This document describes a project on solving the 8 queens problem using object-oriented programming in C++. It includes an introduction to the 8 queens puzzle, a methodology section on the backtracking algorithm used, pseudocode for the algorithm, analysis of the time complexity, a flowchart, results and discussion of the 12 fundamental solutions, and the source code. It was completed by 5 students under the guidance of a professor to fulfill the requirements for a bachelor's degree in computer science and engineering.





![Page | 5
Introduction
Chess composer Max Bezzel published the eight queens
puzzle in 1848. Franz Nauck published the first solutions in
1850.Nauck also extended the puzzle to the n queens problem,
with n queens on a chessboard of n × n squares.
Since then, many mathematicians, including Carl Friedrich
Gauss, have worked on both the eight queens puzzle and its
generalized n-queens version. In 1874, S. Gunther proposed a
method using determinants to find solutions.J.W.L.
Glaisher refined Gunther's approach.
In 1972, Edsger Dijkstra used this problem to illustrate the power
of what he called structured programming. He published a highly
detailed description of a depth-first backtracking algorithm.
The classic example of the use of backtracking is the eight
queens puzzle, that asks for all arrangements of
eight chessqueens on a standard chessboard so that no queen
attacks any other. In the common backtracking approach, the
partial candidates are arrangements of k queens in the first k rows
of the board, all in different rows and columns. Any partial solution
that contains two mutually attacking queens can be abandoned.
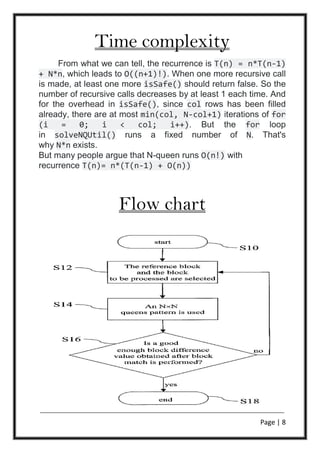
The problem can be quite computationally expensive, as there are
4,426,165,368 (i.e., 64C8) possible arrangements of eight queens
on an 8×8 board, but only 92 solutions. It is possible to use
shortcuts that reduce computational requirements or rules of
thumb that avoids brute-force computational techniques. For
example, by applying a simple rule that constrains each queen to
a single column (or row), though still considered brute force, it is
possible to reduce the number of possibilities to 16,777,216 (that
is, 88
) possible combinations. Generating permutations further
reduces the possibilities to just 40,320 (that is, 8!), which are then
checked for diagonal attacks.
Martin Richards published a program to count solutions to the n-
queens problem using bitwise operations.[3]
. However, this
solution has already been published by Zongyan Qiu](https://image.slidesharecdn.com/queen1-171121115122/85/N-Queens-problem-6-320.jpg)
![Page | 6
Methodology
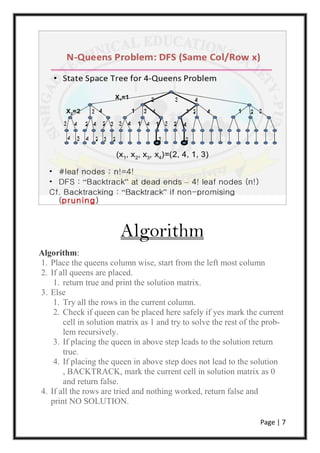
Backtracking is a general algorithm for finding all (or some)
solutions to some computational problems, notably constraint
satisfaction problems, that incrementally builds candidates to the
solutions, and abandons each partial candidate ("backtracks") as
soon as it determines that the candidate cannot possibly be
completed to a valid solution.[1][2]
The backtracking algorithm enumerates a set of partial
candidates that, in principle, could be completed in various ways
to give all the possible solutions to the given problem. The
completion is done incrementally, by a sequence of candidate
extension steps.
Conceptually, the partial candidates are represented as the nodes
of a tree structure, the potential search tree. Each partial
candidate is the parent of the candidates that differ from it by a
single extension step; the leaves of the tree are the partial
candidates that cannot be extended any further.
The backtracking algorithm traverses this search tree recursively,
from the root down, in depth-first order. At each node c, the
algorithm checks whether c can be completed to a valid solution.
If it cannot, the whole sub-tree rooted at c is skipped (pruned).
Otherwise, the algorithm (1) checks whether c itself is a valid
solution, and if so reports it to the user; and (2) recursively
enumerates all sub-trees of c. The two tests and the children of
each node are defined by user-given procedures.
Therefore, the actual search tree that is traversed by the algorithm
is only a part of the potential tree. The total cost of the algorithm
is the number of nodes of the actual tree times the cost of
obtaining and processing each node. This fact should be
considered when choosing the potential search tree and
implementing the pruning test.](https://image.slidesharecdn.com/queen1-171121115122/85/N-Queens-problem-7-320.jpg)

![Page | 11
Source code
#include<iostream>
#include<cmath>
#include<stdlib.h>
using namespace std;
int board[20],count=0;
void queen(int ,int);
int main(){
int n;
cout<<("Enter the queens number");
cin>>n;
queen(1,n);
return 0;
}](https://image.slidesharecdn.com/queen1-171121115122/85/N-Queens-problem-12-320.jpg)
![Page | 12
/* print solution */
void print(int N)
{
cout<<"Solution"<<++count<<":nn";
for (int i = 0; i < N; i++)
{
for (int j = 0; j < N; j++){
if(board[i]==j)
cout<<"Qnt";
else
cout<<"0t";
} cout<<"n";
}
}](https://image.slidesharecdn.com/queen1-171121115122/85/N-Queens-problem-13-320.jpg)
![Page | 13
/*check if a queen can be placed on board[r]*/
int place(int row,int column){
int j;
int flag=1;
for(j=1;j<=row-1;j++){
if((board[j]==column) ||
(abs(board[j]-column)==abs(j-row))){
flag= 0;
}
}
return flag;}](https://image.slidesharecdn.com/queen1-171121115122/85/N-Queens-problem-14-320.jpg)
![Page | 14
/* solves the N Queen problem using Backtracking.*/
void queen(int row ,int n){
int j;
for(j=1;j<=n;j++){
if(place(row,j)==1){
board[row]=j;
if(row==n){print(n);
}else{
queen(row+1,n);
}
}
}
}](https://image.slidesharecdn.com/queen1-171121115122/85/N-Queens-problem-15-320.jpg)