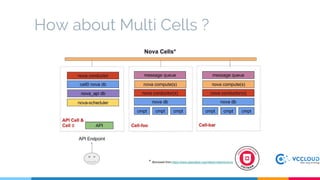
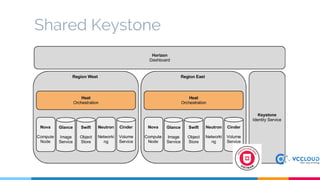
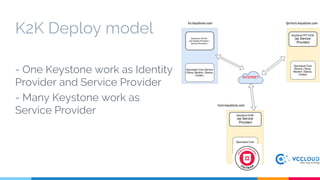
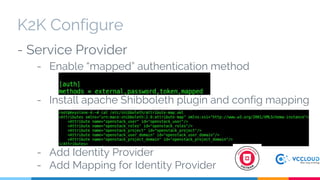
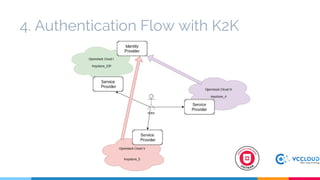
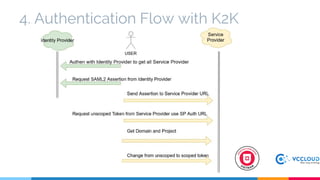
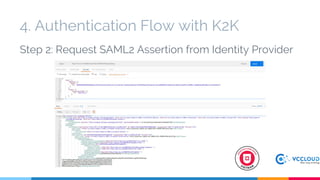
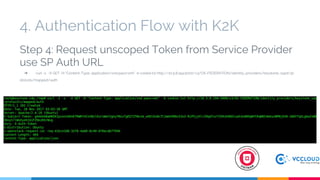
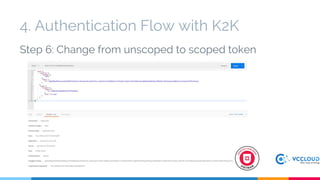
Keystone at Openstack discussed multi-site deployment models for Openstack and the problems with using a shared Keystone database across sites. It introduced Keystone to Keystone (K2K) as a solution that allows federated authentication between Keystone instances. K2K enables each Keystone to act independently while still providing cross-cloud authentication. The presentation covered K2K's authentication flow, configuration, and benefits like independent upgrades and high availability of local users even if the Identity Provider is unavailable. Future work may include high availability and disaster recovery support for the Keystone Identity Provider site.