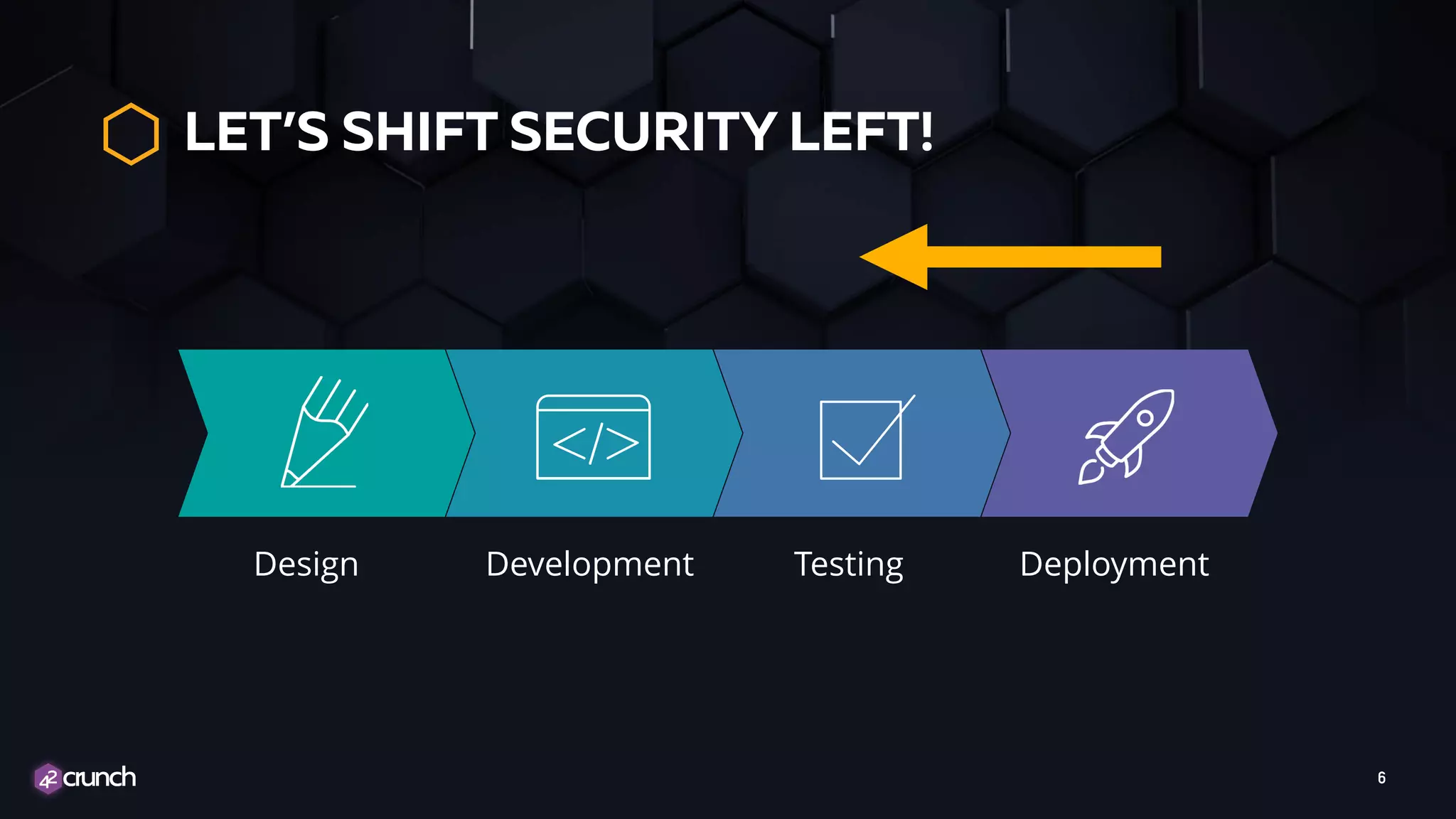
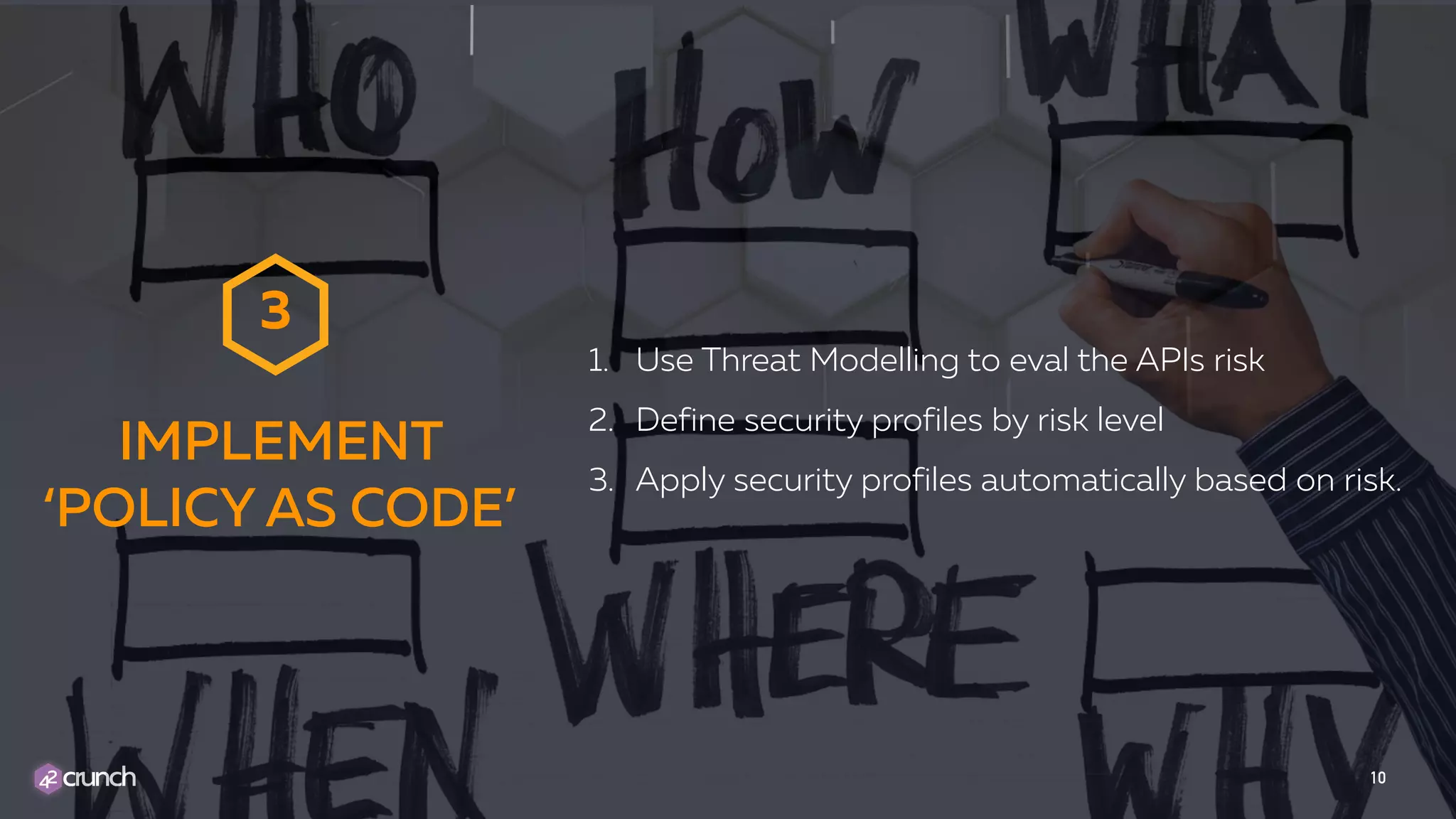
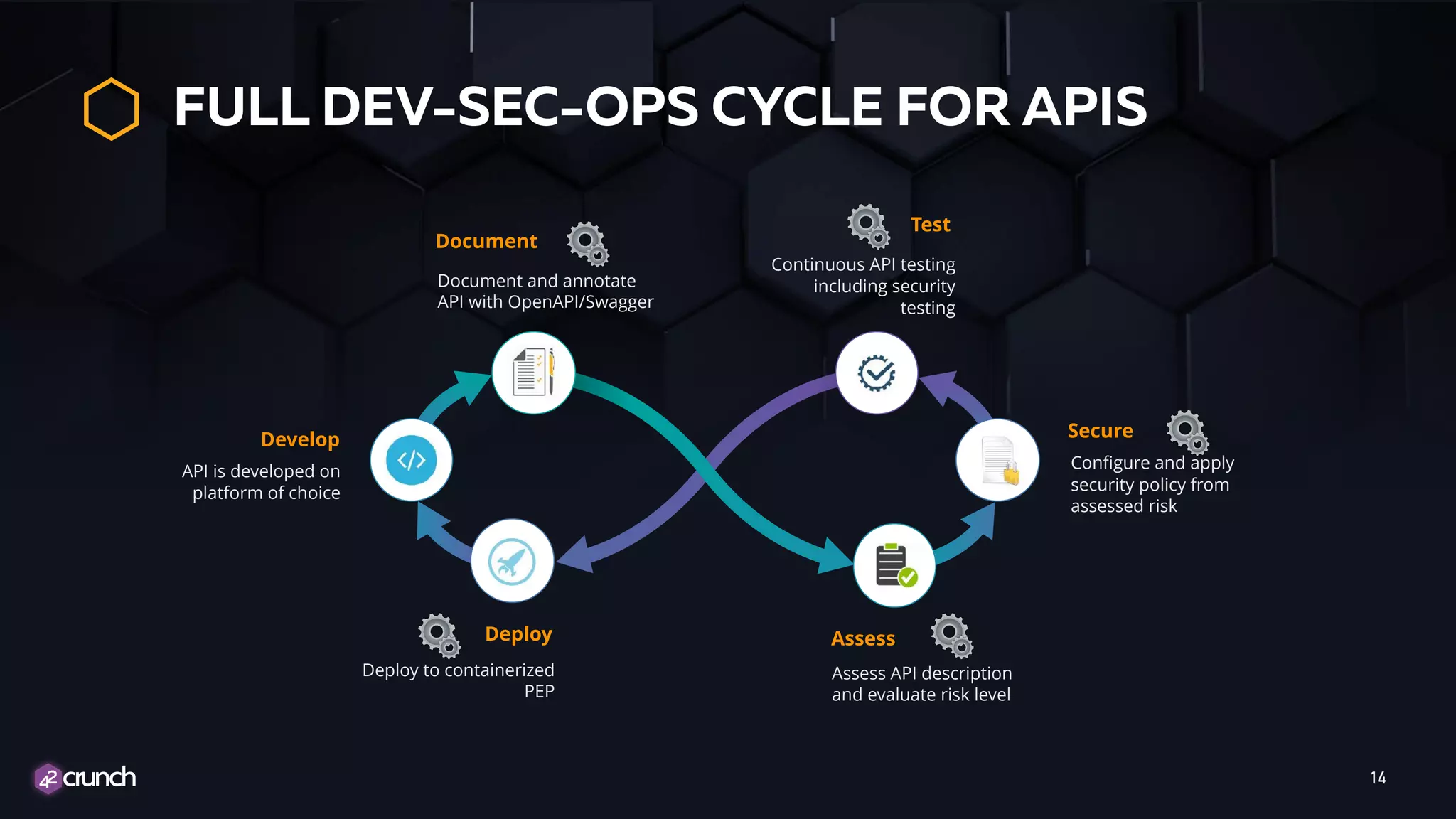
The document discusses the integration of security into the DevSecOps process for APIs, emphasizing the need for security measures to be implemented throughout the software development lifecycle. Key strategies include translating security requirements into code, utilizing threat modeling, and applying automated security profiles based on risk levels. It stresses the importance of collaboration among development, operations, and security teams to ensure comprehensive risk management and response.