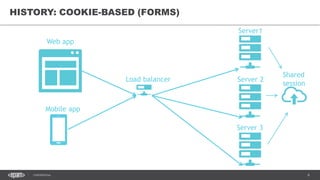
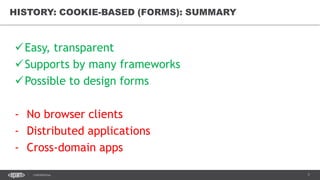
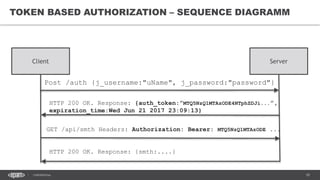
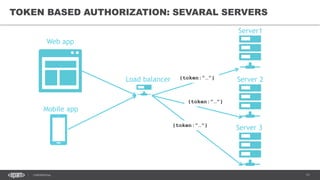
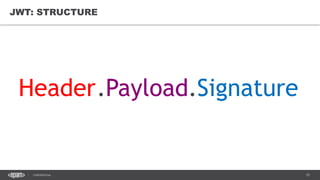
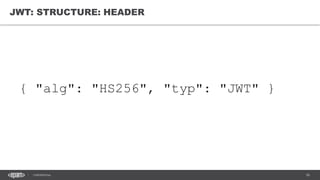
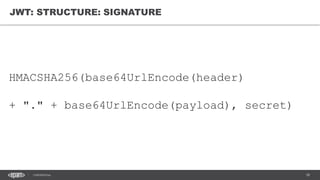
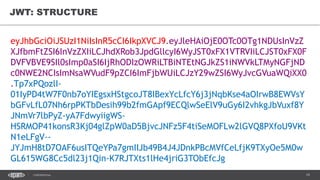
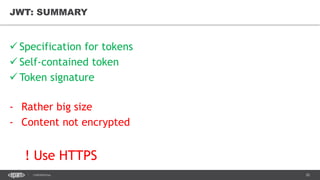
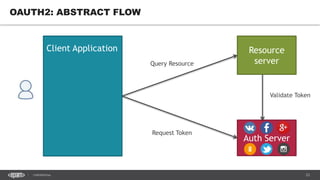
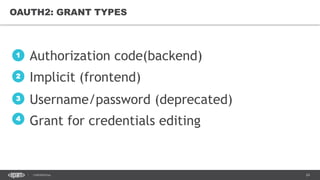
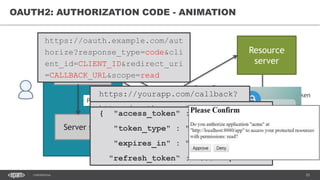
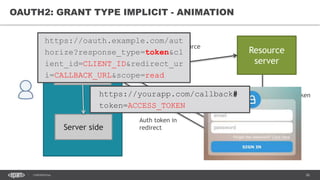
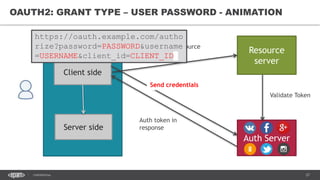
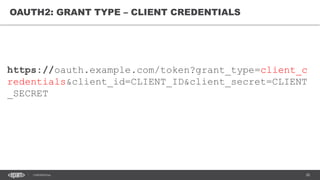
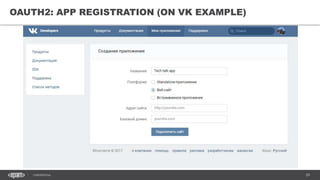
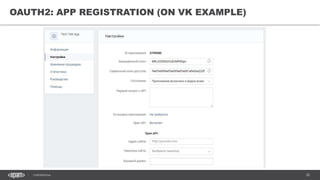
The document discusses token-based authorization and JSON web tokens (JWTs). It provides an overview of token-based authorization, including its advantages over cookie-based authorization. JWTs are described as a specification for tokens that contain encoded JSON claims in a compact URL-safe string. The document also covers OAuth2, describing its authorization grant types and flows at a high level.