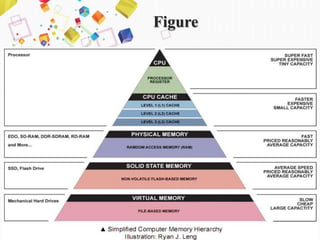
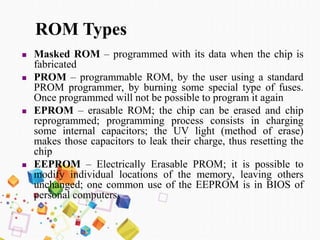
This document discusses the memory hierarchy in computers. It begins by explaining that computer memory is organized in a pyramid structure from fastest and smallest memory (cache) to slower and larger auxiliary memory. The main types of memory discussed are RAM, ROM, cache memory, and auxiliary storage. RAM is further divided into SRAM and DRAM. The document provides details on the characteristics of each memory type including access speed, volatility, capacity and cost. Diagrams are included to illustrate concepts like RAM, ROM, cache levels and auxiliary devices. Virtual memory is also briefly introduced at the end.