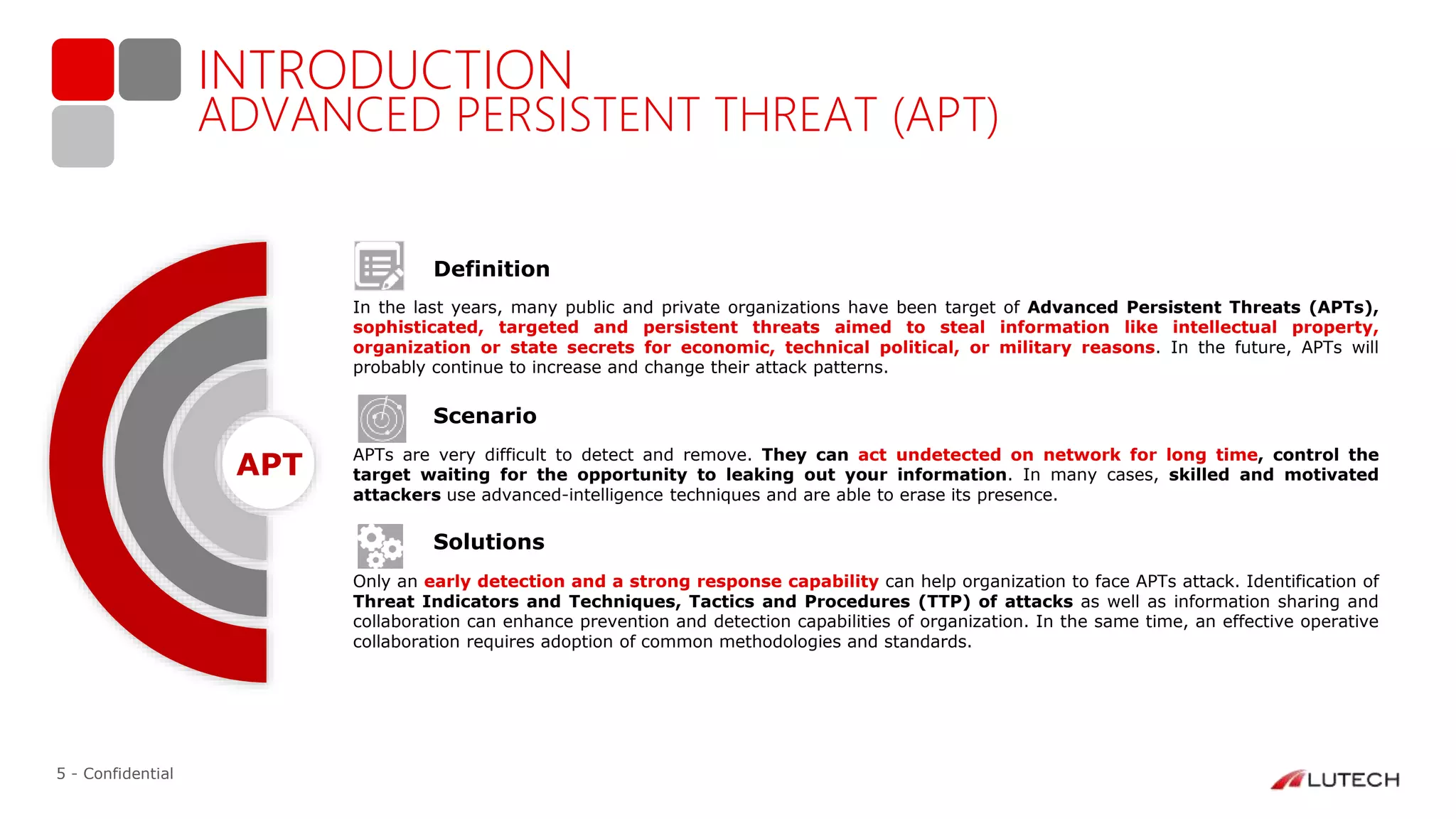
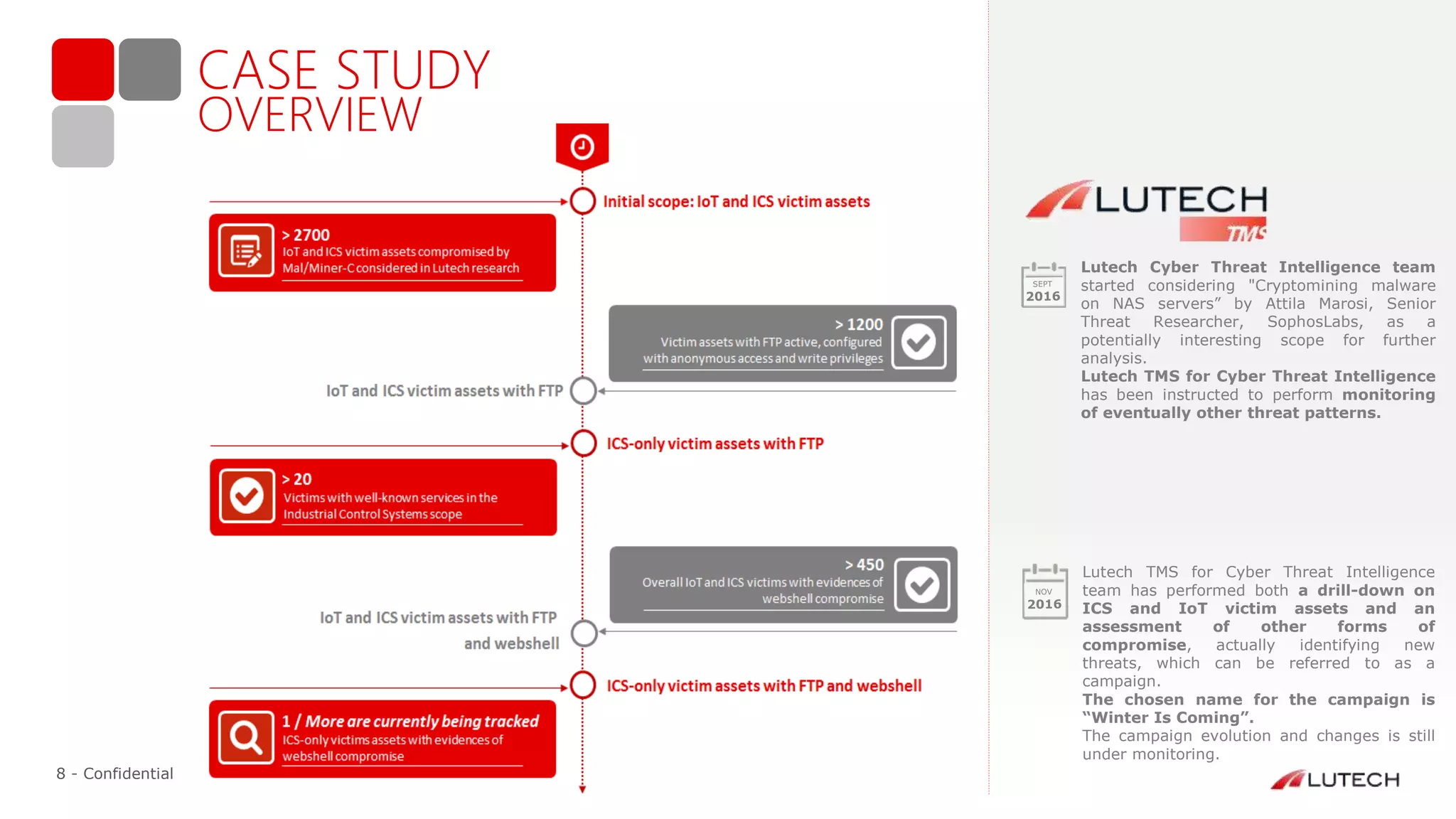
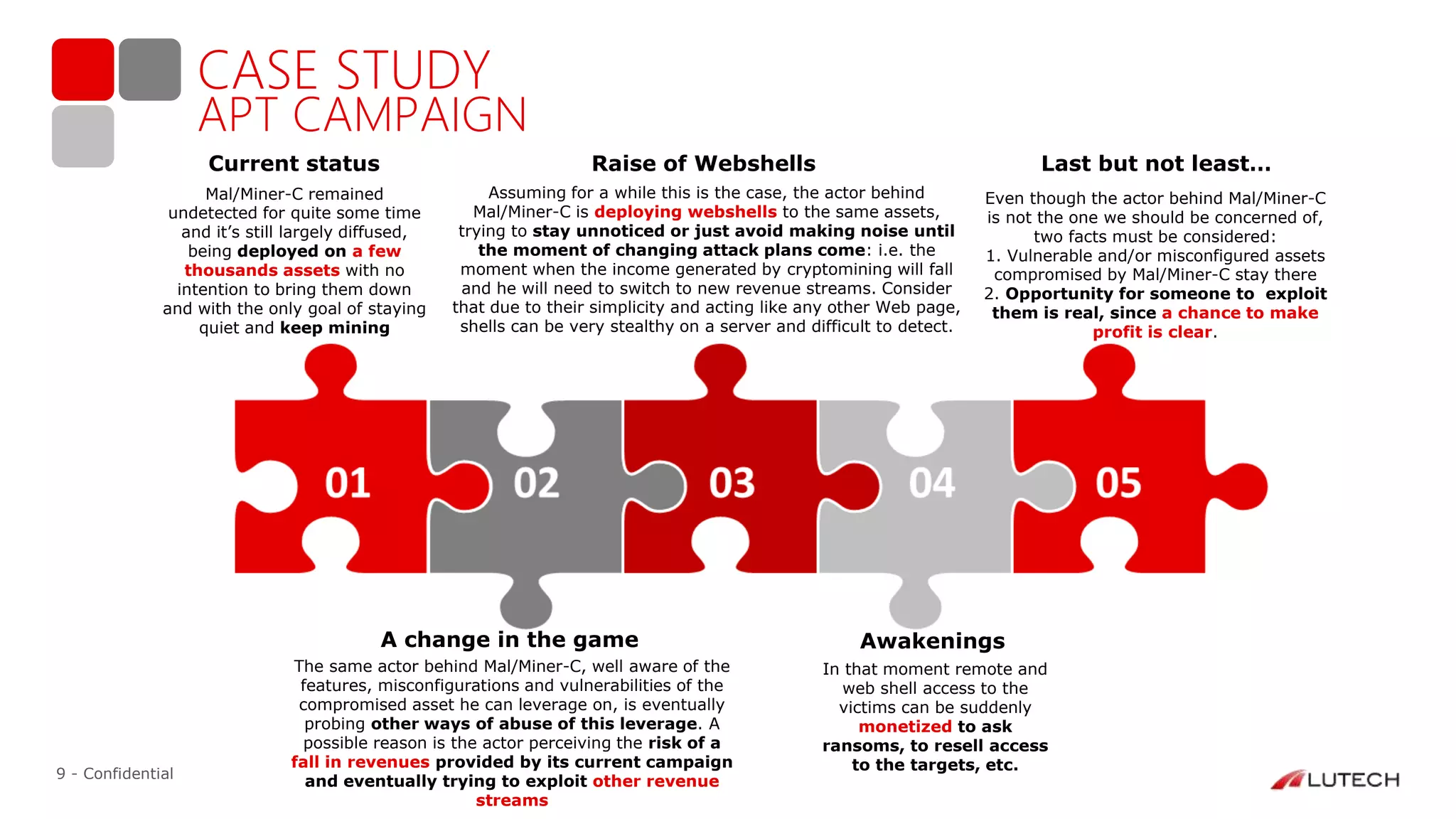
The document discusses a case study on advanced persistent threats (APTs), particularly focusing on a campaign named 'winter is coming.' It outlines the evolution of cyber threat intelligence services provided by Lutech, detailing the techniques and strategies used in monitoring and responding to such threats. The report emphasizes the importance of early detection, threat assessment, and operational collaboration to mitigate APT risks effectively.






![19 - Confidential
f.faenzi@lutech.it
@francescofaenzi
CONTACTS & OFFICES @Lutechspa
@Lutech_TMS
www.lutech.it
wwww.lutech.co.uk
solutioncenter.lutech.it
info@lutech.it
Via Milano 150,
20093 Cologno Monzese [MI]
+39 02 25427011 Phone
+39 02 25427090 Fax
HEADQUARTER
TECHNICAL
DEPARTMENT
Via W.A. Mozart, 47
20093 Cologno Monzese [MI]
ROME
OFFICE
Other OFFICES in
Italy
Milano, Modena, Firenze, Roma,
Pomezia, Napoli, Bari, Catania
Via A. Mantegna, 4 | P
arco Leonardo
00054 Fiumicino [RM]
+39 06 227501 Phone
+39 06 22771542 Fax
Nucleus Innovation Centre
Brunel Way, Dartford, Kent DA1
5GA
United Kingdom
+44 208 181 4321 Phone
LUTECH UK](https://image.slidesharecdn.com/02-170512143001/75/Advanced-Persistent-Threat-in-ICS-SCADA-IOT-world-a-case-study-19-2048.jpg)