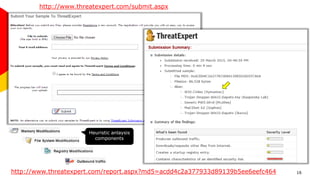
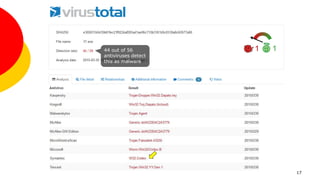
The document discusses the identification, monitoring, and reporting of malware, defining it as software that intentionally exhibits harmful behaviors. It categorizes various types of malware, highlights the challenges of malware reversing, and presents tools like the Sysinternals Process Monitor for analyzing processes in Windows. The document also emphasizes safely analyzing malware in isolated virtualized environments to prevent infections and outlines methods for reporting suspected malware through online services.


![3
Identifying, Monitoring, and Reporting Malware
Types of Malware
There are several types of malware that affect computer systems [6] [7]:
Viruses: require some deliberate action to help them spread.
Worms: similar to a virus but can spread by itself over computer networks.
Trojan Horses: performs hidden malicious or annoying operations.
Backdoor: a vulnerability purposely embedded in software.
Rabbit: a program that exhausts system resources.
Ransomware: lock computer files, victim has to pay to unlock.
Criminalware: Steal sensitive information.](https://image.slidesharecdn.com/7identifyingreportingmalware-150414024324-conversion-gate01/85/Identifying-Monitoring-and-Reporting-Malware-3-320.jpg)


![6
Identifying, Monitoring, and Reporting Malware
Safe & Practical Malware Reversing
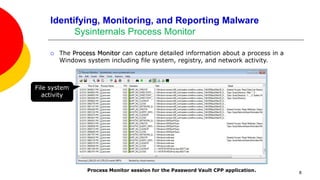
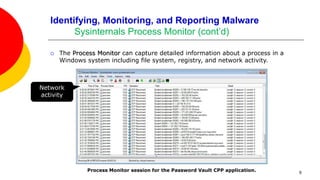
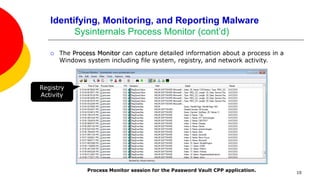
We want to become familiar with using tools to identify, monitor, and report
software that might be malicious.
Reversing malware directly is especially challenging because several anti-
reversing techniques will have been applied to the code.
Given that unexpected catastrophes can arise when installing a virus, worm,
backdoor, etc… for academic purposes; we could still learn something from
working with contrived or benign “malware”.
In 1996, Mark Russinovich founded a company called “Winternals Software”
where he was the chief software architect on a comprehensive suite of tools for
diagnosing, debugging, and repairing Windows® systems and applications [9].](https://image.slidesharecdn.com/7identifyingreportingmalware-150414024324-conversion-gate01/85/Identifying-Monitoring-and-Reporting-Malware-6-320.jpg)

![14
Identifying, Monitoring, and Reporting Malware
Is Open Source More Trustworthy?
The data on the number of vulnerabilities found in the 5 most popular Internet
browsers does not support the proposition that open source is more secure.
Big 5: Google Chrome, Mozilla Firefox, Internet Explorer, Opera and Safari.
Mozilla Firefox was affected by 270 new vulnerabilities in 2013, more than any
other browser; 245 new vulnerabilities were found in Google Chrome, 126 in
Internet Explorer, 75 in Apple Safari, 11 in Opera [Secunia].
The two browsers containing the most open source (Chrome based Chromium,
Firefox based on Mozilla), have the most vulnerabilities…
Of course we need temper this judgement with the observation that popular
software is targeted more often.](https://image.slidesharecdn.com/7identifyingreportingmalware-150414024324-conversion-gate01/85/Identifying-Monitoring-and-Reporting-Malware-14-320.jpg)