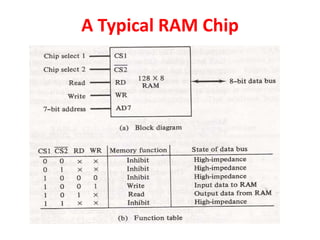
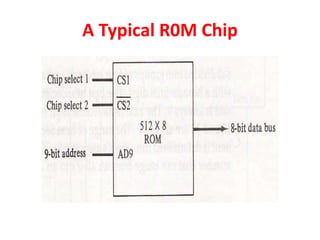
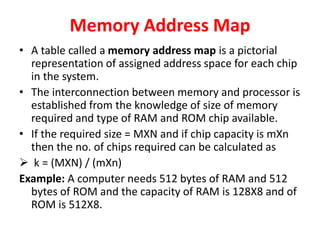
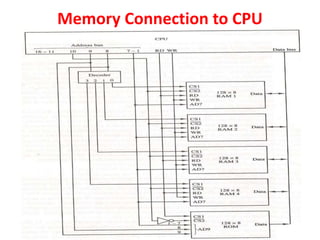
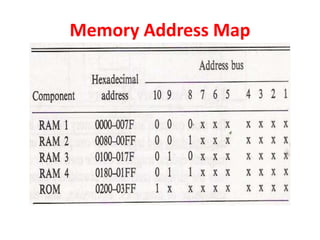
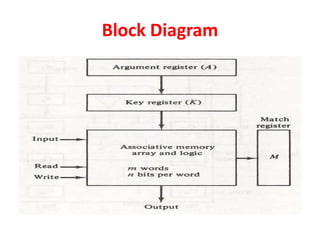
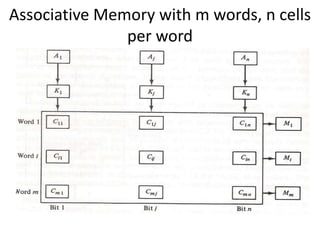
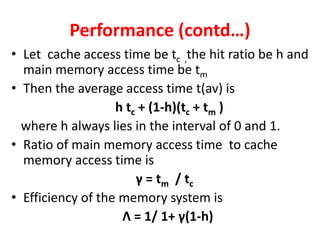
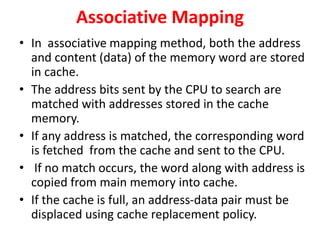
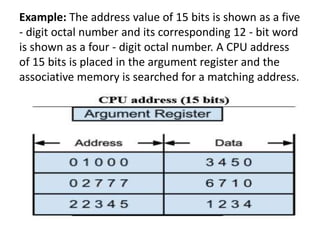
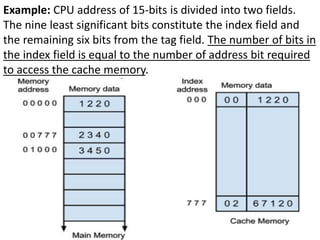
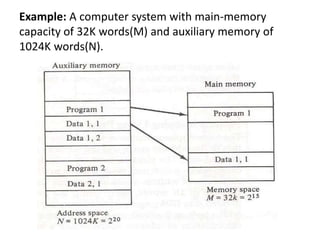
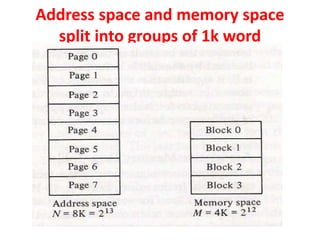
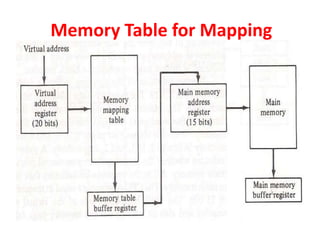
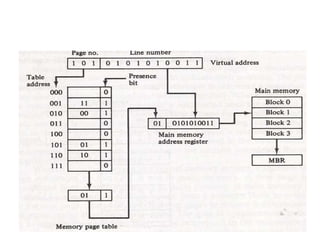
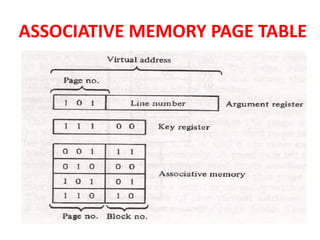
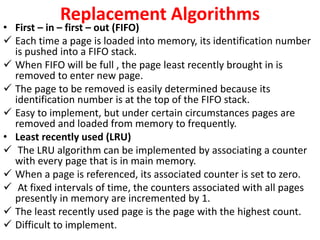
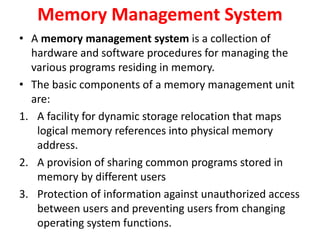
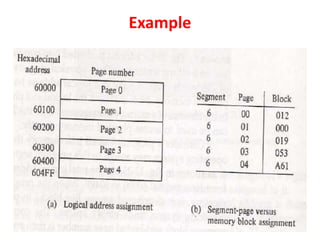
The document discusses memory organization, focusing on the hierarchy of memory types including CPU registers, cache, main memory, and auxiliary memory. It explains key concepts such as associative memory, cache management strategies, and virtual memory, detailing how these components interact to optimize performance and storage. Additionally, it covers memory management systems, emphasizing dynamic allocation, segmented pages, and address mapping techniques.