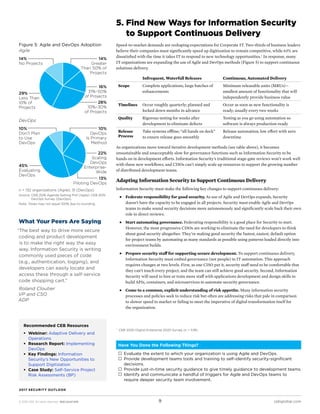
This document outlines 10 imperatives for information security functions in 2017. It discusses how information security will need to shift from a focus on governance to enabling business growth and digital strategies. Some of the key imperatives include:
1) Pivoting board conversations from risk avoidance to enabling business growth through digital innovation.
2) Formalizing IT risk management across the organization as technology becomes more critical.
3) Helping the business reassess the value of data collection relative to new privacy and security risks.
The document argues that information security will need to adopt more of a management focus over operations to support new digital initiatives and continuous delivery models. It also emphasizes the need to consider security risks outside of