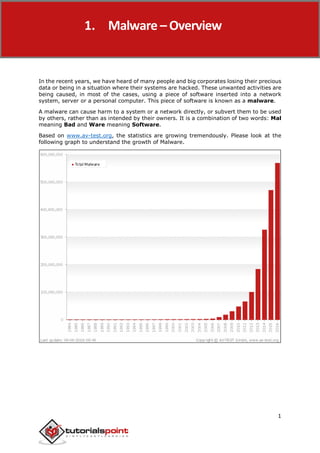
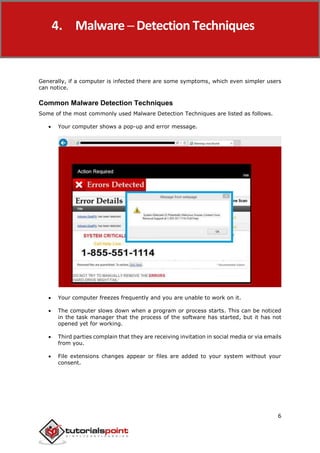
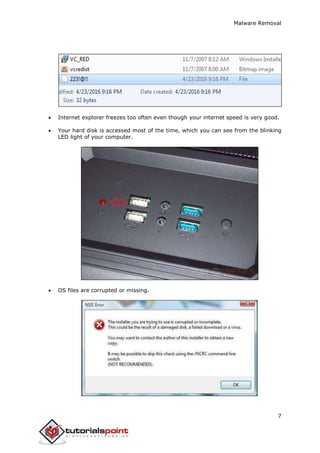
This document provides an overview of malware removal. It discusses how malware works by entering systems, distributing, exploiting vulnerabilities, infecting, and executing harmful activities. It also describes common types of malware like viruses, adware, spyware, Trojans, rootkits, botnets, and ransomware. The document outlines techniques for detecting malware based on system symptoms like pop-ups, freezing, slow performance, unauthorized file changes, and excessive hard disk access. It emphasizes the importance of preparing to remove malware by backing up data and downloading removal tools before starting the removal process.