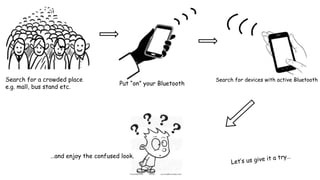
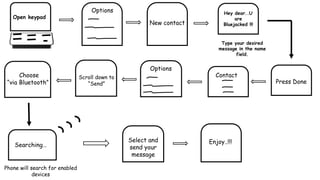
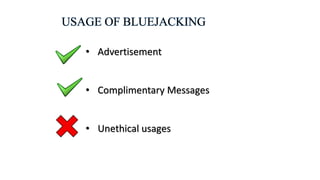
This document summarizes a seminar on bluejacking presented by three students. Bluejacking involves sending unsolicited messages to Bluetooth-enabled devices. It can target devices like laptops, mobiles, and PDAs. The seminar covered how bluejacking works using Bluetooth technology and the OBEX protocol to transmit data within a limited range. It explained what is needed to bluejack others, such as a Bluetooth phone, and provided steps to search for and send messages to nearby devices. Potential uses of bluejacking, related concepts like bluesnarfing and bluebugging, and precautions were also outlined before concluding with references.