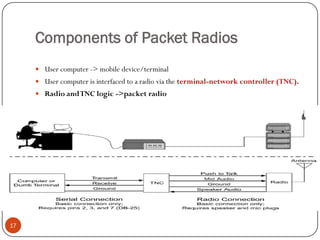
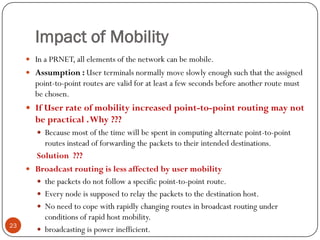
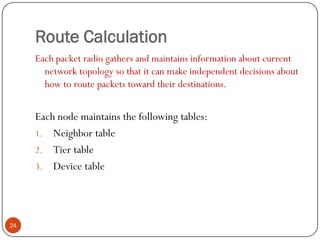
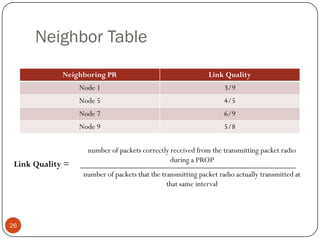
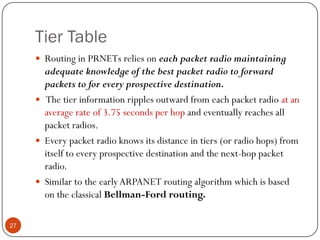
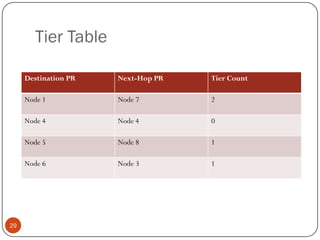
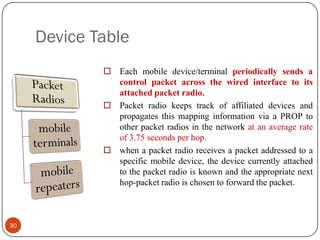
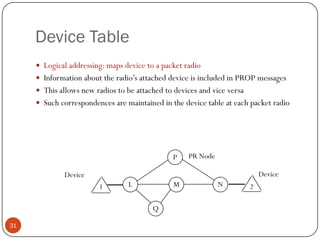
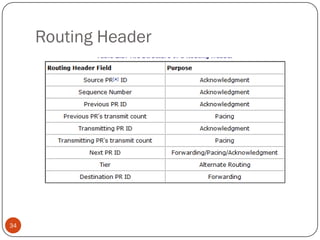
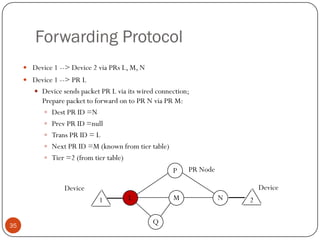
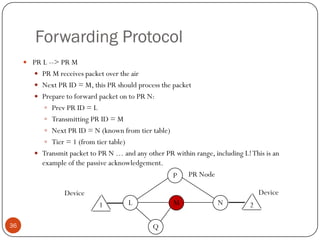
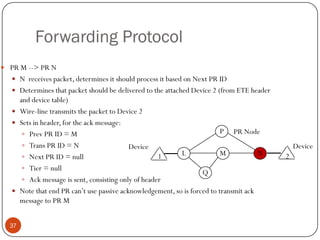
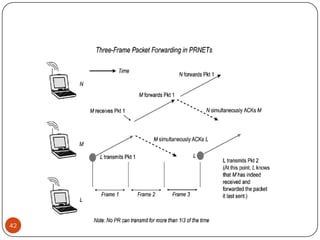
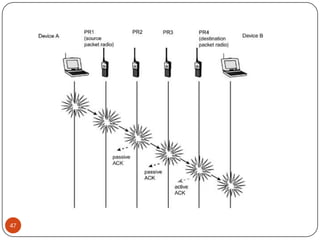
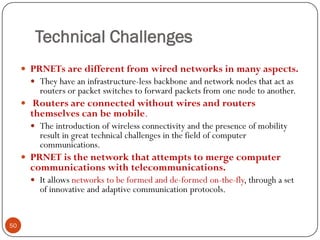
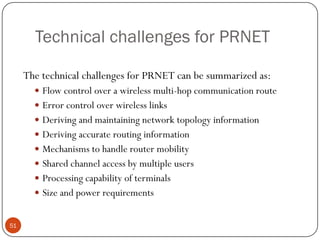
This document discusses the origins and development of ad hoc networks. It describes how packet radio networks (PRNETs) in the 1970s, developed by DARPA, were the first generation of ad hoc networks. PRNETs used multi-hop routing between mobile radio terminals and packet radios to communicate without fixed infrastructure. The document outlines the key components and routing techniques of PRNETs, including point-to-point and broadcast routing. It also discusses how subsequent generations in the 1980s-1990s focused on improving performance, scalability, and developing commercial applications like Bluetooth.