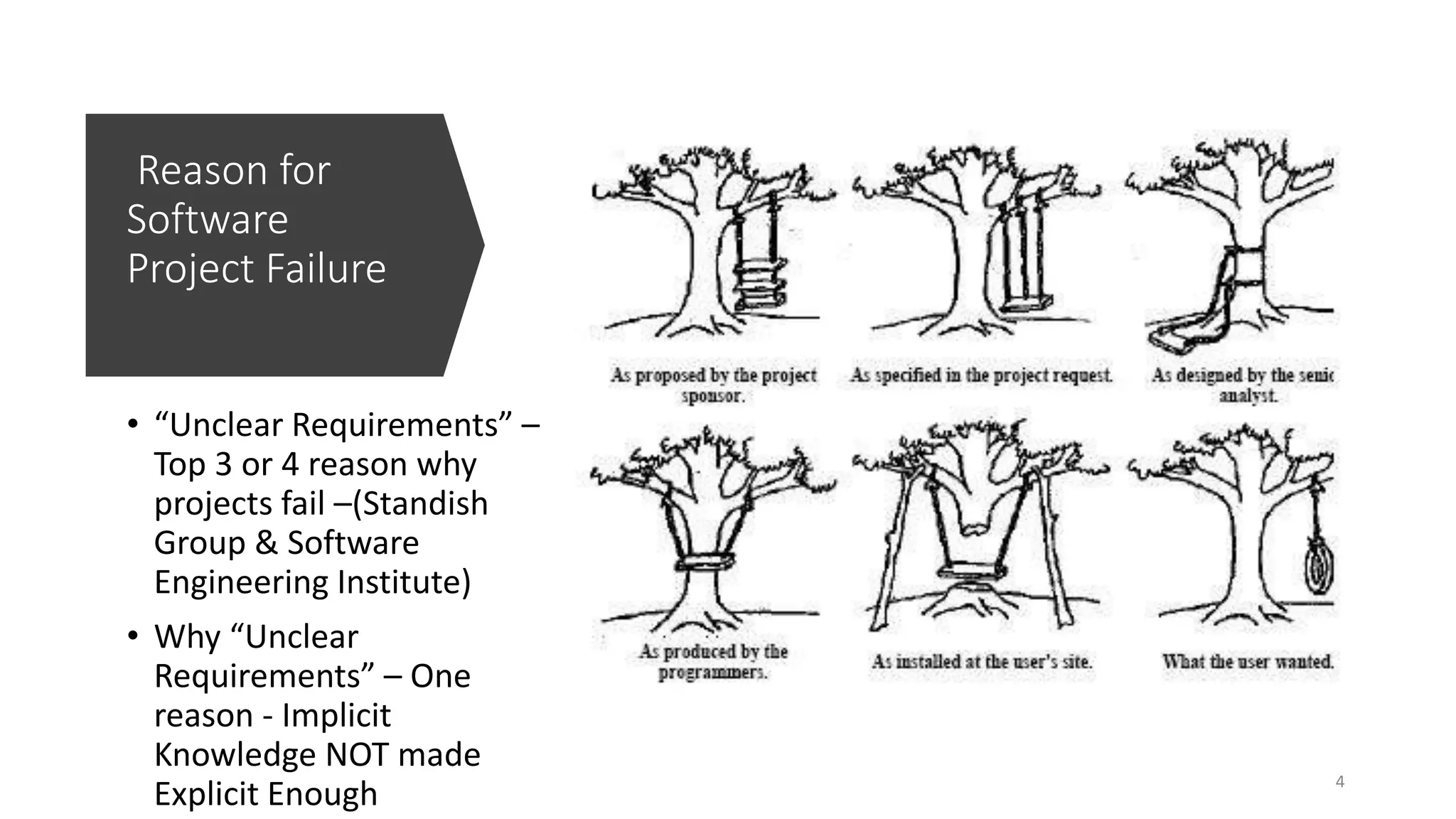
The document discusses the importance of making implicit security requirements explicit in the context of cyber-physical systems, specifically in critical maritime infrastructure (CMI). It presents a systematic approach using System Theoretic Process Analysis (STPA) to analyze security requirements and threats, highlighting the relevance of safety analyses in enhancing security measures. The conclusions emphasize the significance of accurate security requirements and propose future work to verify system constraints using event-B.