Intel Confidential Flows
•Download as PPTX, PDF•
3 likes•599 views
This document discusses security and safety requirements for Intel systems. It describes performing threat analysis and risk assessment (TARA) along with hazard analysis and risk assessment (HARA) to define security and safety goals. Additionally, it proposes adding security mechanisms such as checking for file tampering and application trust when monitoring graphics systems to protect against threats.
Report
Share
Report
Share
Recommended
Fiori and S/4 authorizations: What are the biggest challenges, and where do t...

Fiori and S/4 authorizations: What are the biggest challenges, and where do t...akquinet enterprise solutions GmbH
Recommended
Fiori and S/4 authorizations: What are the biggest challenges, and where do t...

Fiori and S/4 authorizations: What are the biggest challenges, and where do t...akquinet enterprise solutions GmbH
More Related Content
What's hot
What's hot (20)
Solutions manual for absolute java 5th edition by walter savitch

Solutions manual for absolute java 5th edition by walter savitch
An integrative solution towards SOTIF and AV safety

An integrative solution towards SOTIF and AV safety
Software engineering a practitioners approach 8th edition pressman solutions ...

Software engineering a practitioners approach 8th edition pressman solutions ...
Contrast & Compare & Contrast Information Security Roles 

Contrast & Compare & Contrast Information Security Roles
Getting the Most from Your CA Advanced Authentication Solution

Getting the Most from Your CA Advanced Authentication Solution
Critical System Validation in Software Engineering SE21

Critical System Validation in Software Engineering SE21
Similar to Intel Confidential Flows
Similar to Intel Confidential Flows (20)
Automated Interpretation and Integration of Security Tools Using Semantic Kno...

Automated Interpretation and Integration of Security Tools Using Semantic Kno...
Architecture-centric Support for Integrating Security Tool in a Security Orch...

Architecture-centric Support for Integrating Security Tool in a Security Orch...
ОЛЬГА АКСЬОНЕНКО «Безпечна розробка програмного забезпечення в Agile проектах...

ОЛЬГА АКСЬОНЕНКО «Безпечна розробка програмного забезпечення в Agile проектах...
Security Testing Report Hitachi Application Q1 Sep 2015

Security Testing Report Hitachi Application Q1 Sep 2015
INTERFACE by apidays 2023 - Security Exposure Management in API First World, ...

INTERFACE by apidays 2023 - Security Exposure Management in API First World, ...
Chapter 4 - Quality Characteristics for Technical Testing

Chapter 4 - Quality Characteristics for Technical Testing
SOURCE CODE ANALYSIS TO REMOVE SECURITY VULNERABILITIES IN JAVA SOCKET PROGR...

SOURCE CODE ANALYSIS TO REMOVE SECURITY VULNERABILITIES IN JAVA SOCKET PROGR...
More from Alan Tatourian
More from Alan Tatourian (9)
Systems architecture with the functional safety/security emphasis

Systems architecture with the functional safety/security emphasis
Securing future connected vehicles and infrastructure

Securing future connected vehicles and infrastructure
Recently uploaded
(COD) ̄Young Call Girls In Dwarka , New Delhi꧁❤ 7042364481❤꧂ Escorts Service i...

(COD) ̄Young Call Girls In Dwarka , New Delhi꧁❤ 7042364481❤꧂ Escorts Service i...Hot Call Girls In Sector 58 (Noida)
Indian Downtown Call Girls # 00971528903066 # Indian Call Girls In Downtown D...

Indian Downtown Call Girls # 00971528903066 # Indian Call Girls In Downtown D...Business Bay Call Girls || 0529877582 || Call Girls Service in Business Bay Dubai
Hotel Escorts Sushant Golf City - 9548273370 Call Girls Service in Lucknow, c...

Hotel Escorts Sushant Golf City - 9548273370 Call Girls Service in Lucknow, c...Call Girls In Delhi Whatsup 9873940964 Enjoy Unlimited Pleasure
call girls in Jama Masjid (DELHI) 🔝 >༒9953330565🔝 genuine Escort Service 🔝✔️✔️

call girls in Jama Masjid (DELHI) 🔝 >༒9953330565🔝 genuine Escort Service 🔝✔️✔️9953056974 Low Rate Call Girls In Saket, Delhi NCR
Call Girls in Shri Niwas Puri Delhi 💯Call Us 🔝9953056974🔝

Call Girls in Shri Niwas Puri Delhi 💯Call Us 🔝9953056974🔝9953056974 Low Rate Call Girls In Saket, Delhi NCR
Hauz Khas Call Girls ☎ 7042364481 independent Escorts Service in delhi

Hauz Khas Call Girls ☎ 7042364481 independent Escorts Service in delhiHot Call Girls In Sector 58 (Noida)
꧁༒☬ 7042364481 (Call Girl) In Dwarka Delhi Escort Service In Delhi Ncr☬༒꧂

꧁༒☬ 7042364481 (Call Girl) In Dwarka Delhi Escort Service In Delhi Ncr☬༒꧂Hot Call Girls In Sector 58 (Noida)
Recently uploaded (20)
Not Sure About VW EGR Valve Health Look For These Symptoms

Not Sure About VW EGR Valve Health Look For These Symptoms
Call me @ 9892124323 Call Girl in Andheri East With Free Home Delivery

Call me @ 9892124323 Call Girl in Andheri East With Free Home Delivery
(COD) ̄Young Call Girls In Dwarka , New Delhi꧁❤ 7042364481❤꧂ Escorts Service i...

(COD) ̄Young Call Girls In Dwarka , New Delhi꧁❤ 7042364481❤꧂ Escorts Service i...
Indian Downtown Call Girls # 00971528903066 # Indian Call Girls In Downtown D...

Indian Downtown Call Girls # 00971528903066 # Indian Call Girls In Downtown D...
Hotel Escorts Sushant Golf City - 9548273370 Call Girls Service in Lucknow, c...

Hotel Escorts Sushant Golf City - 9548273370 Call Girls Service in Lucknow, c...
Russian Call Girls Delhi Indirapuram {9711199171} Aarvi Gupta ✌️Independent ...

Russian Call Girls Delhi Indirapuram {9711199171} Aarvi Gupta ✌️Independent ...
2024 WRC Hyundai World Rally Team’s i20 N Rally1 Hybrid

2024 WRC Hyundai World Rally Team’s i20 N Rally1 Hybrid
Dubai Call Girls Size E6 (O525547819) Call Girls In Dubai

Dubai Call Girls Size E6 (O525547819) Call Girls In Dubai
call girls in Jama Masjid (DELHI) 🔝 >༒9953330565🔝 genuine Escort Service 🔝✔️✔️

call girls in Jama Masjid (DELHI) 🔝 >༒9953330565🔝 genuine Escort Service 🔝✔️✔️
Call Girls in Shri Niwas Puri Delhi 💯Call Us 🔝9953056974🔝

Call Girls in Shri Niwas Puri Delhi 💯Call Us 🔝9953056974🔝
Hauz Khas Call Girls ☎ 7042364481 independent Escorts Service in delhi

Hauz Khas Call Girls ☎ 7042364481 independent Escorts Service in delhi
꧁༒☬ 7042364481 (Call Girl) In Dwarka Delhi Escort Service In Delhi Ncr☬༒꧂

꧁༒☬ 7042364481 (Call Girl) In Dwarka Delhi Escort Service In Delhi Ncr☬༒꧂
Intel Confidential Flows
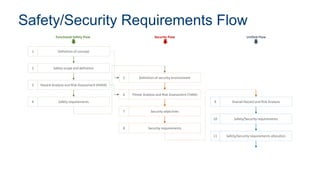
- 1. Intel Confidential 1 Safety/Security Requirements Flow Definition of security environment5 Threat Analysis and Risk Assessment (TARA)6 Security requirements8 Overall Hazard and Risk Analysis9 Safety/Security requirements10 Safety/Security requirements allocation11 Security objectives7 Definition of concept1 Safety scope and definition2 Hazard Analysis and Risk Assessment (HARA)3 Safety requirements4 Functional Safety Flow Security Flow Unified Flow
- 2. Intel Confidential 2 HARA and TARA Done Together Threat Security Goal AssetOwner Attacker Malicious Action Attack Potential Point of Attack with regard to with risk of has a value for has for execution of reduced by performed at TARA HARA Define the safety item Determine features to realize safety item Determine malfunctions of functions Determine operational scenarios Identify possible hazards (effects) Evaluate the ASIL and determine the safety goals
- 3. Intel Confidential 3 Mixed-Criticality Cluster
- 4. Intel Confidential 4 Graphics Fail-Safe Step By Step 1. Monitor parses configuration file for checking criteria 2. Cluster app requests Screen to display a symbol 3. Cluster app requests Monitor to check the rendered symbol 4. Monitor retrieves the framebuffer from Screen 5. Monitor performs checking according to criteria from (1) 6. Monitor notifies the cluster app of the checking results 7. Cluster app decides the course of action
- 5. Intel Confidential 5 Security Mechanism to Protect Graphics 1. Monitor parses configuration file for checking criteria (Was the file tampered with? Is the monitor trusted?) 2. Cluster app requests Screen to display a symbol (Does the application run in a trusted sandbox? Is the application trusted?) 3. Cluster app requests Monitor to check the rendered symbol 4. Monitor retrieves the framebuffer from Screen 5. Monitor performs checking according to criteria from (1) 6. Monitor notifies the cluster app of the checking results 7. Cluster app decides the course of action Does the application trust the message? Was the configuration file tampered? Is the application trusted? Is the monitor trusted?
