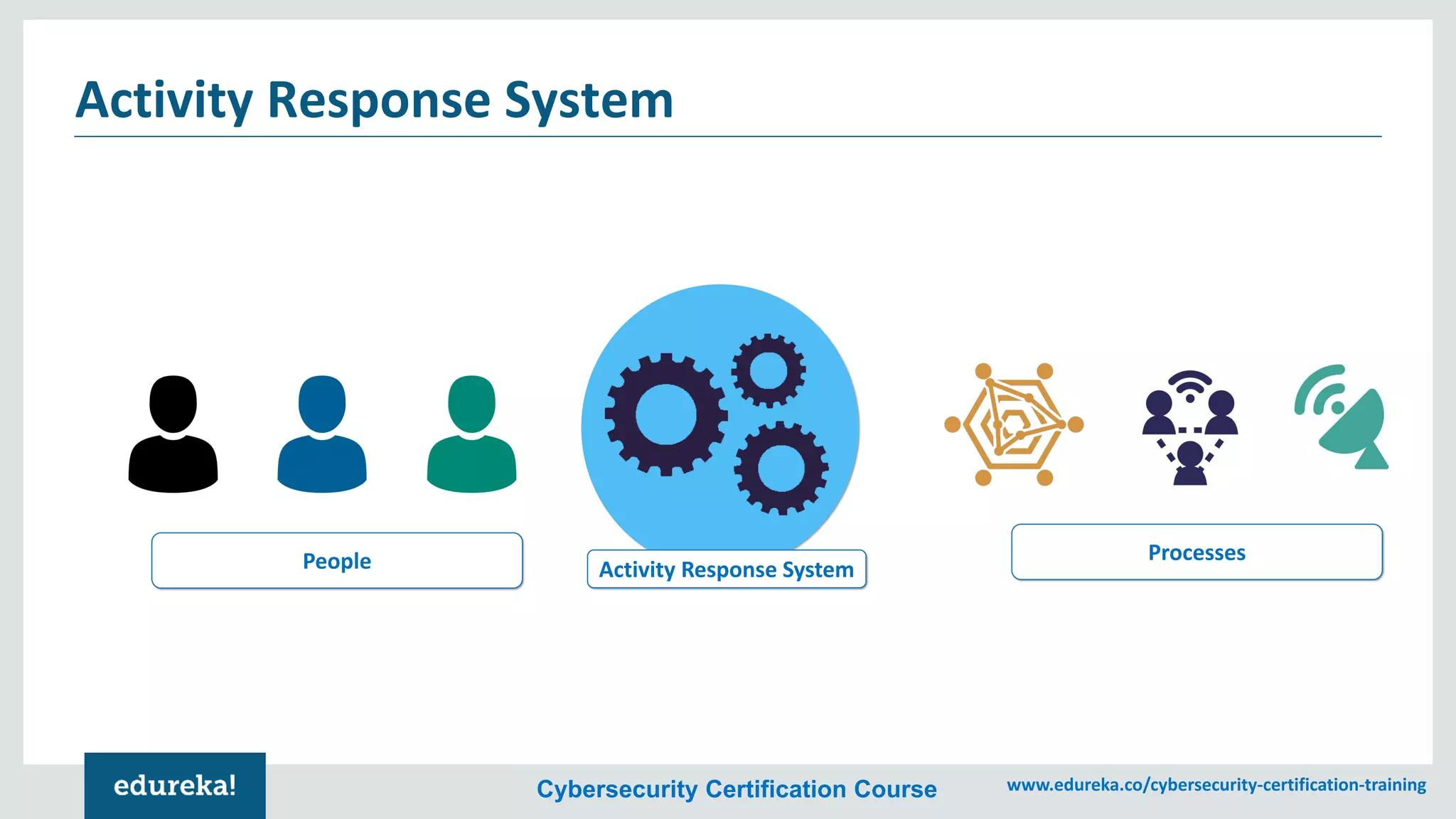
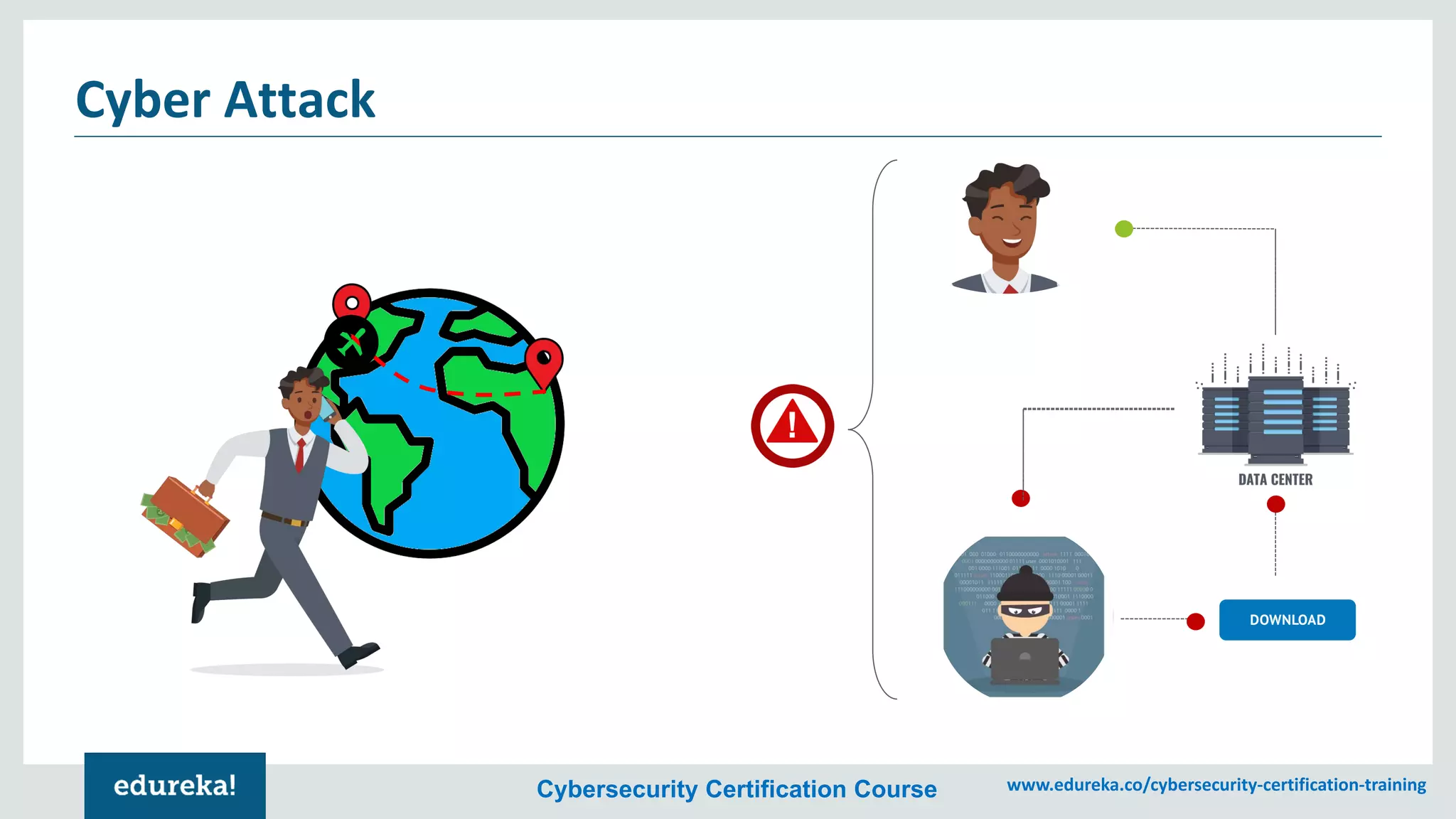
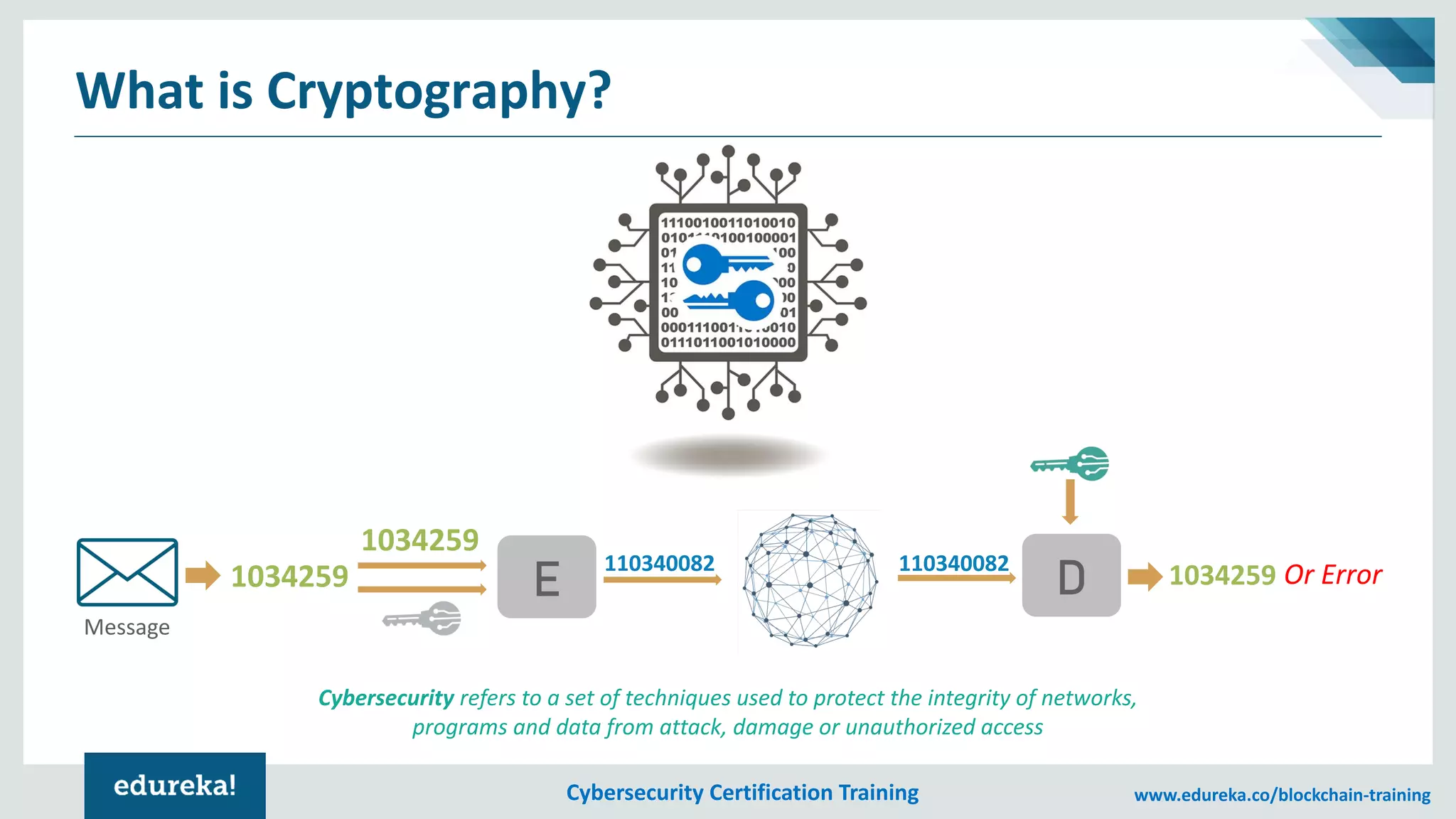
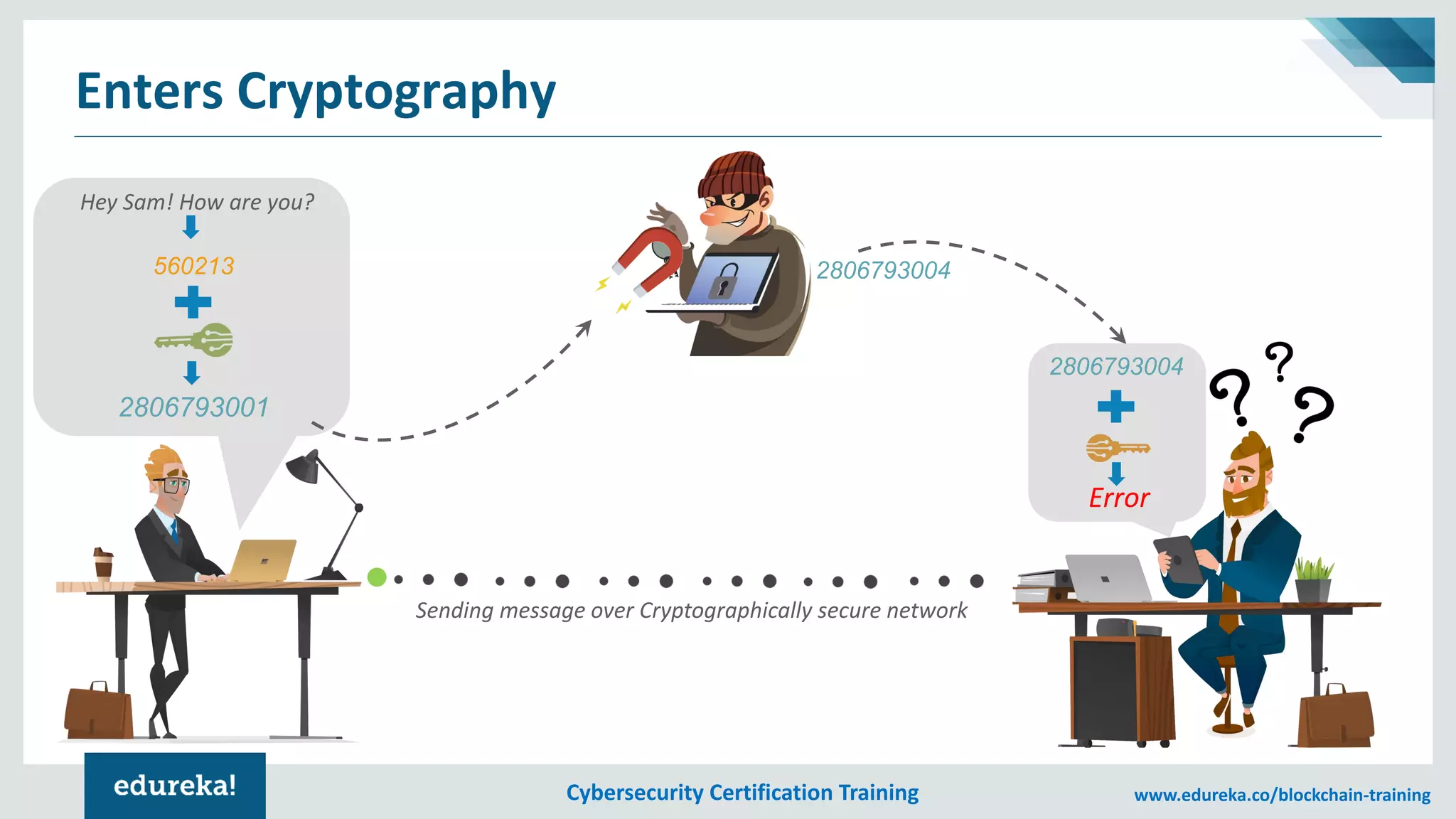
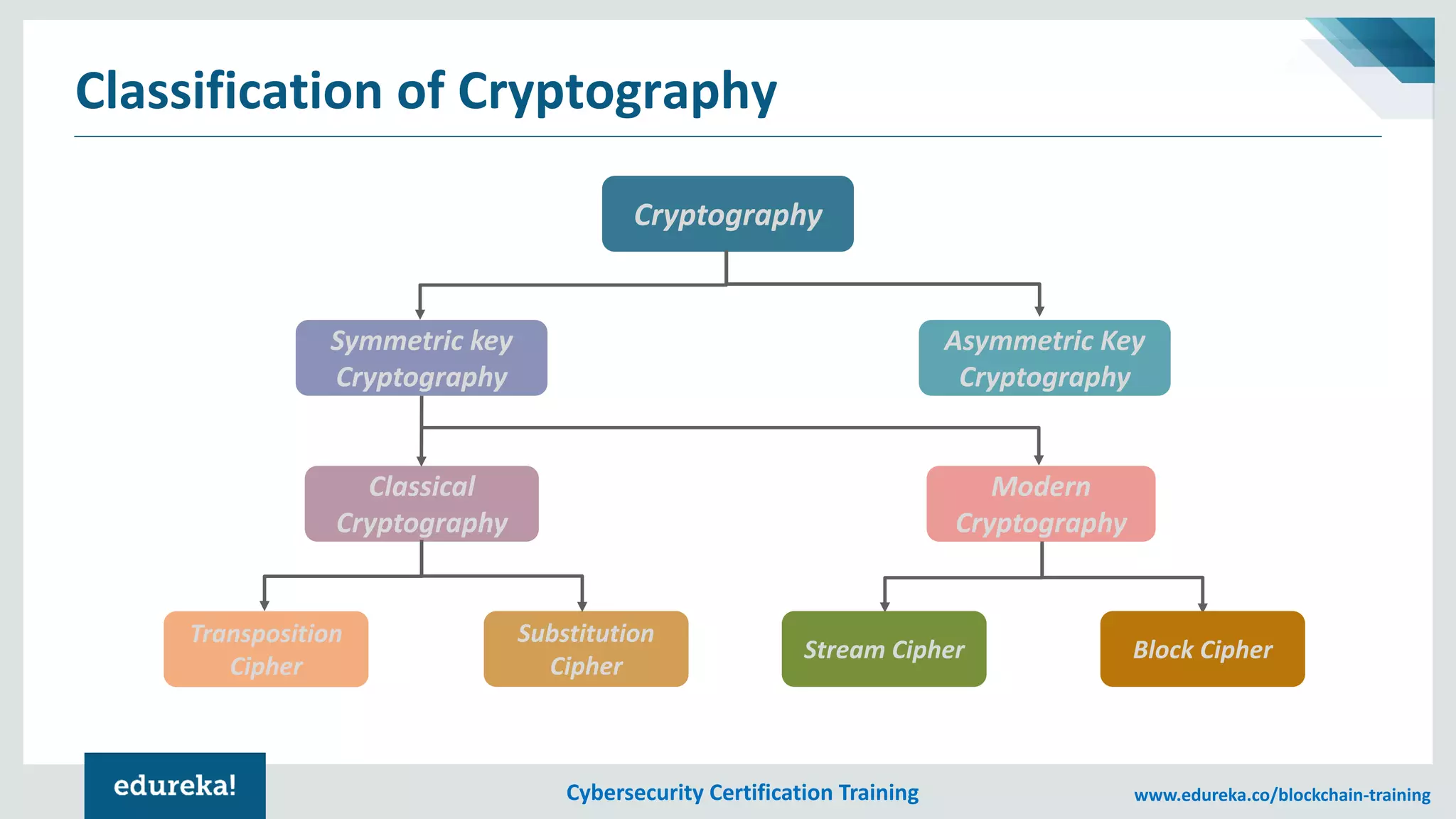
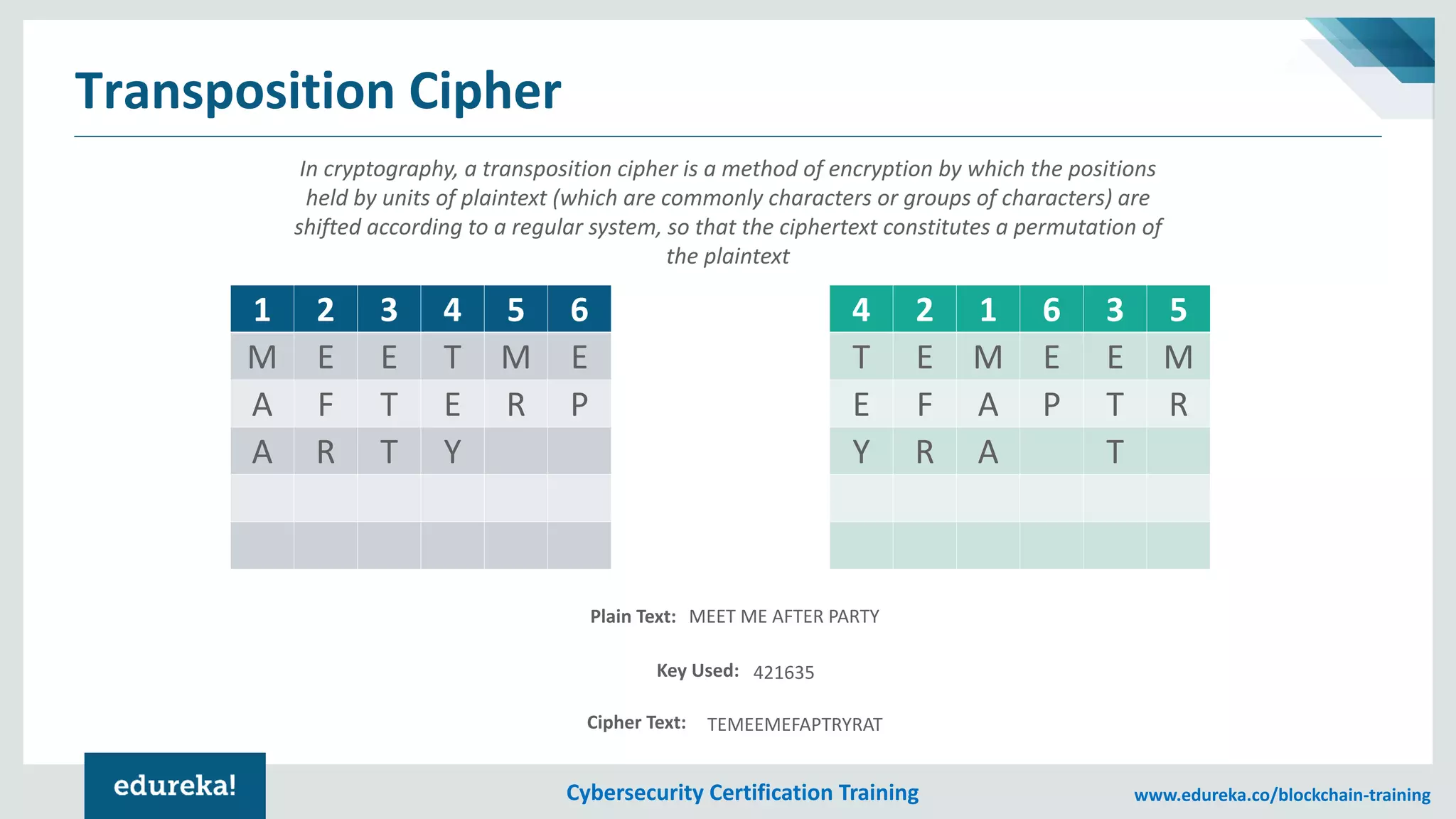
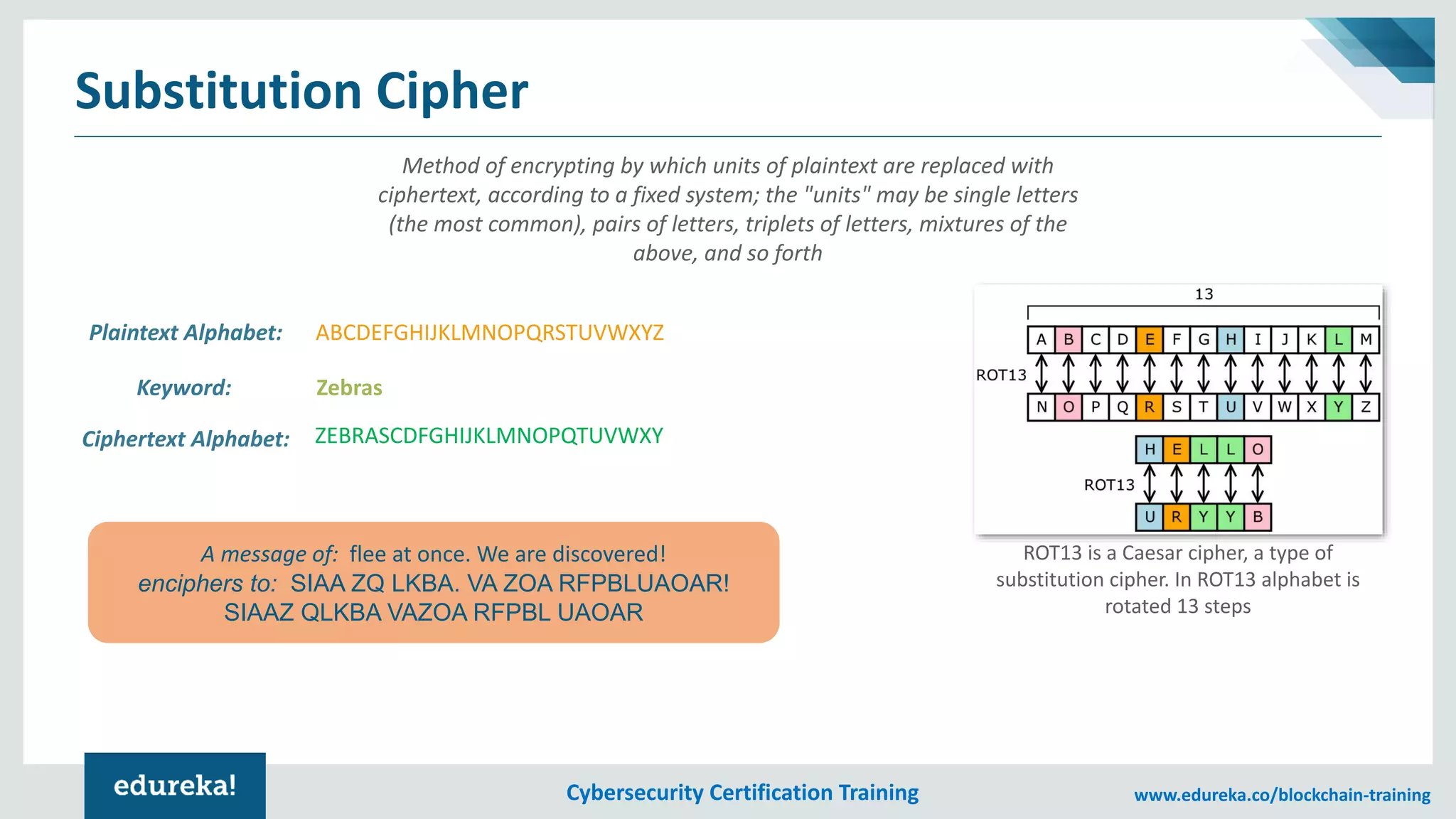
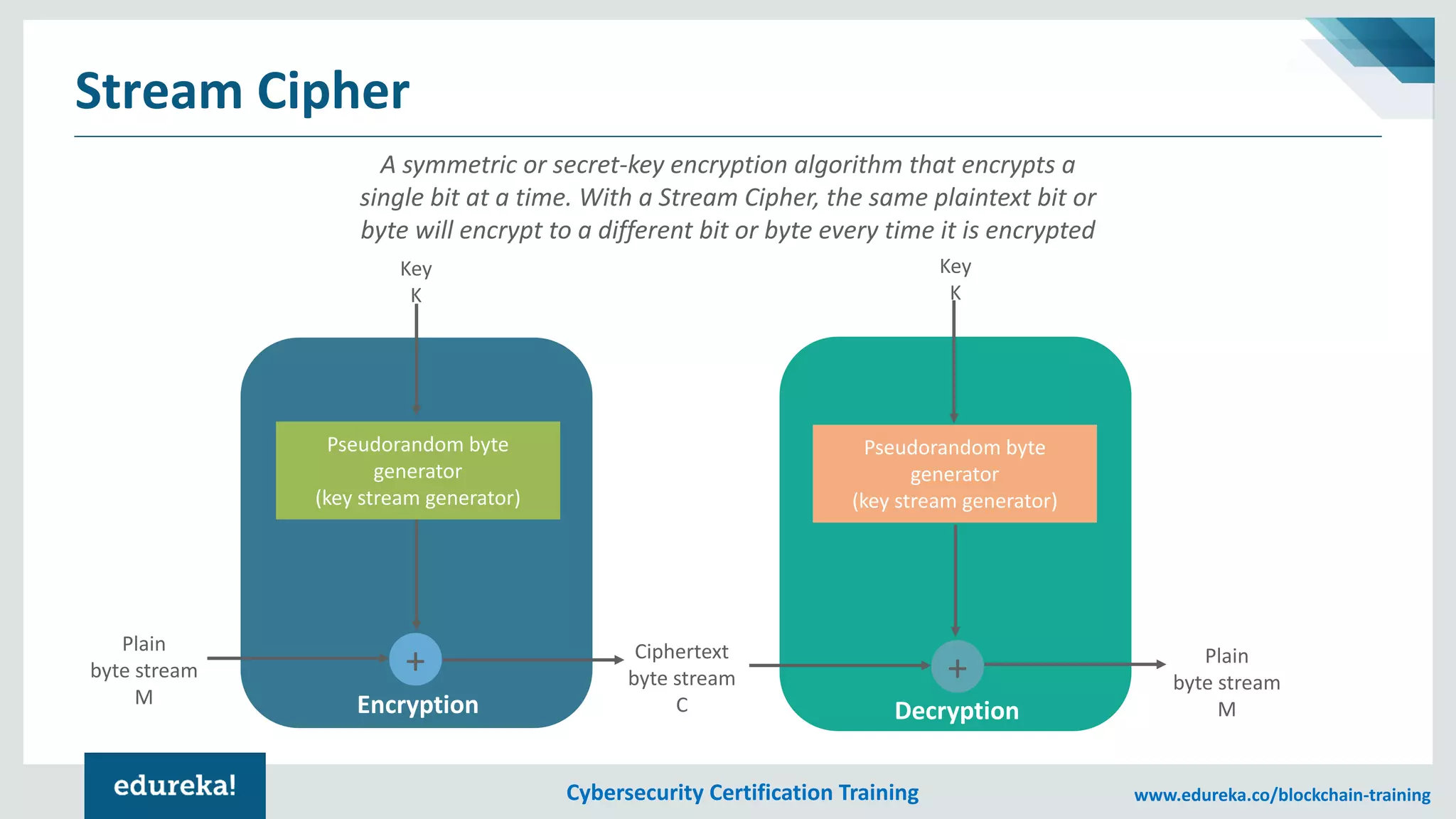
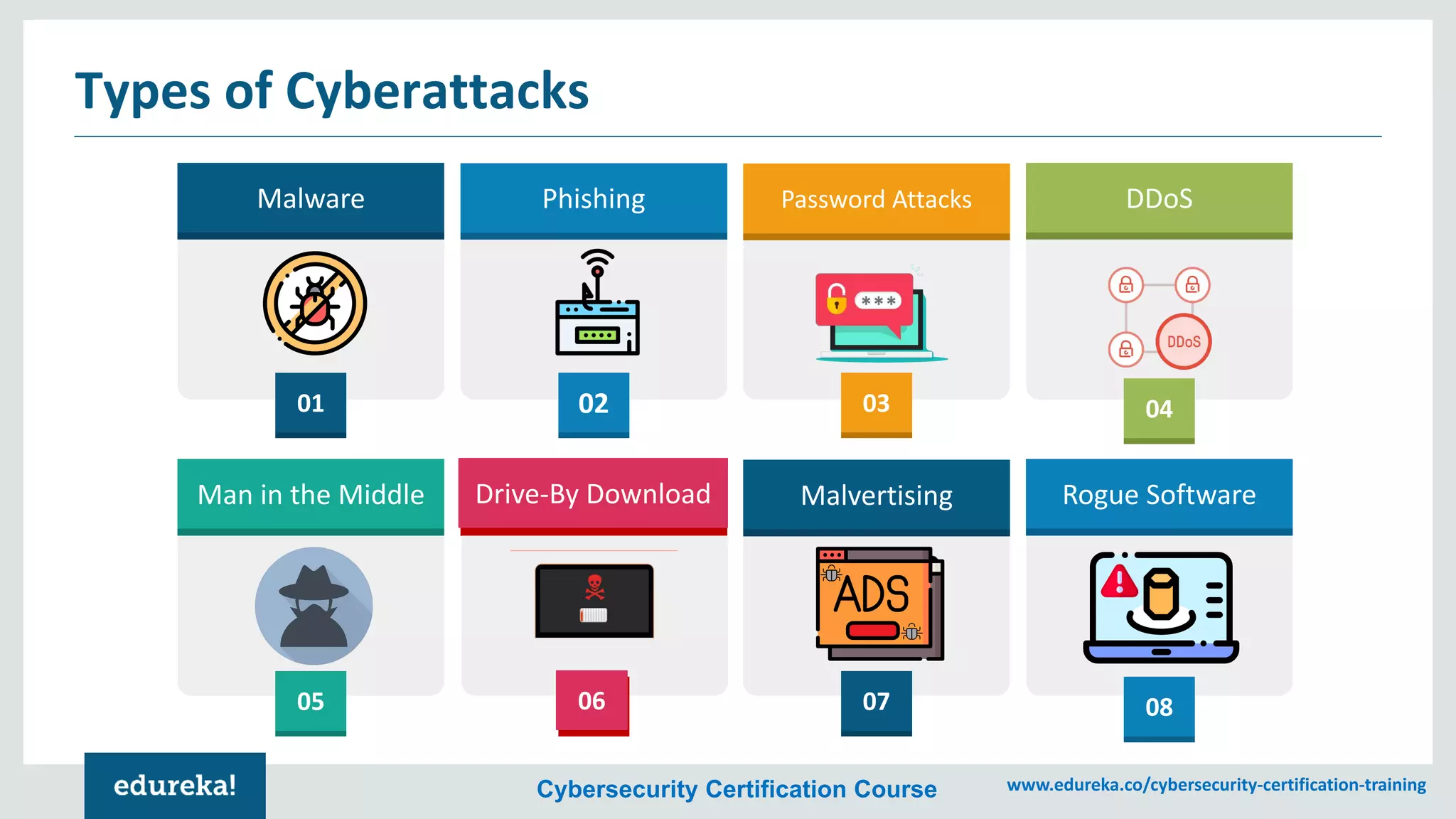
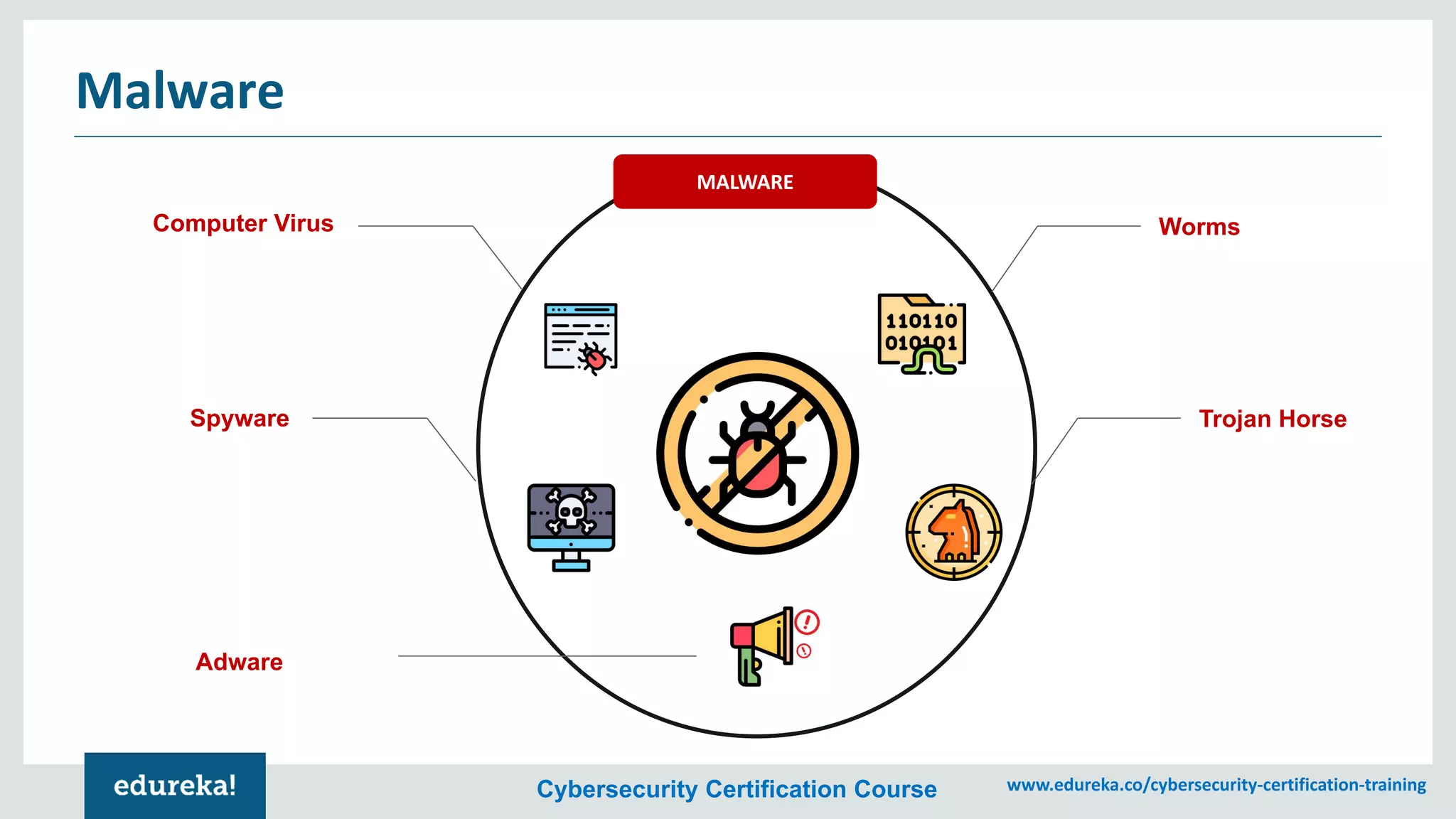
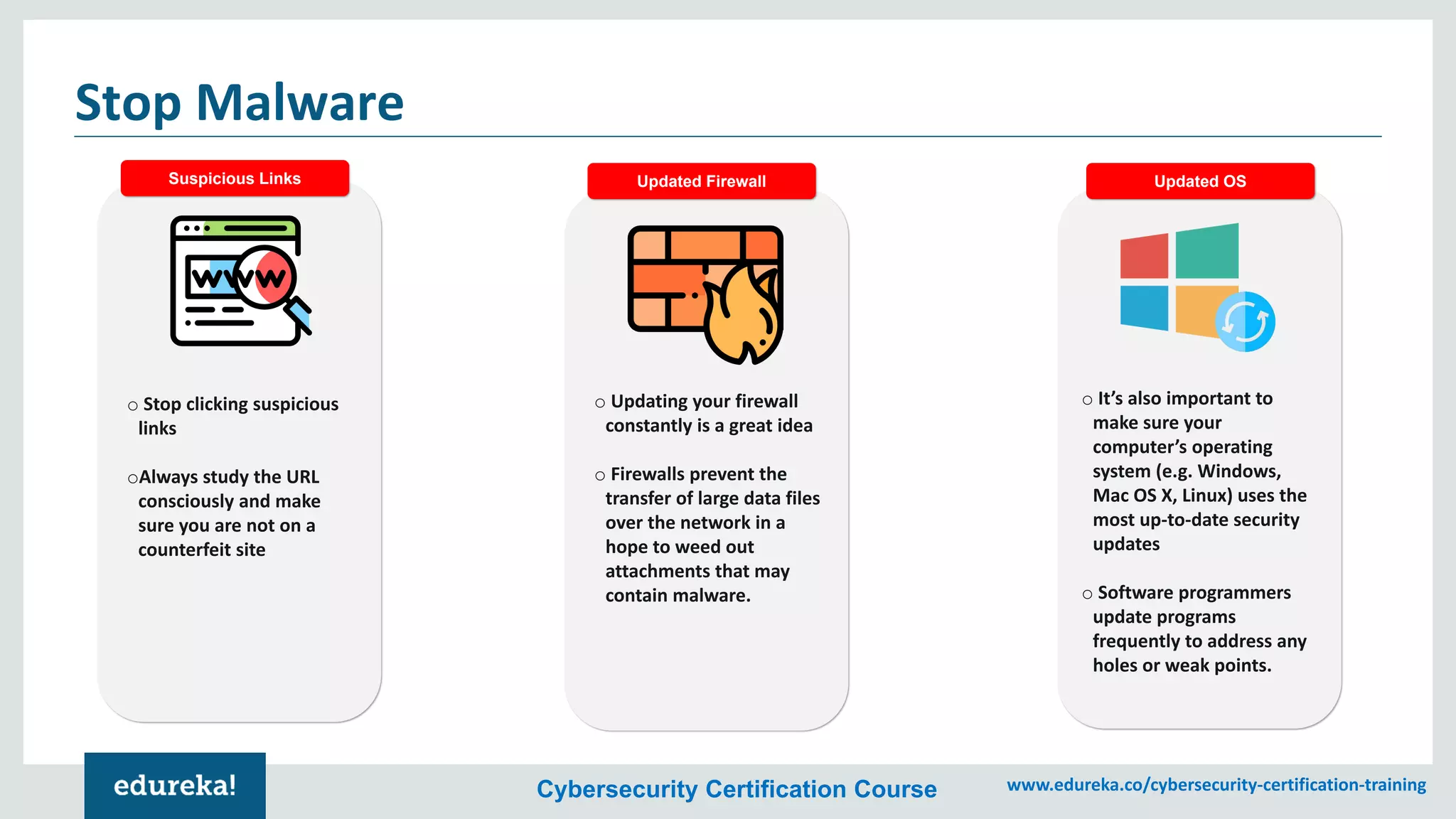
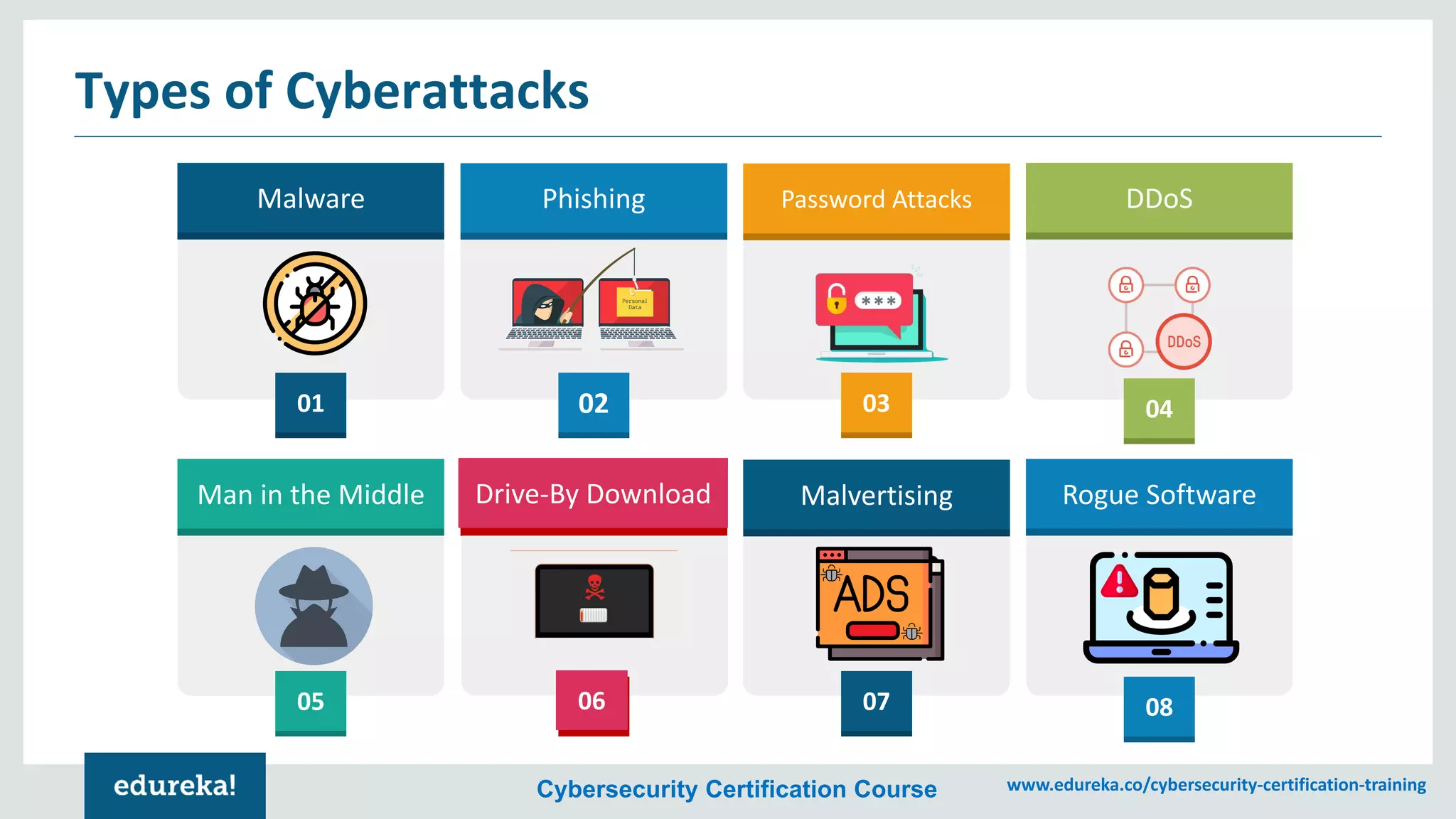
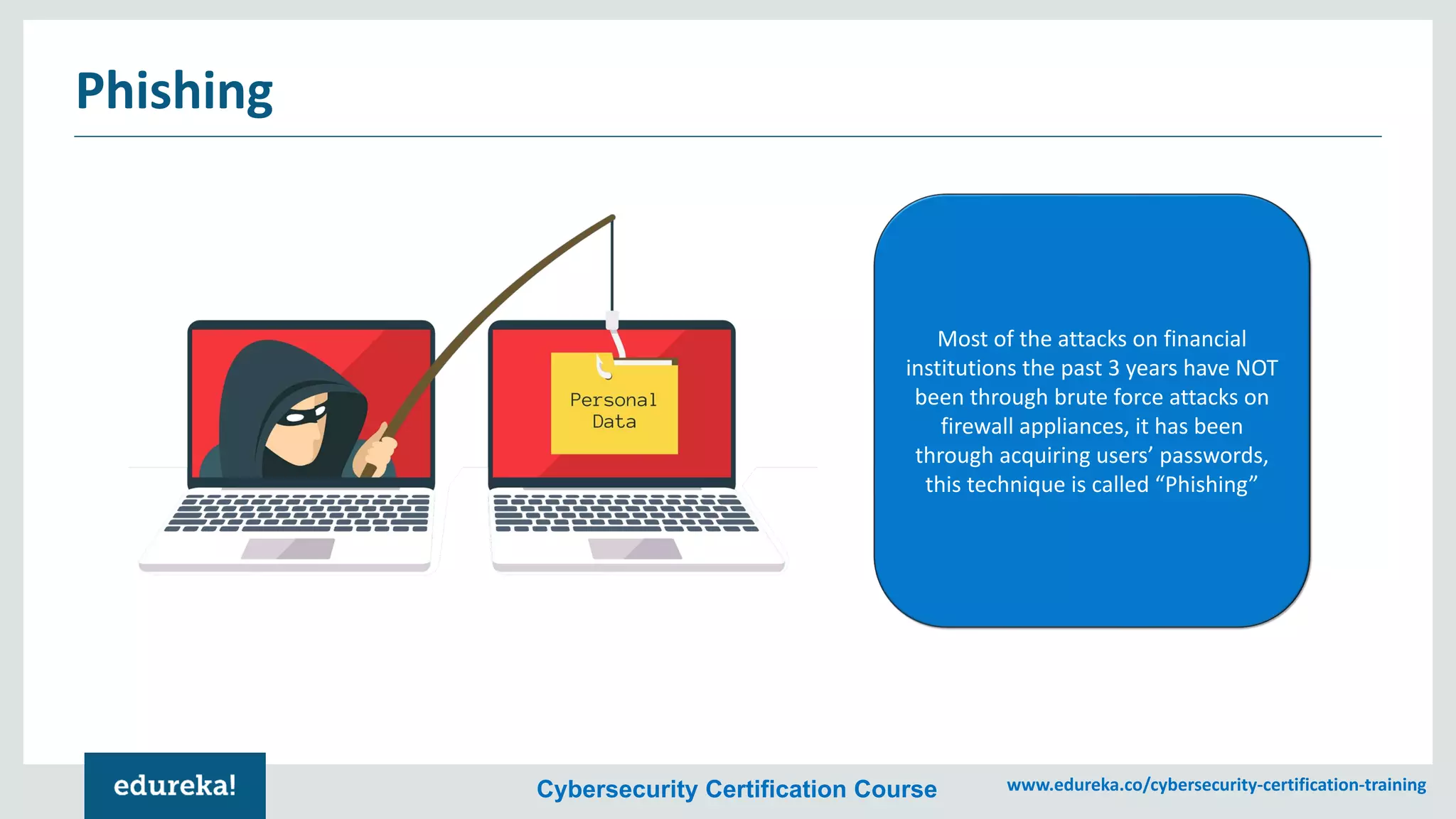
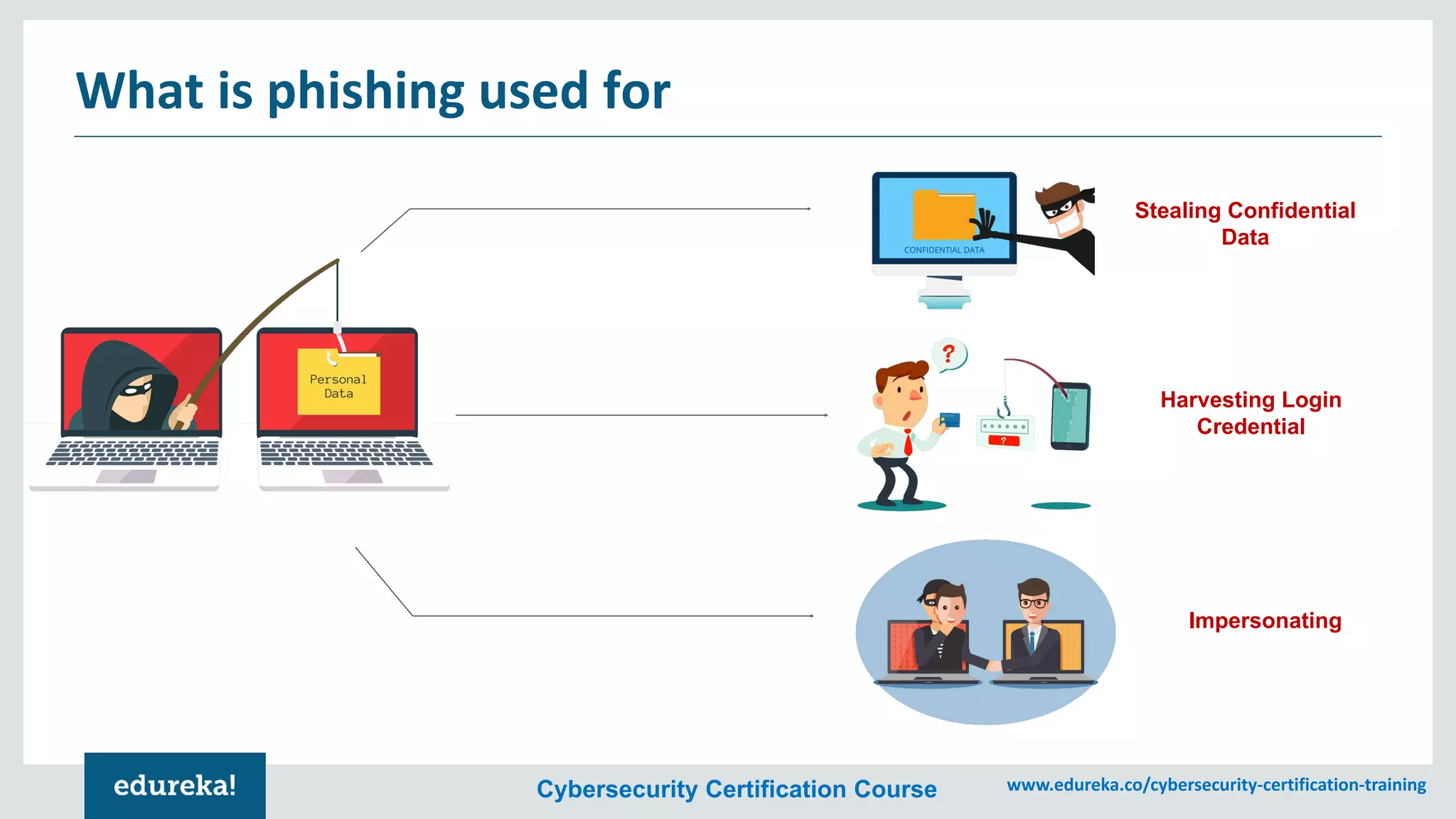
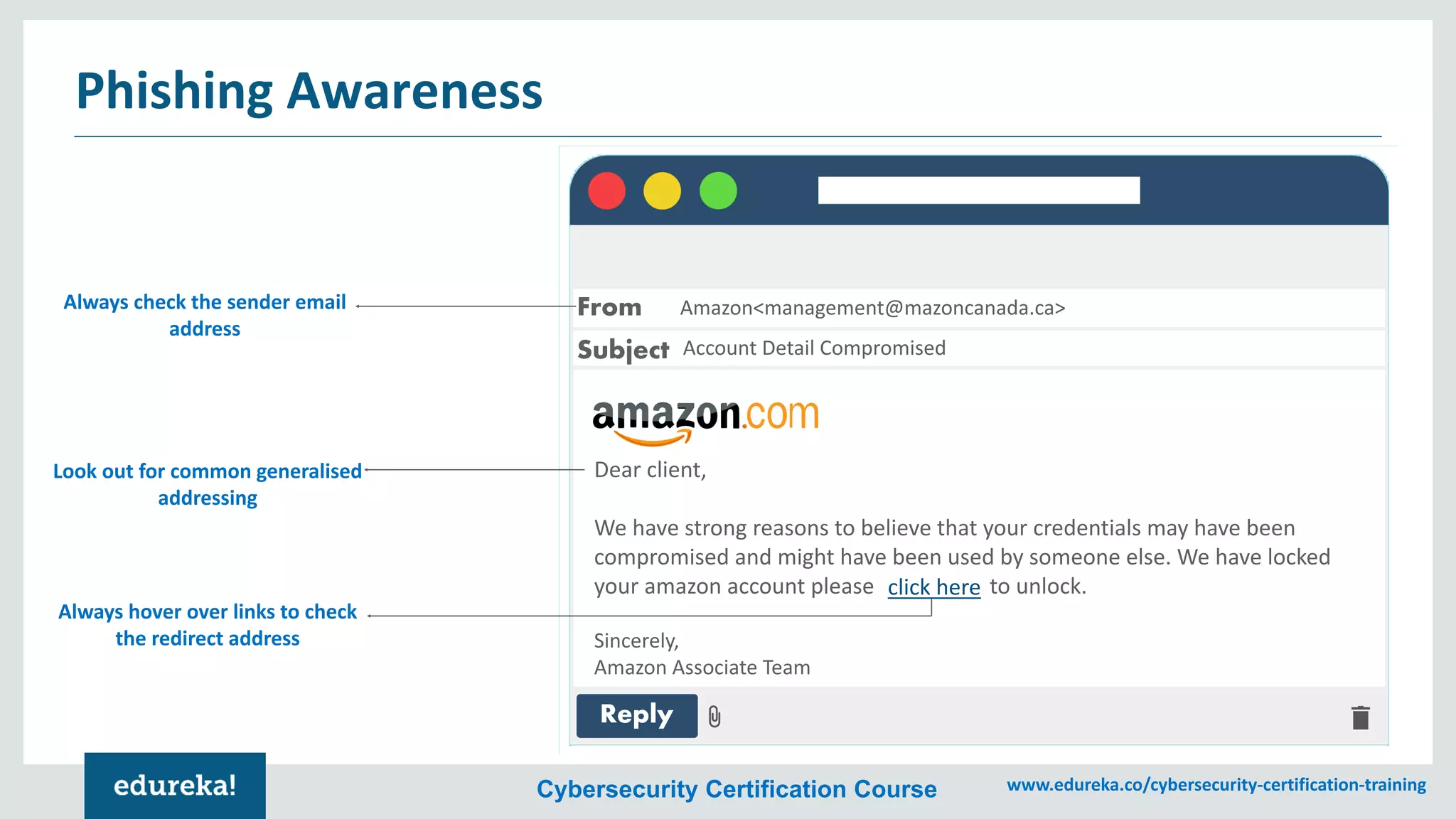
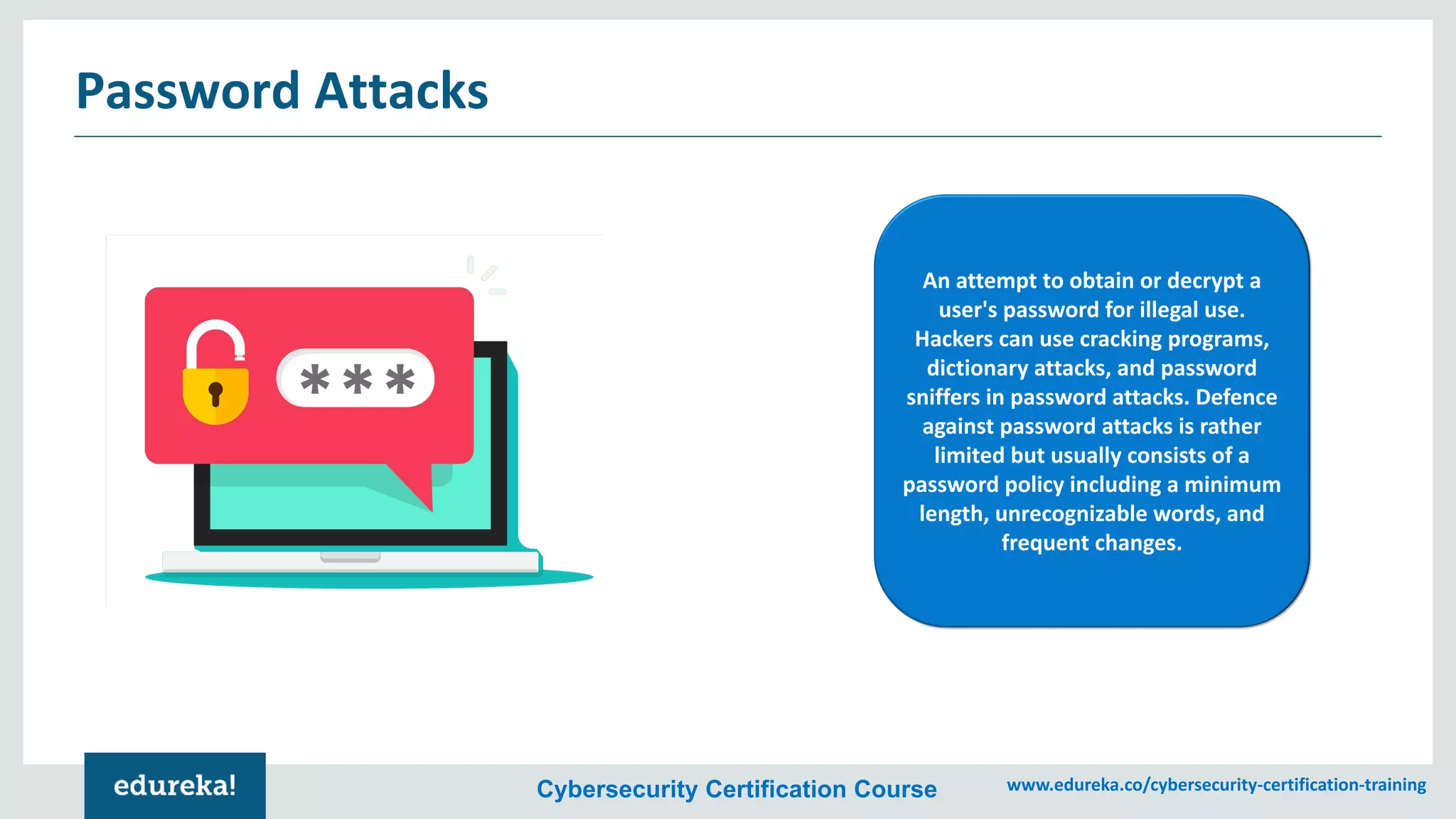
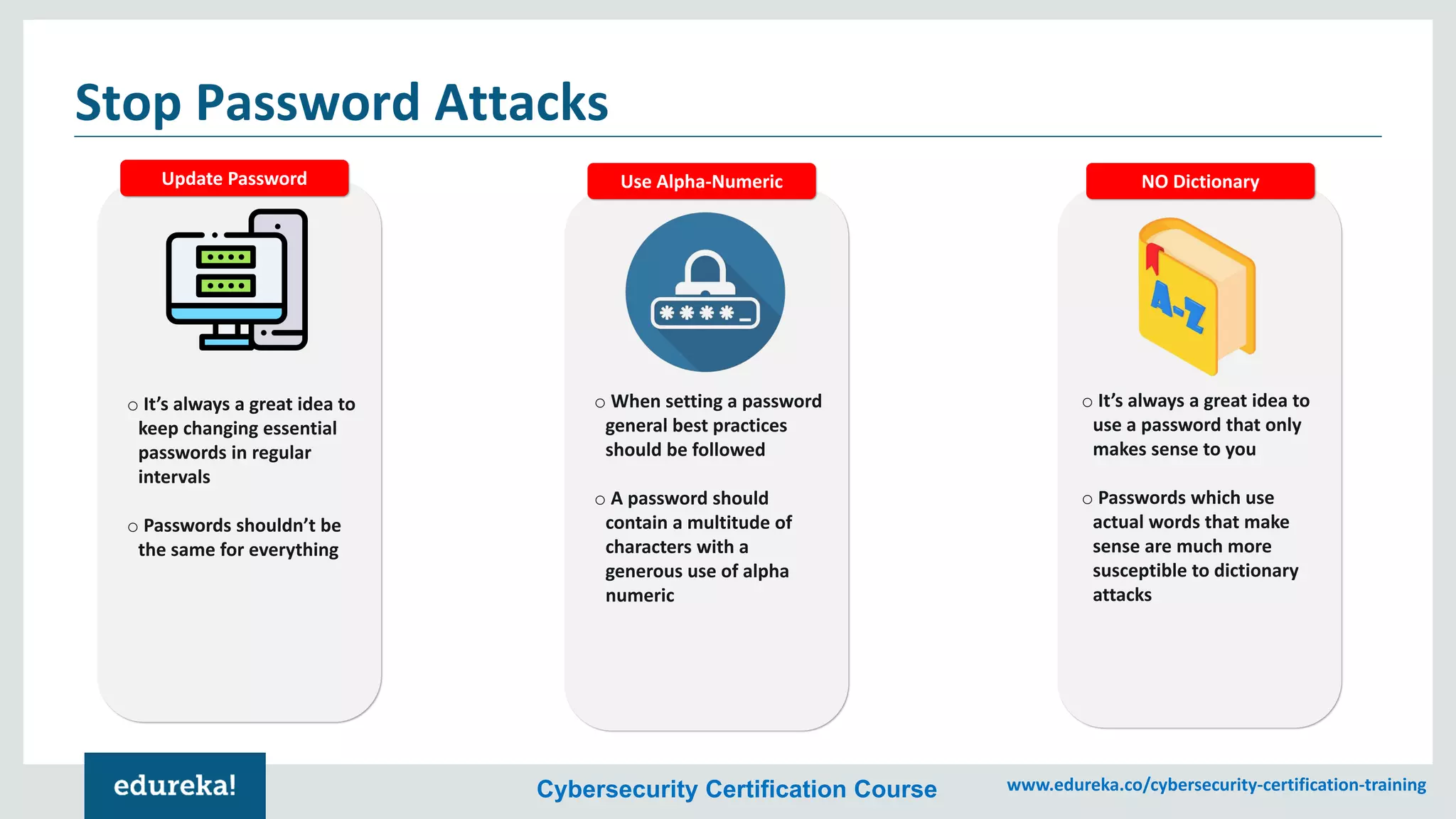
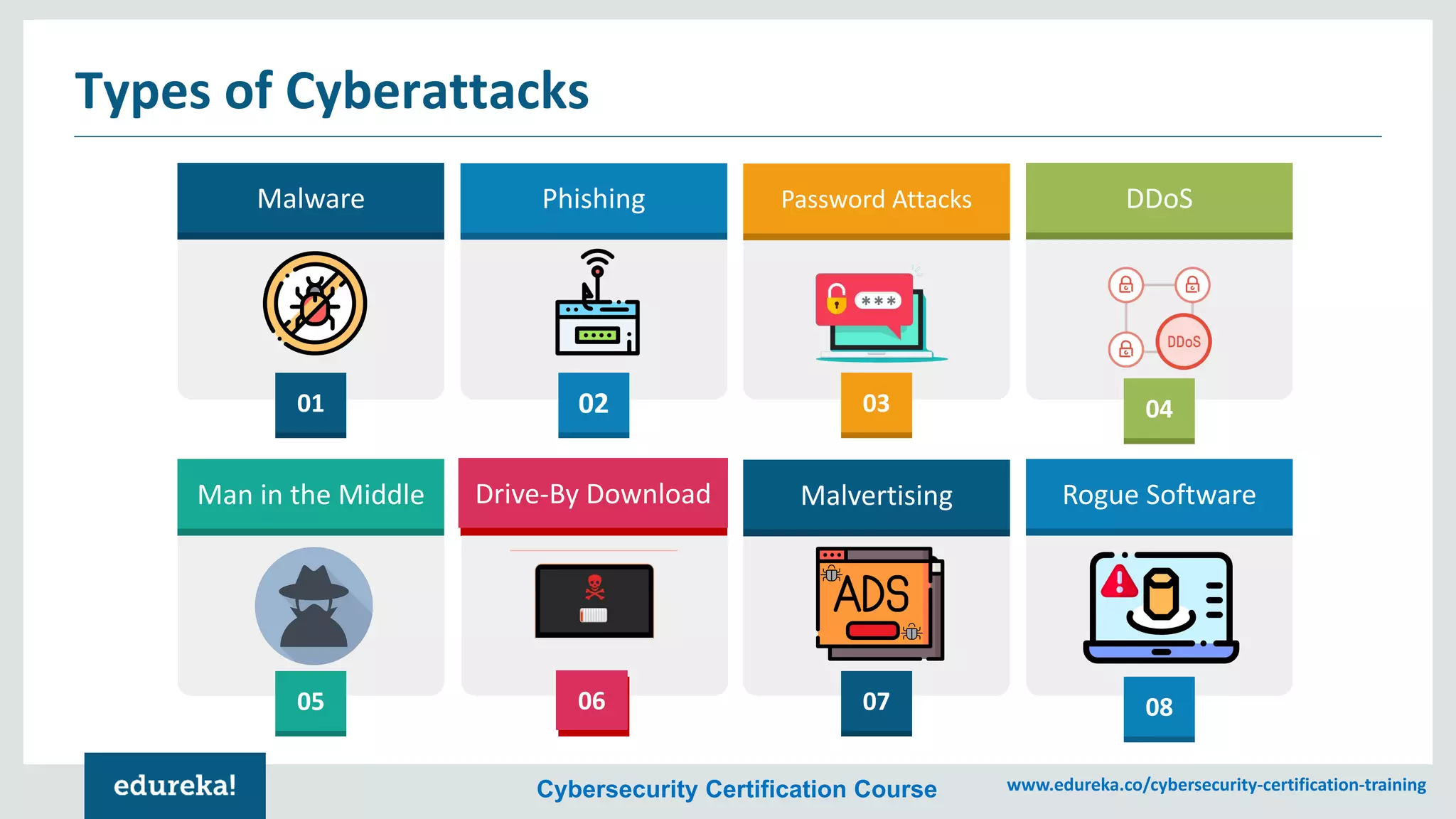
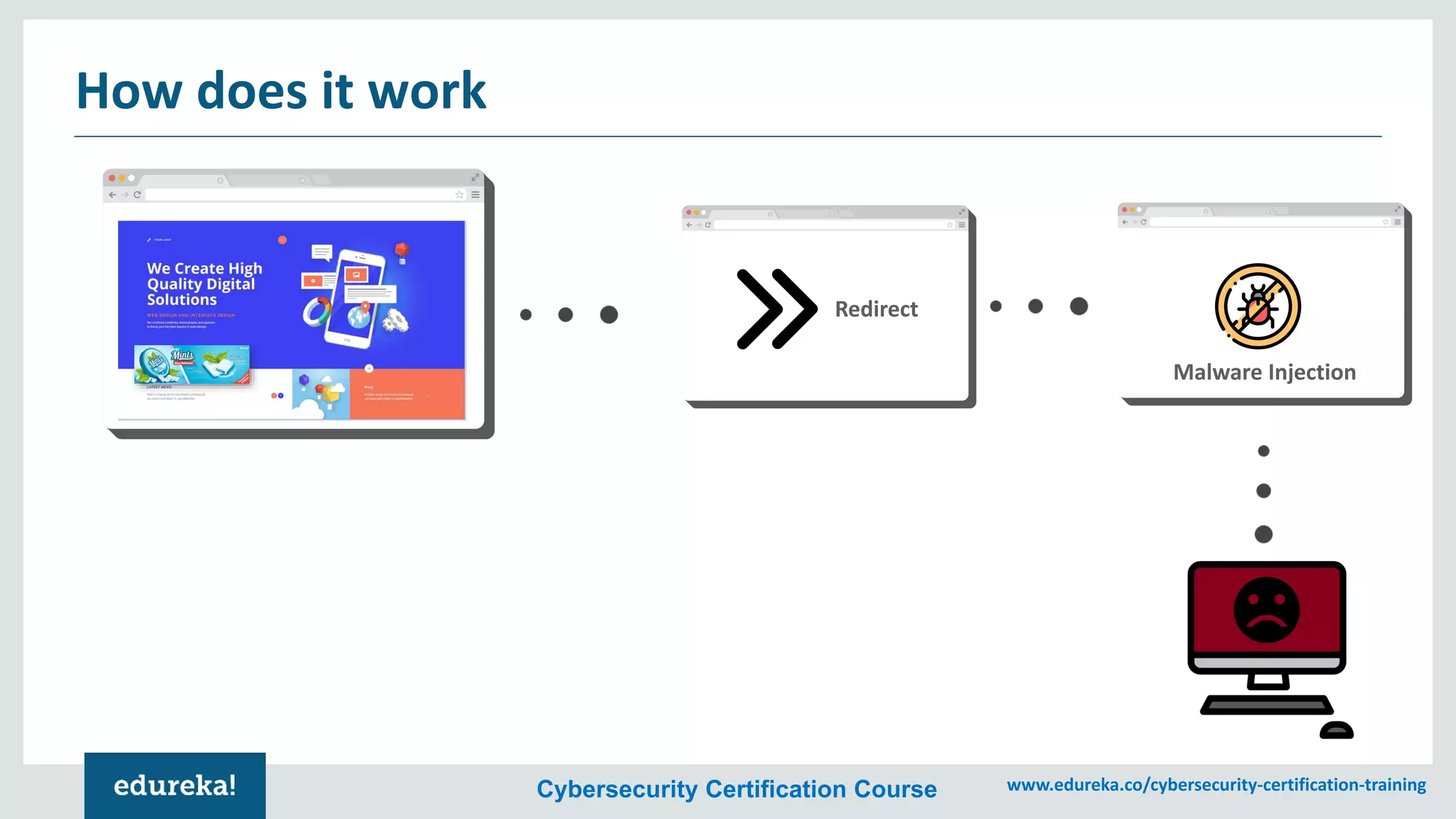
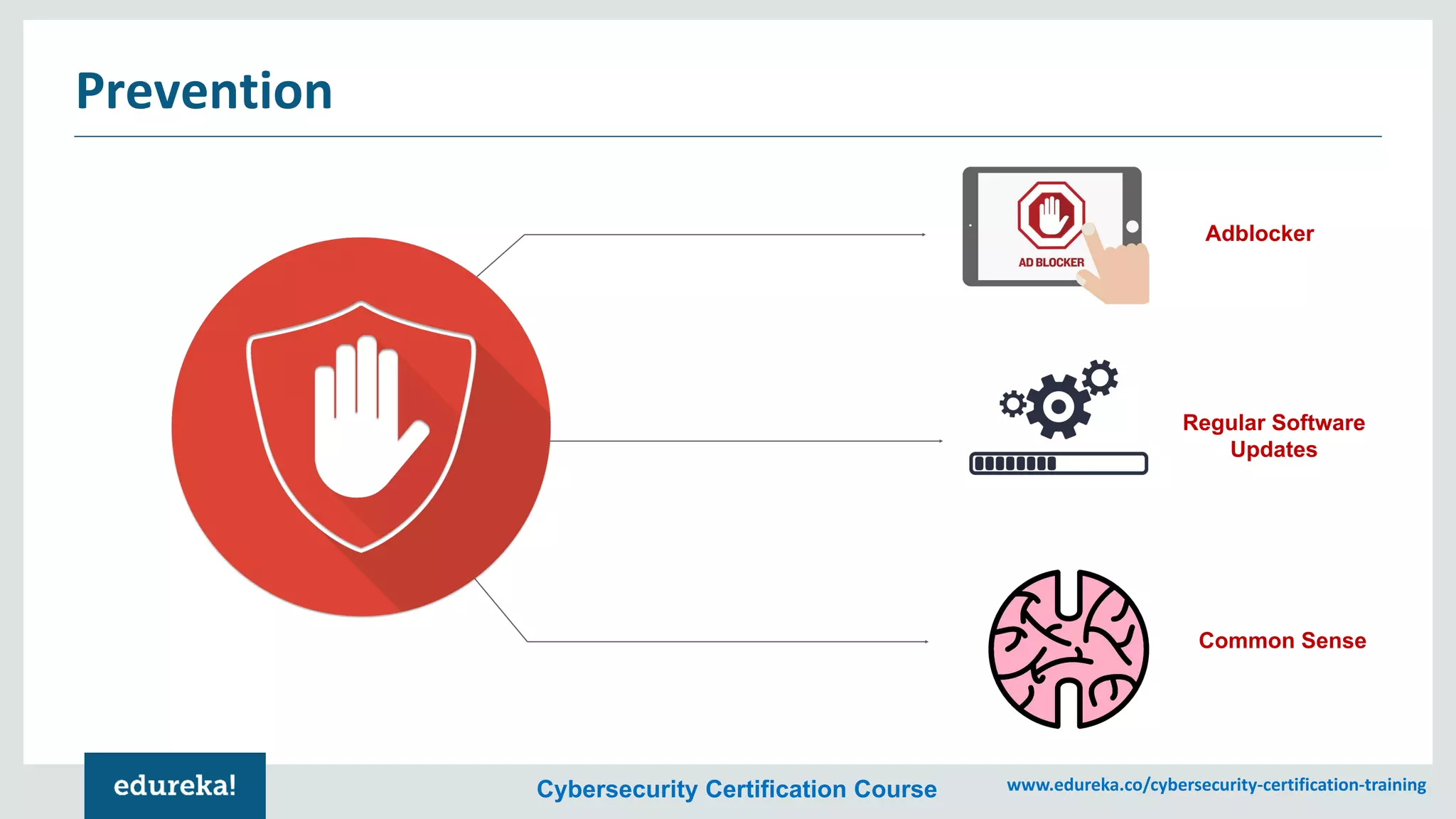
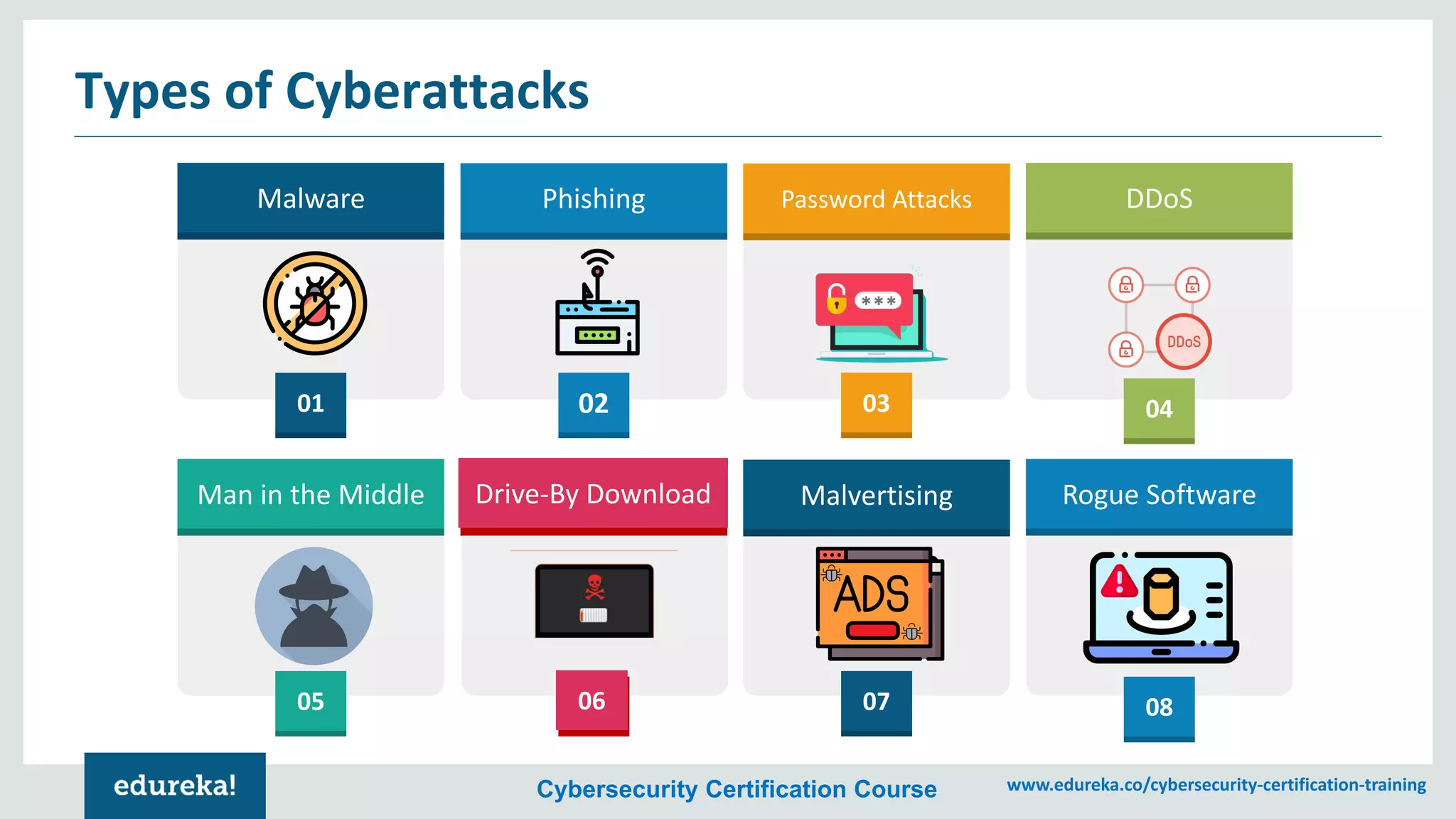
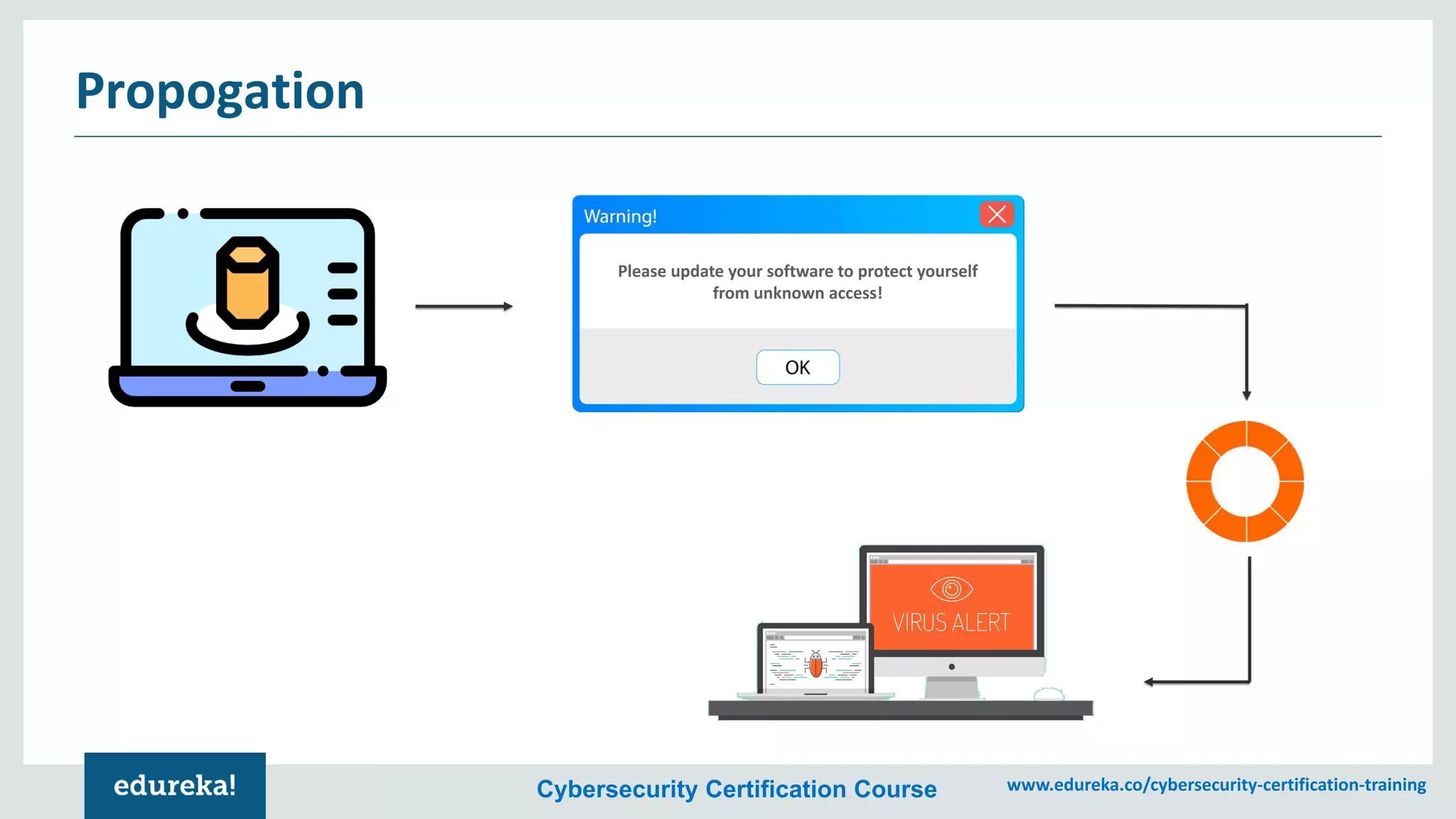
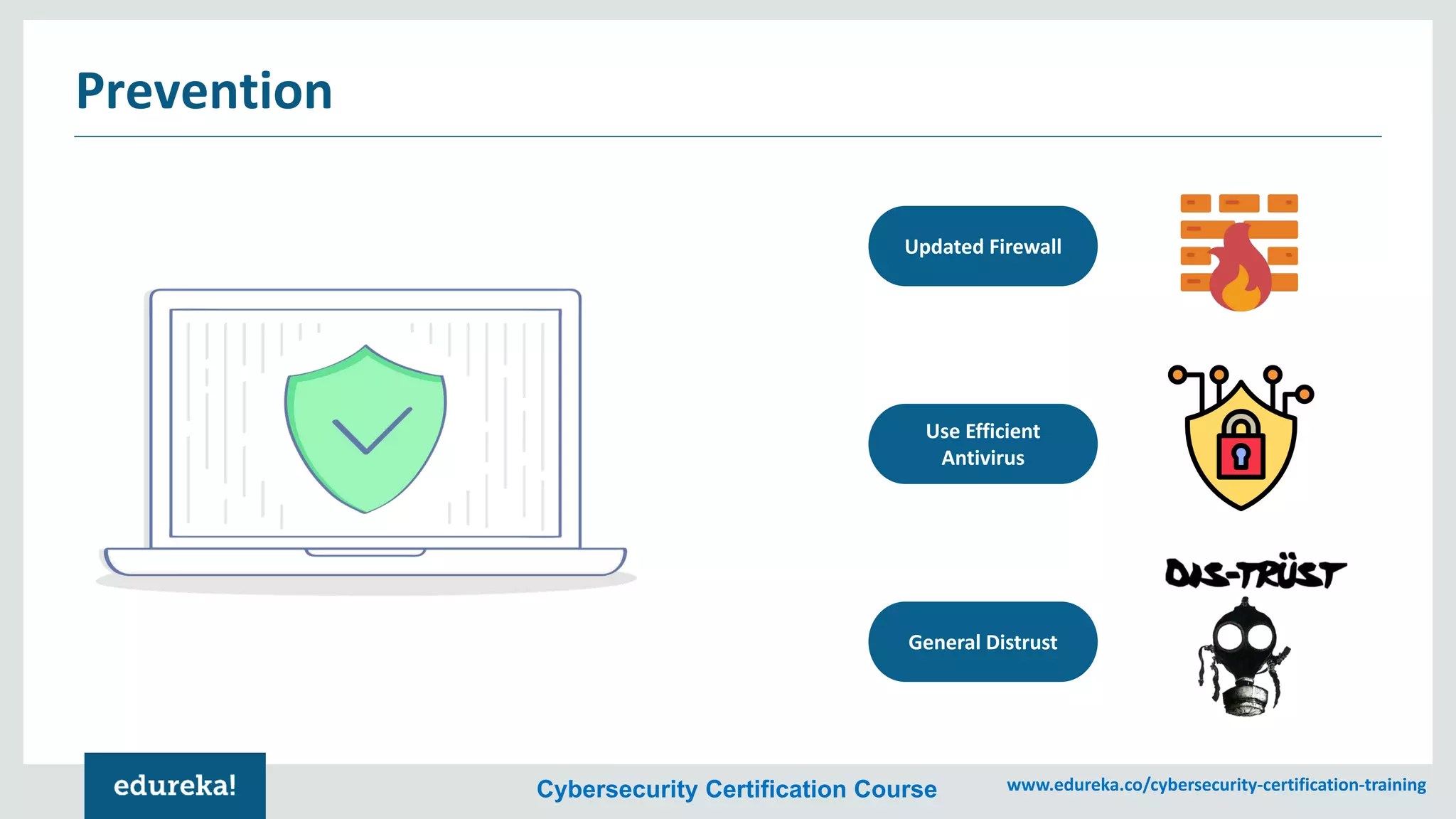
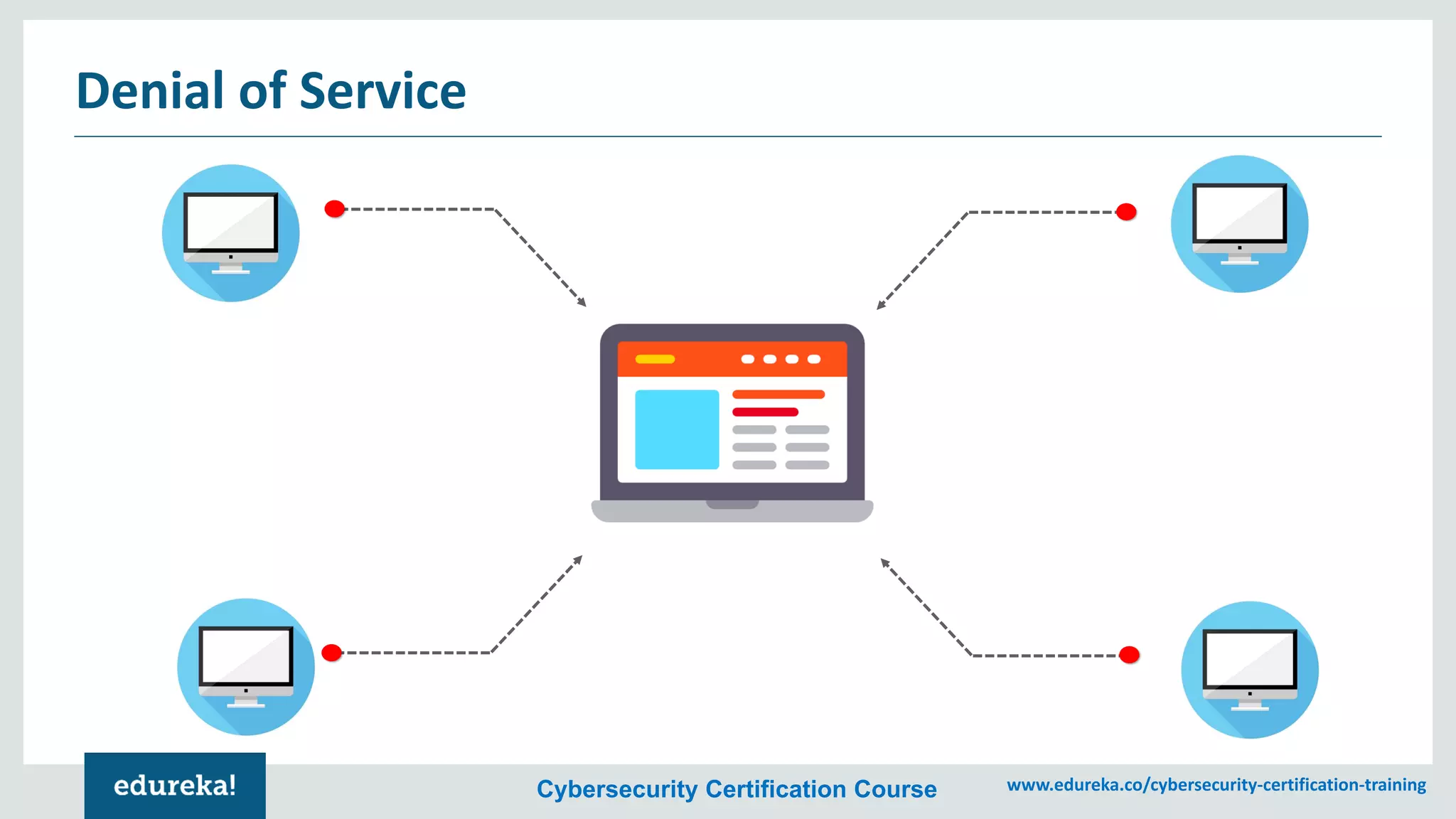
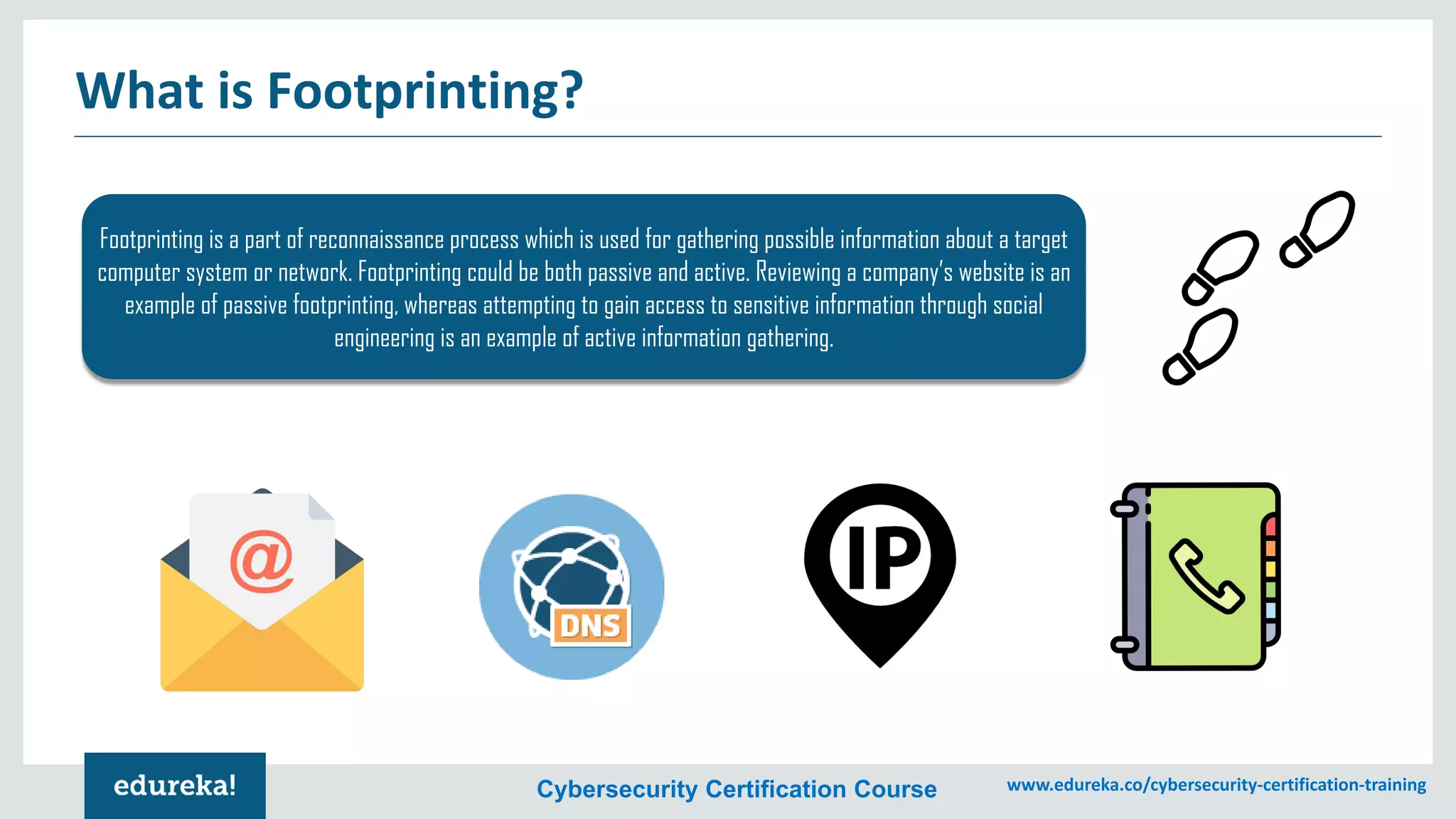
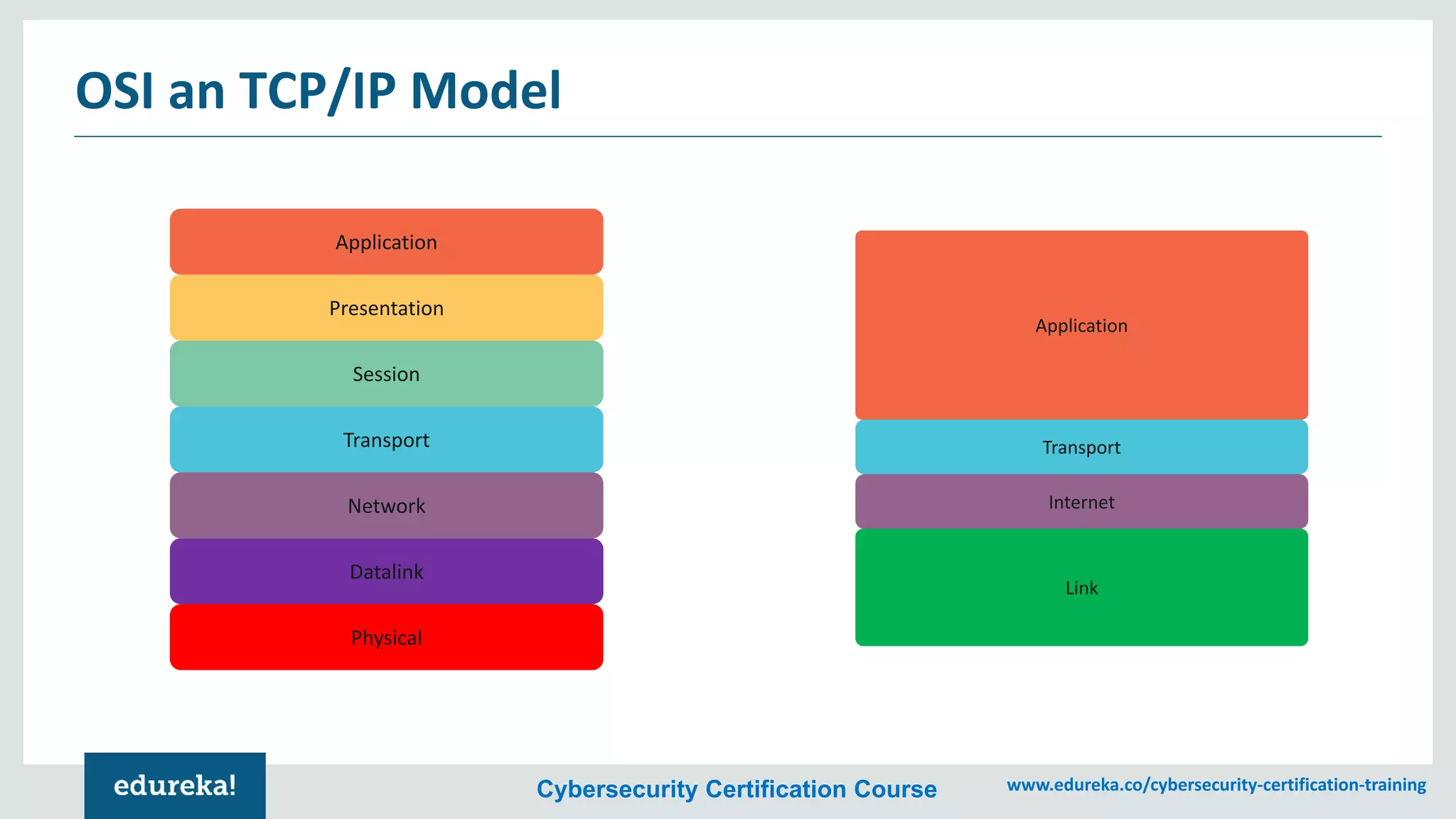
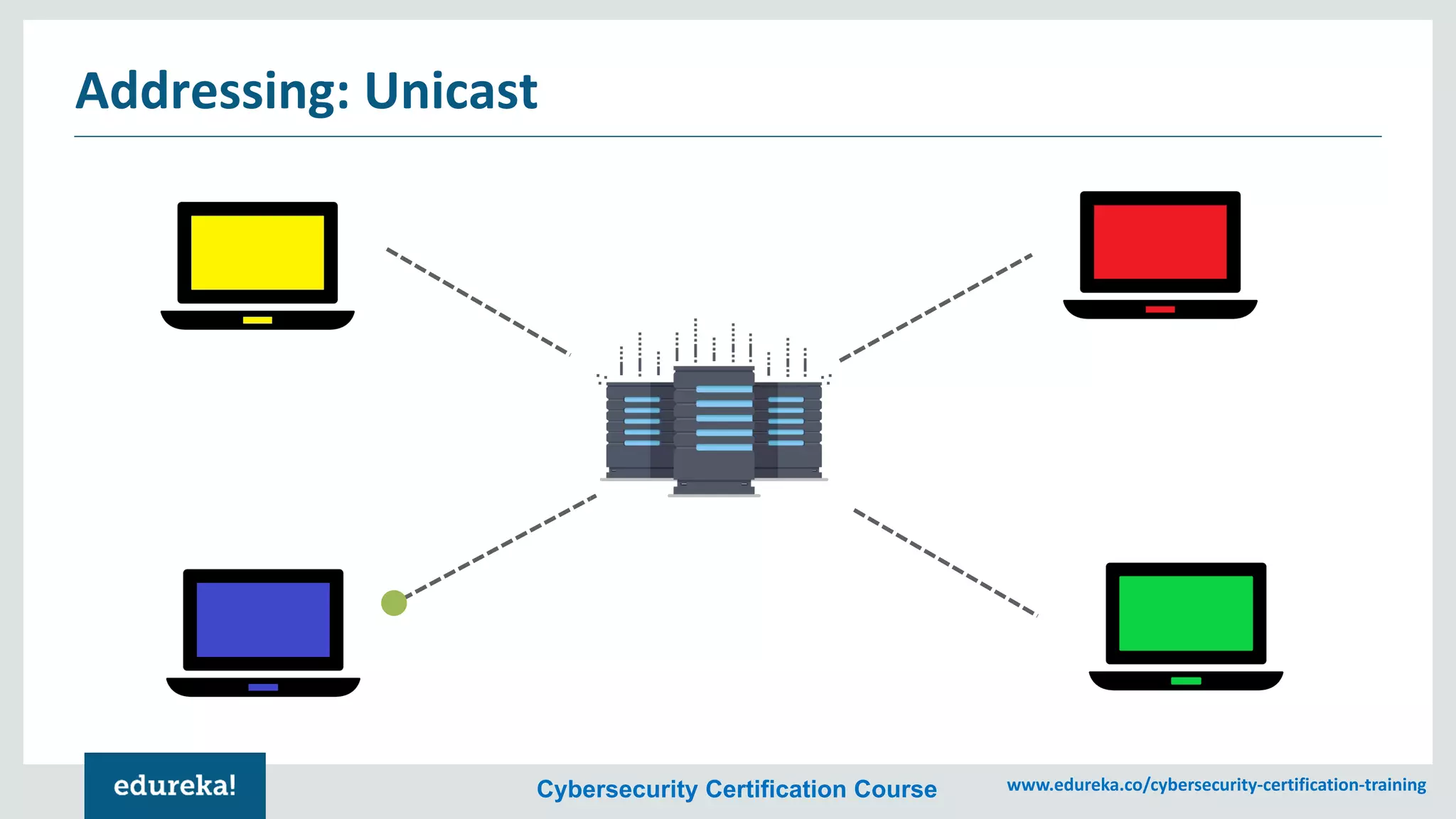
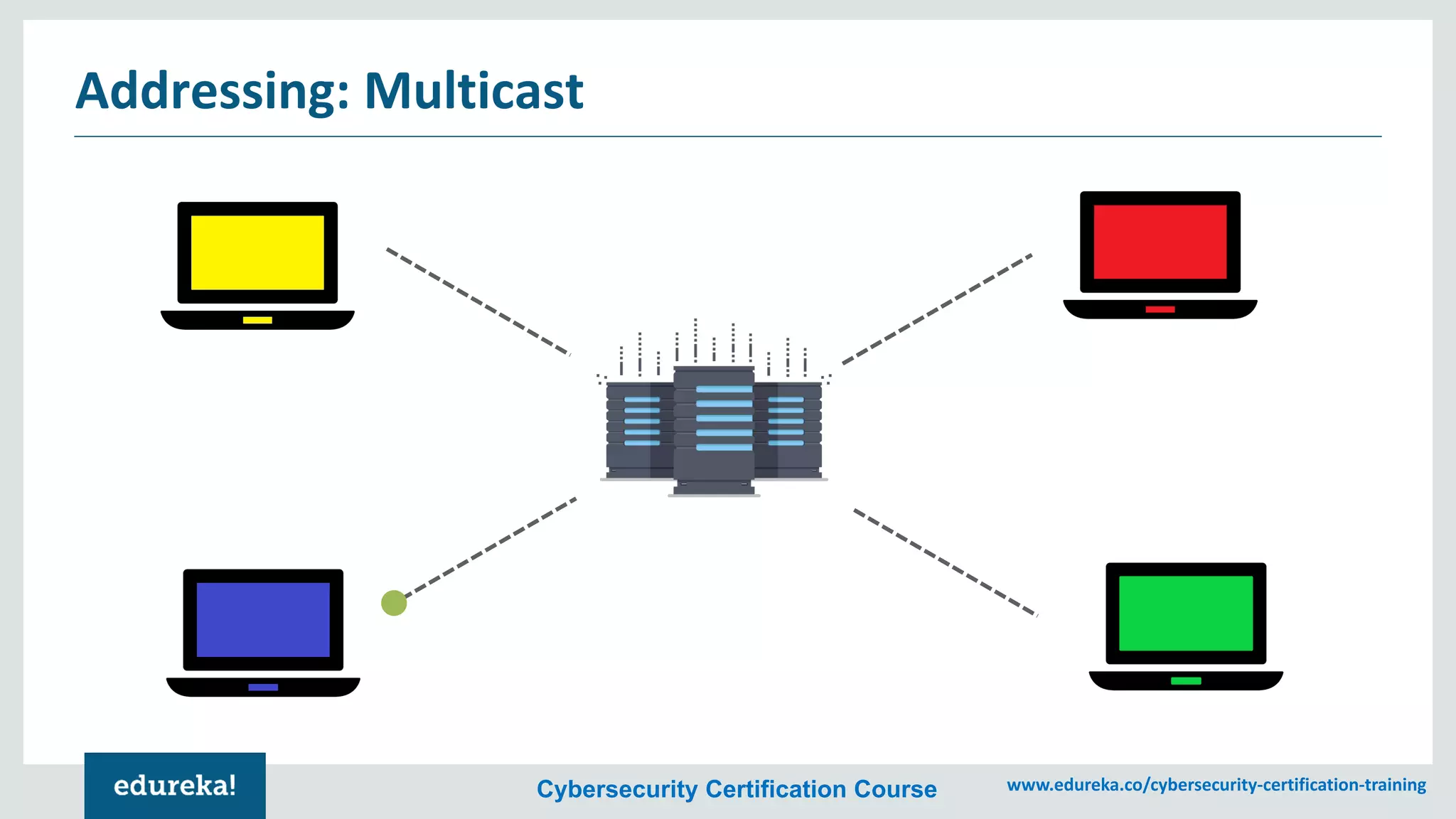
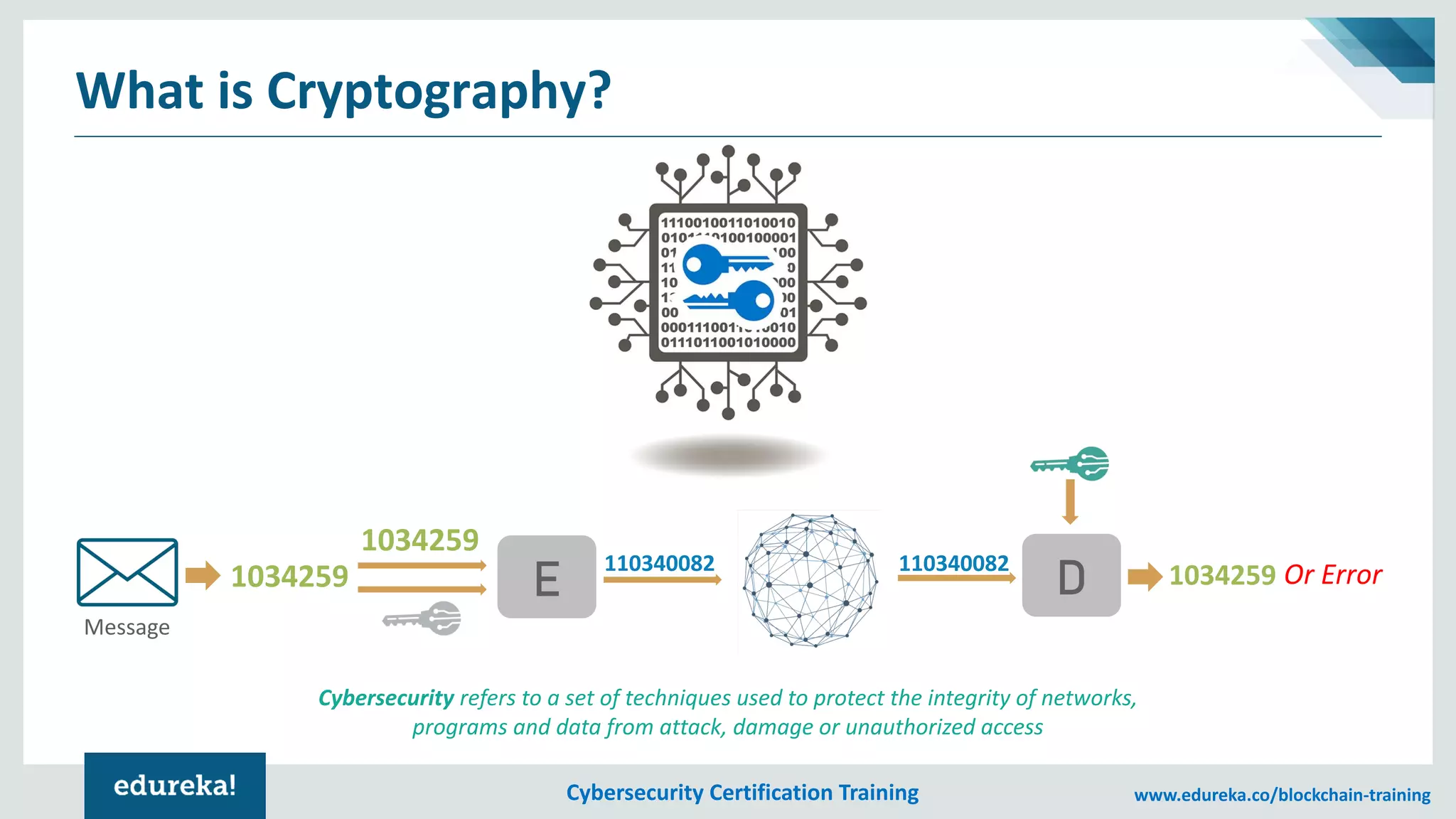
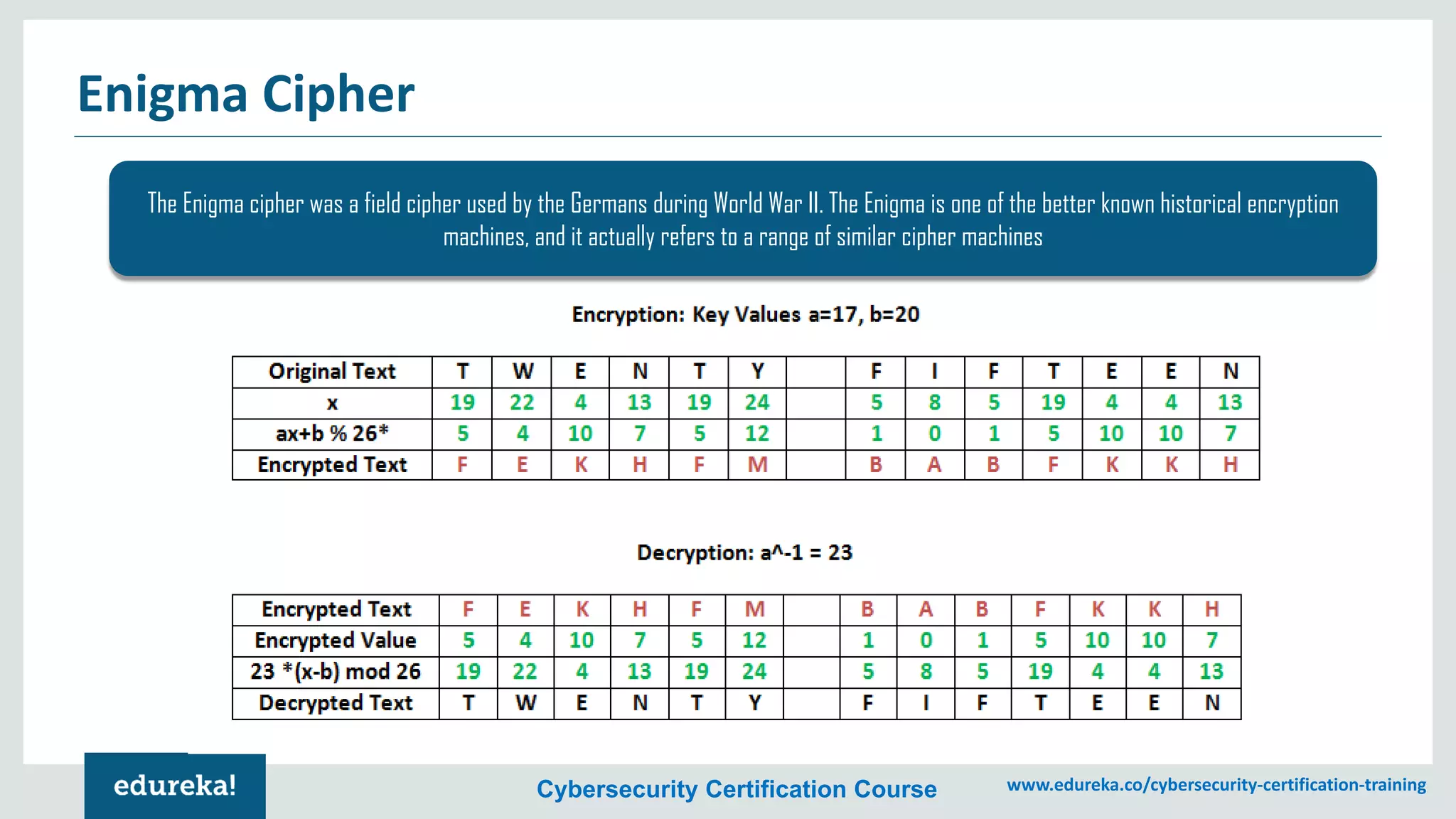
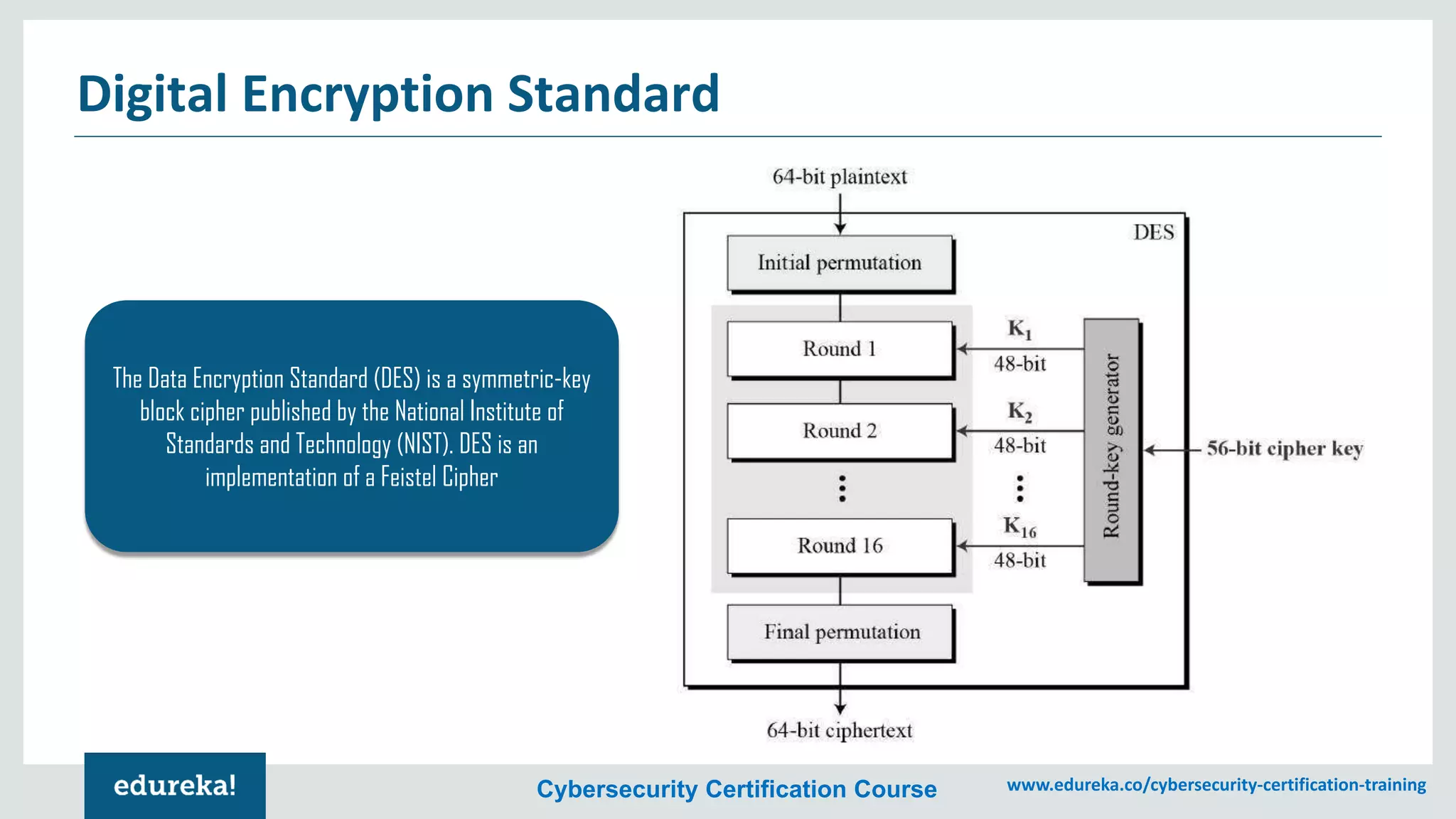
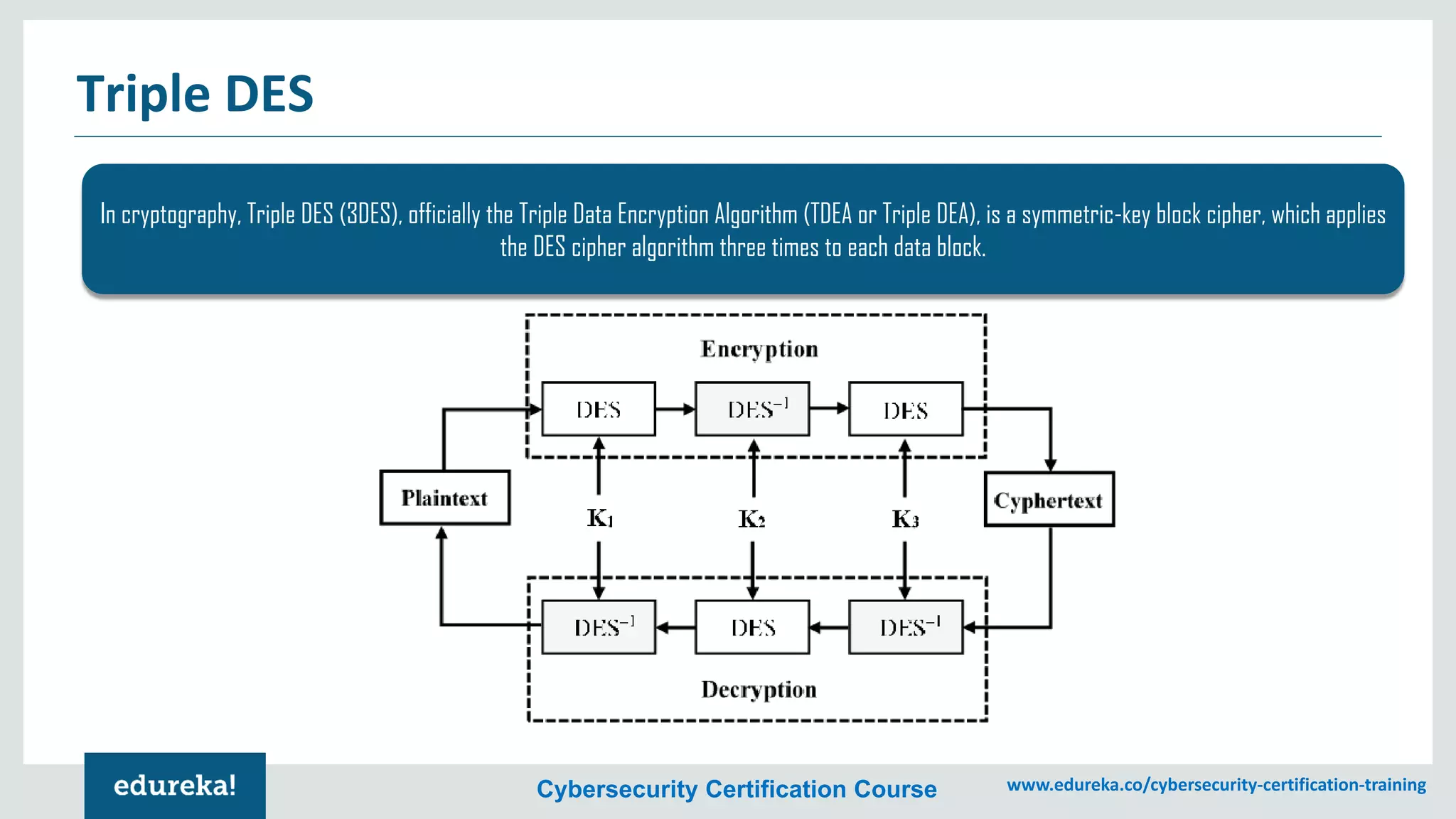
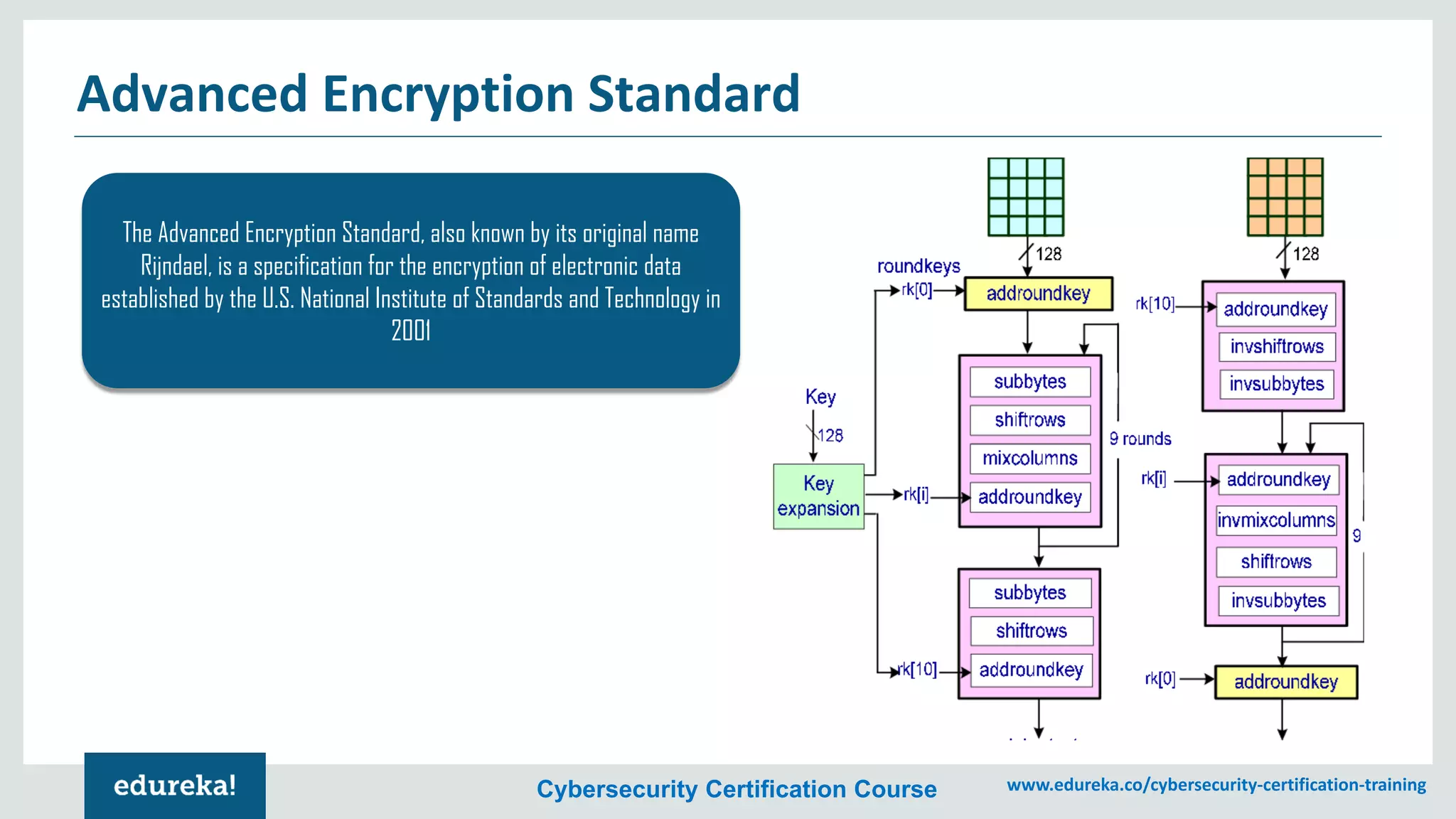
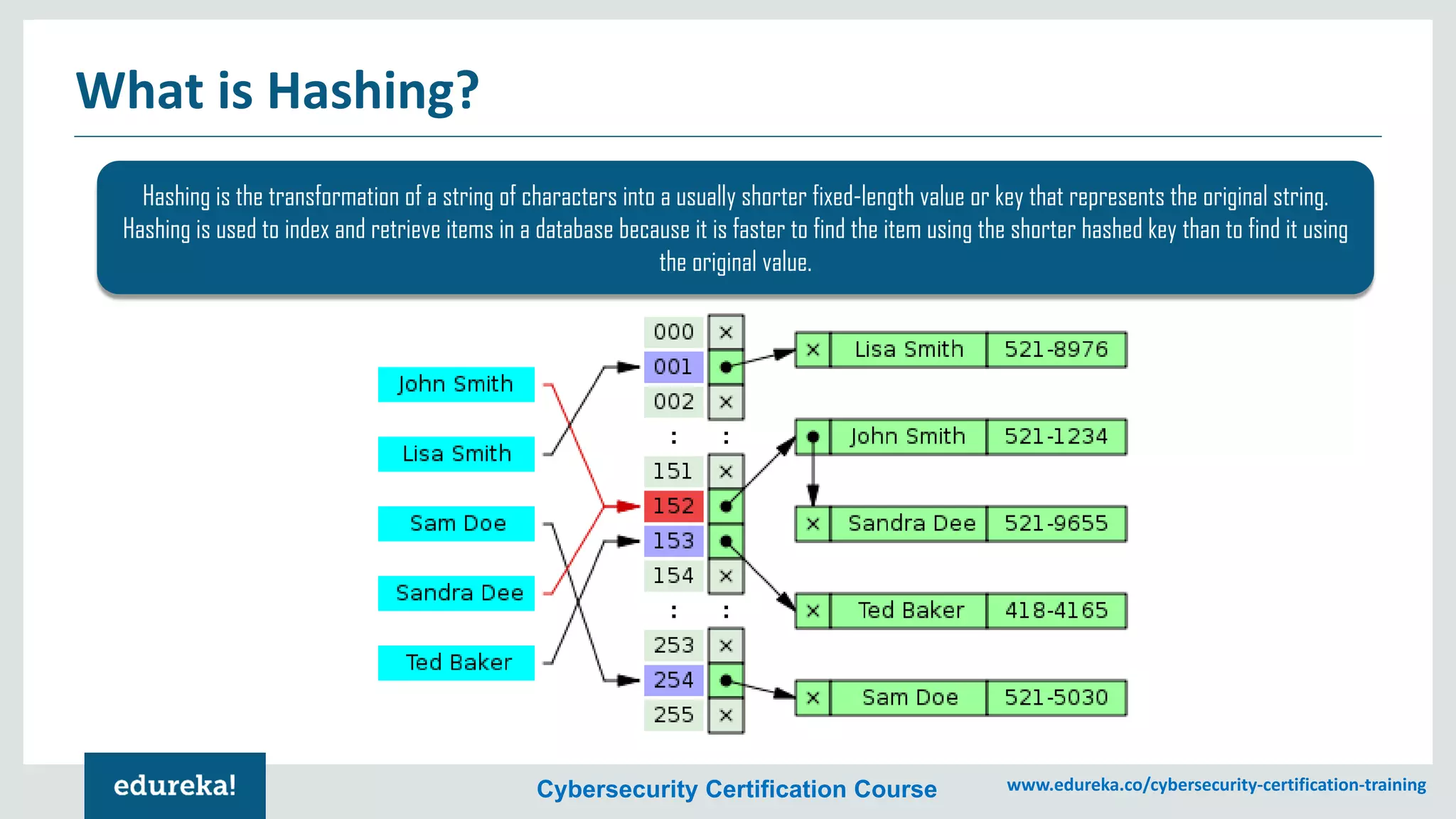
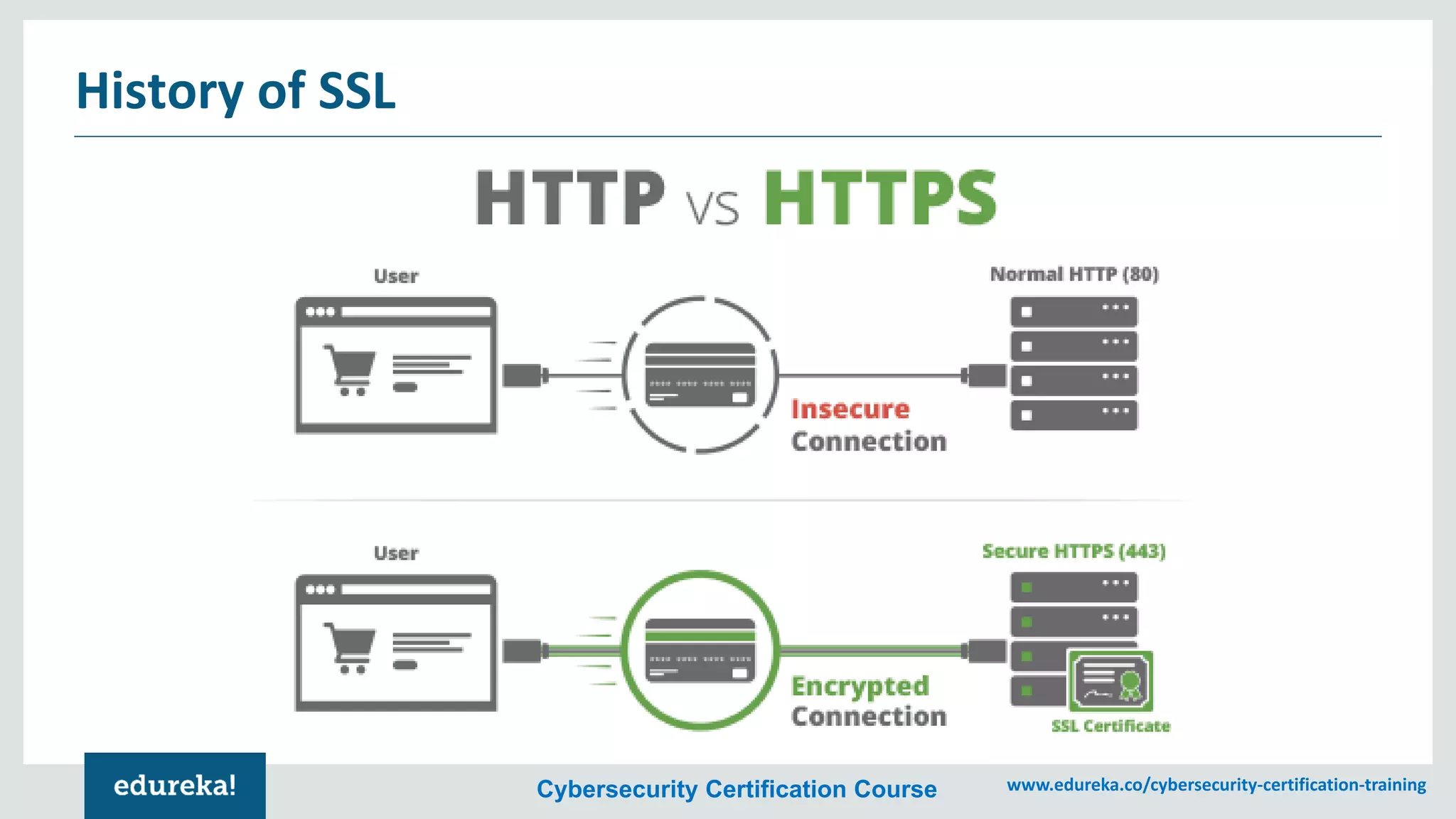
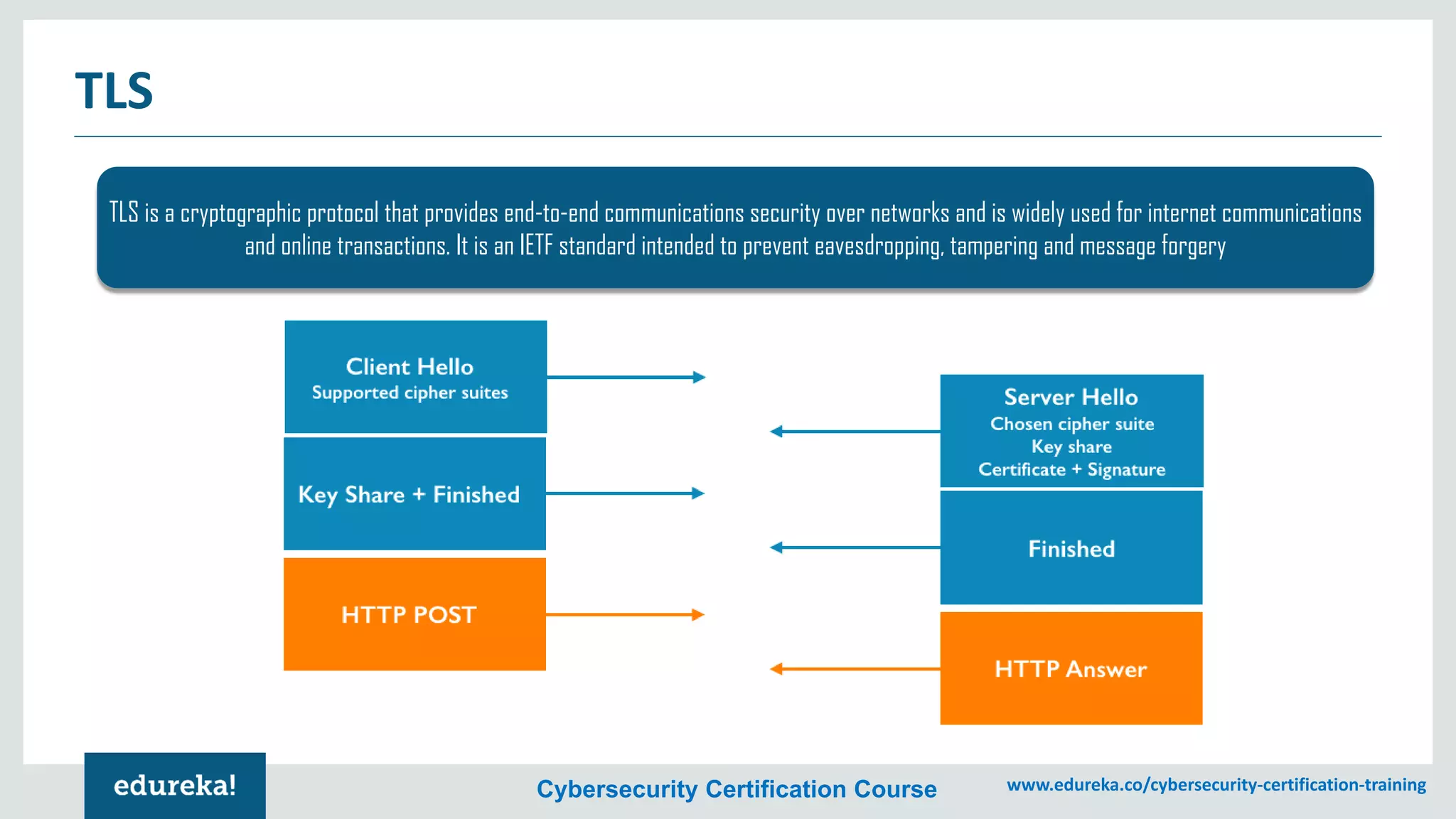
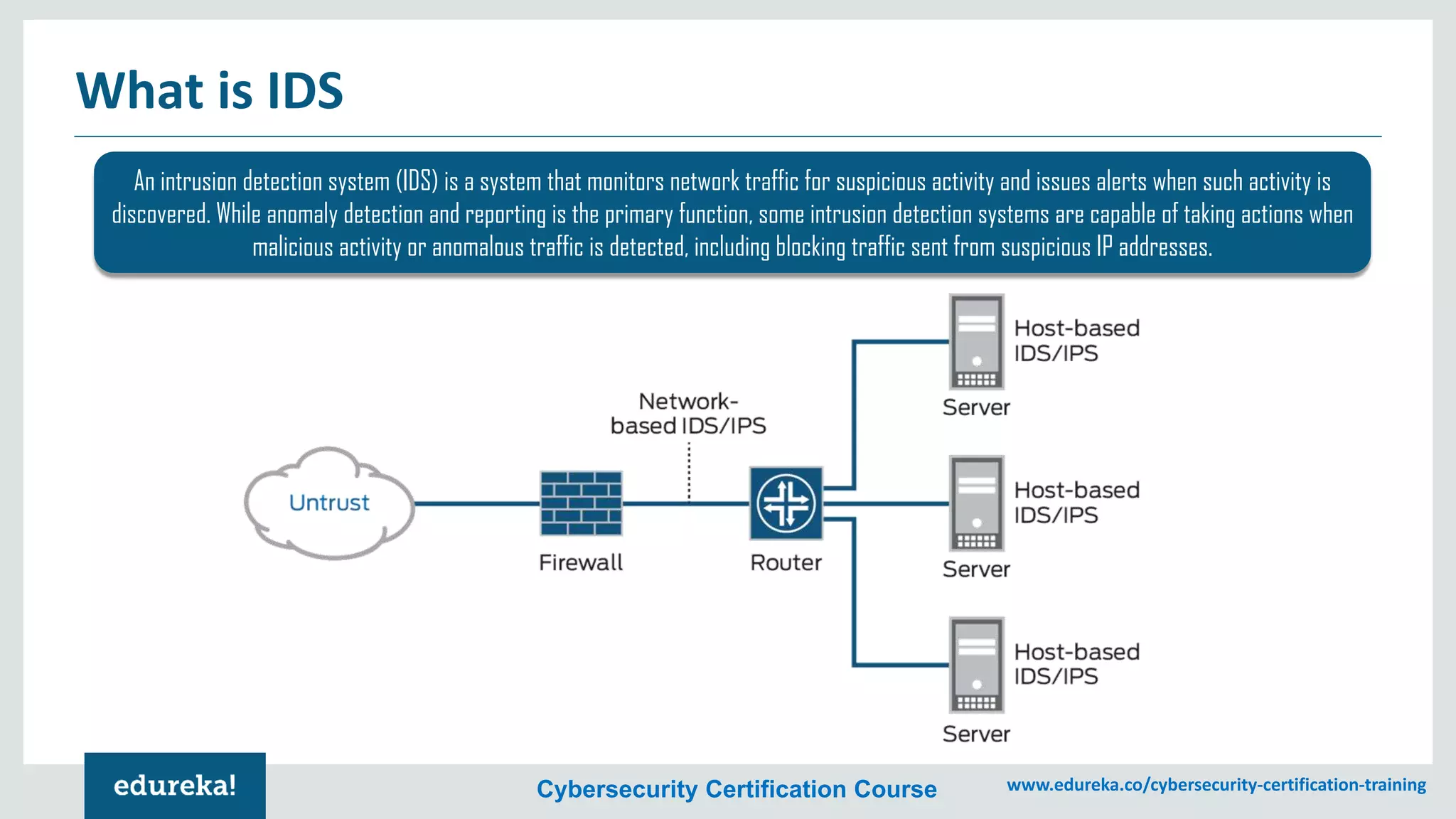
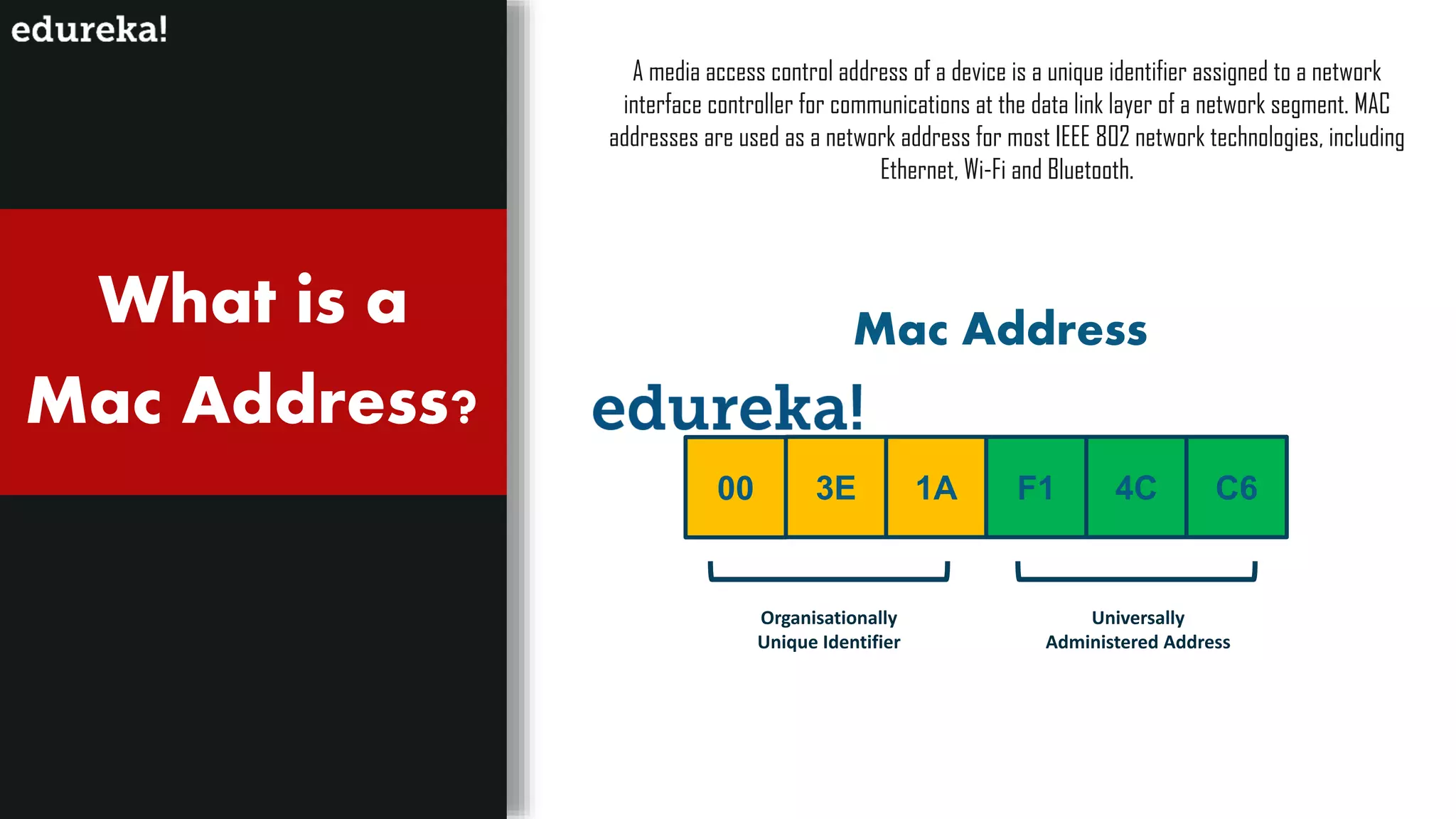
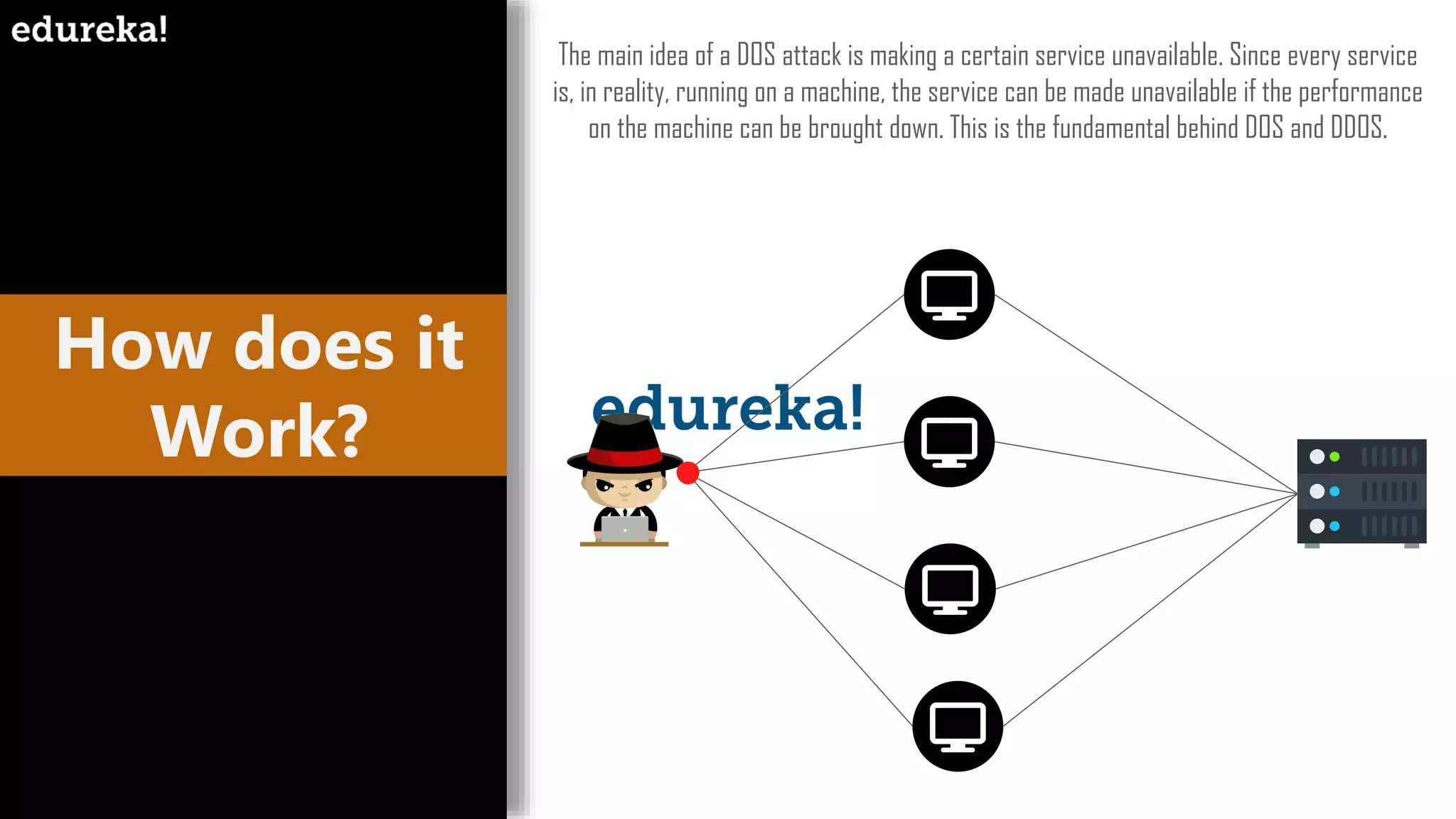
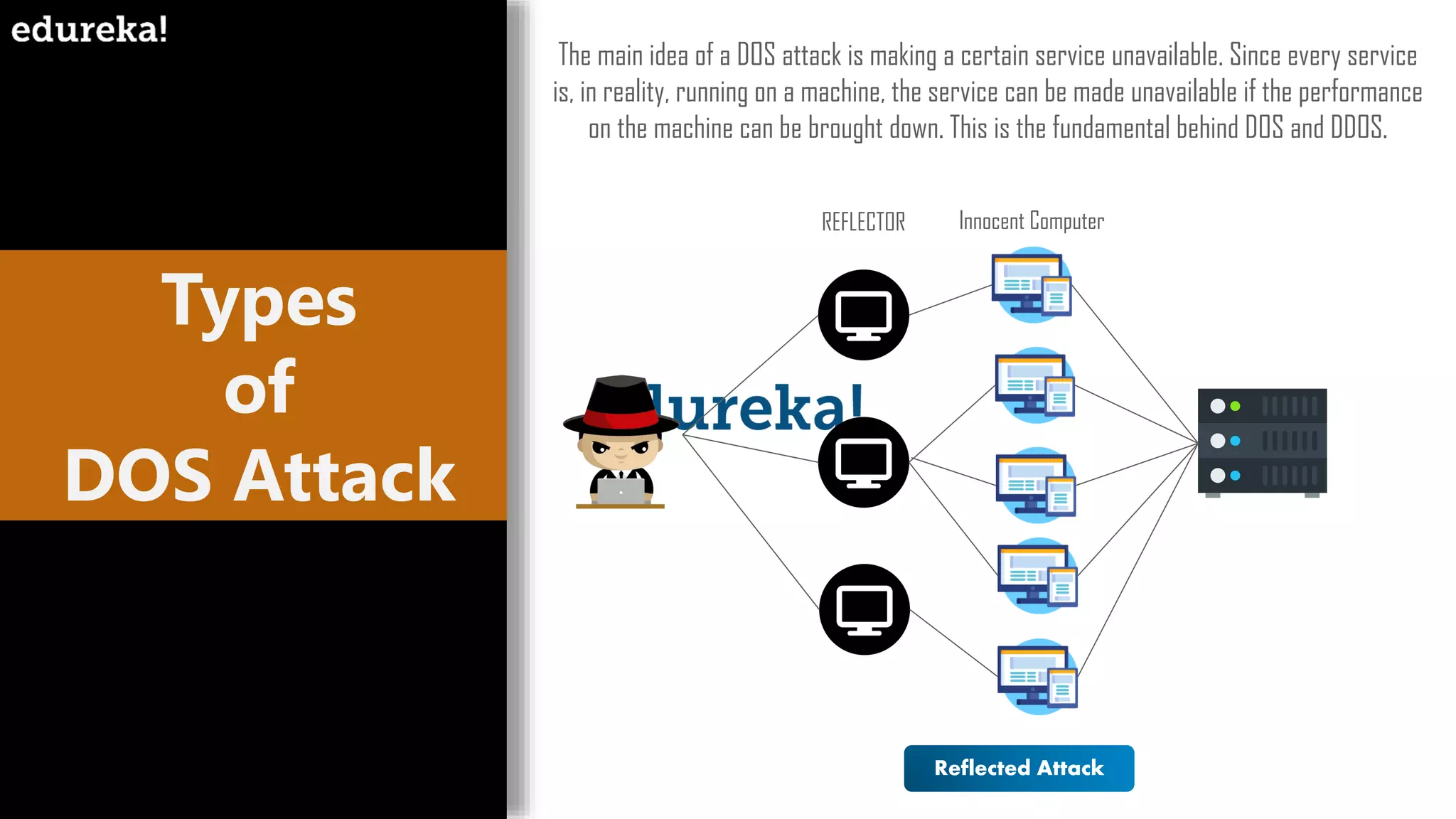
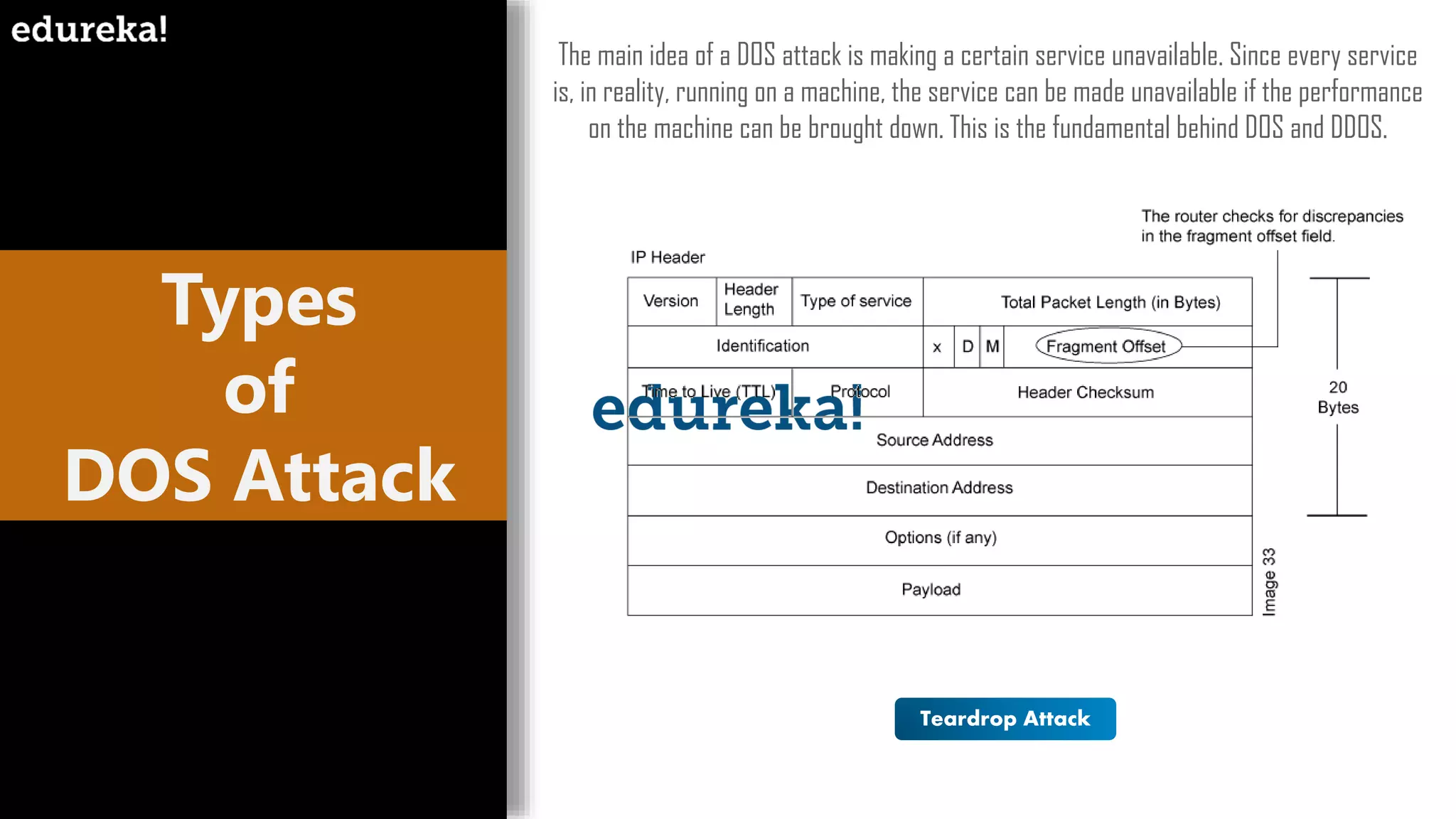
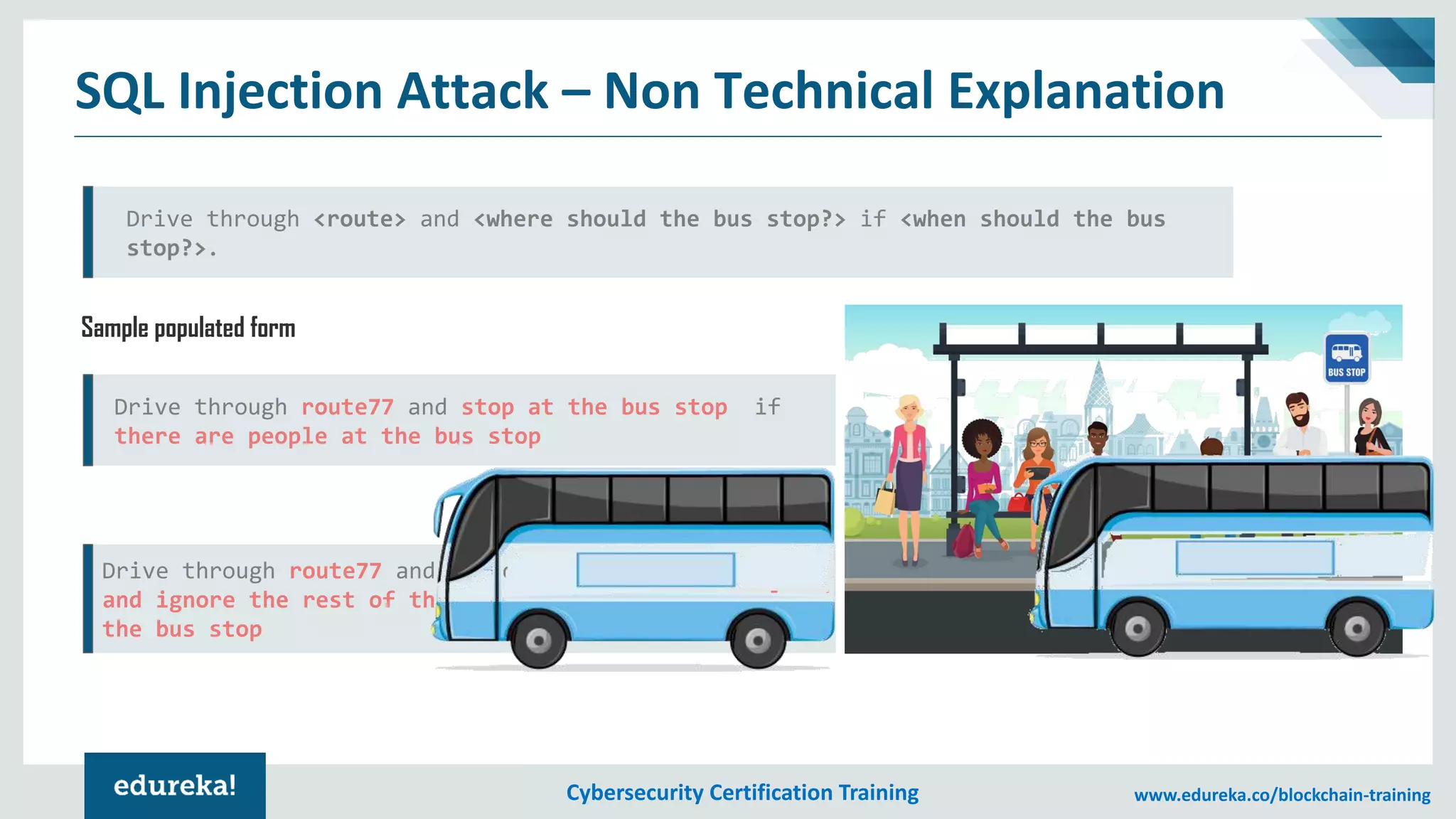
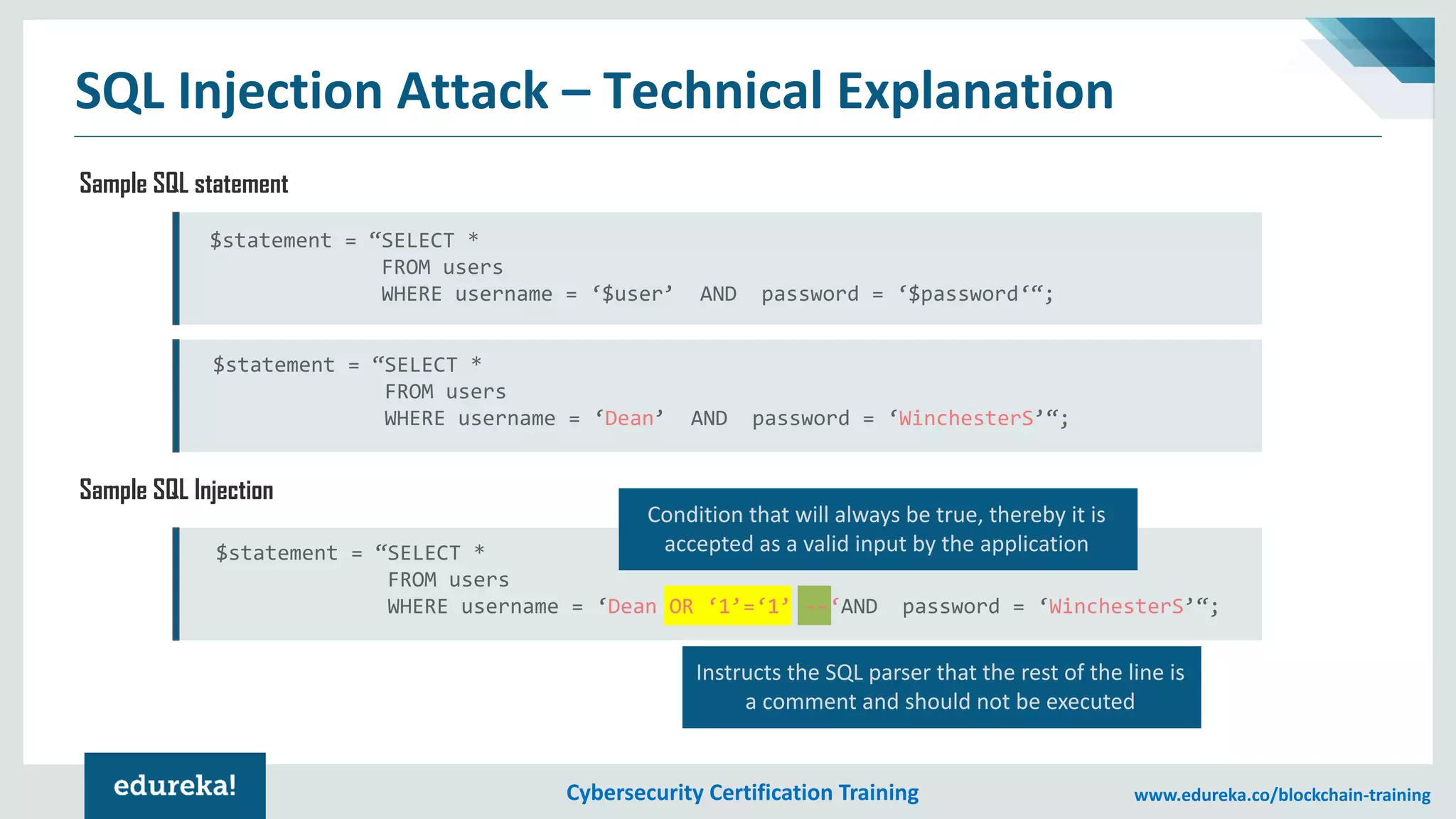
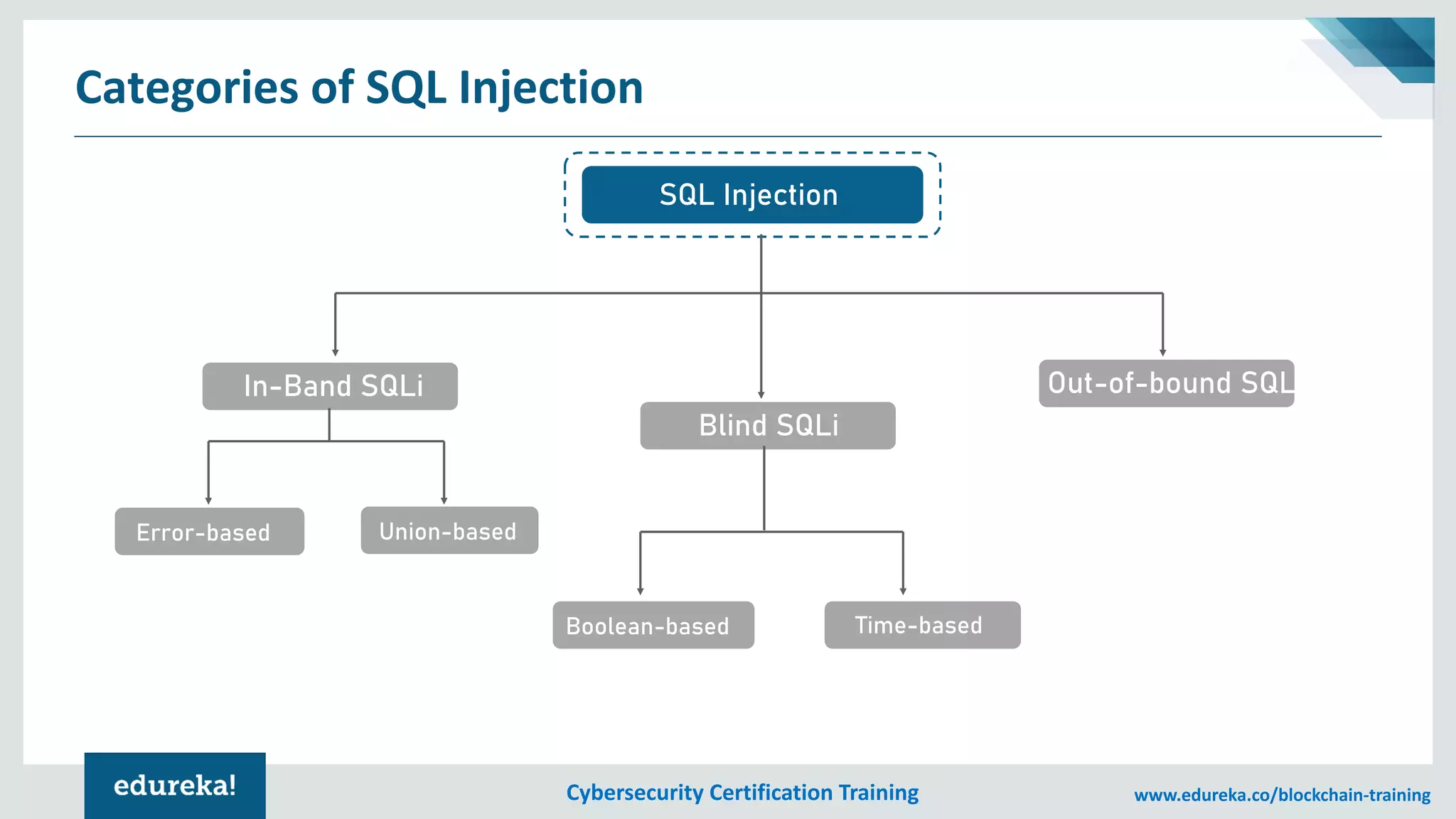
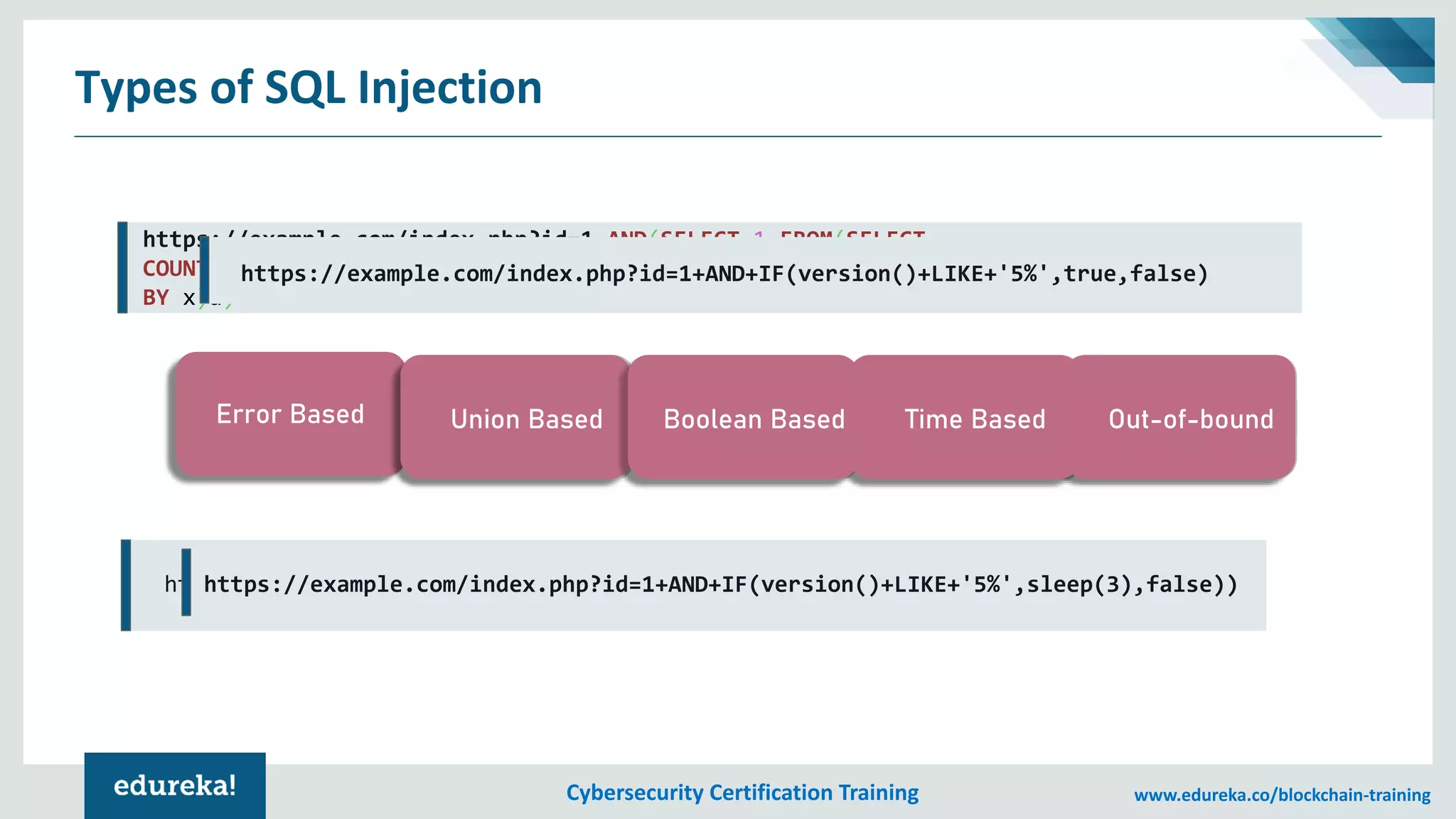
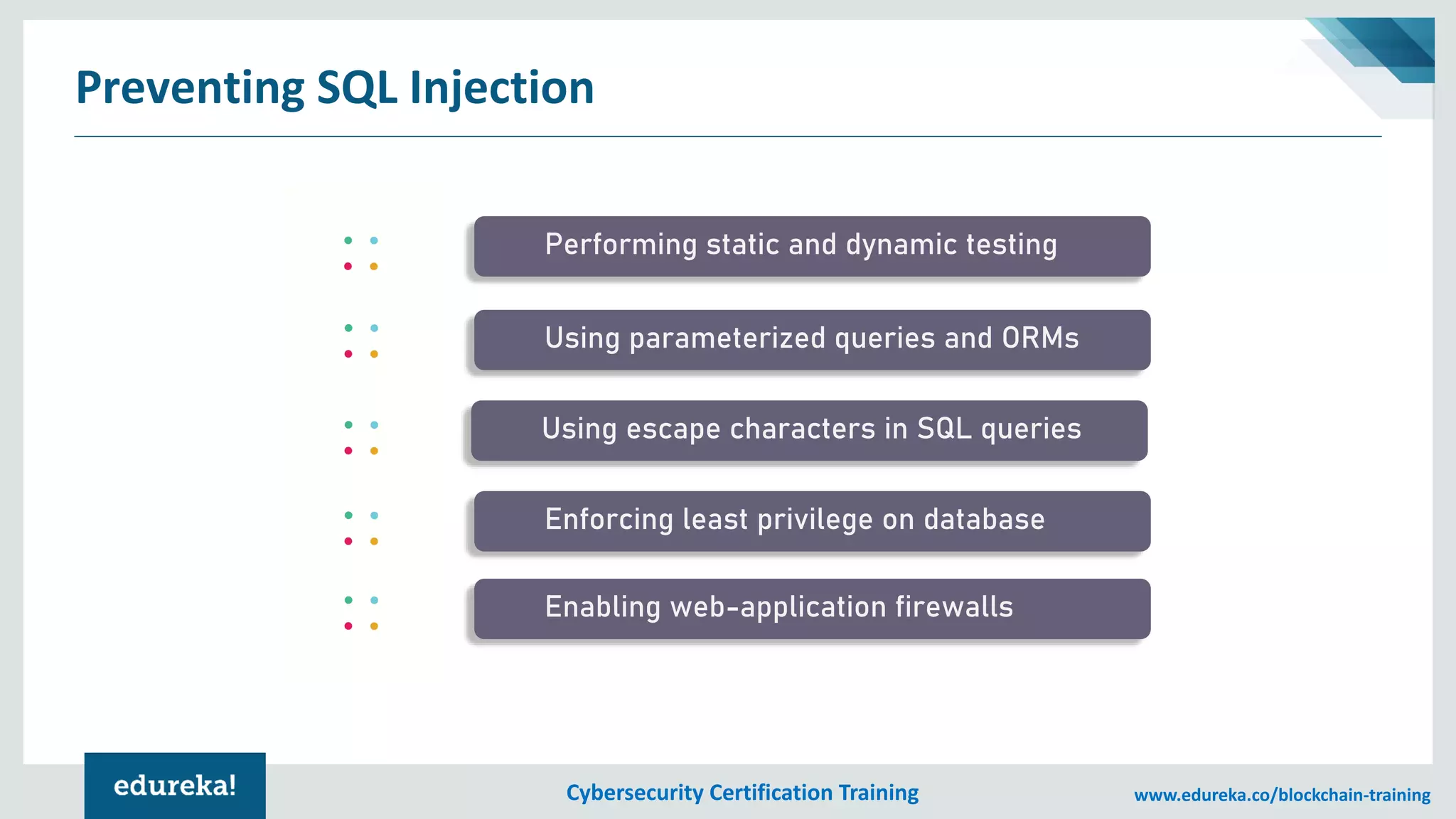
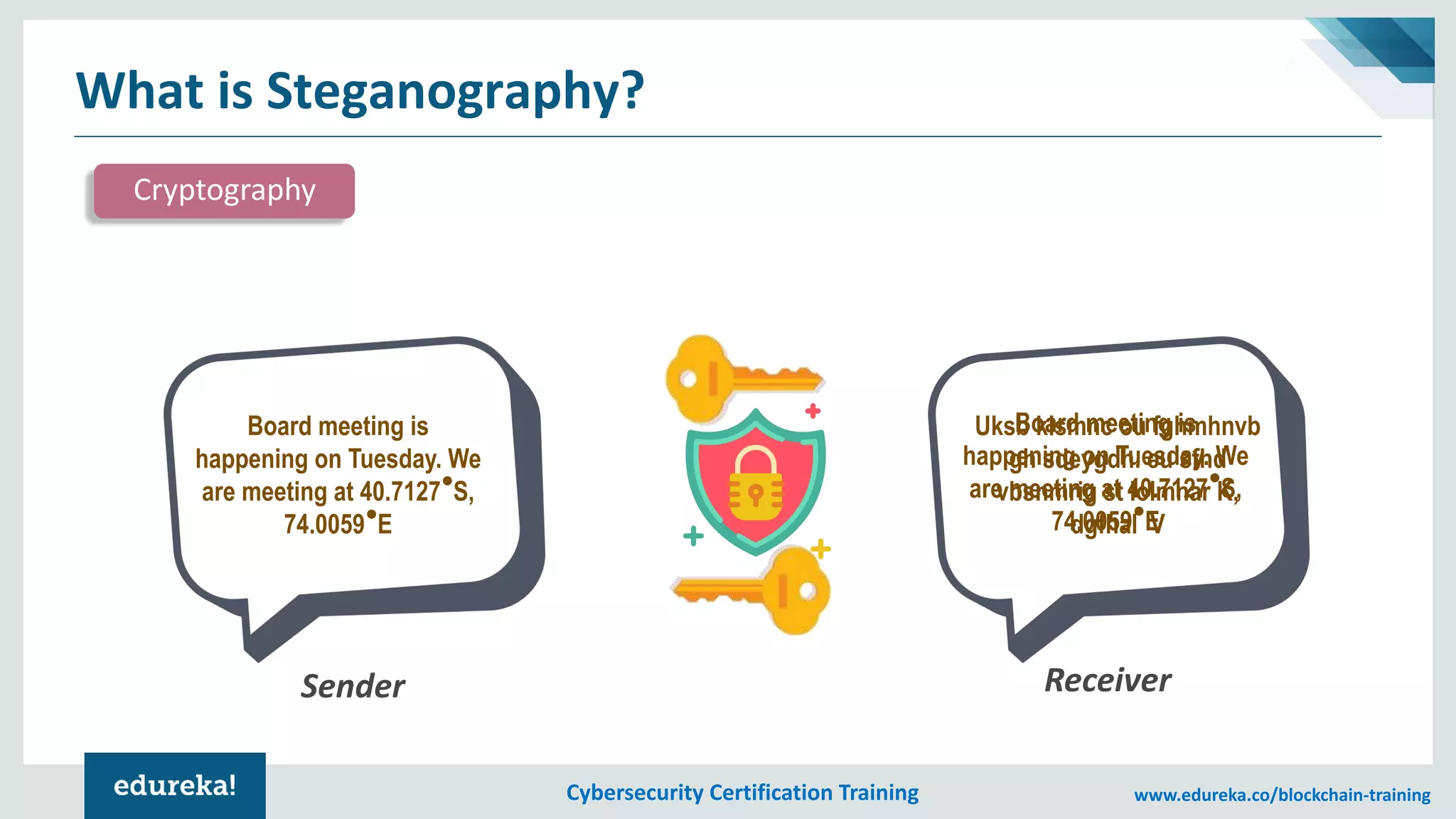
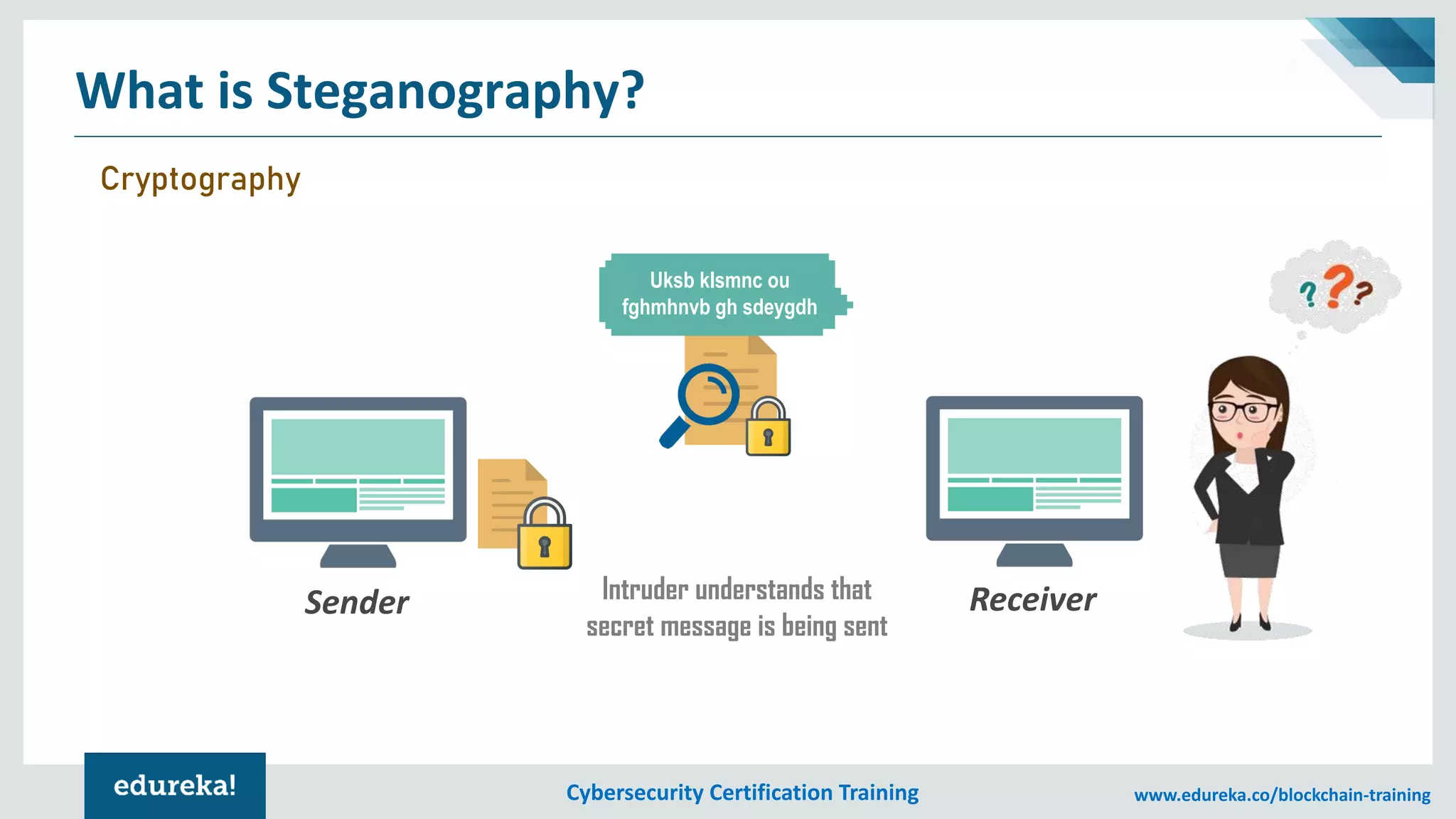
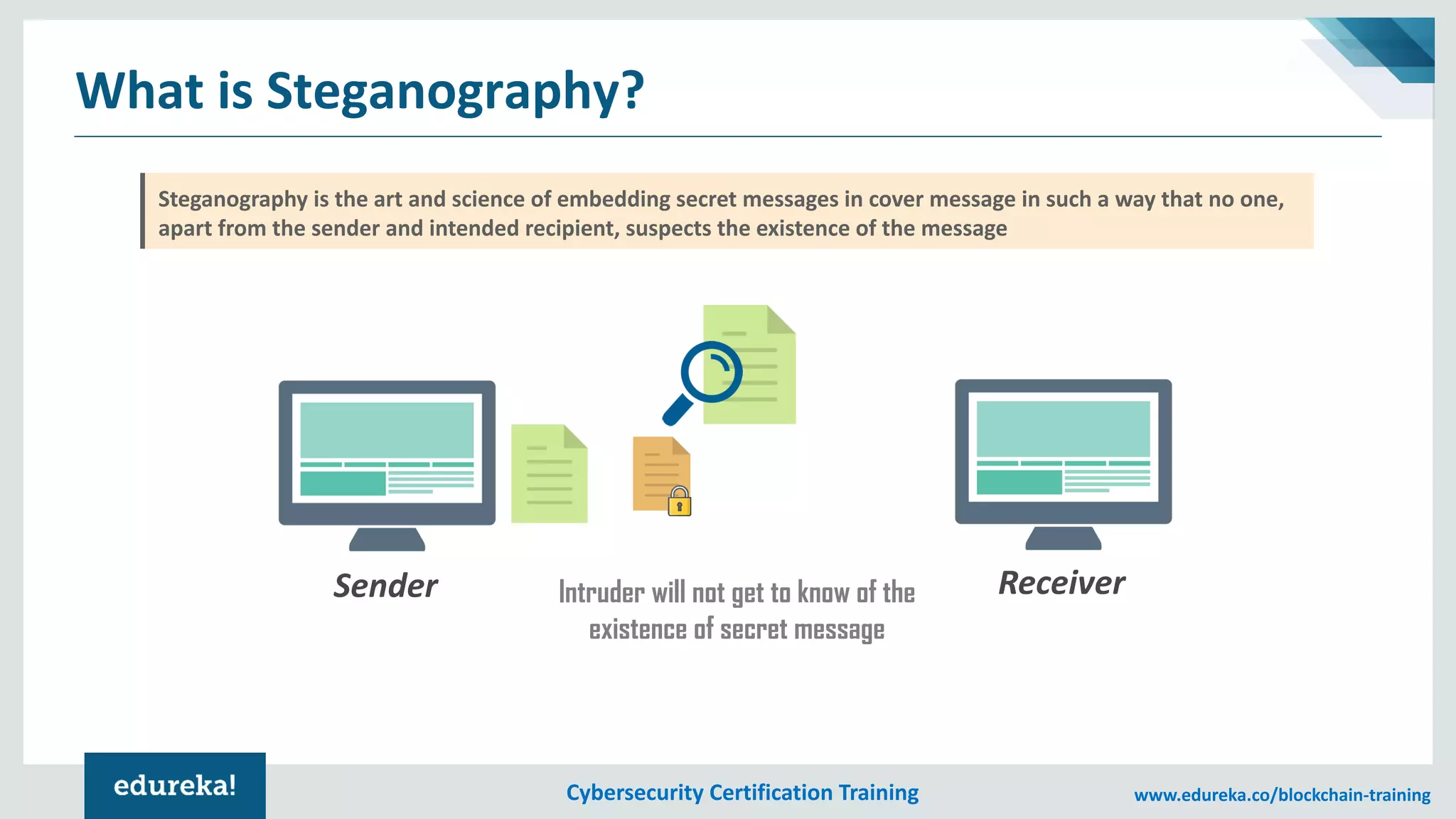
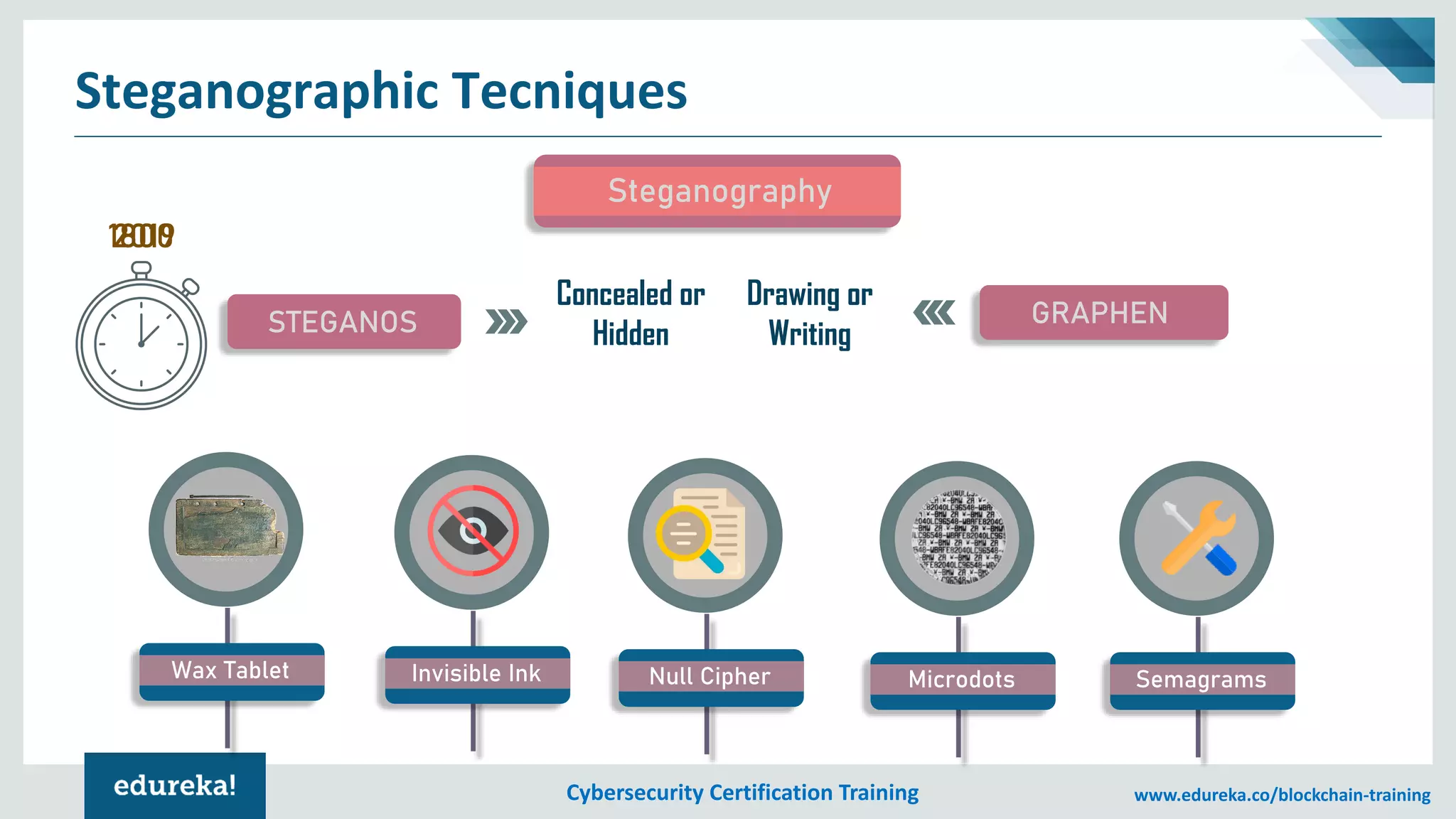
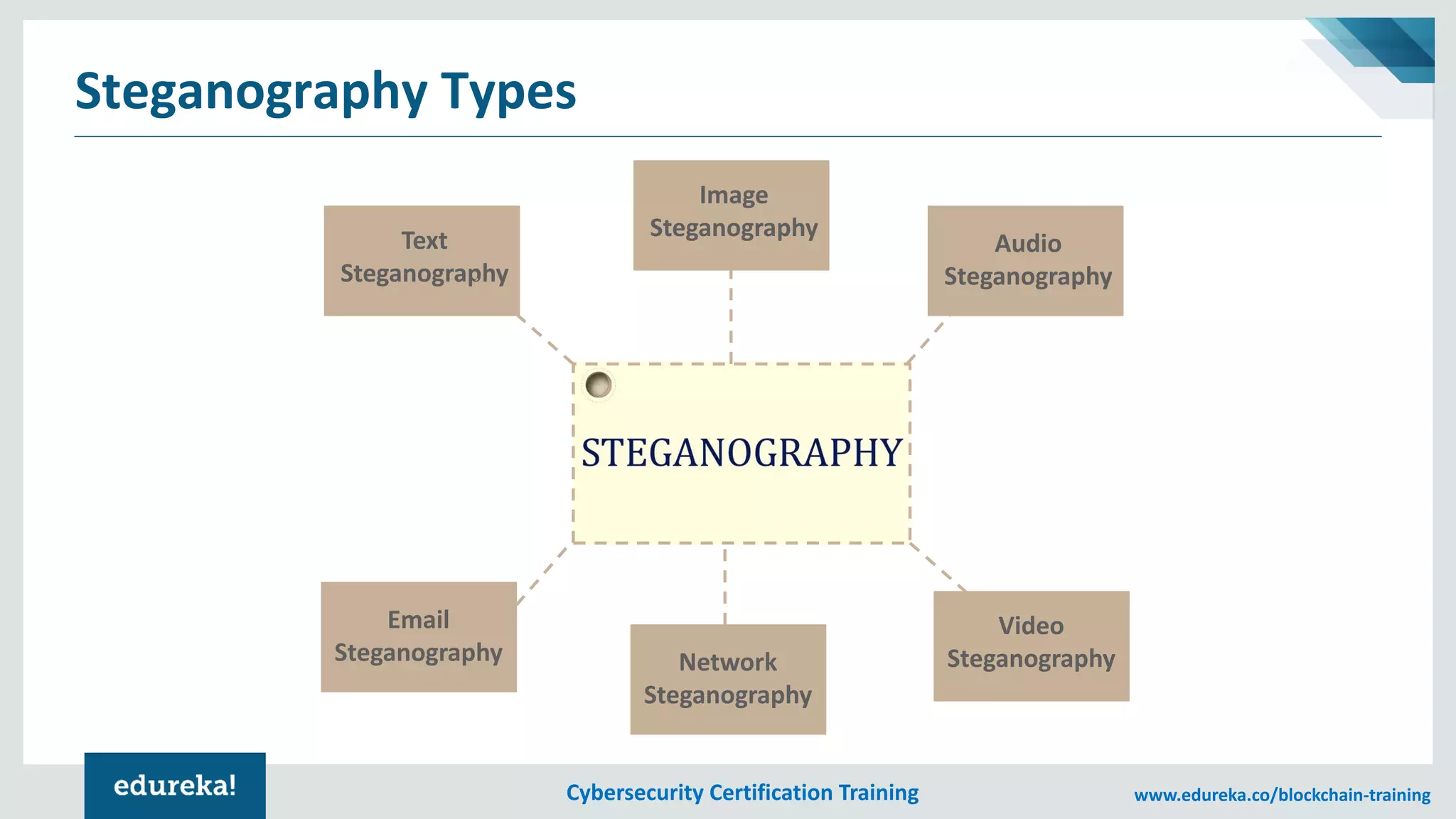
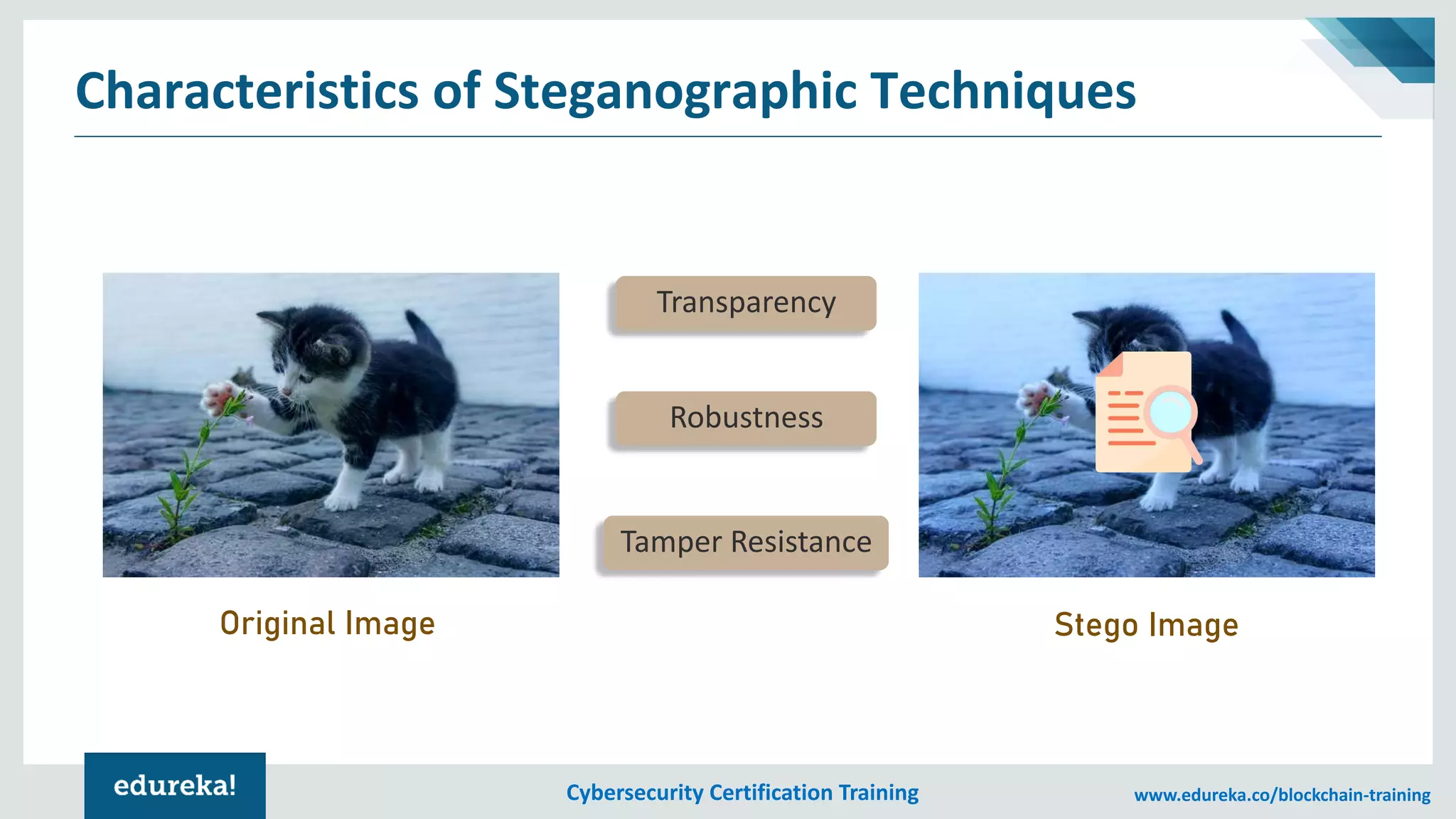
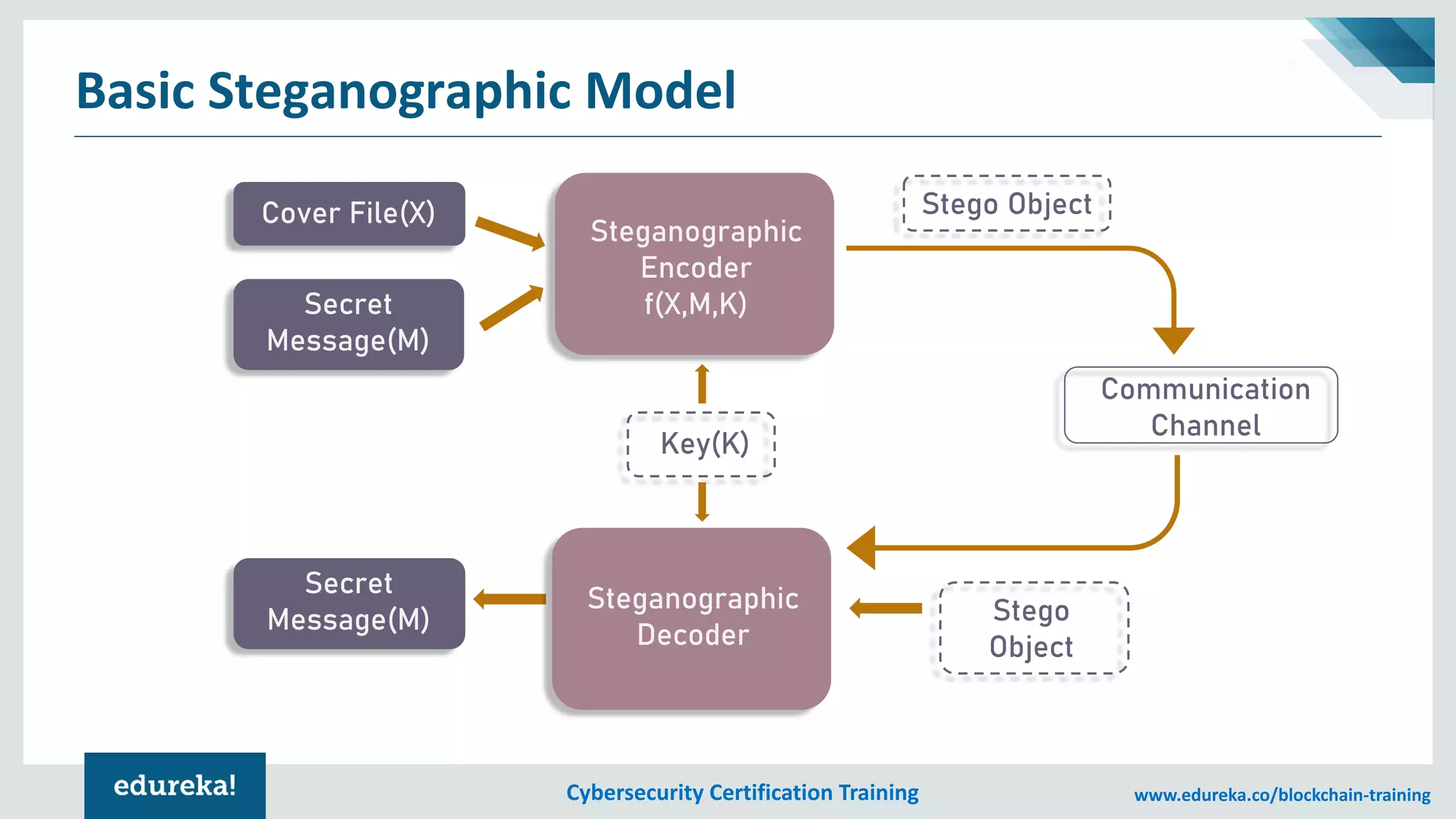
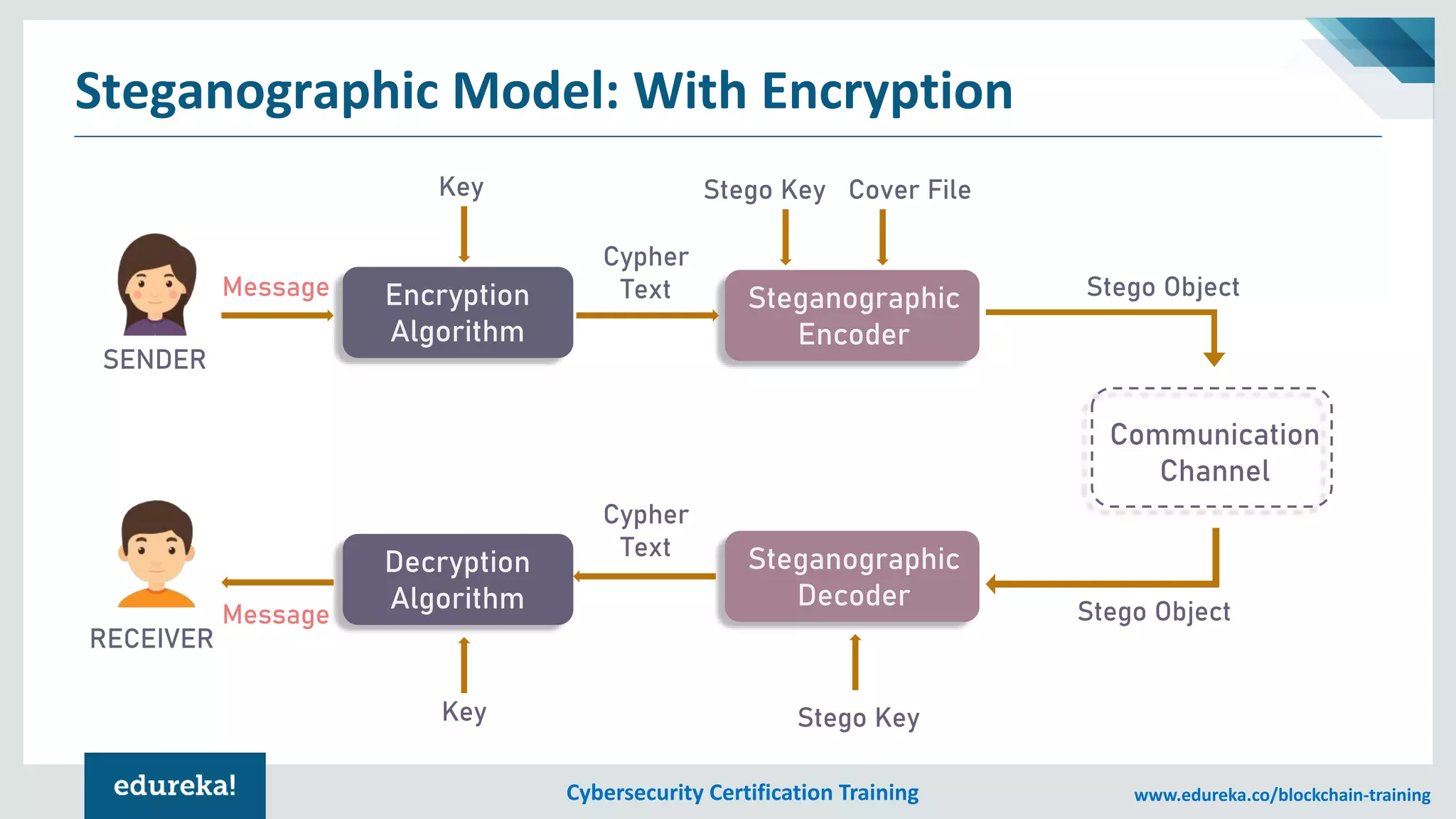
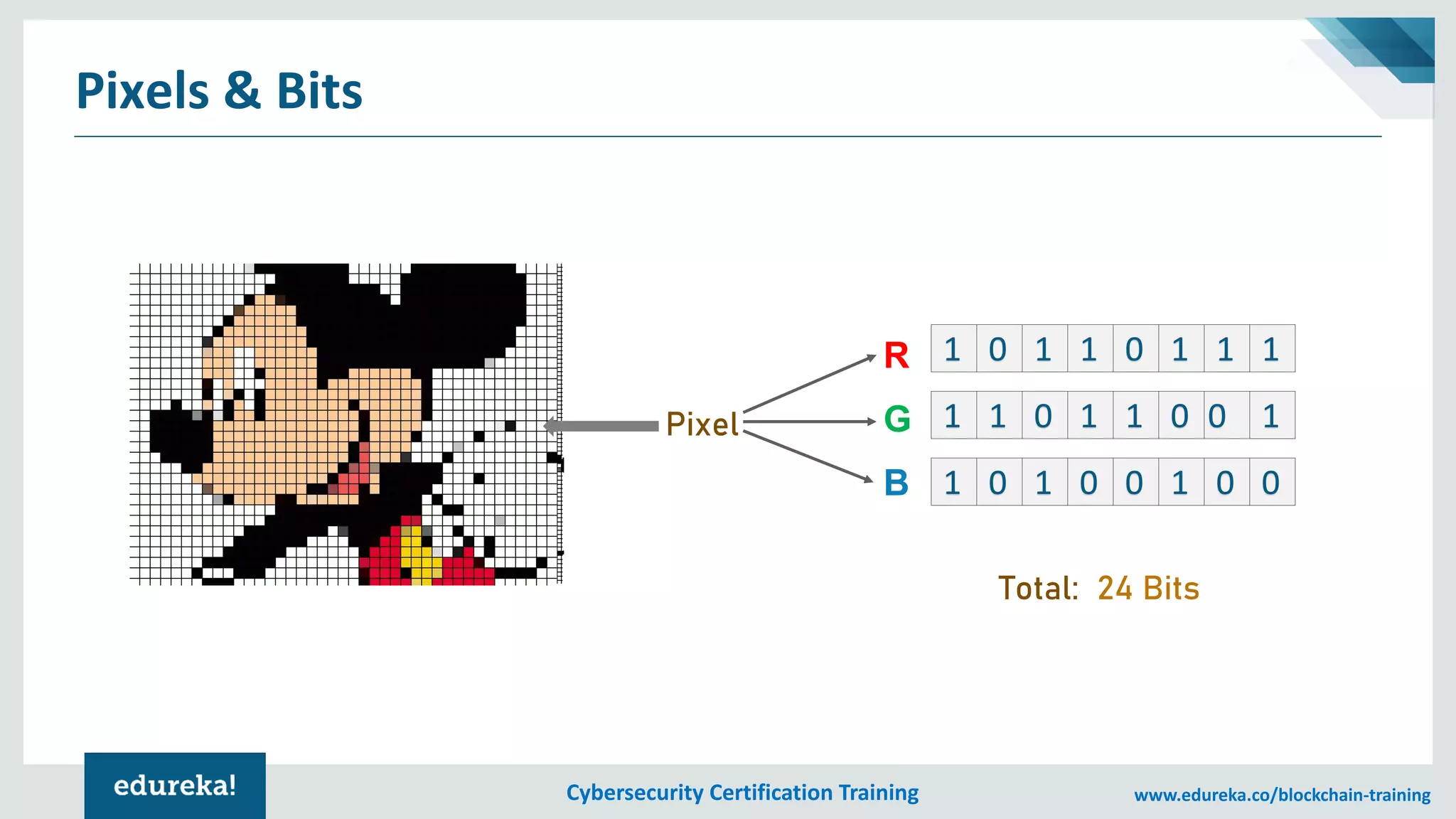
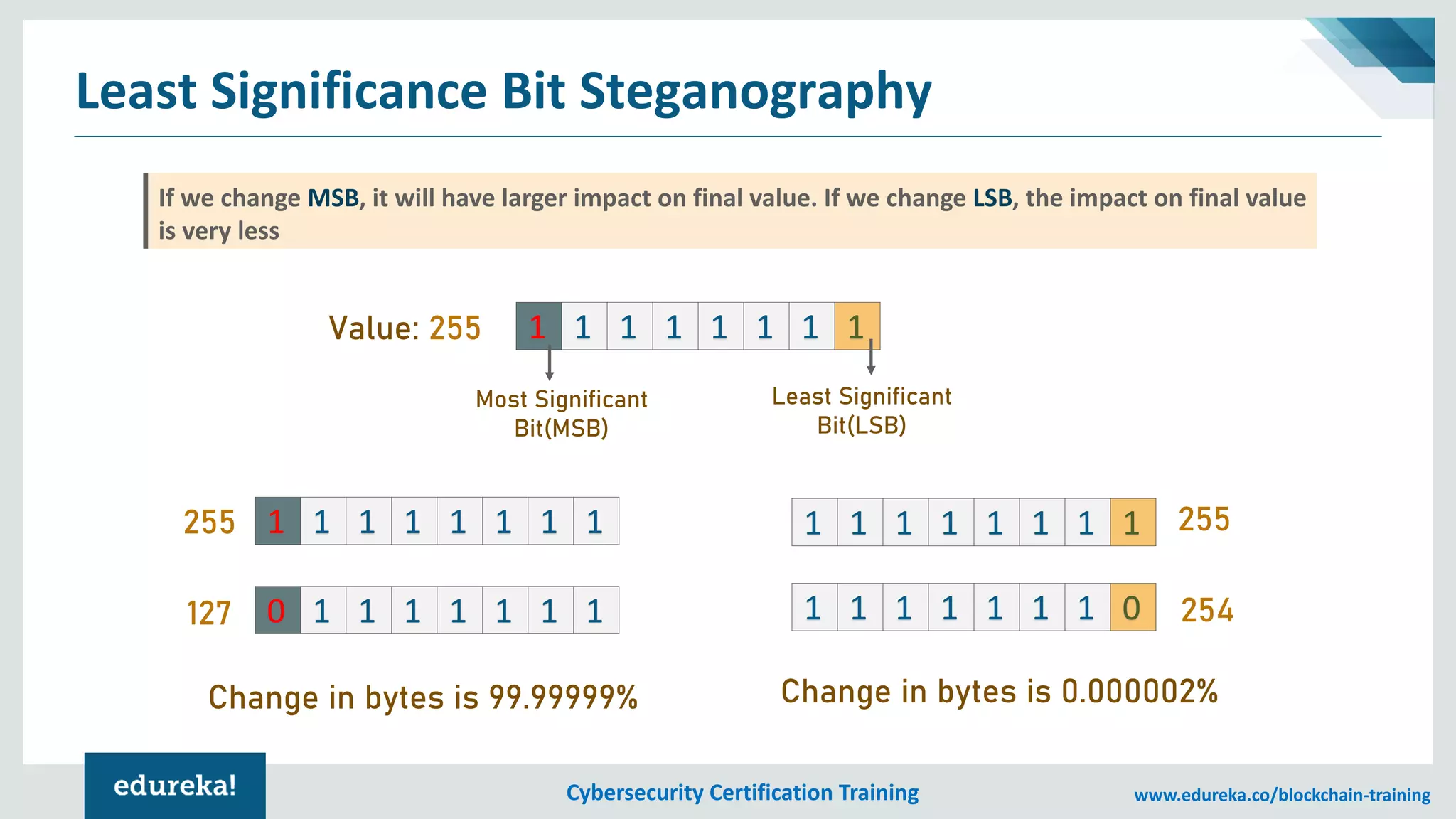
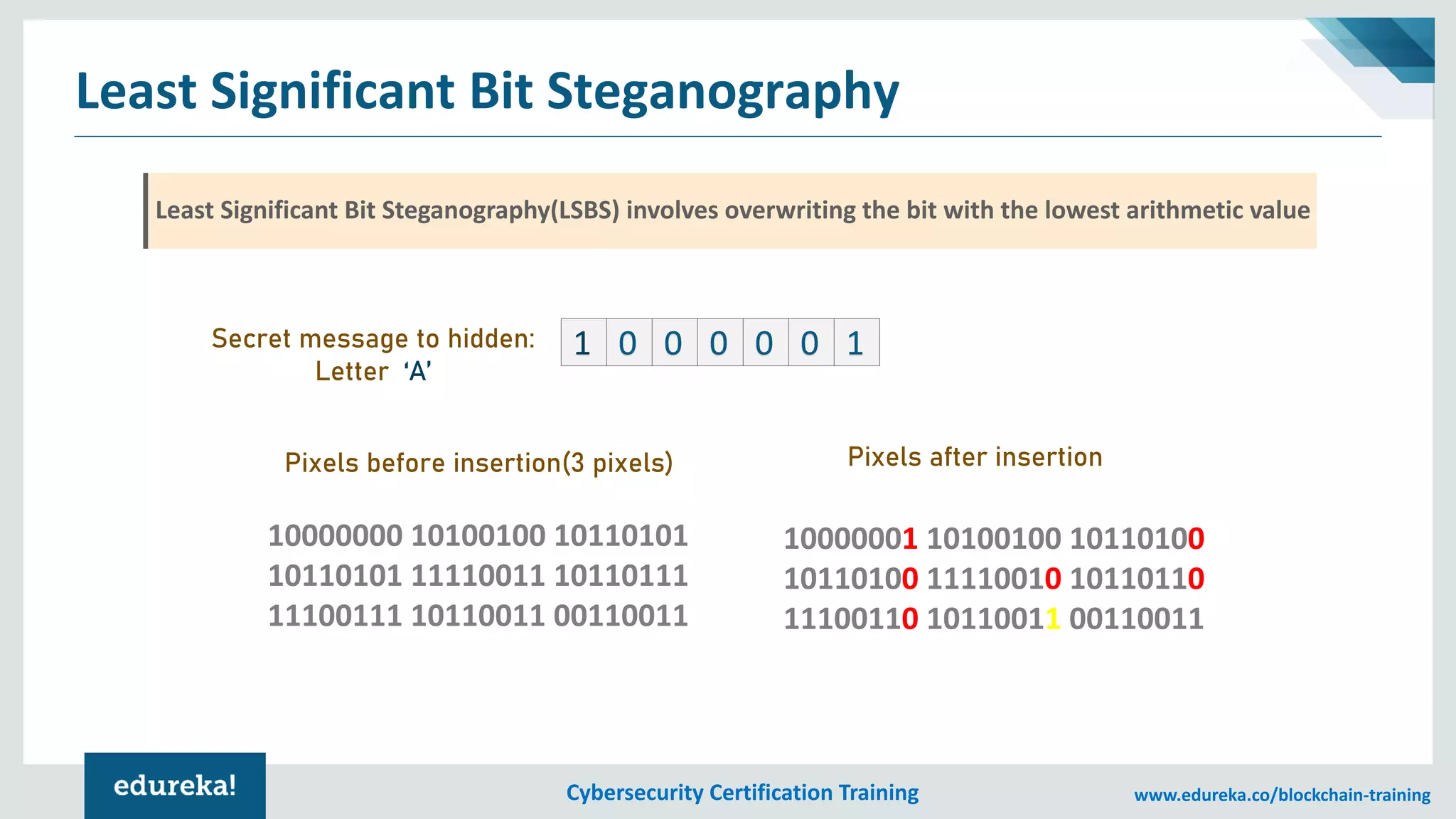
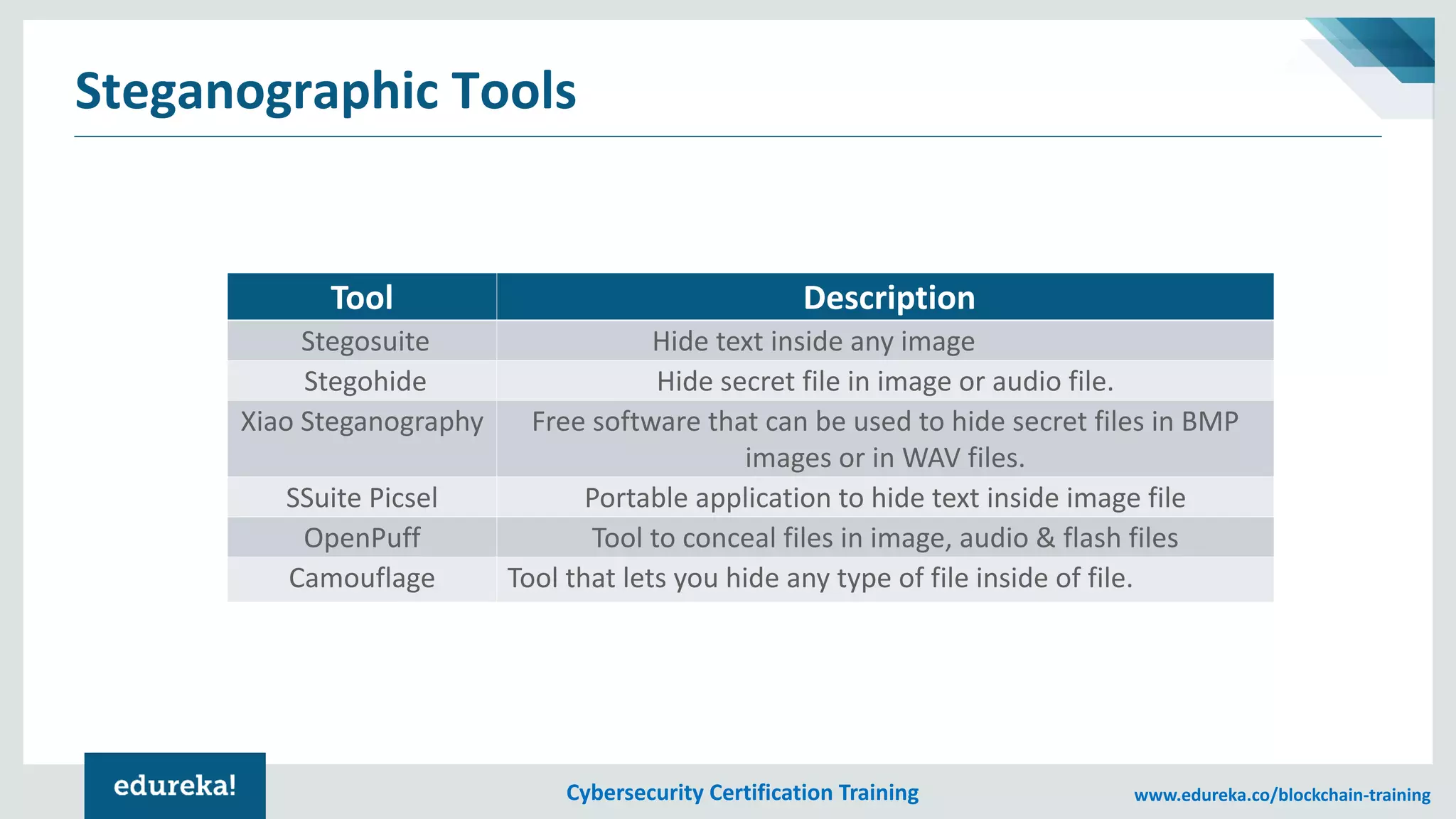
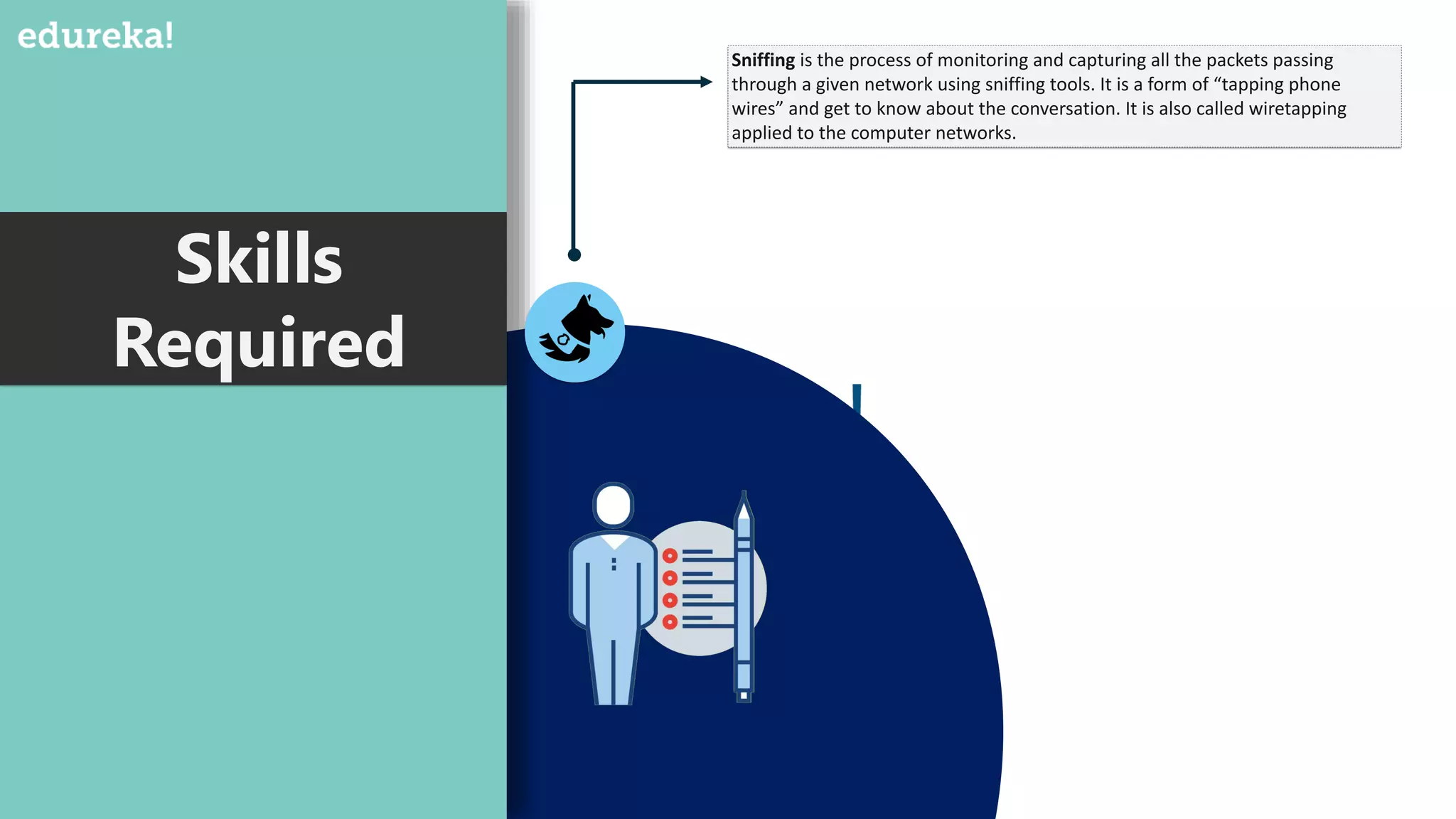
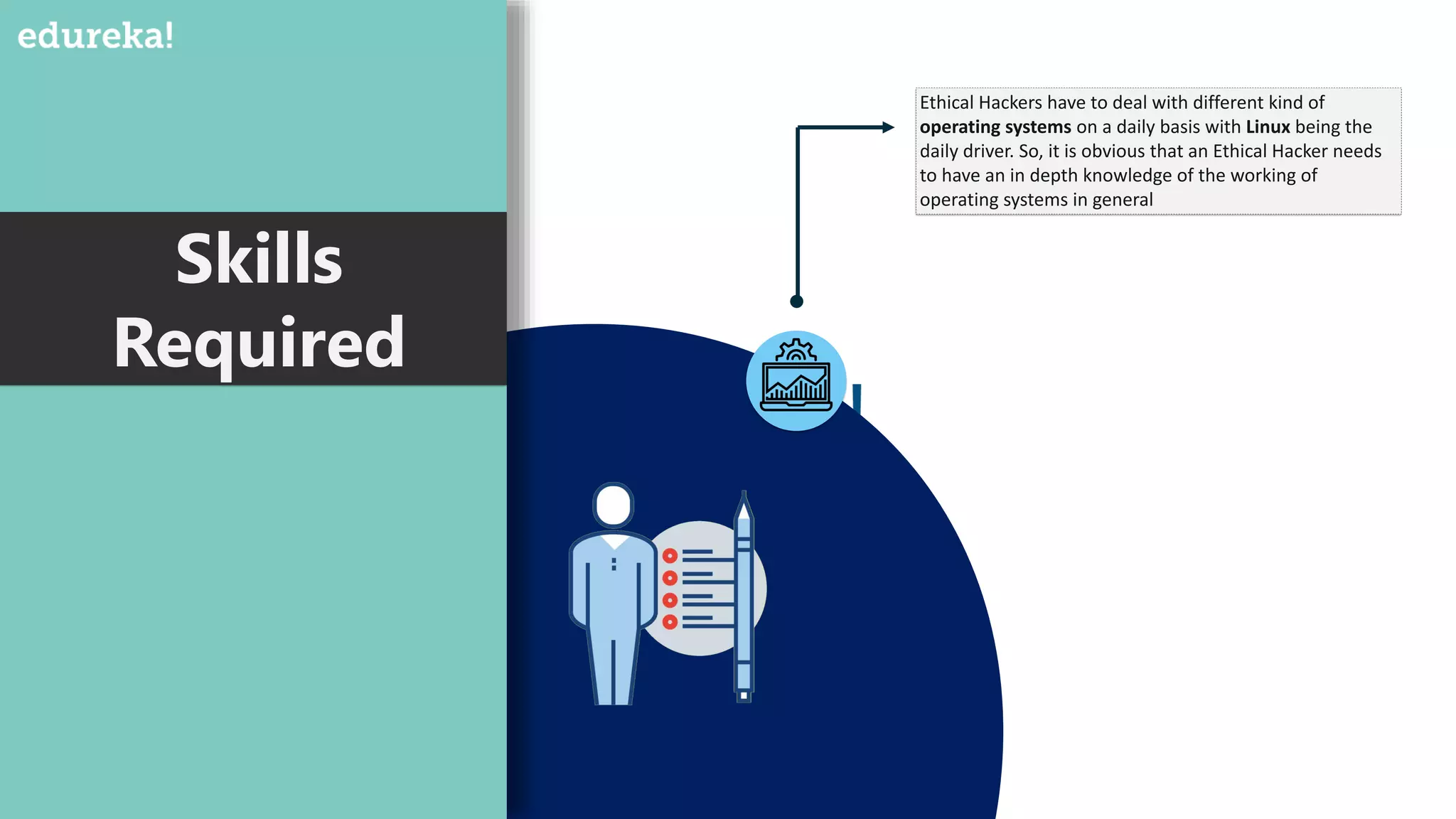
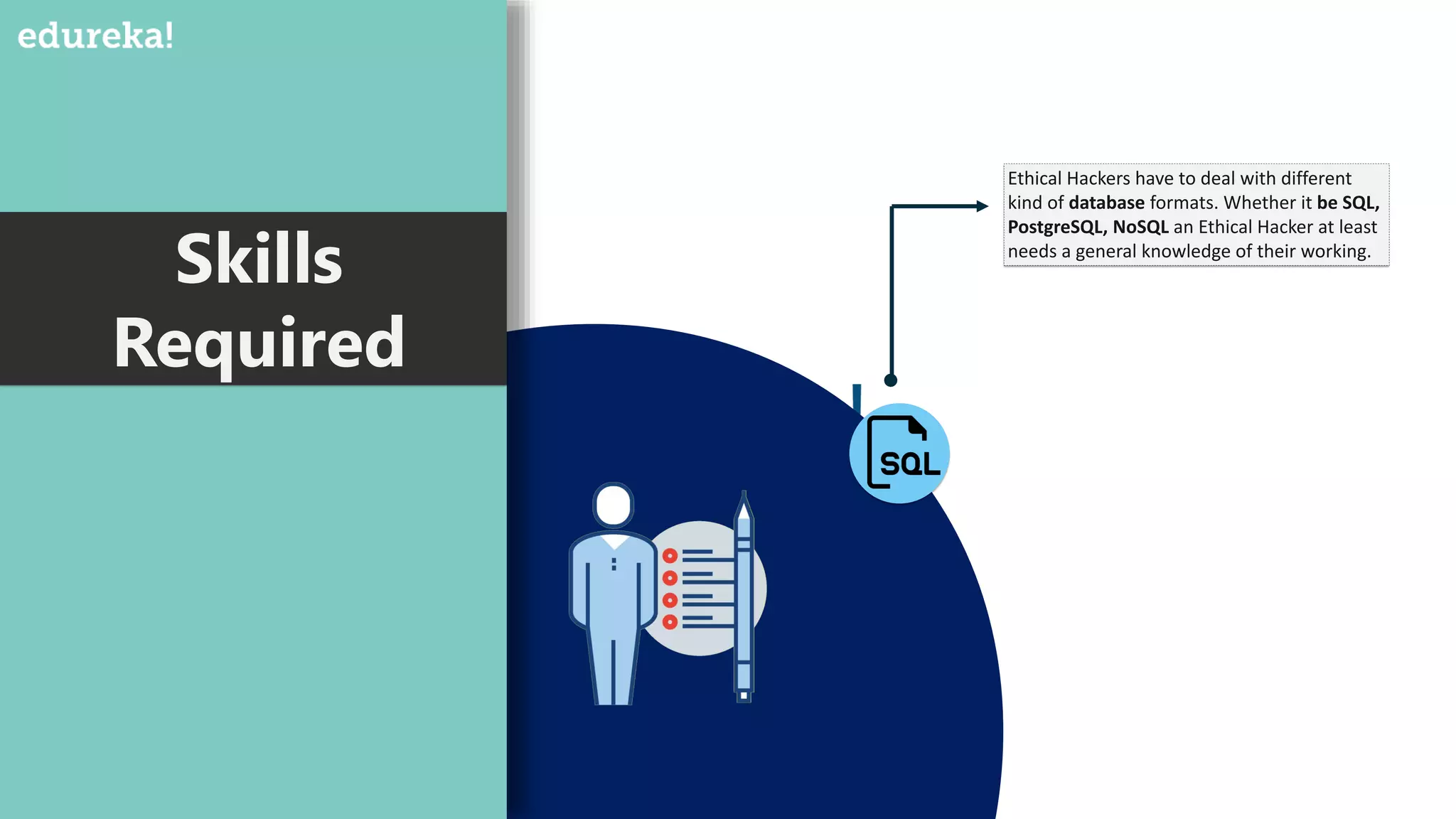
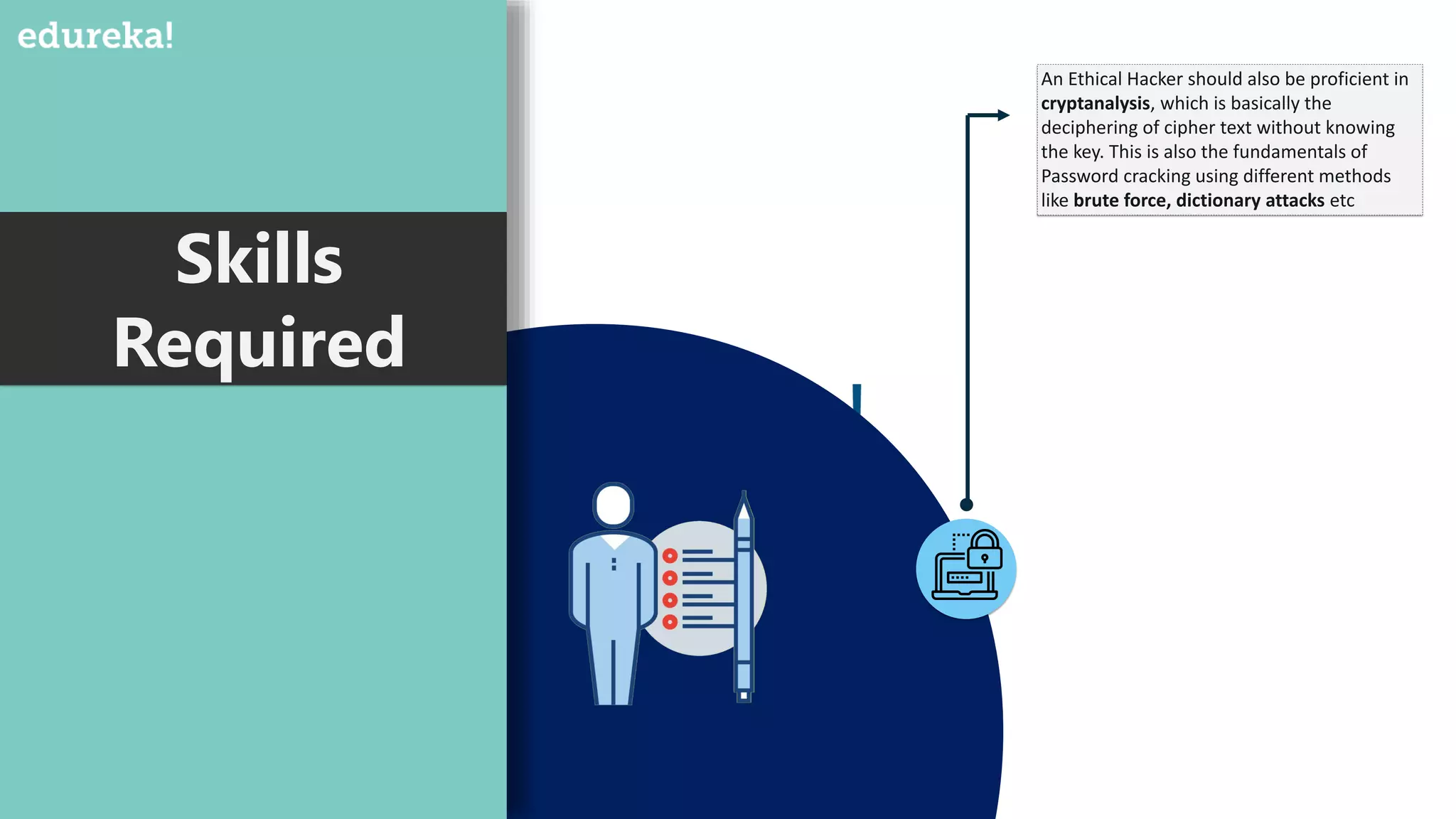
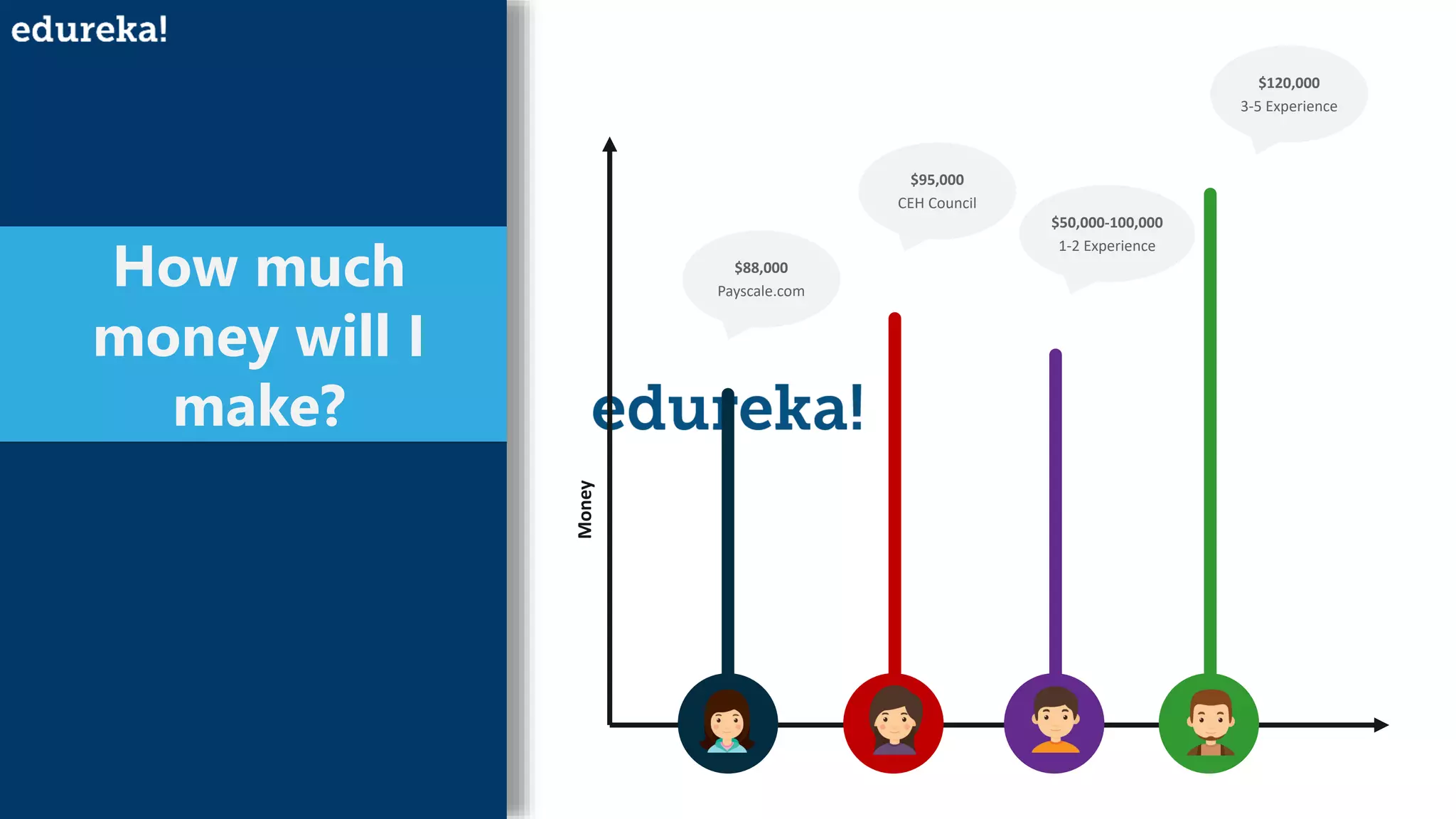
The document provides an overview of cybersecurity, including the importance of cyber protection, the CIA triad (confidentiality, integrity, availability), and various types of cyber threats such as phishing, malware, and DDoS attacks. It also discusses cybersecurity strategies, the role of cryptography, and different algorithms for secure communication. Lastly, the content emphasizes the need for risk management and vigilance against evolving cyber threats.