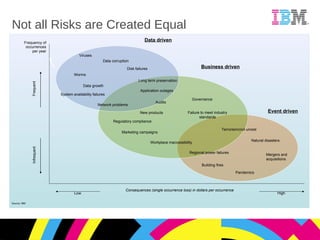
The document discusses managing and mitigating risk in businesses. It outlines an evolving risk landscape with new technologies, data growth, and regulatory compliance challenges. Different types of risks are described, from frequent low impact issues to infrequent high impact disasters. Key success factors for managing risk include lowering costs, ensuring compliance, protecting data and applications, and securing the data center. IBM is positioned as being able to help businesses fuel innovation, secure data, meet compliance, and secure their data centers from threats to ensure productivity and reputation.