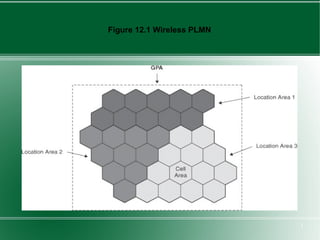
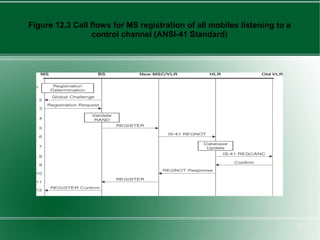
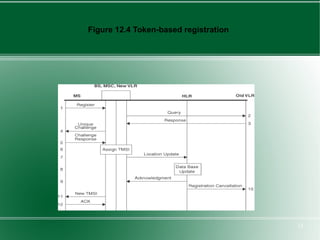
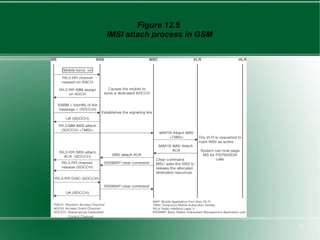
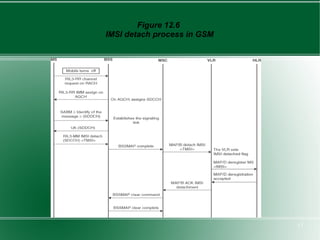
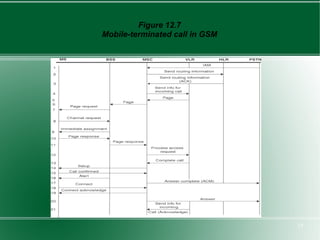
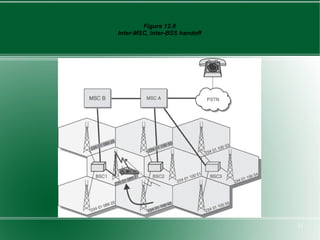
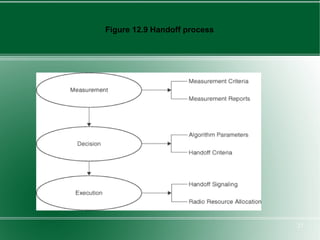
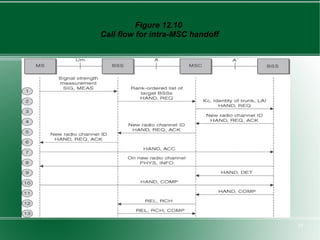
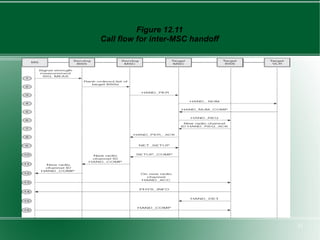
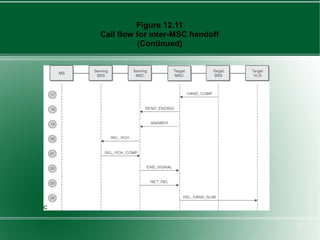
The document provides an overview of mobility management in wireless networks. It discusses radio mobility and network mobility, and key aspects like location management, registration, and handoff. Mobility management functions aim to enable subscriber mobility through tracking location and delivering calls. Location is tracked through registering with location areas and updating on area crossings. Handoff allows maintaining connections as subscribers move between cells.