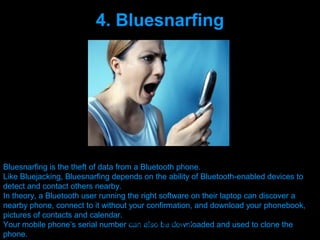
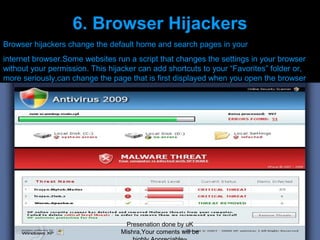
This presentation is intended for an experienced audience knowledgeable about MS Office, internet, networks, Windows operating systems, and general PC troubleshooting. Attendees should understand common IT security issues like viruses, spyware, malware, and botnets as well as remedies for these issues. The presentation will be delivered by Mishra and comments from the audience are welcome.






![2. Backdoor Trojans
A backdoor Trojan allows someone to take control of another user’s
computer via the internet without their permission.
A backdoor Trojan may pose as legitimate software, just as other Trojan horse programs
do, so that users run it. Alternatively – as is now increasingly common – users may
allow Trojans onto their computer by following a link in spam mail.
Once the Trojan is run, it adds itself to the computer’s startup routine. It can then
monitor the computer until the user is connected to the internet. When the computer
goes online, the person who sent the Trojan can perform many actions – for example,
run programs on the infected computer, access personal files, modify and upload files,
track the user’s keystrokes, or send out spam mail
Examples
Trojan-Spy.HTML.Smitfraud.c [Kaspersky], Phish-BankFraud.eml.a [McAfee],
Presenation done by uK
Trj/Citifraud.A [Panda coments will be
Mishra,Your Software], generic5 [AVG](https://image.slidesharecdn.com/itsecurity-121106001925-phpapp01/85/I-T-Security-Threats-7-320.jpg)