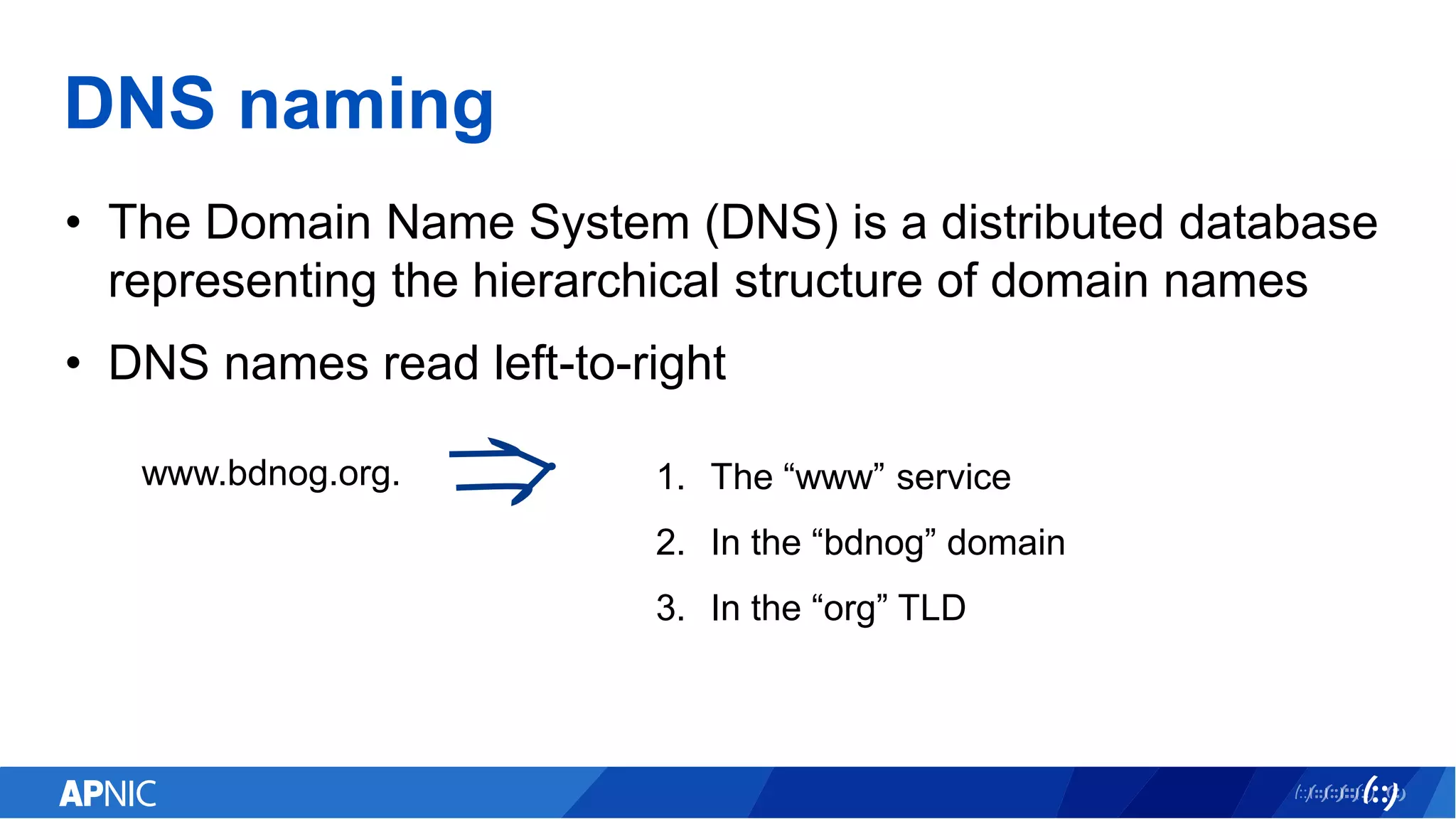
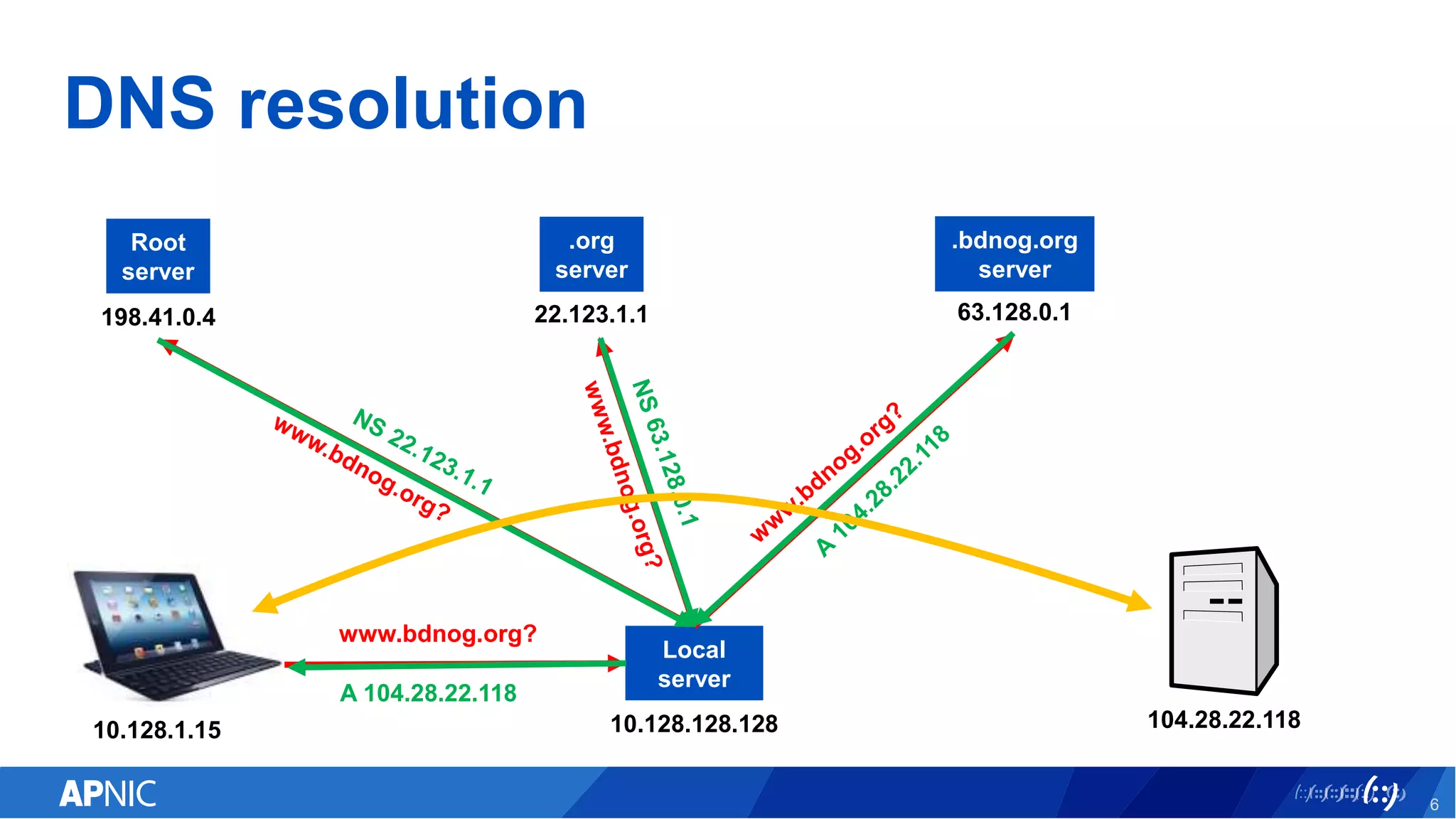
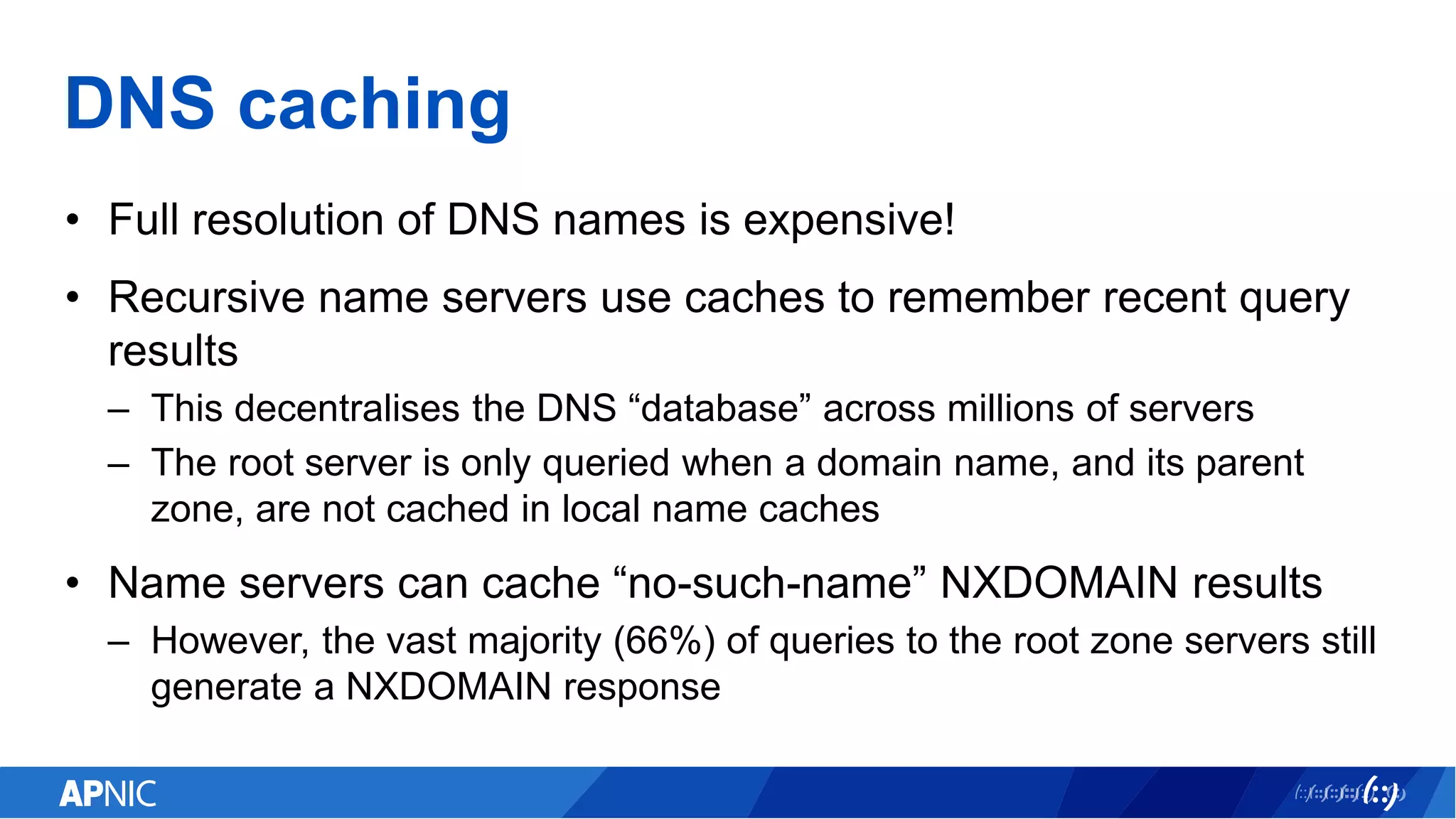
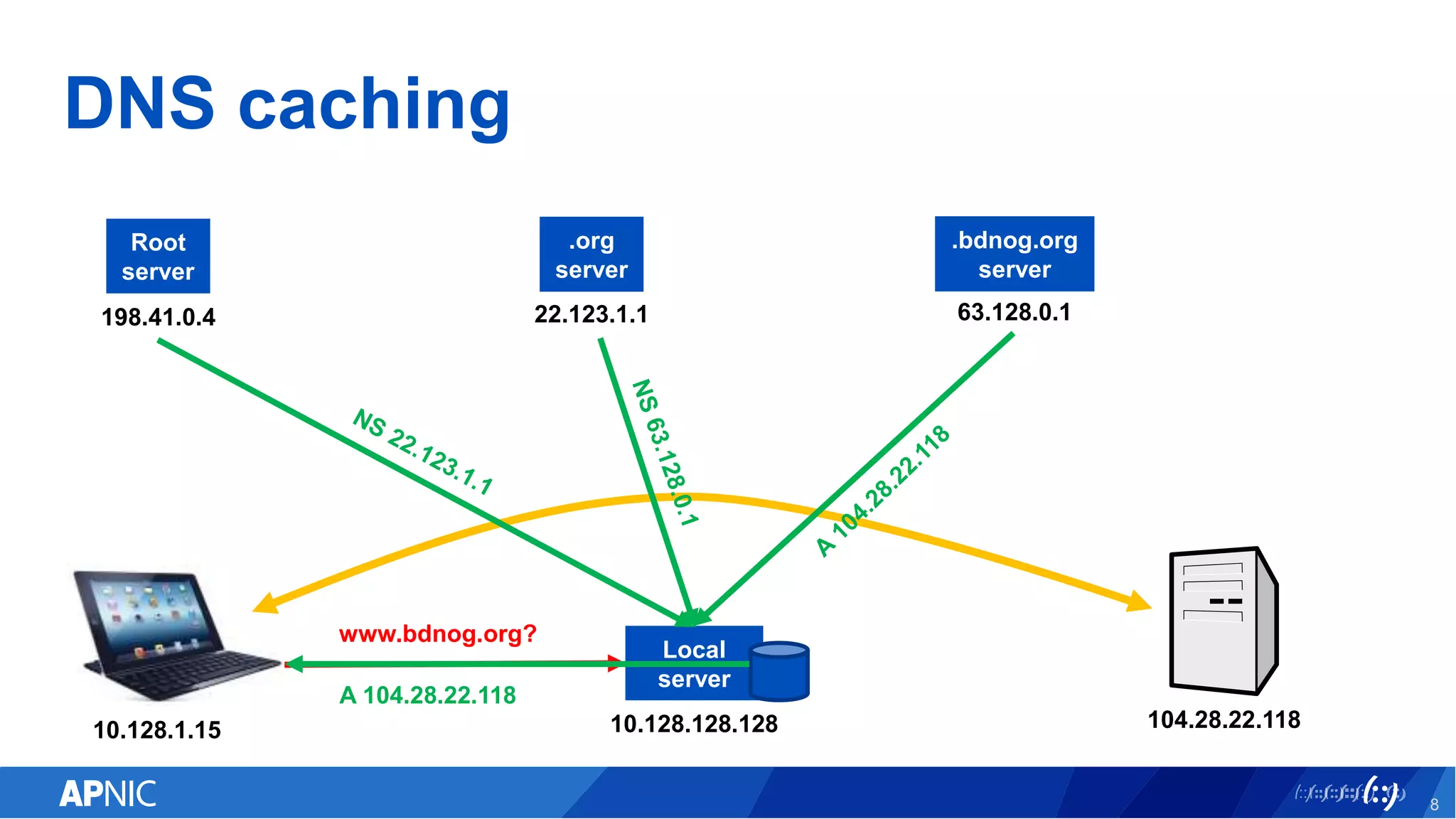
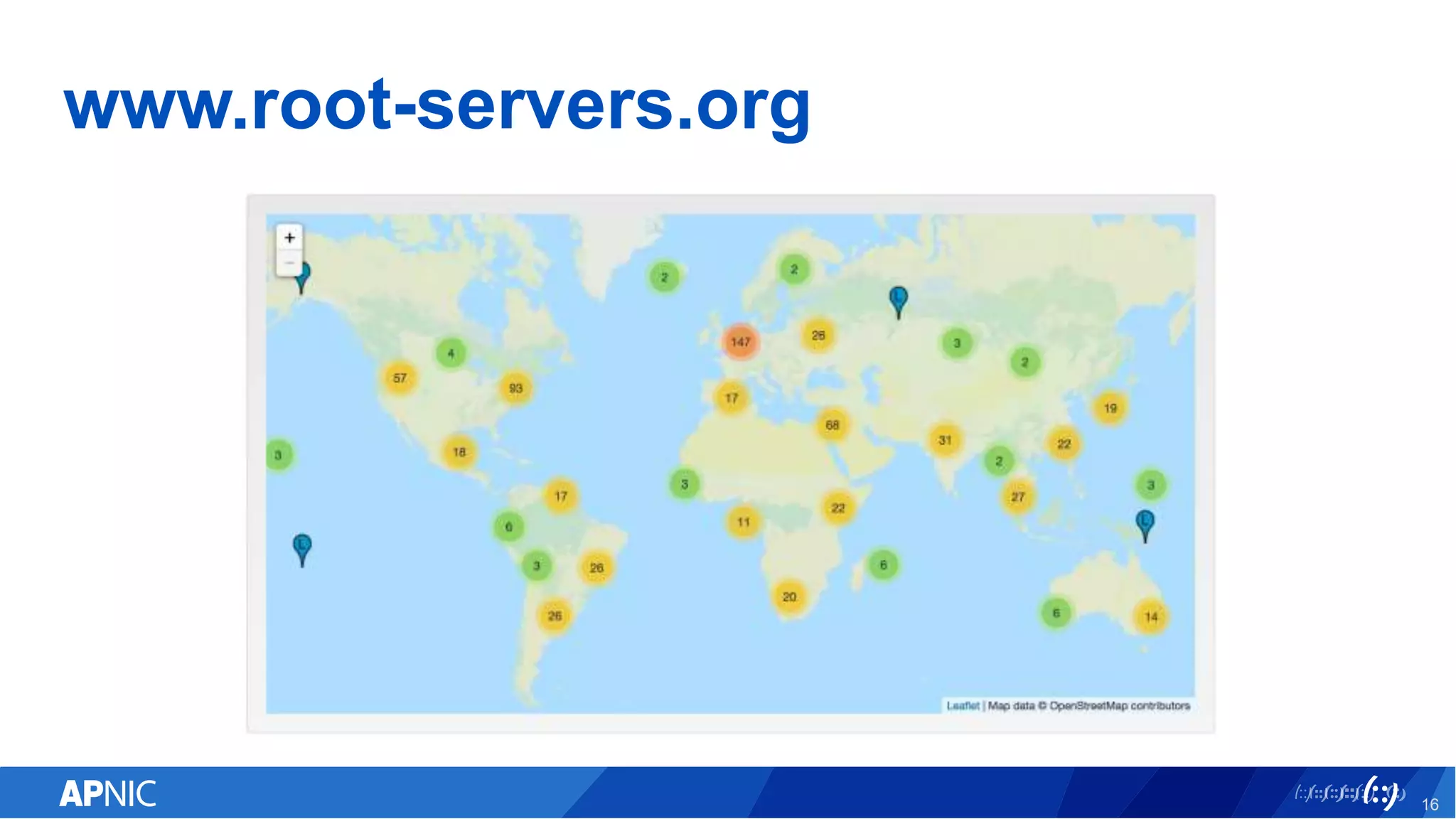
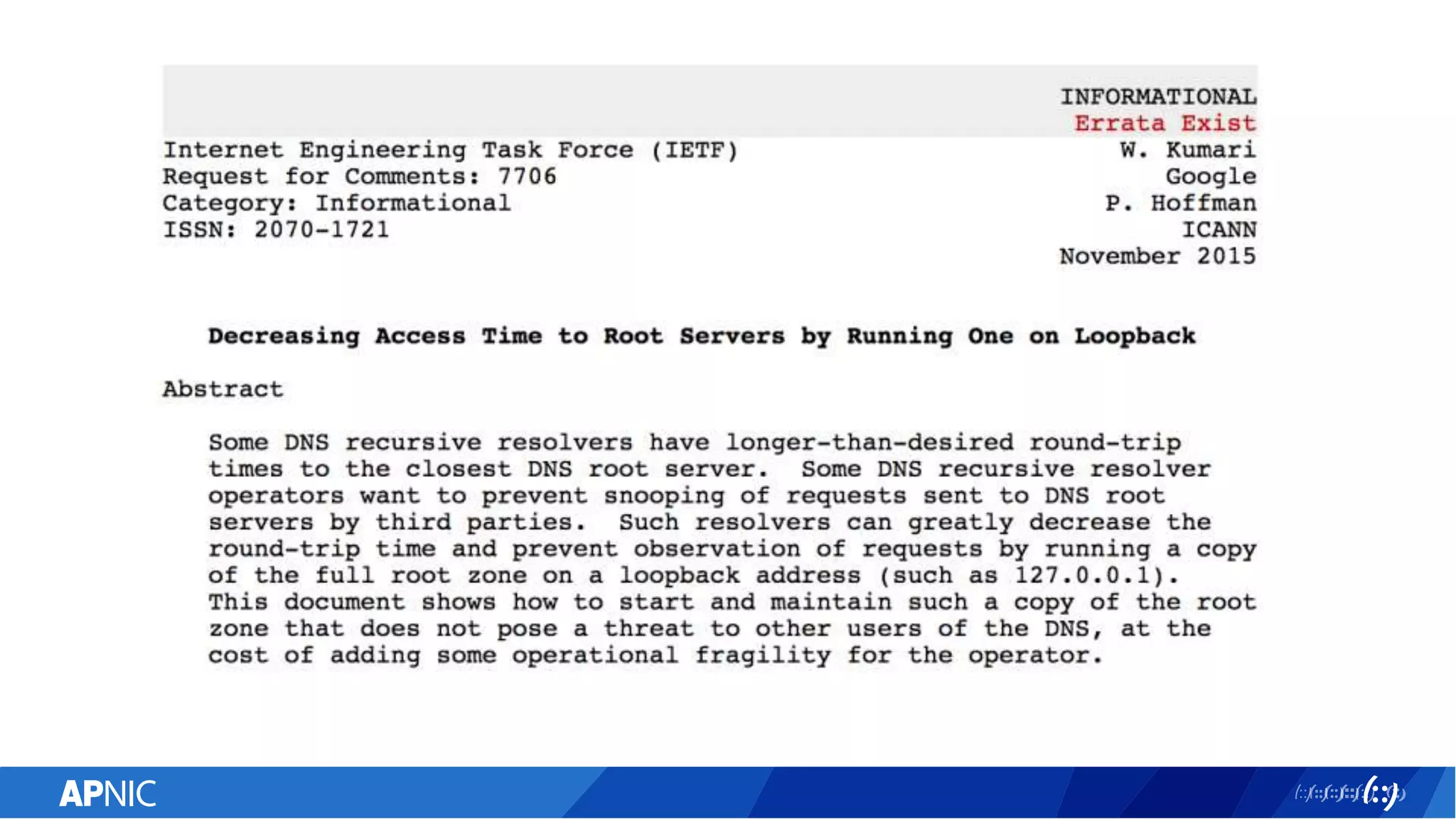
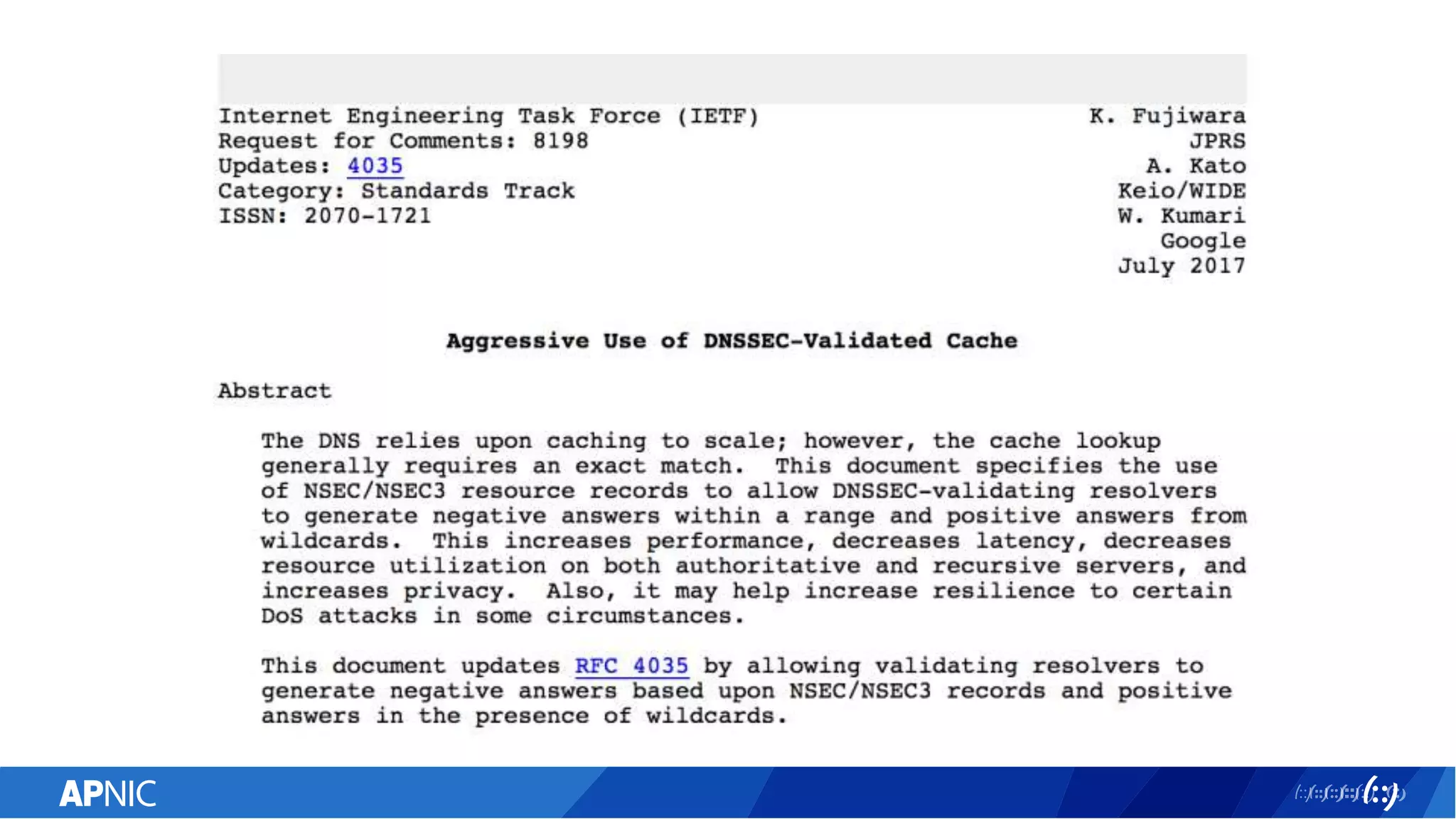
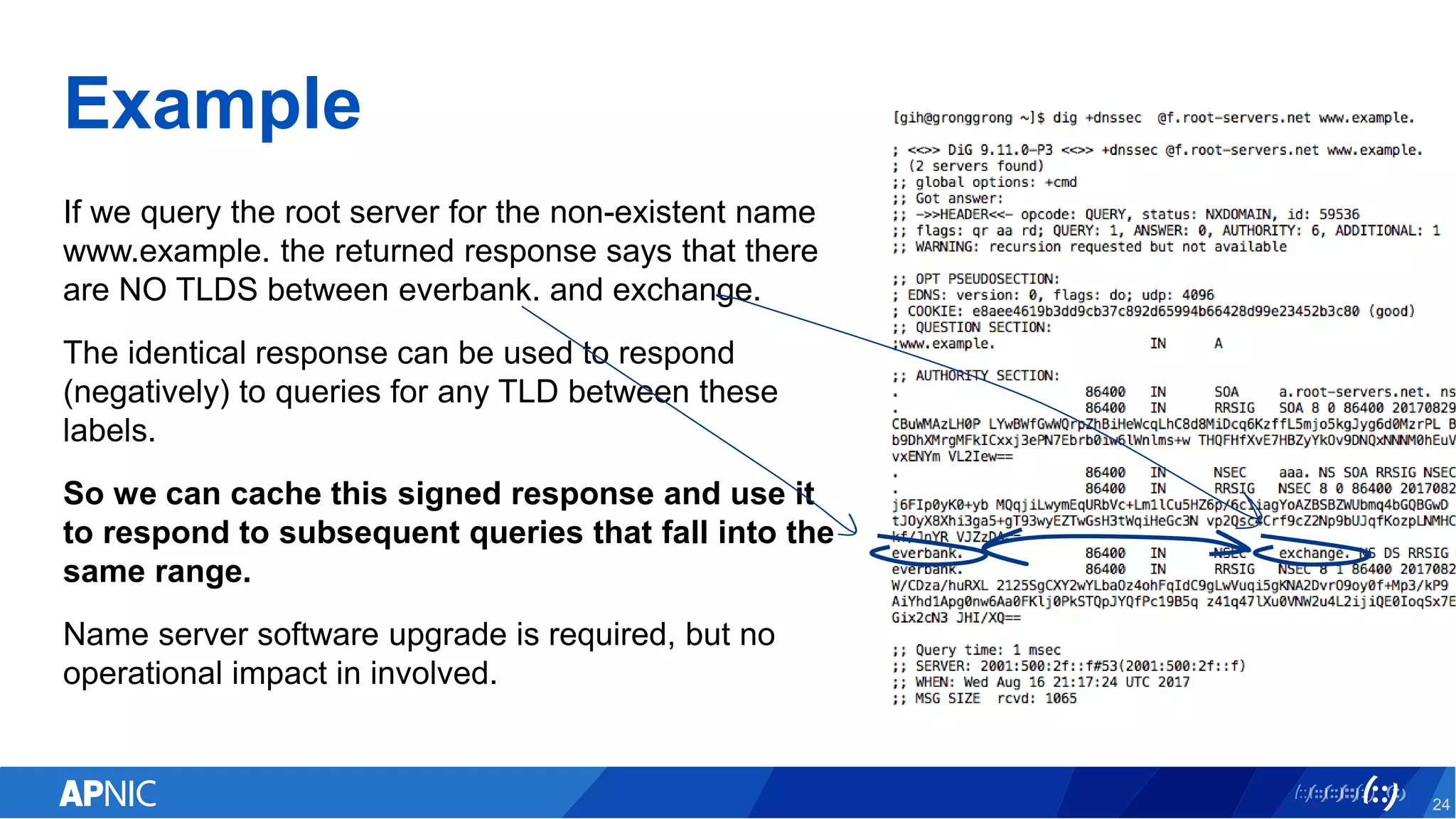
The document discusses the vulnerabilities of the DNS and root servers to DDoS attacks and outlines current and proposed mitigation techniques, including the use of DNSSEC and anycast. It highlights the importance of caching in DNS resolution and introduces RFC proposals for improving efficiency and security. APNIC's involvement in initiatives to enhance DNS resilience, particularly through collaboration and updates, is also emphasized.