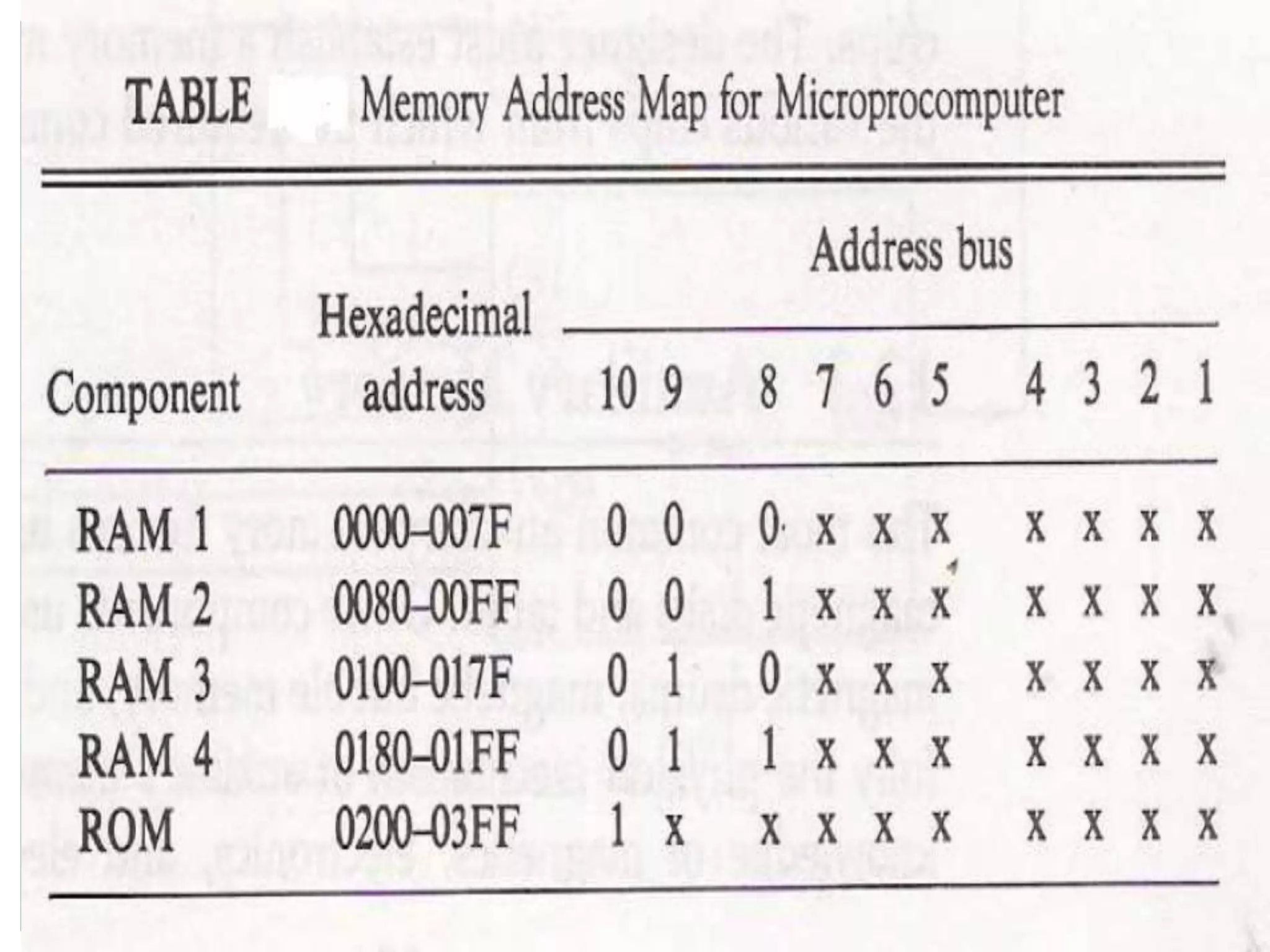
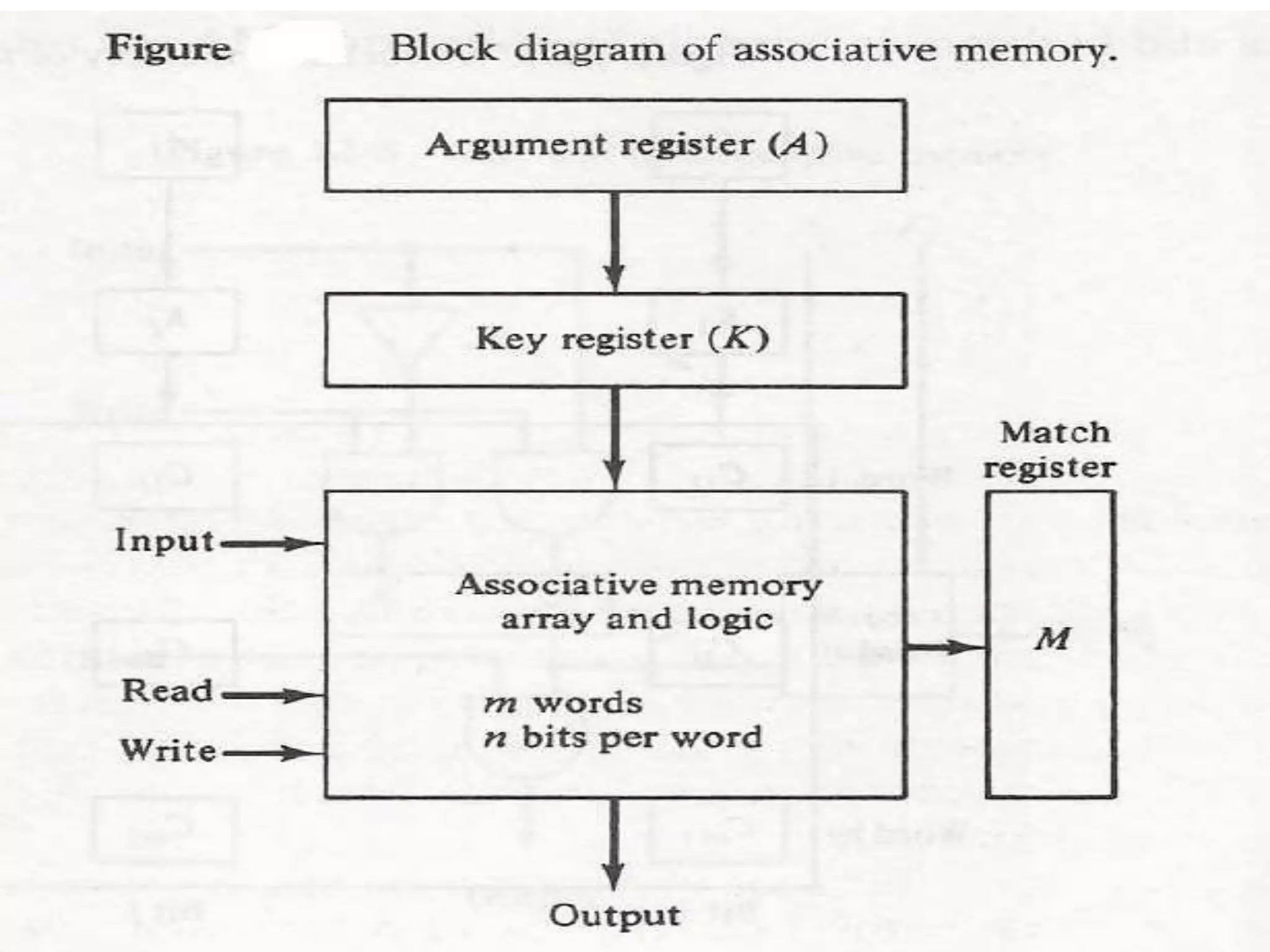
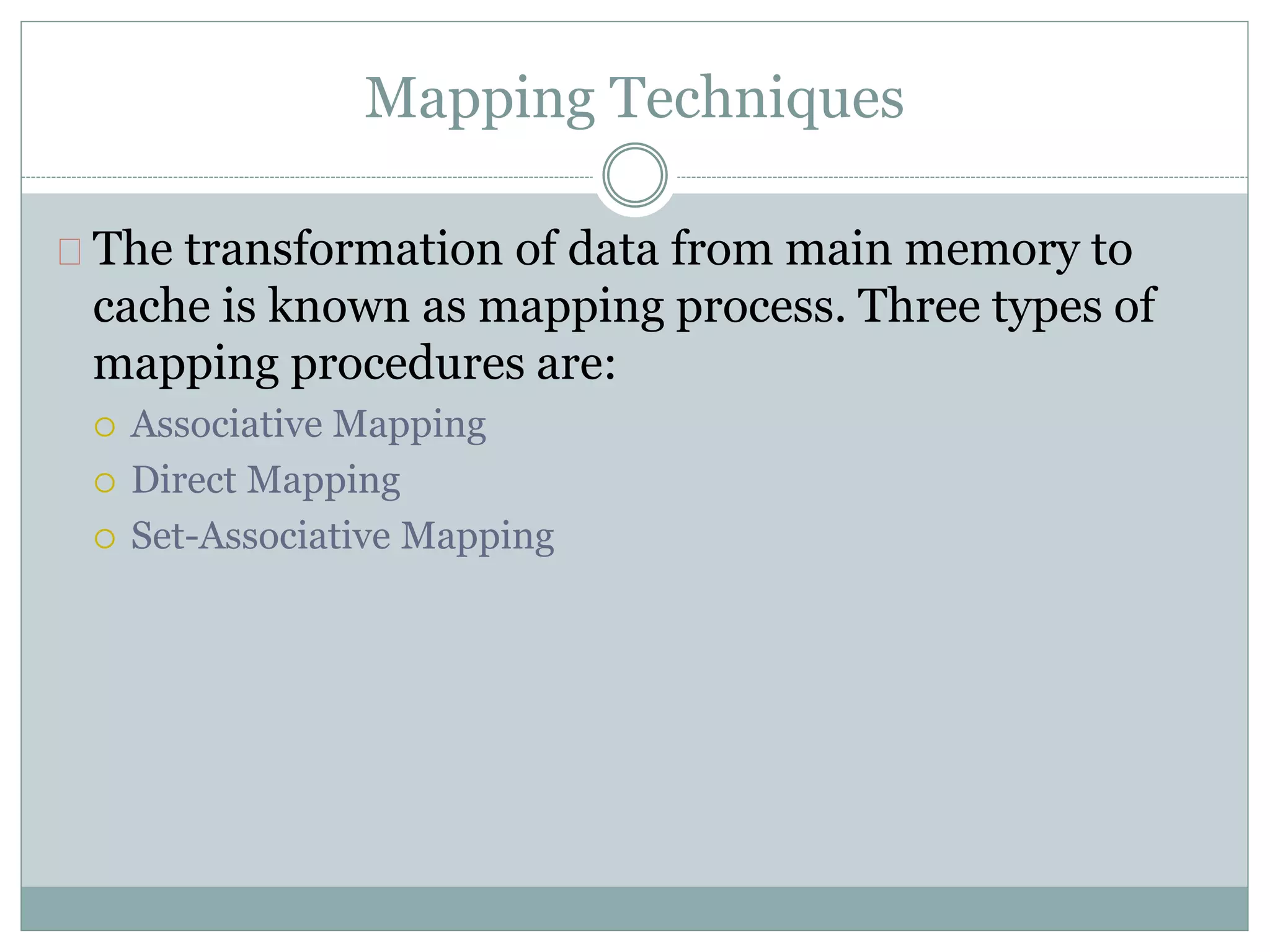
This document discusses memory hierarchy and organization, including main memory, cache memory, virtual memory, and mapping techniques. It provides details on different types of memory like RAM, ROM, cache mapping using direct mapping, set associative mapping, and associative mapping. It also discusses concepts of virtual memory like address space, memory space, page frames, and page replacement algorithms.