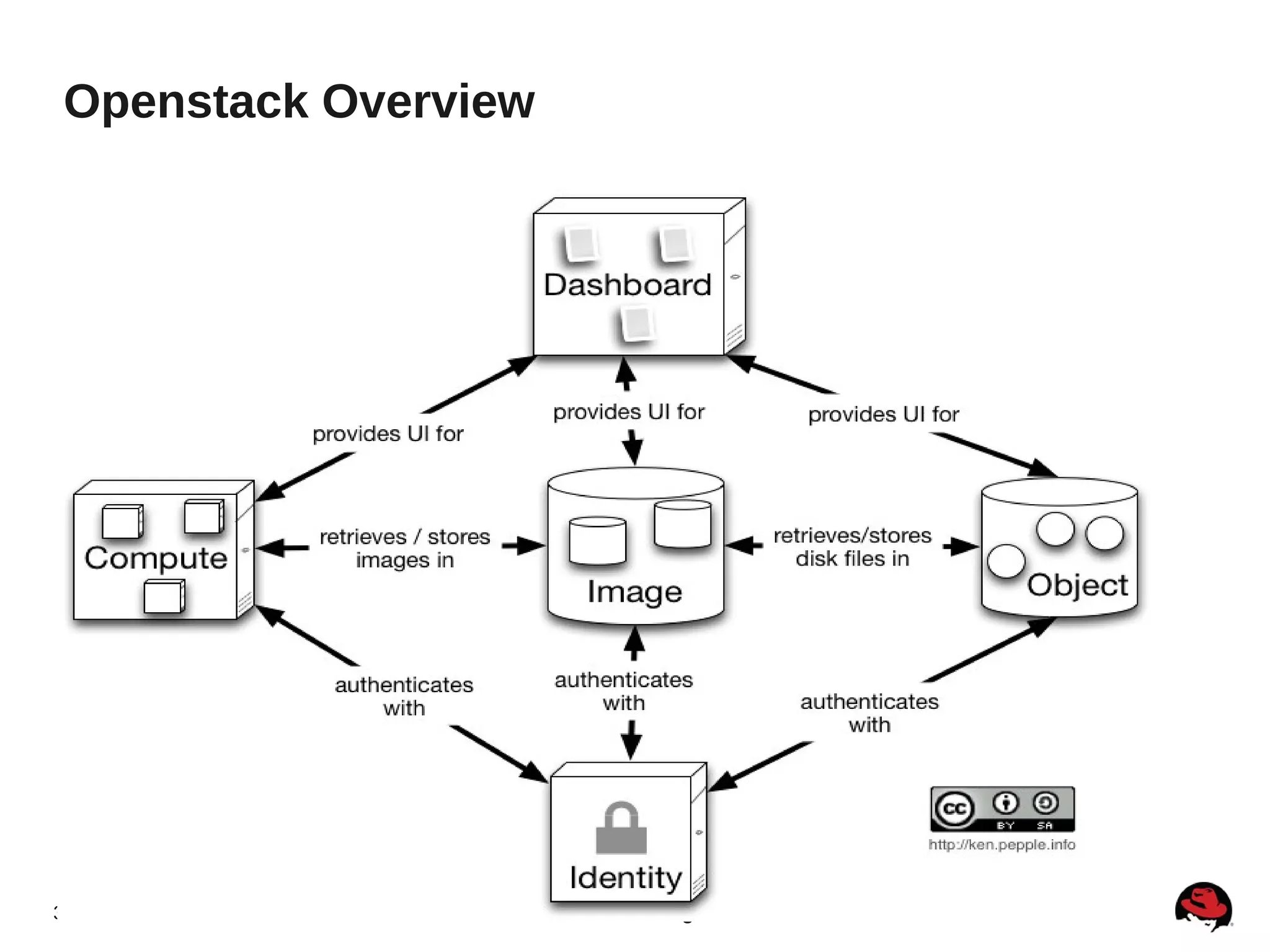
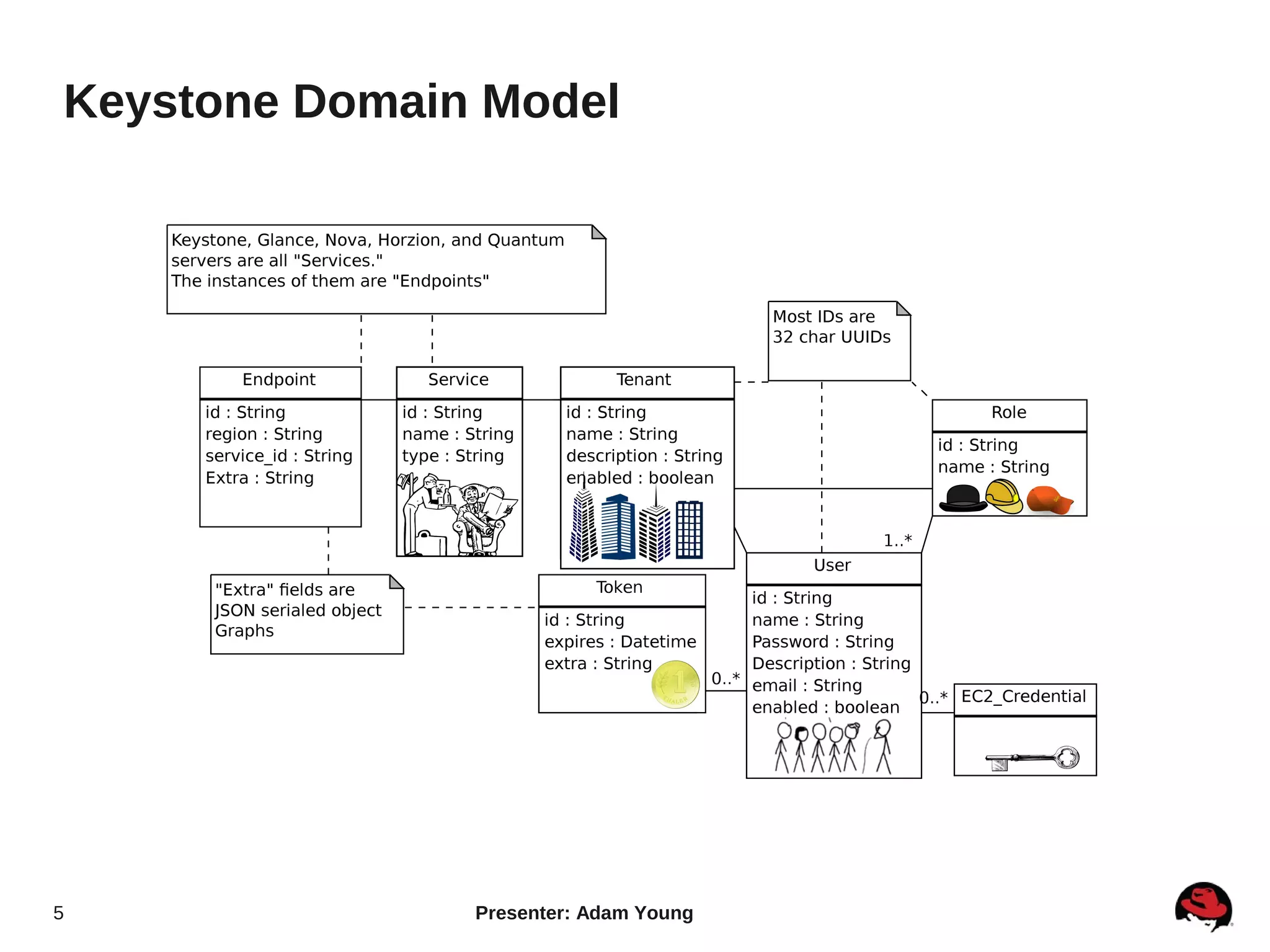
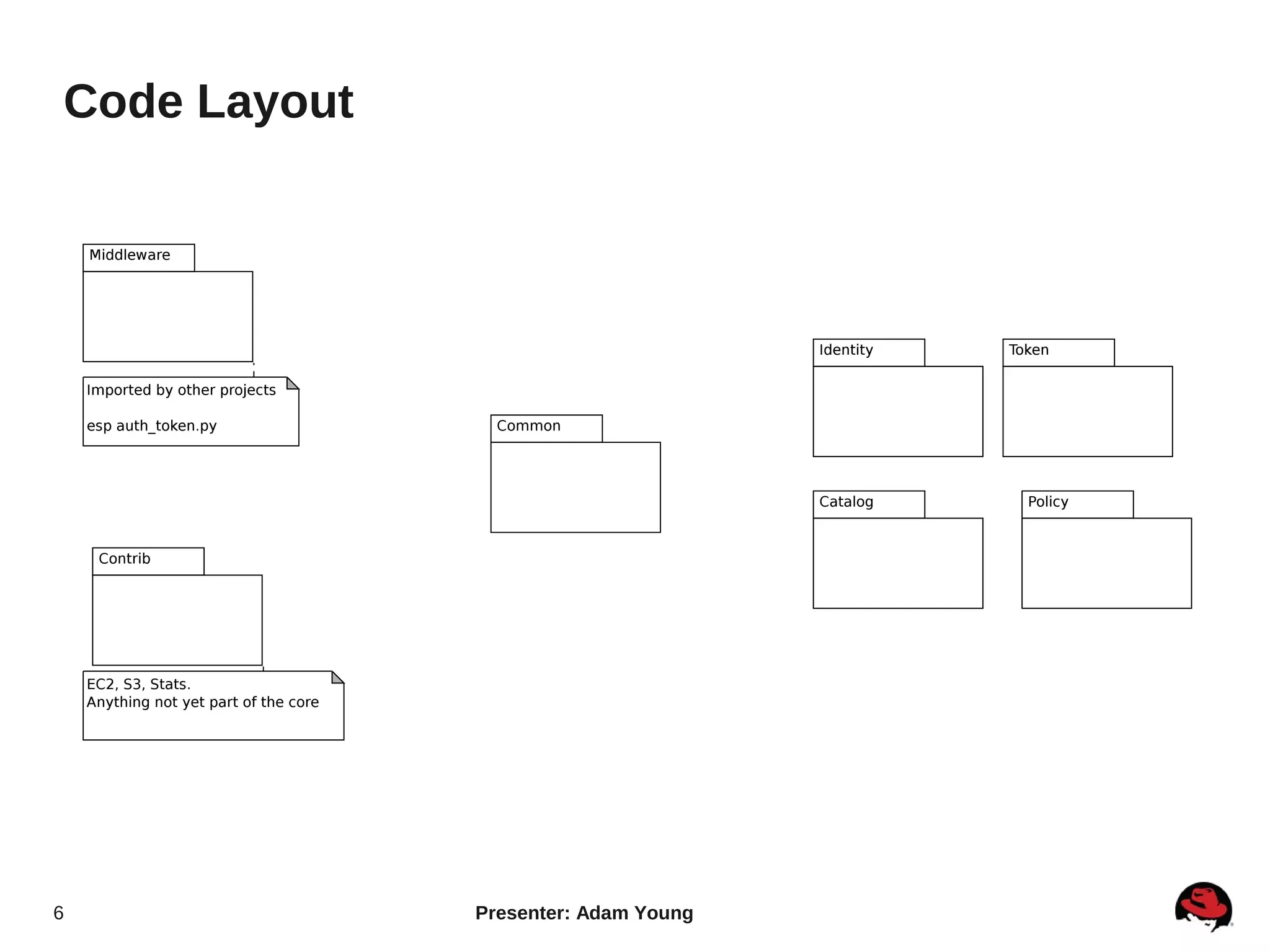
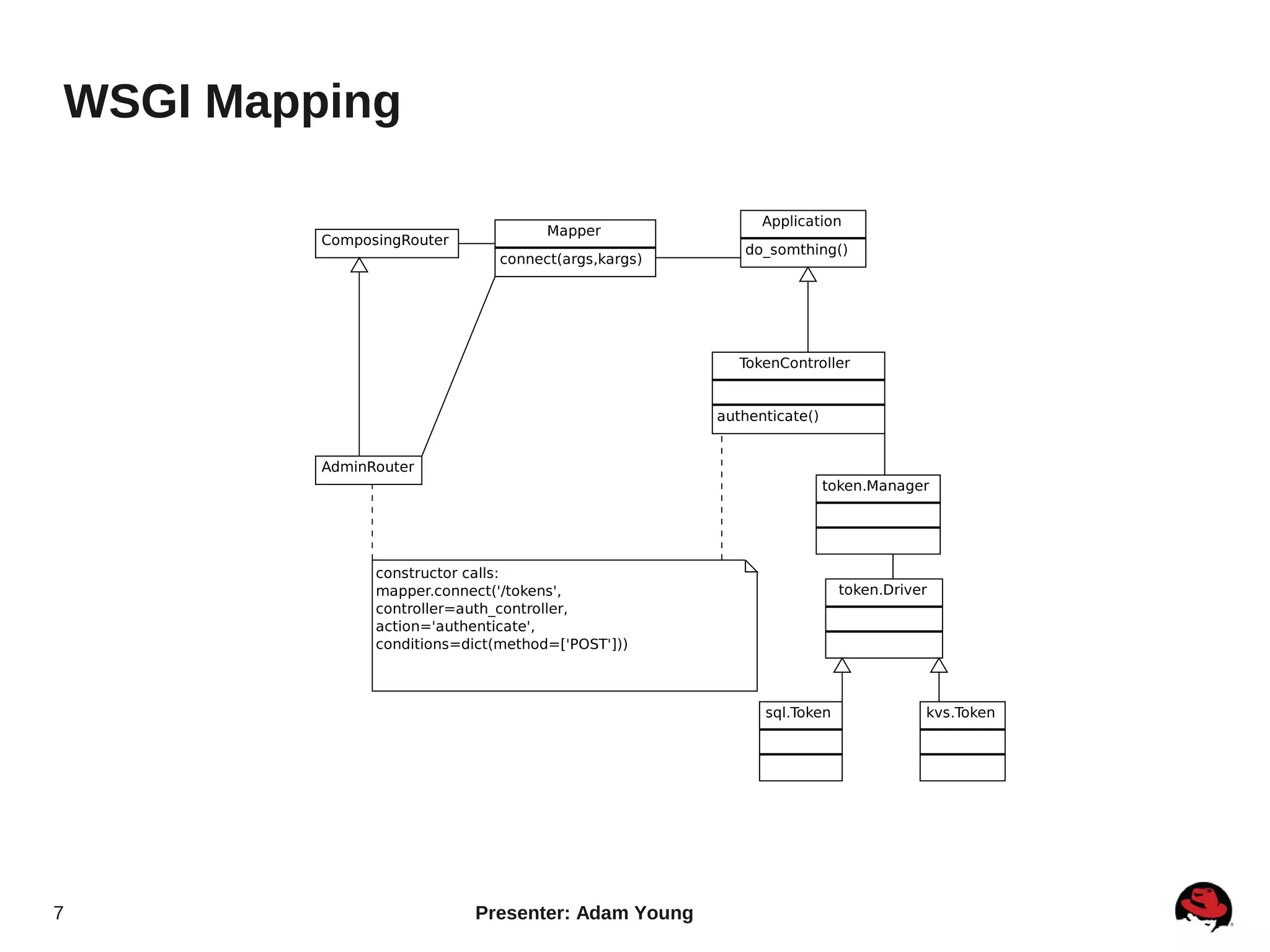
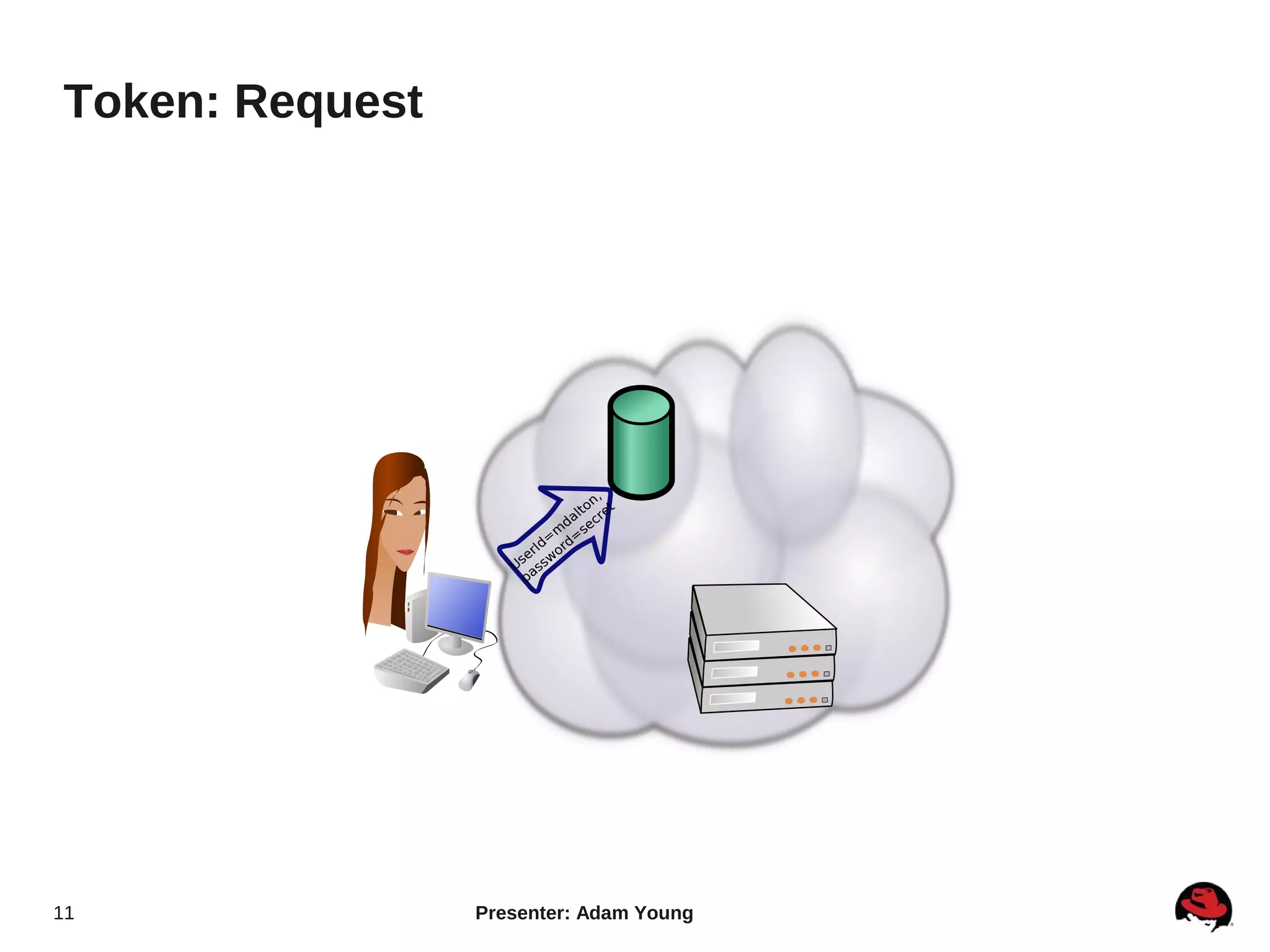
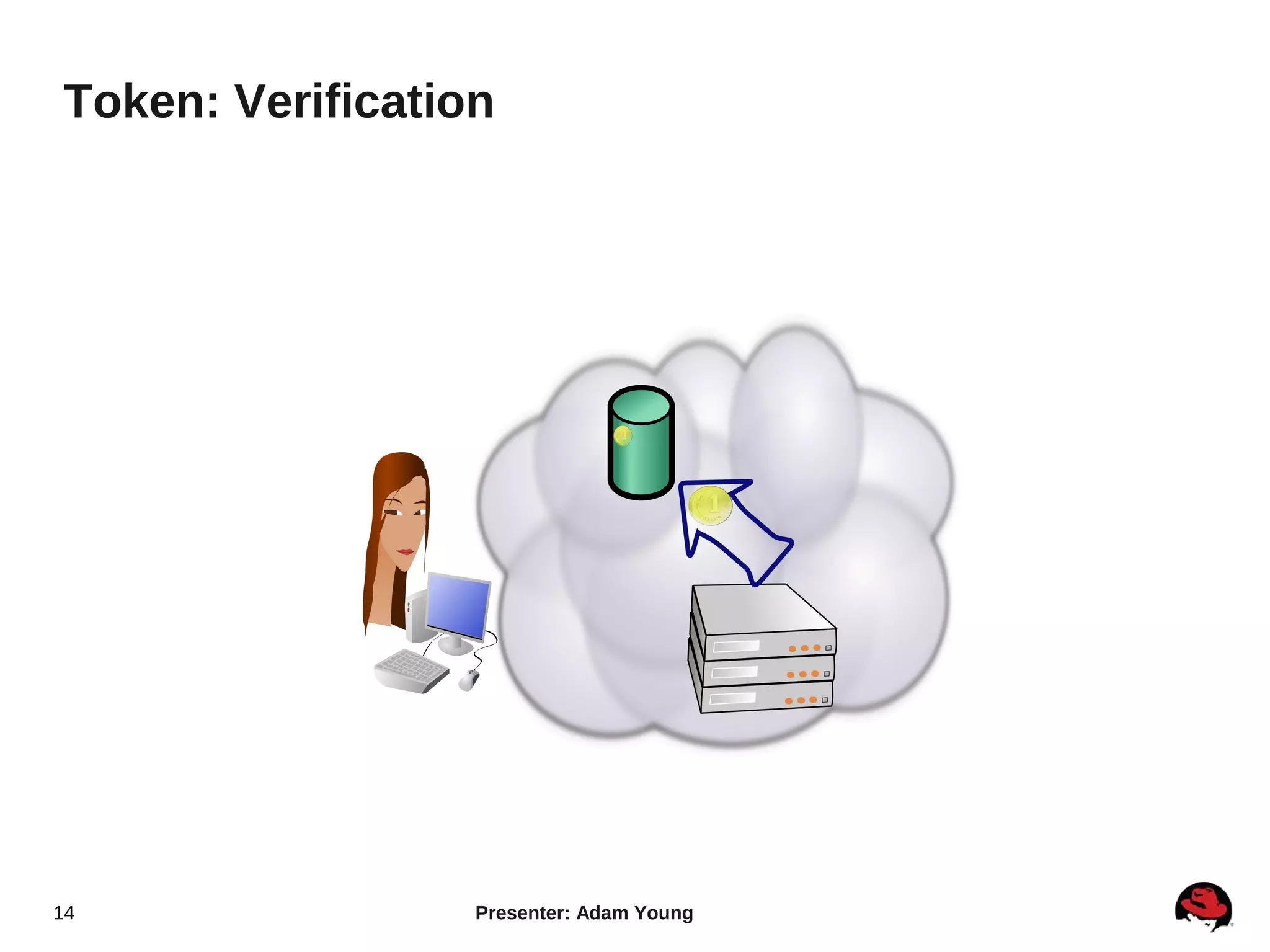
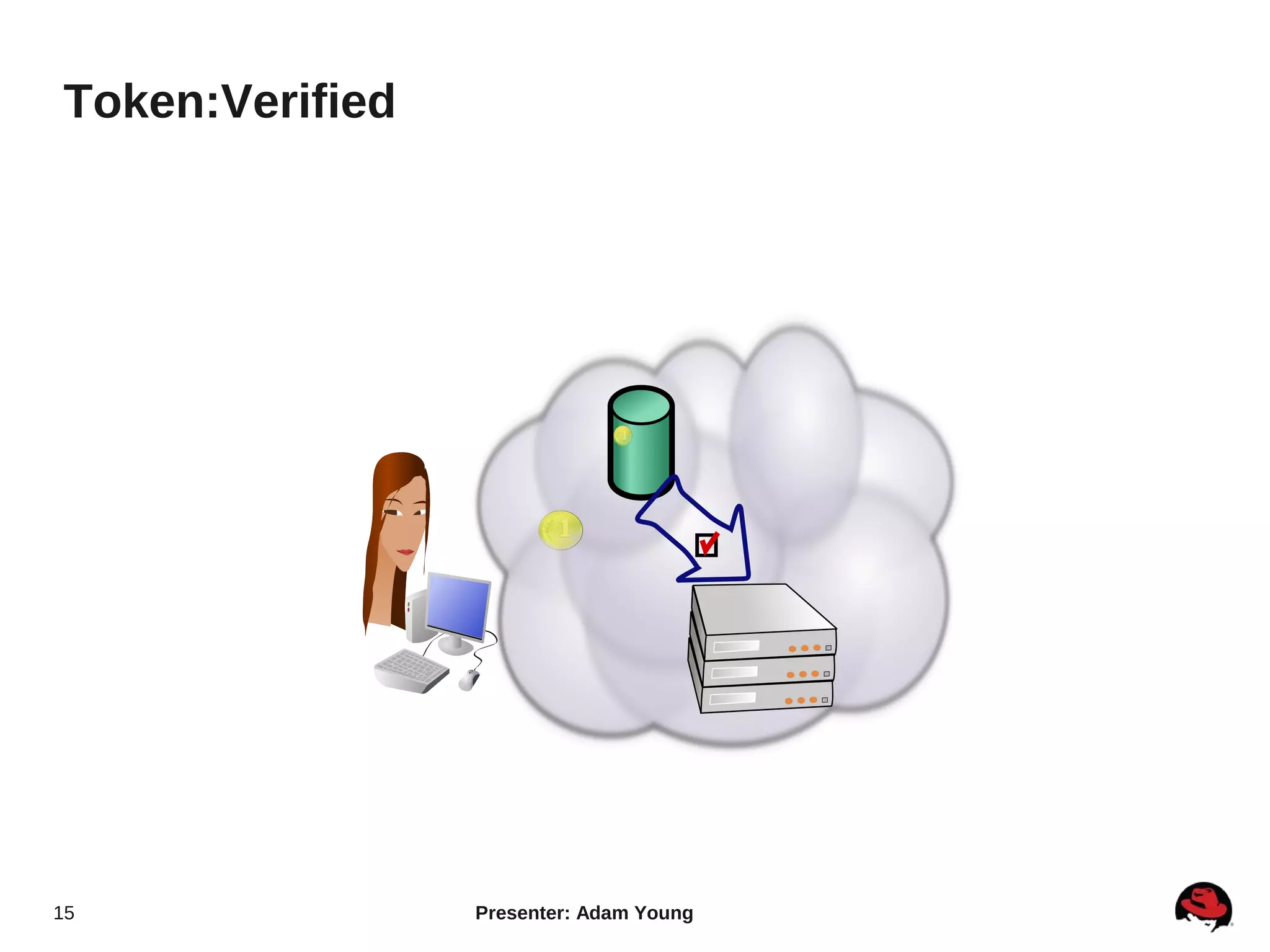
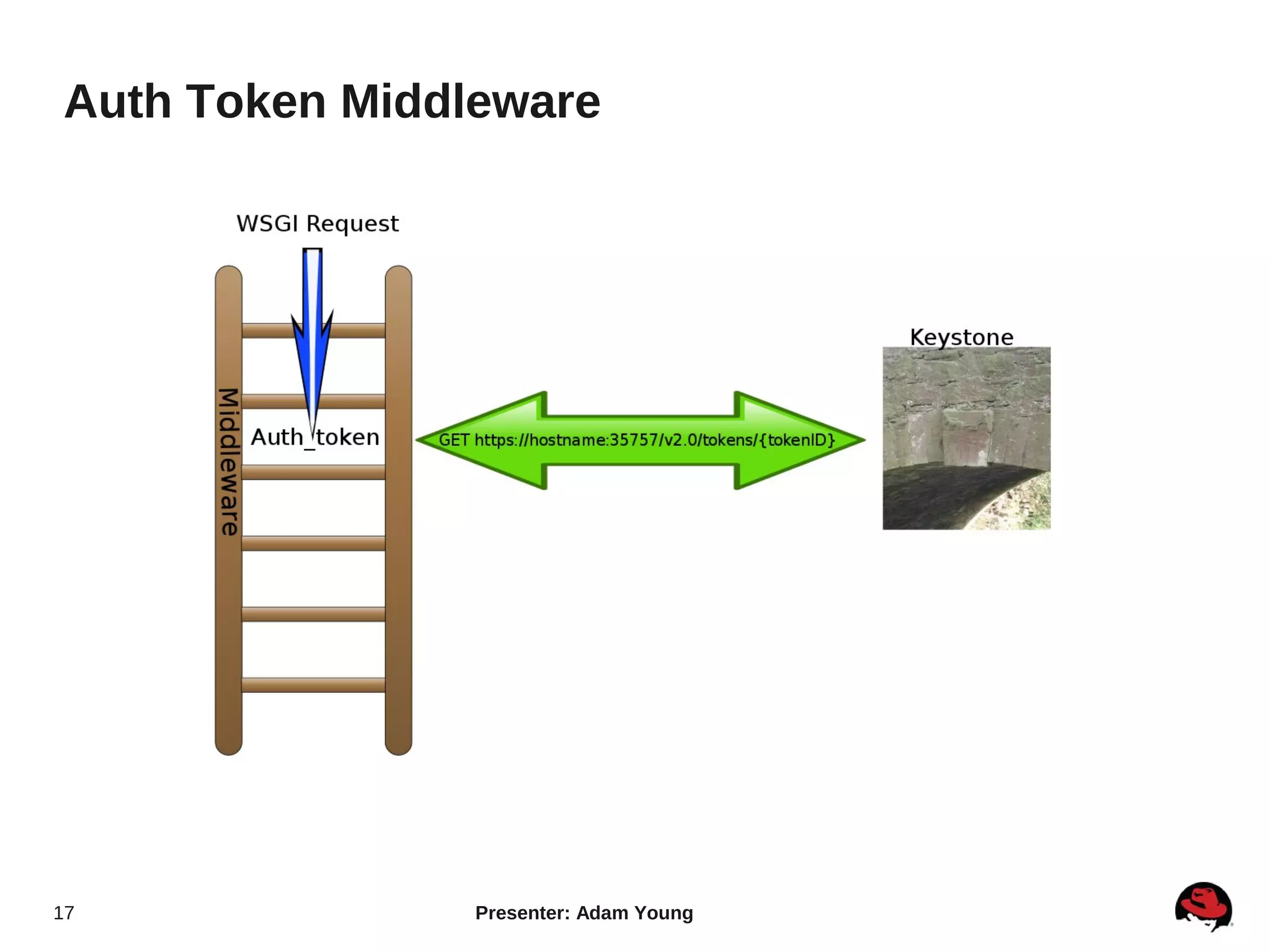
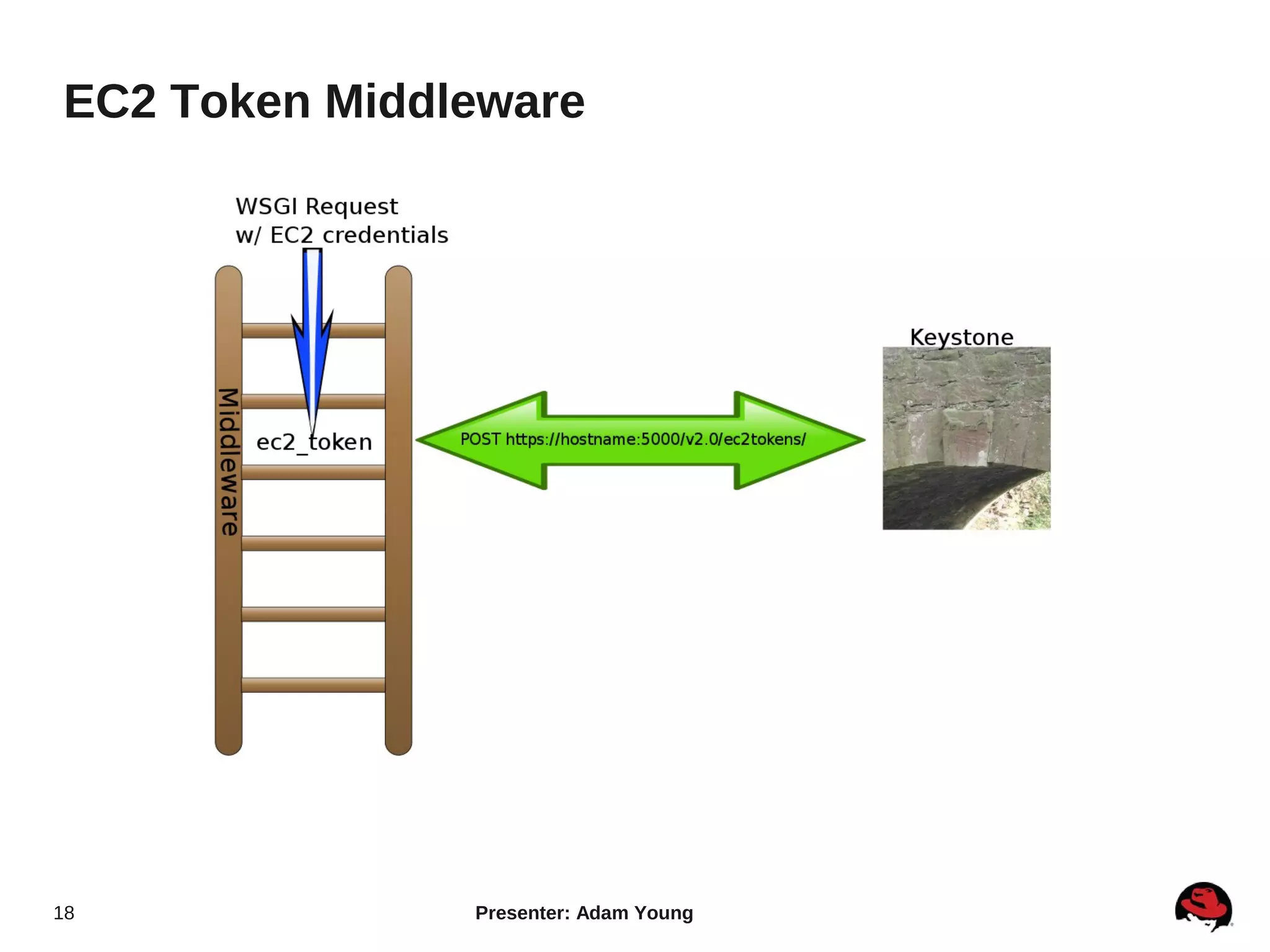
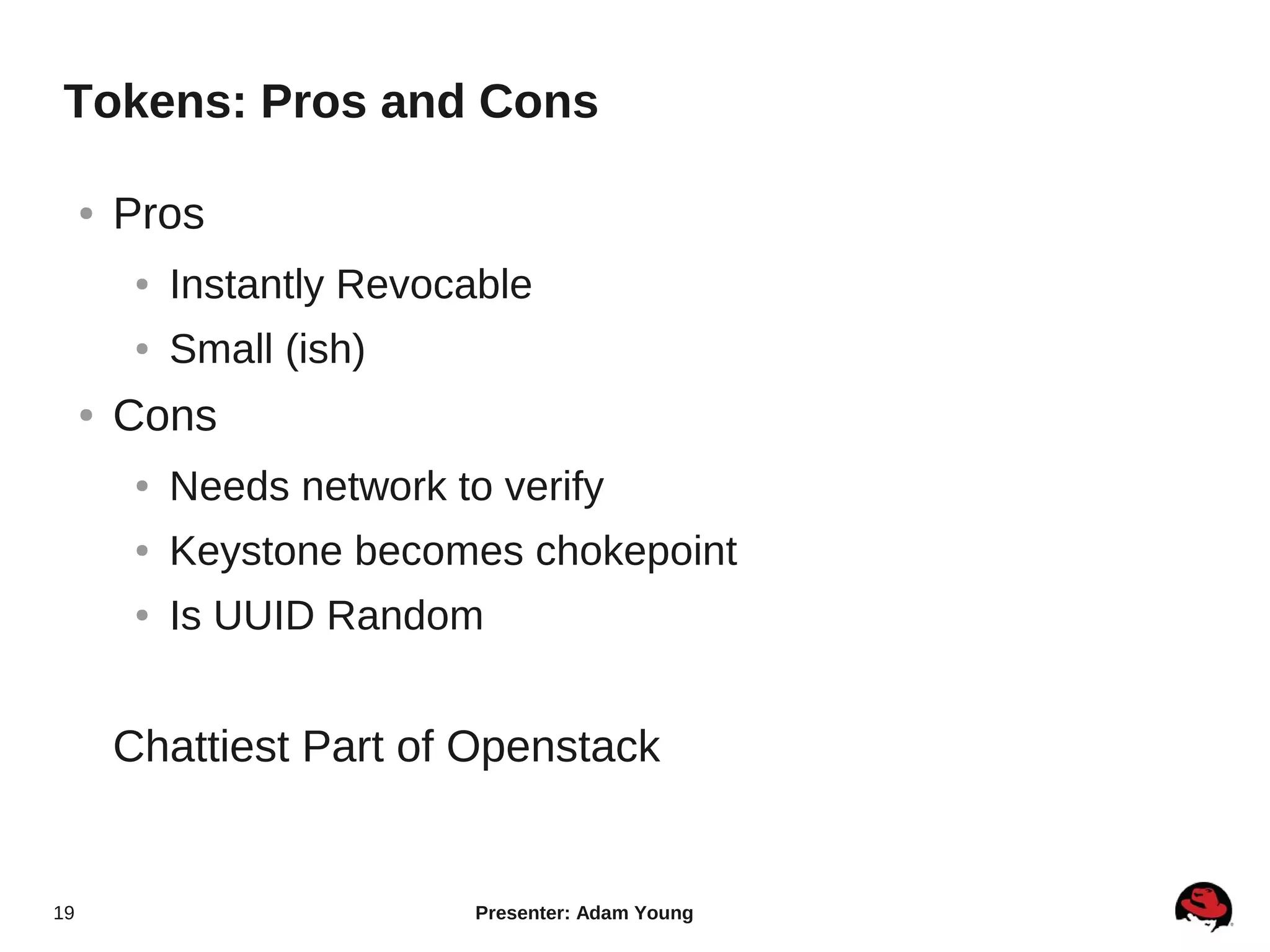
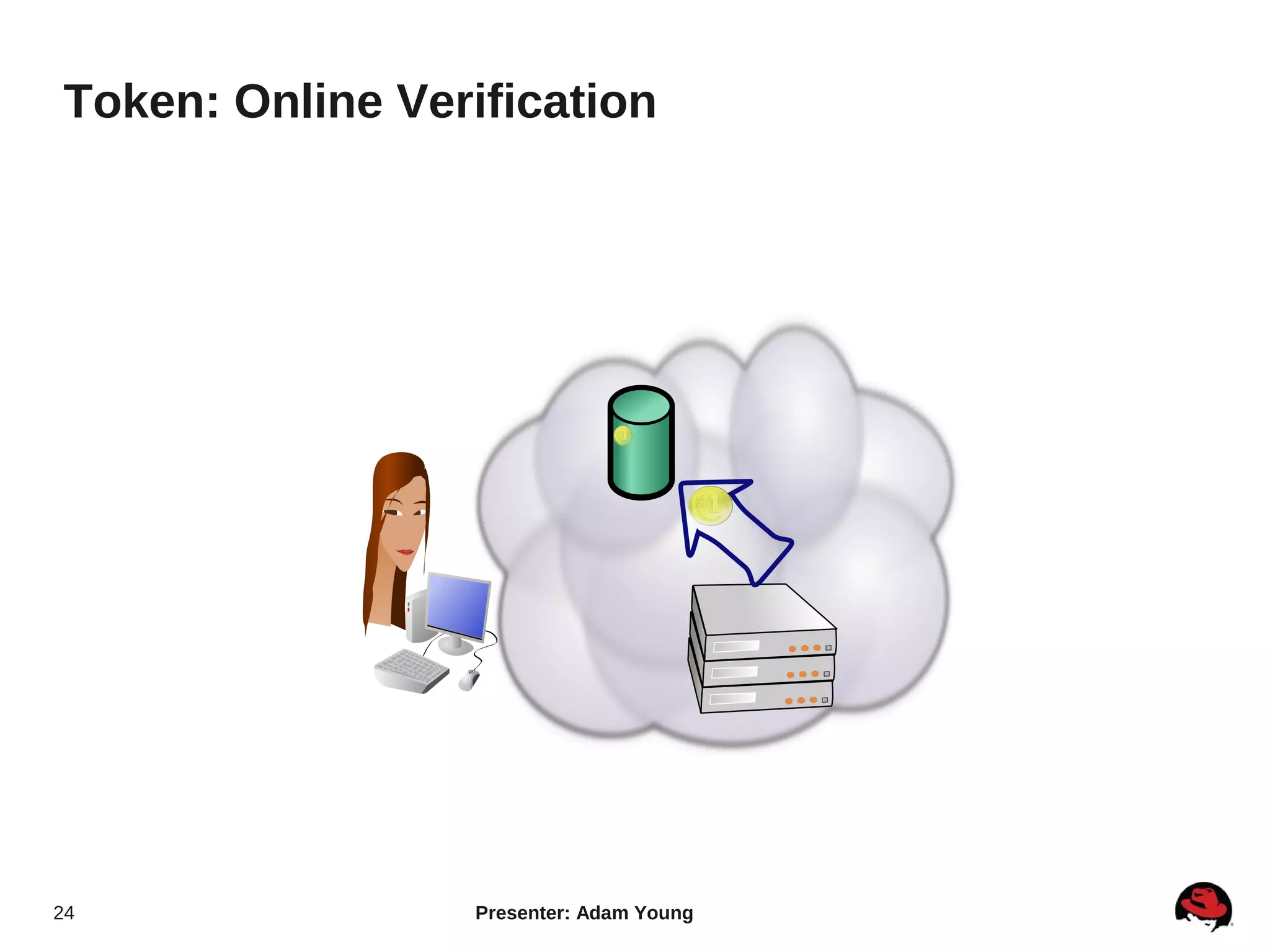
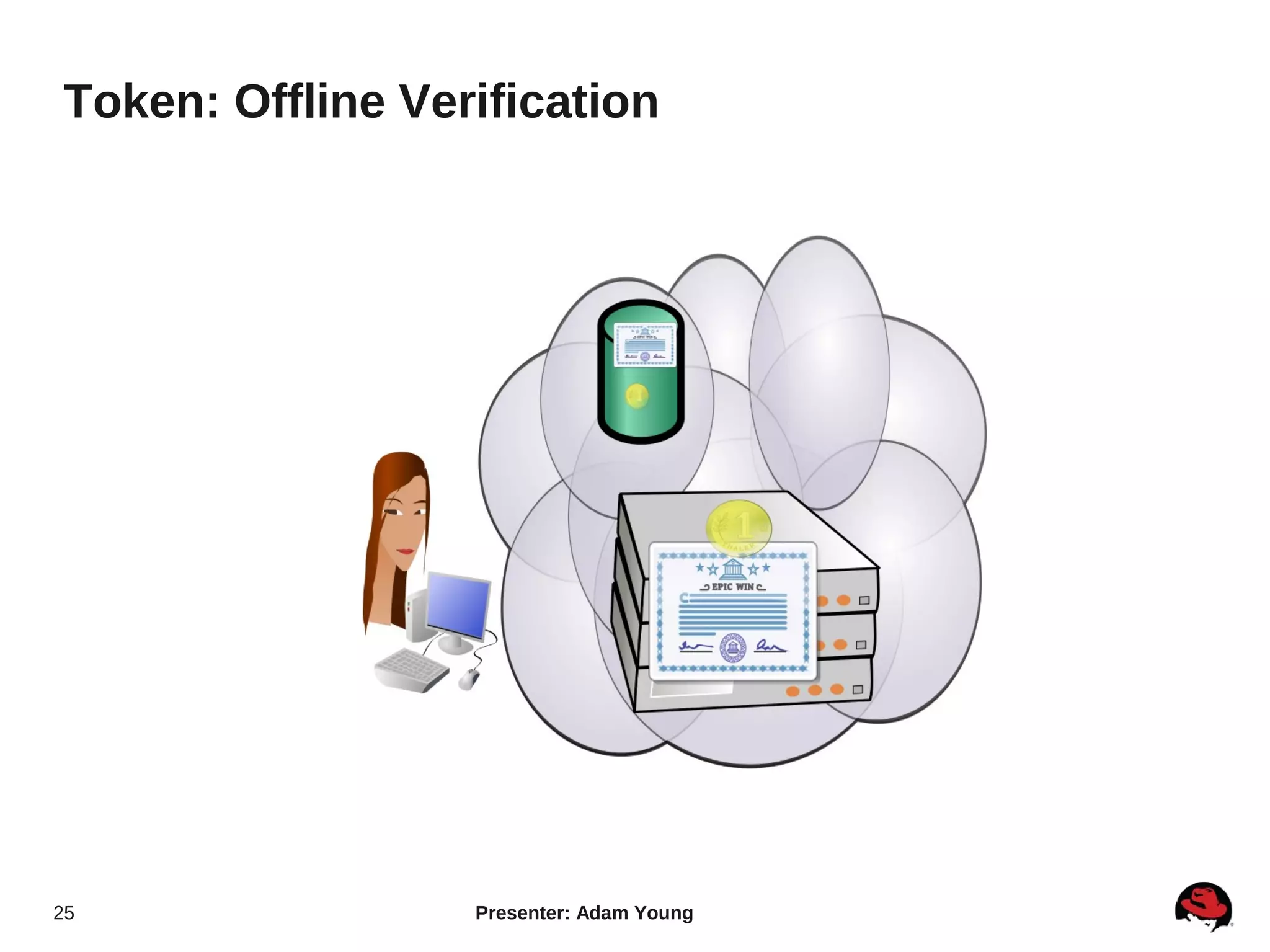
The document summarizes a presentation about the Keystone identity management service in Openstack. The presentation covered an overview of Keystone, its code layout and domain model, how it uses tokens for authentication and authorization, supported backends for persistence, and upcoming features like API version 3 and expanded support for domains, policies, and PKI signed tokens. The presentation concluded with links to more information on Keystone and its roadmap.