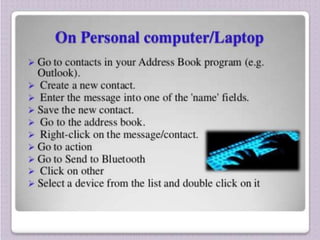
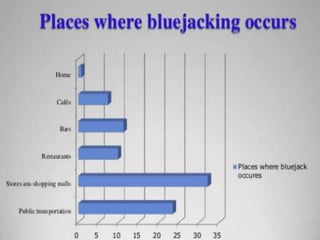
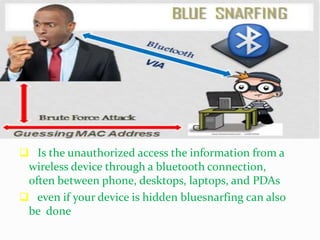
This document discusses bluejacking, which is sending unsolicited messages to Bluetooth-enabled devices. It defines Bluetooth and how to bluejack by enabling Bluetooth, finding discoverable devices, and using software tools like Bluespam, Freejack, and Easyjack to send files and text messages. Related concepts covered are bluesnarfing, unauthorized access of information from Bluetooth devices; bluecasting, providing media to other devices; and bluebugging, taking control of a phone to call the attacker. The document provides an introduction, explanation of steps and tools, usage scenarios, security issues, related attacks, and prevention of bluejacking.