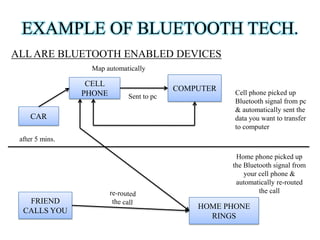
This document discusses the seminar on bluejacking presented by Dr. V.K. Patle and Swarnima Shrivastava. Bluejacking involves sending unsolicited messages to Bluetooth devices using OBEX protocol. It outlines how bluejacking works by creating a contact on the attacker's phone and sending it to discoverable Bluetooth devices within range. While bluejacking does not alter data, it can be used irresponsibly to threaten or harass users. The document recommends disabling Bluetooth when not in use to prevent bluejacking attacks.