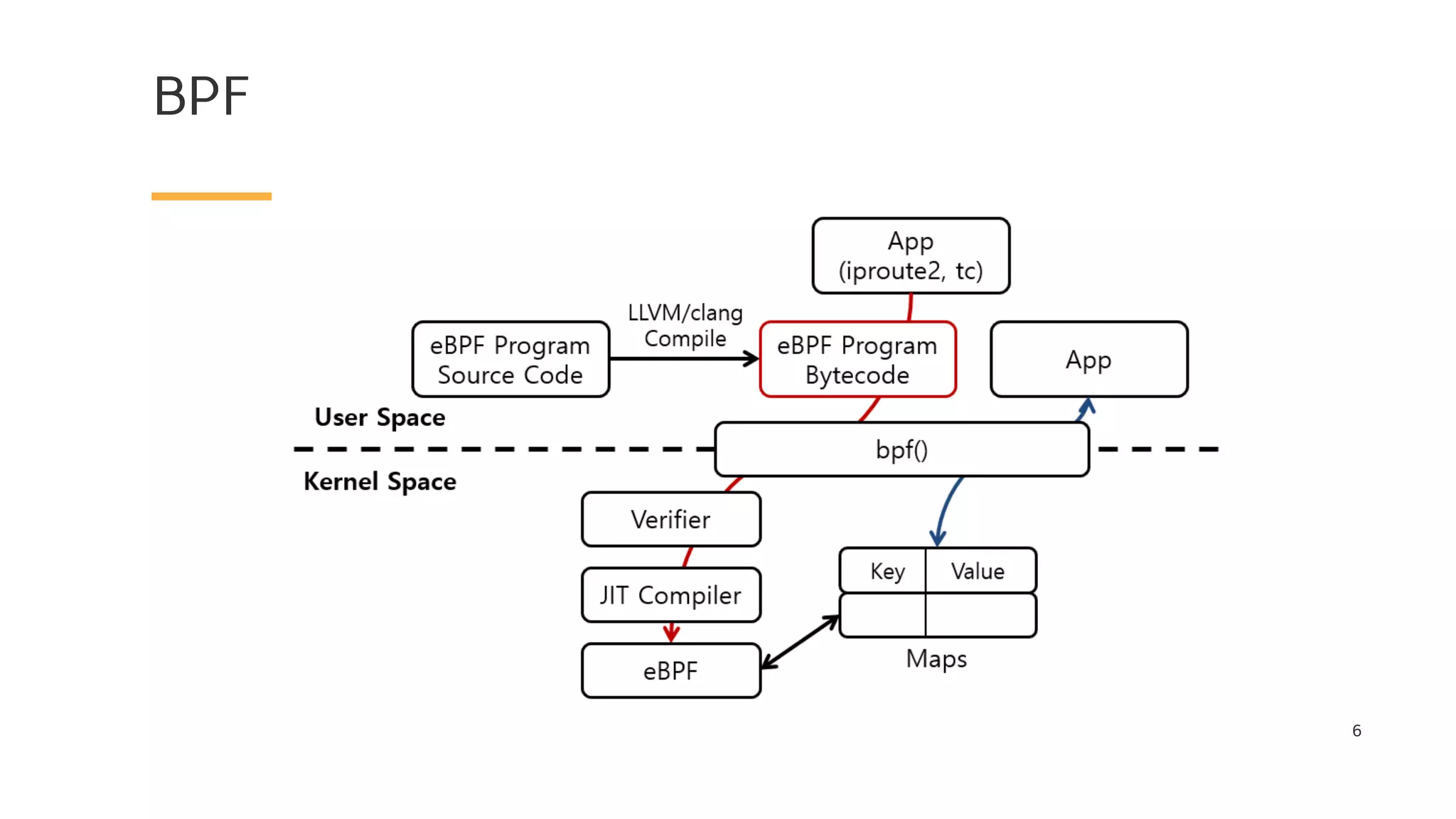
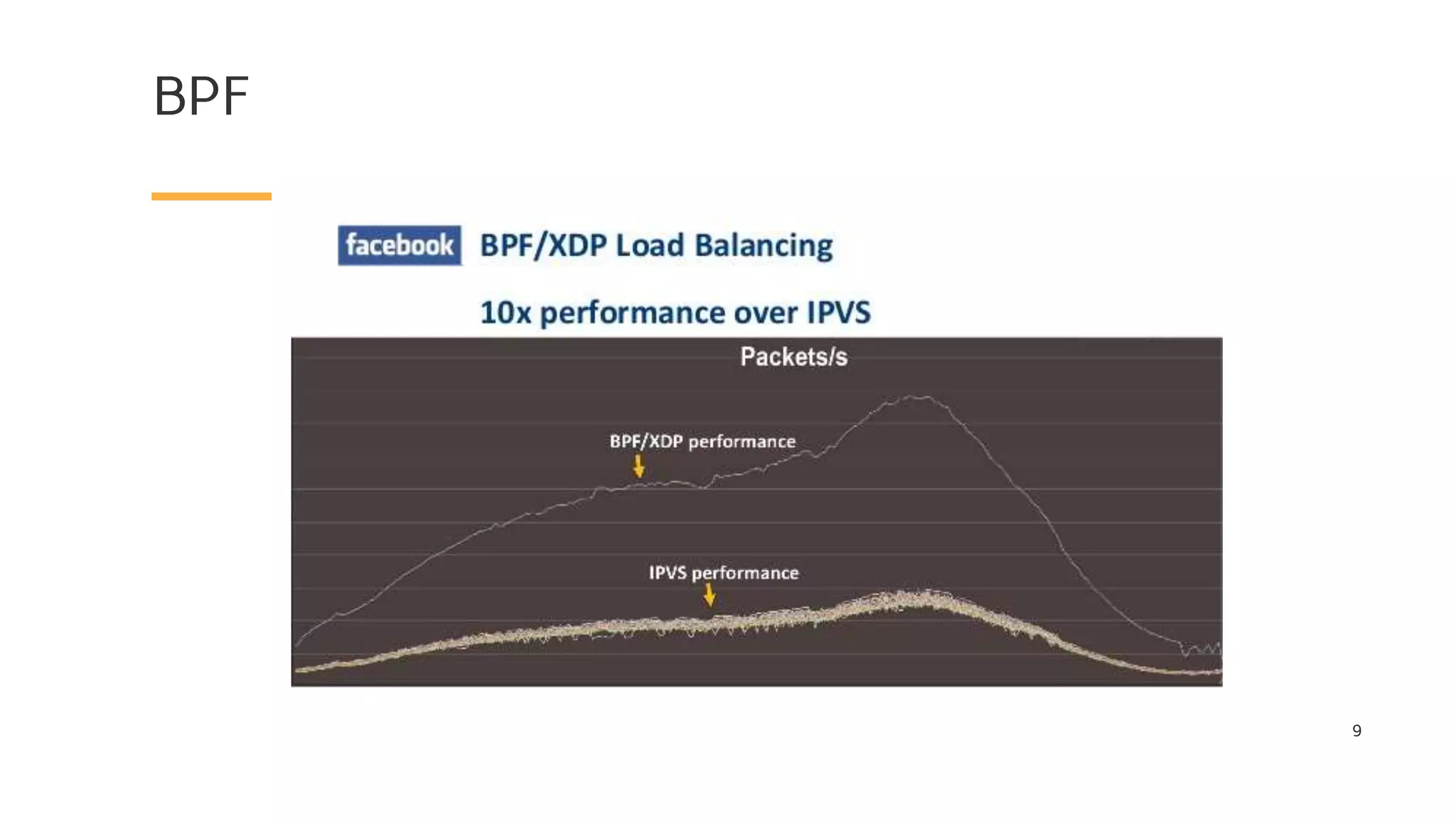
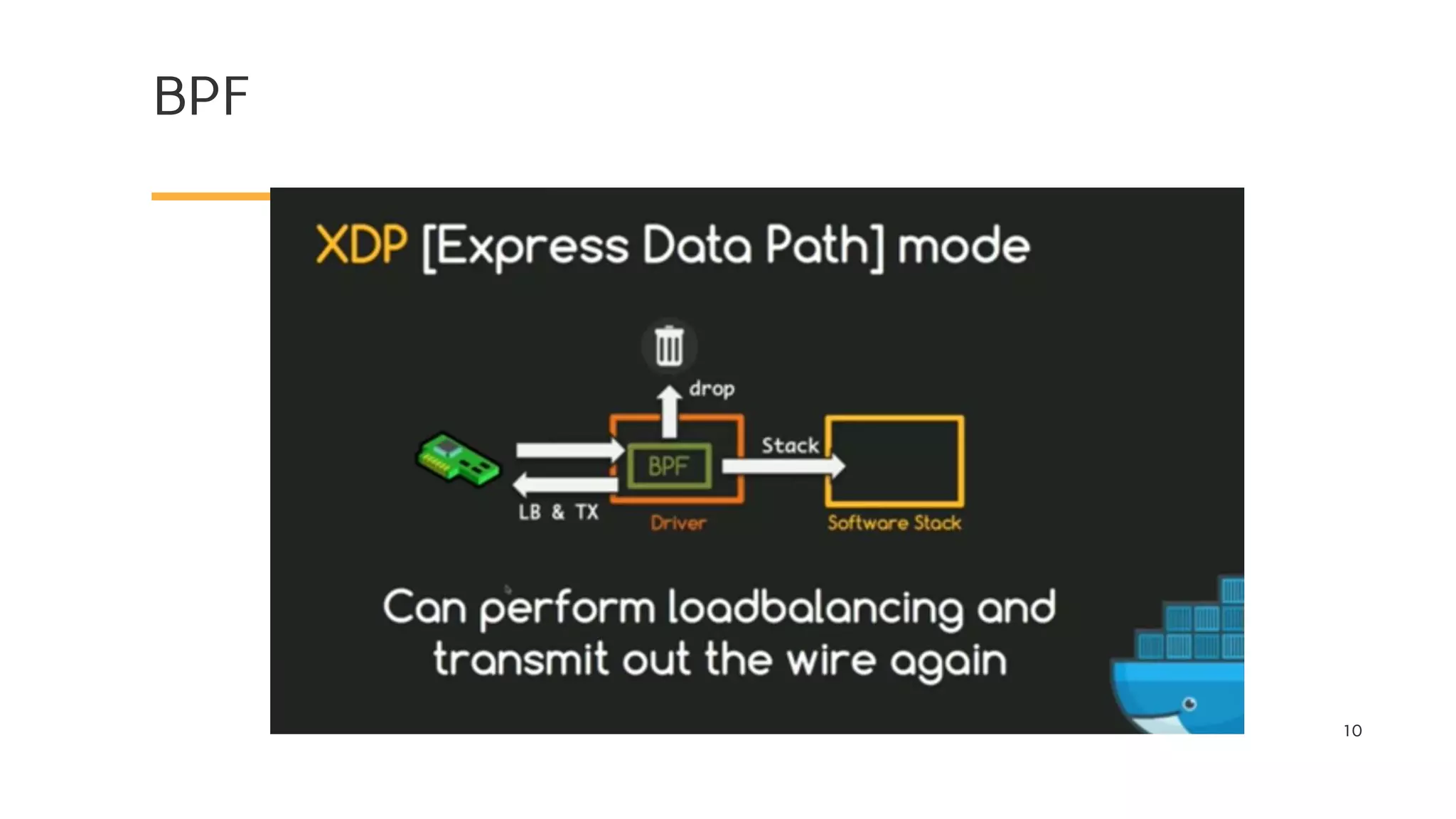
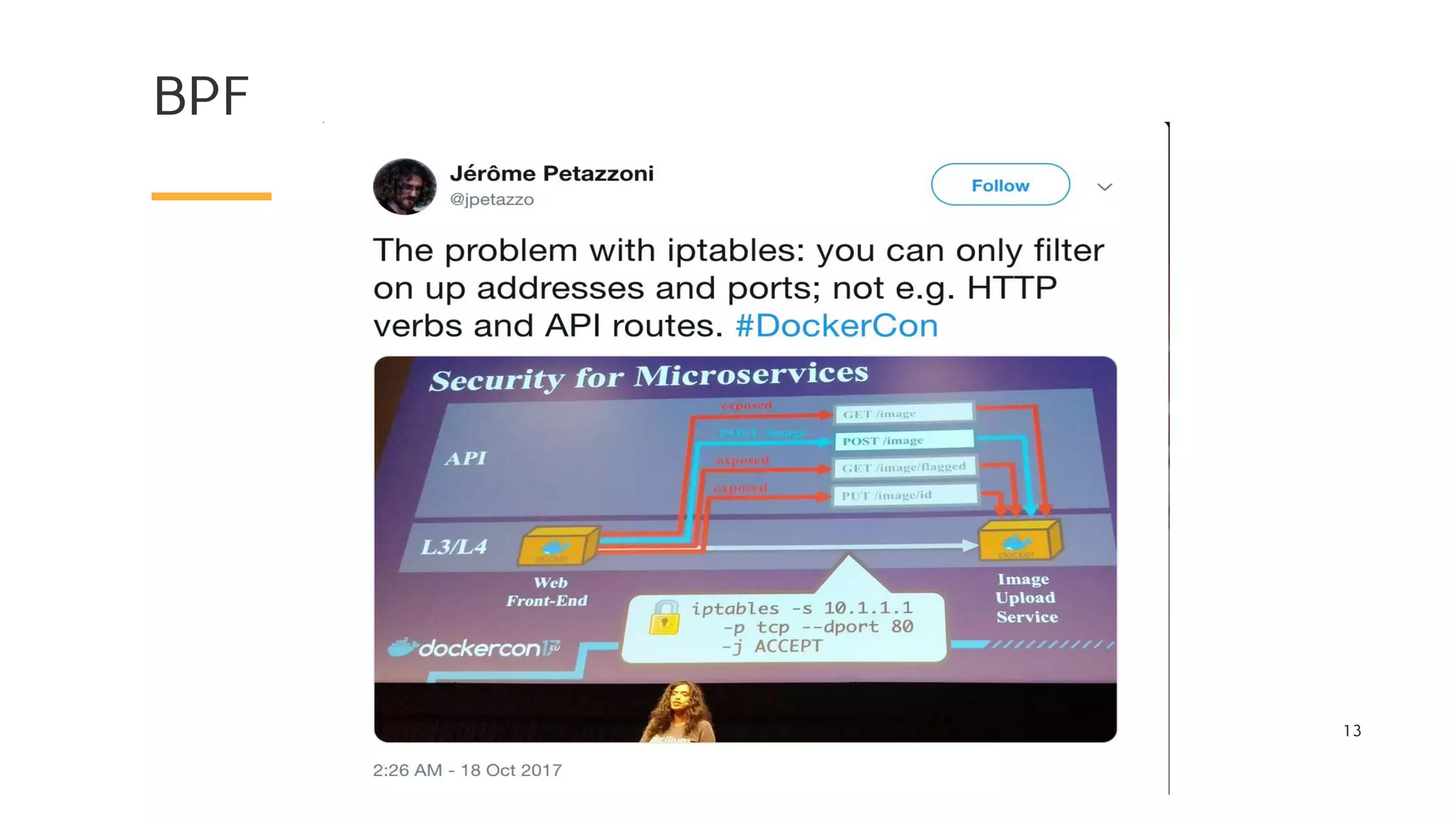
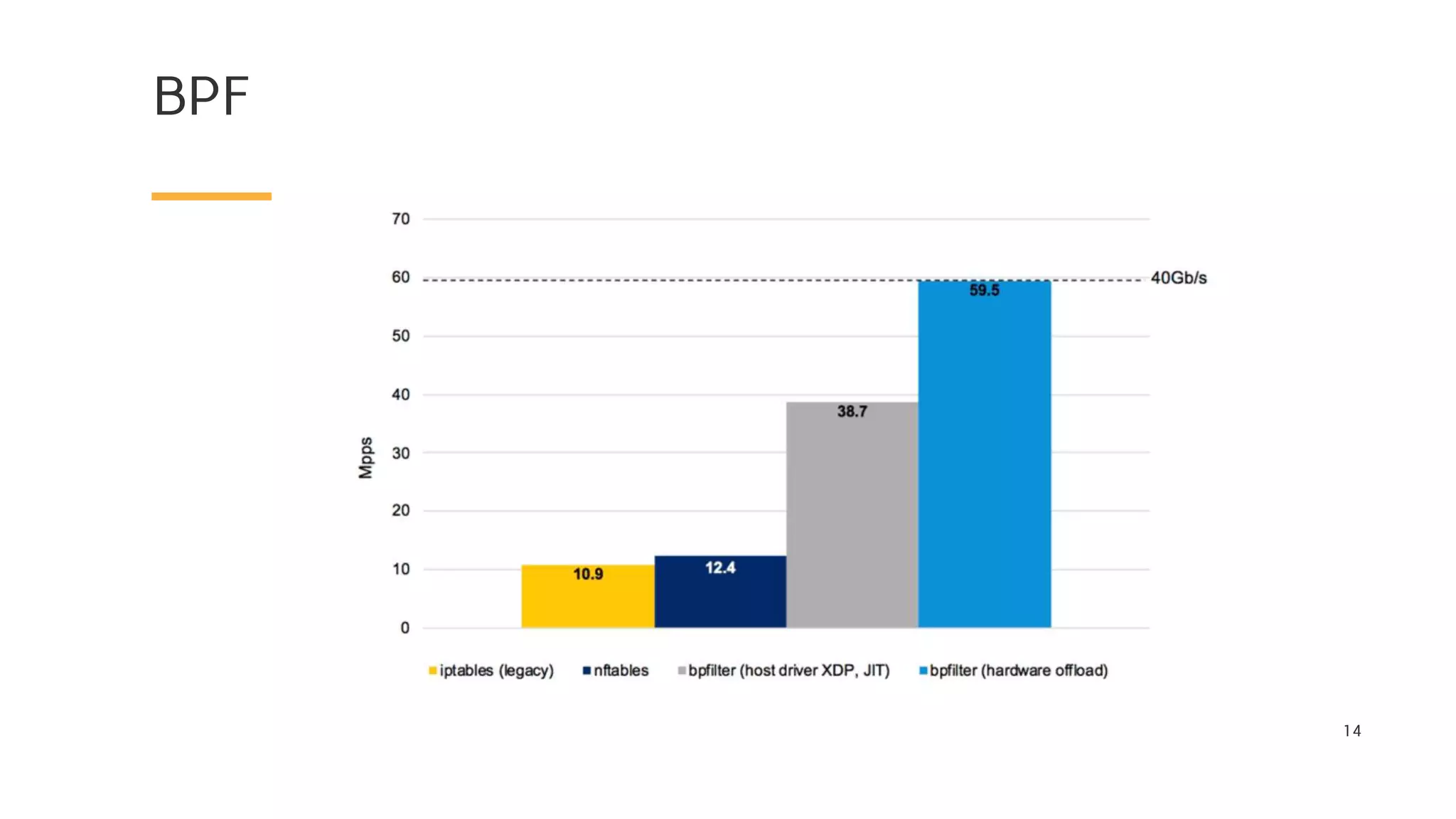
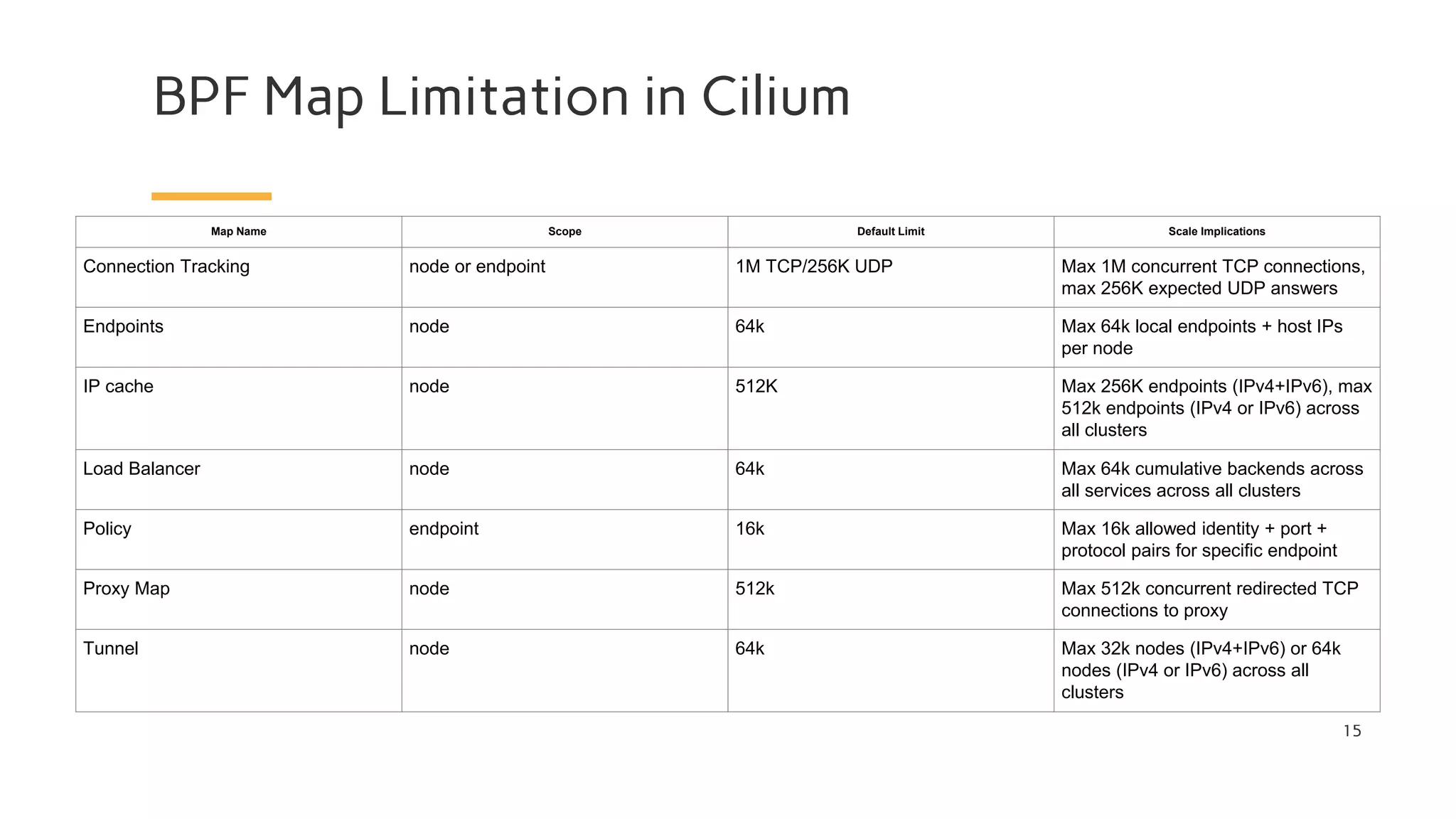
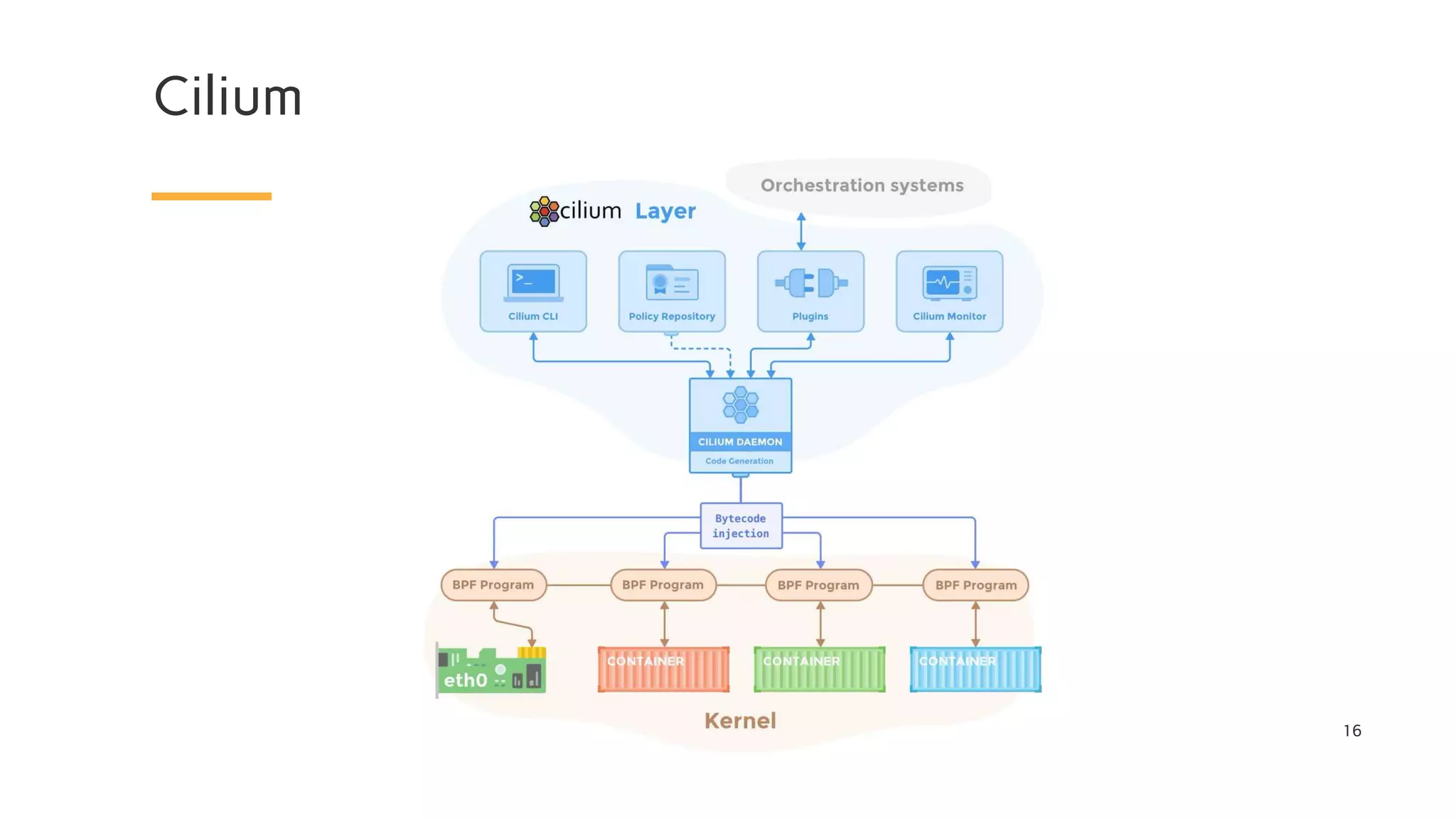
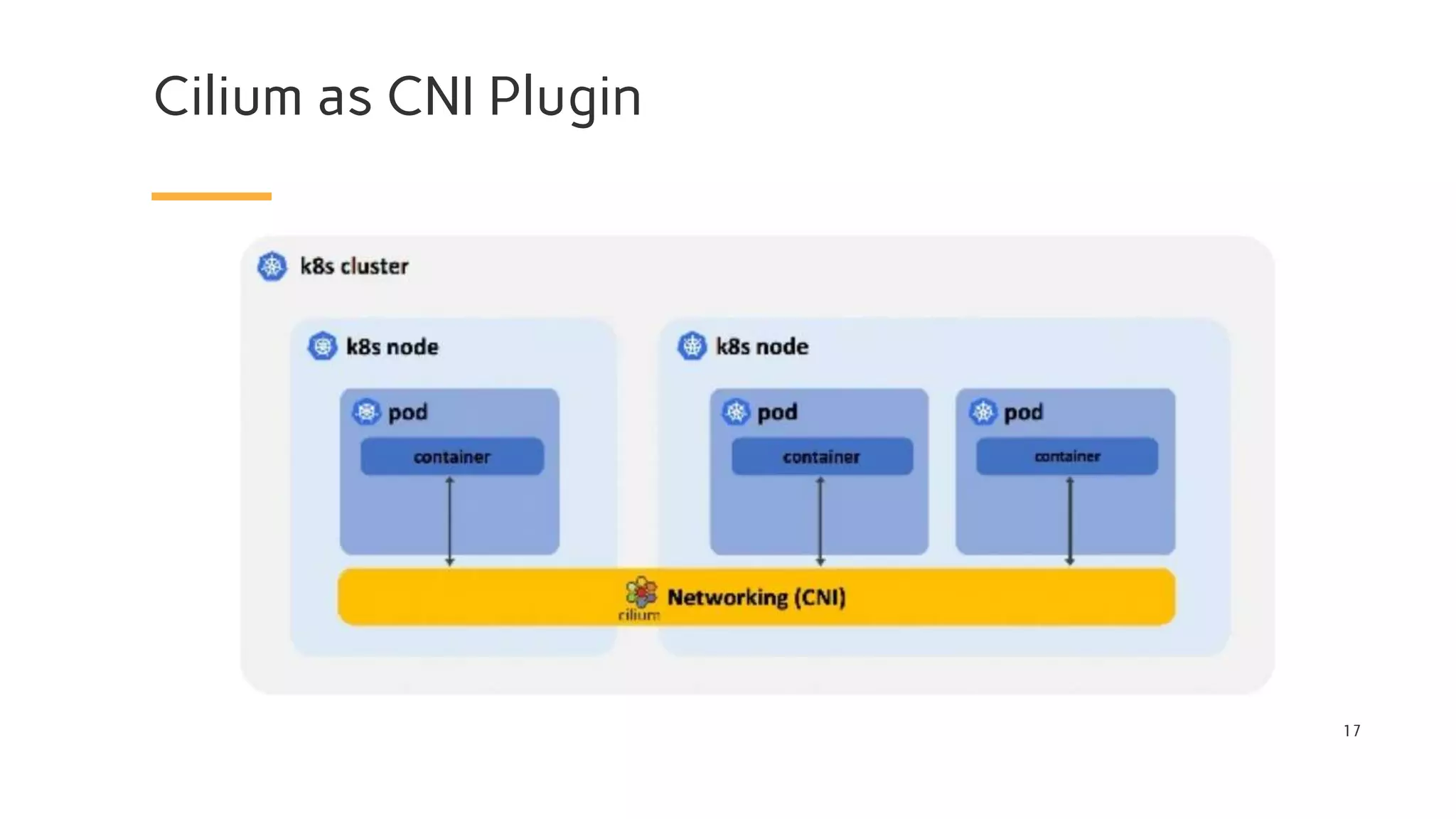
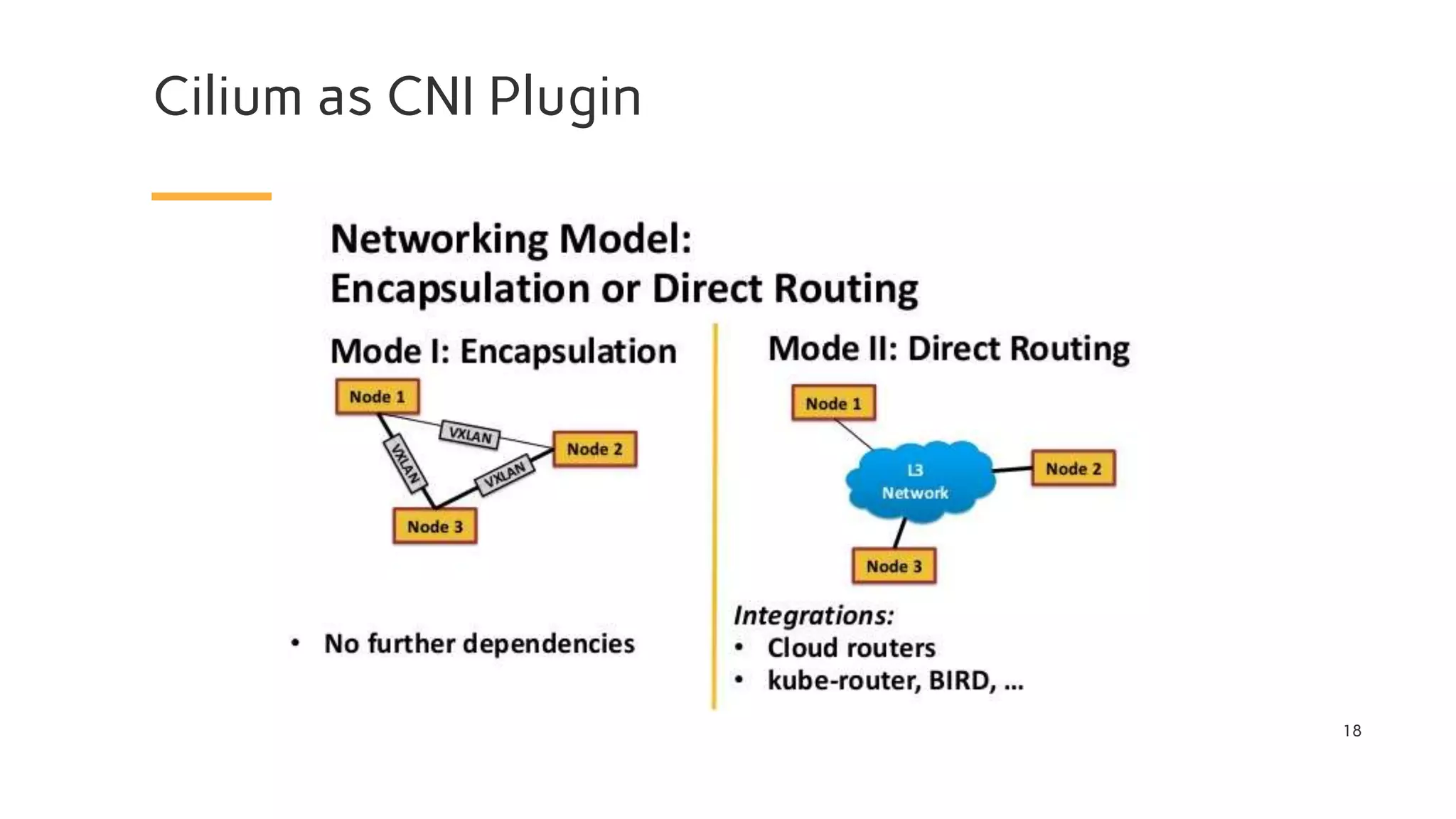
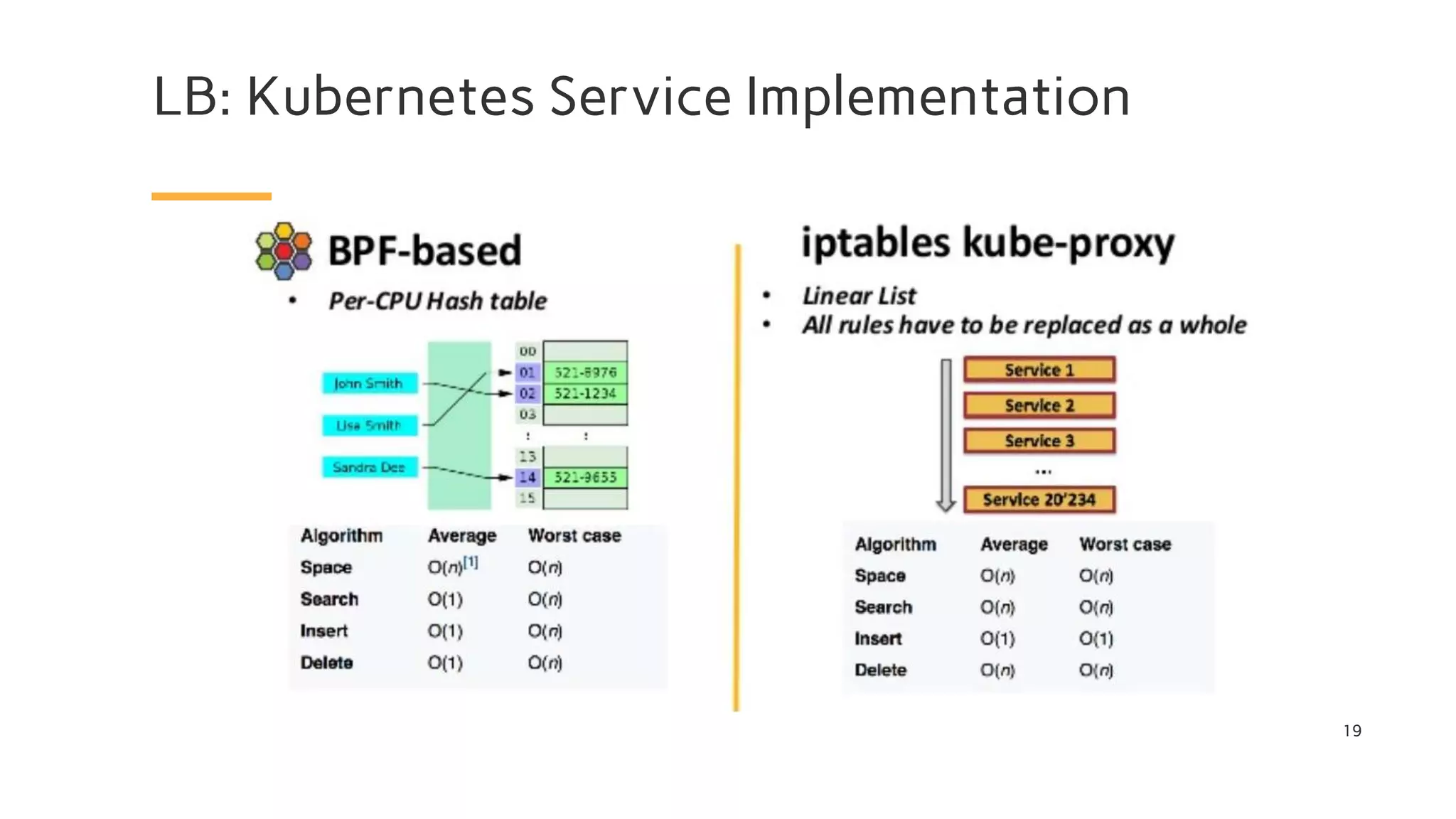
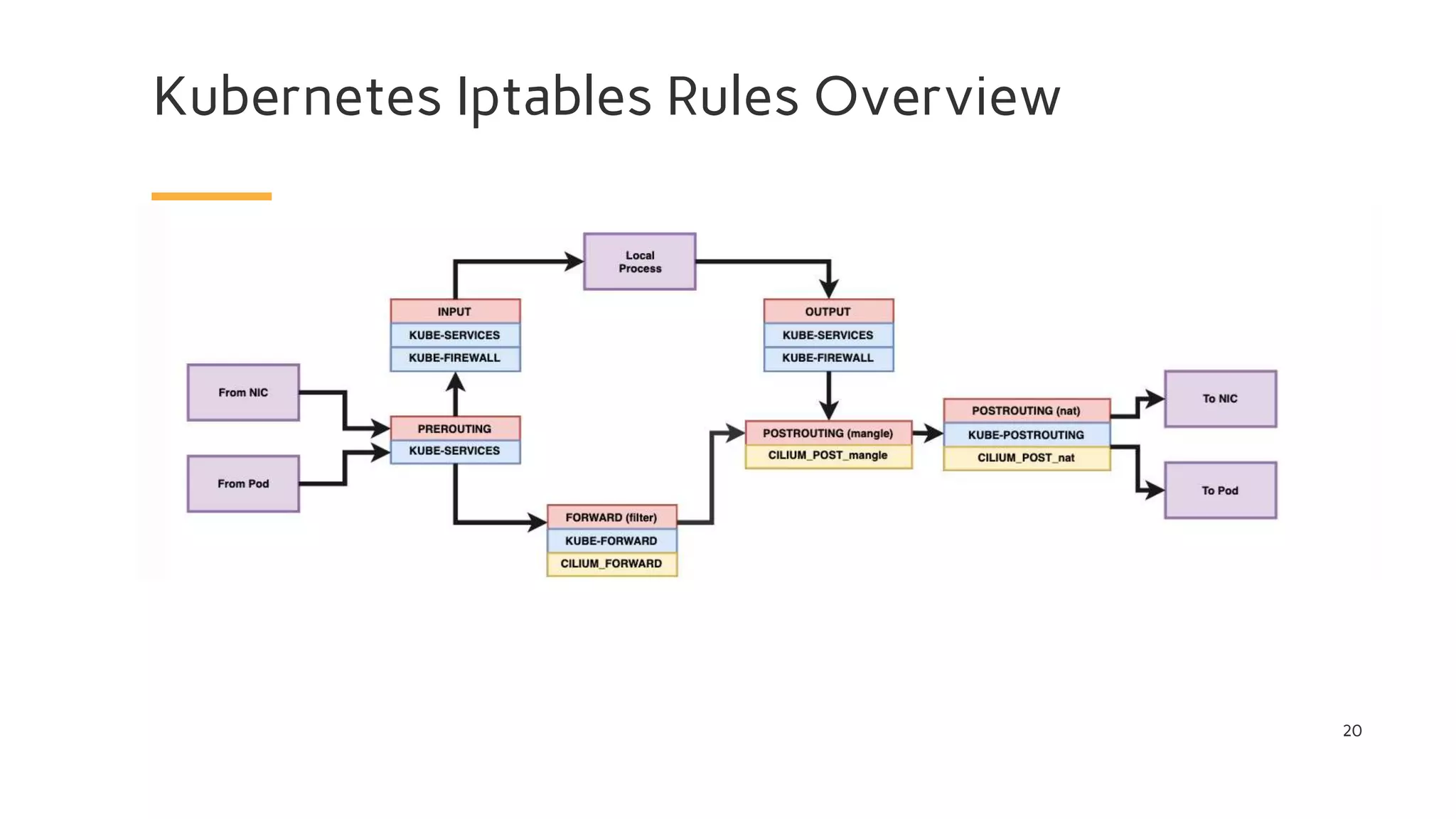
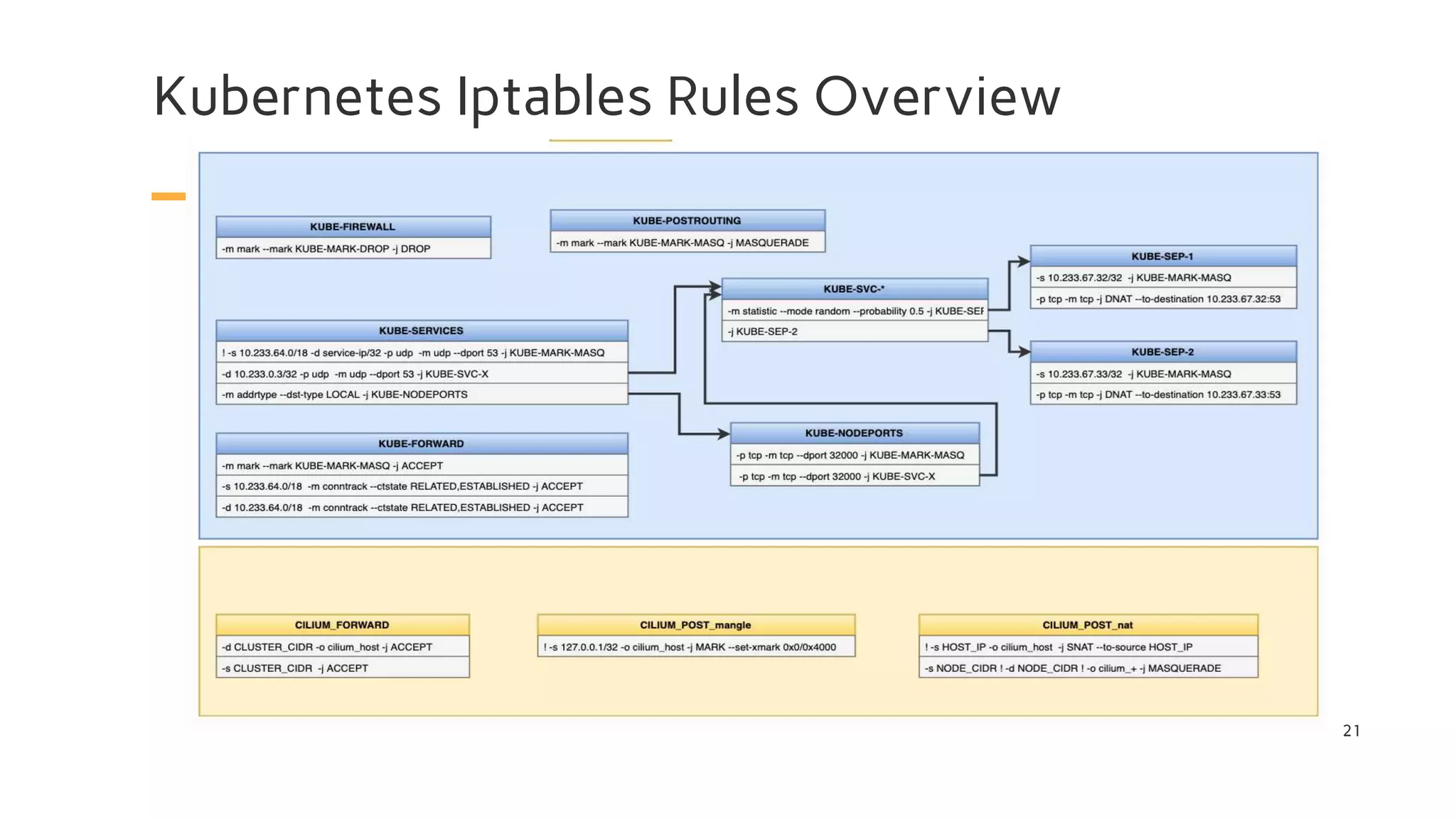
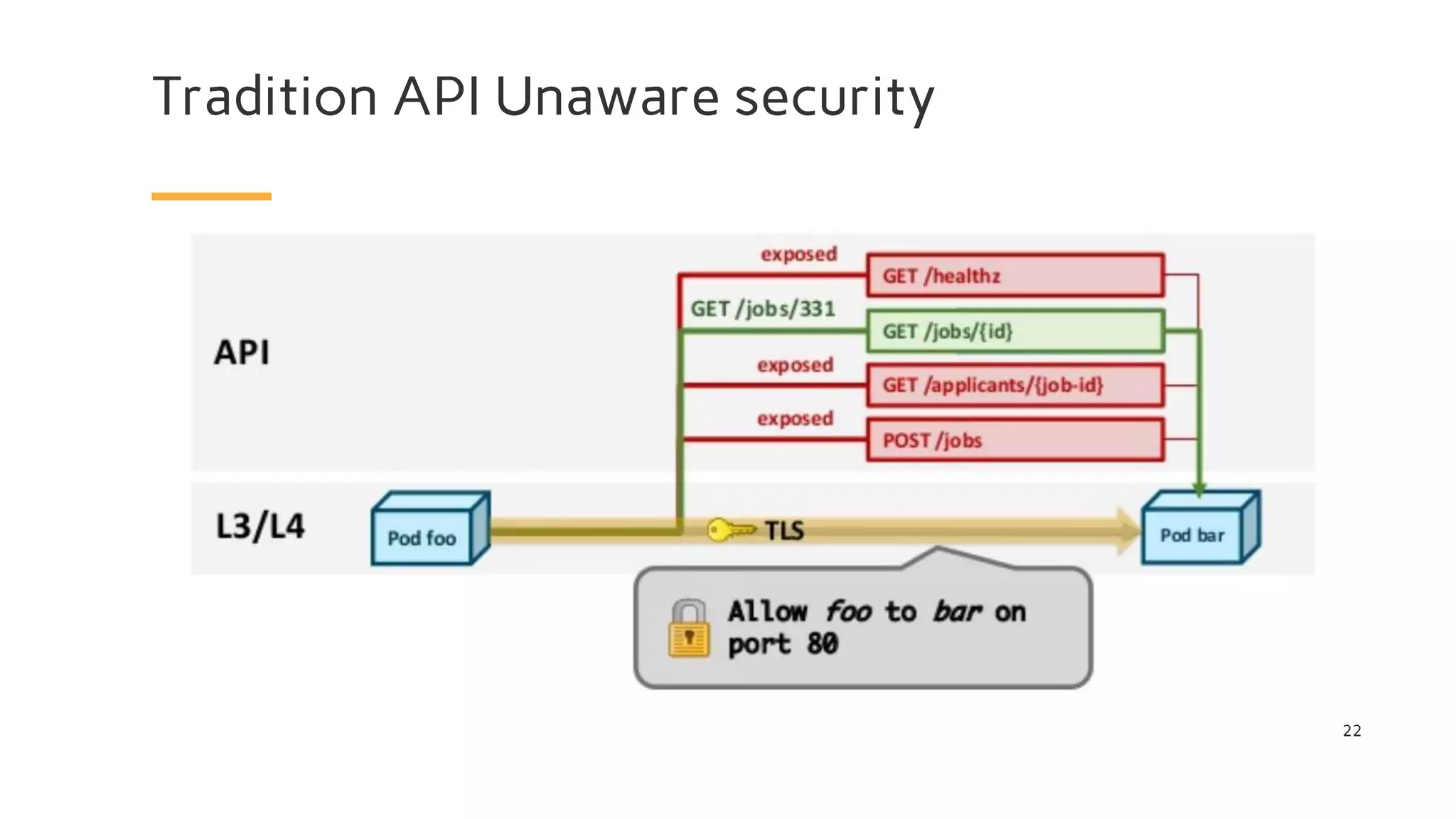
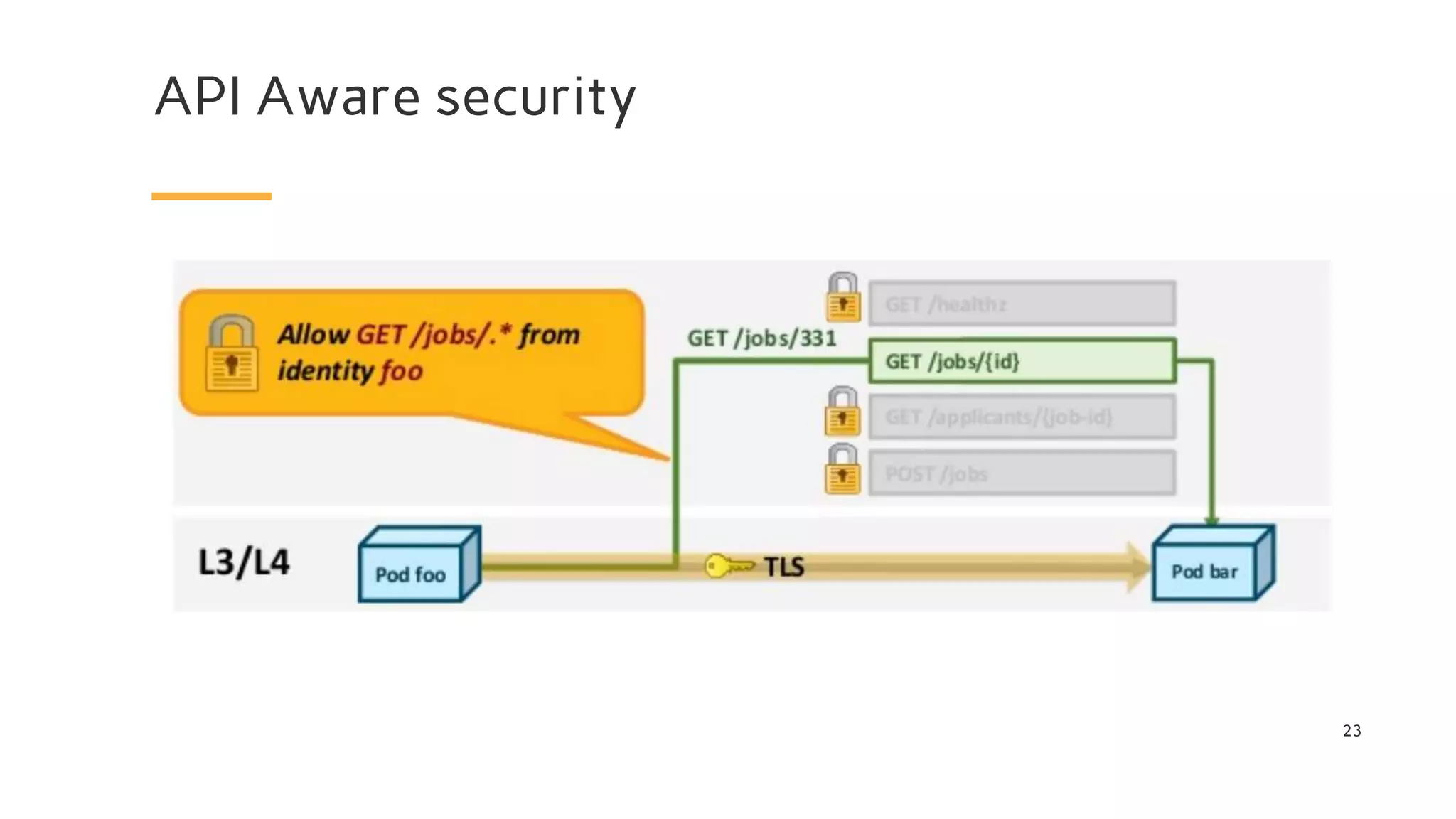
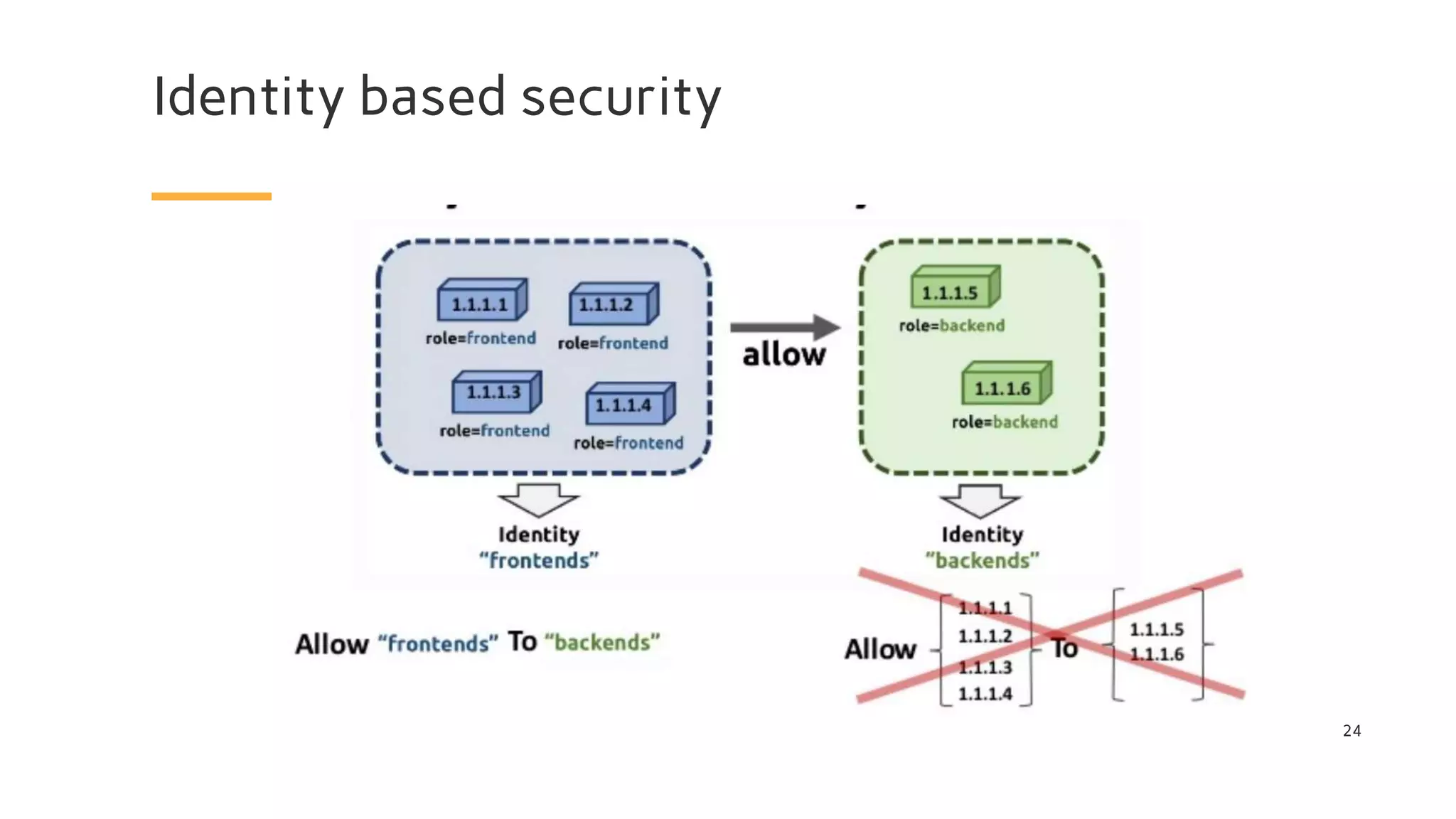
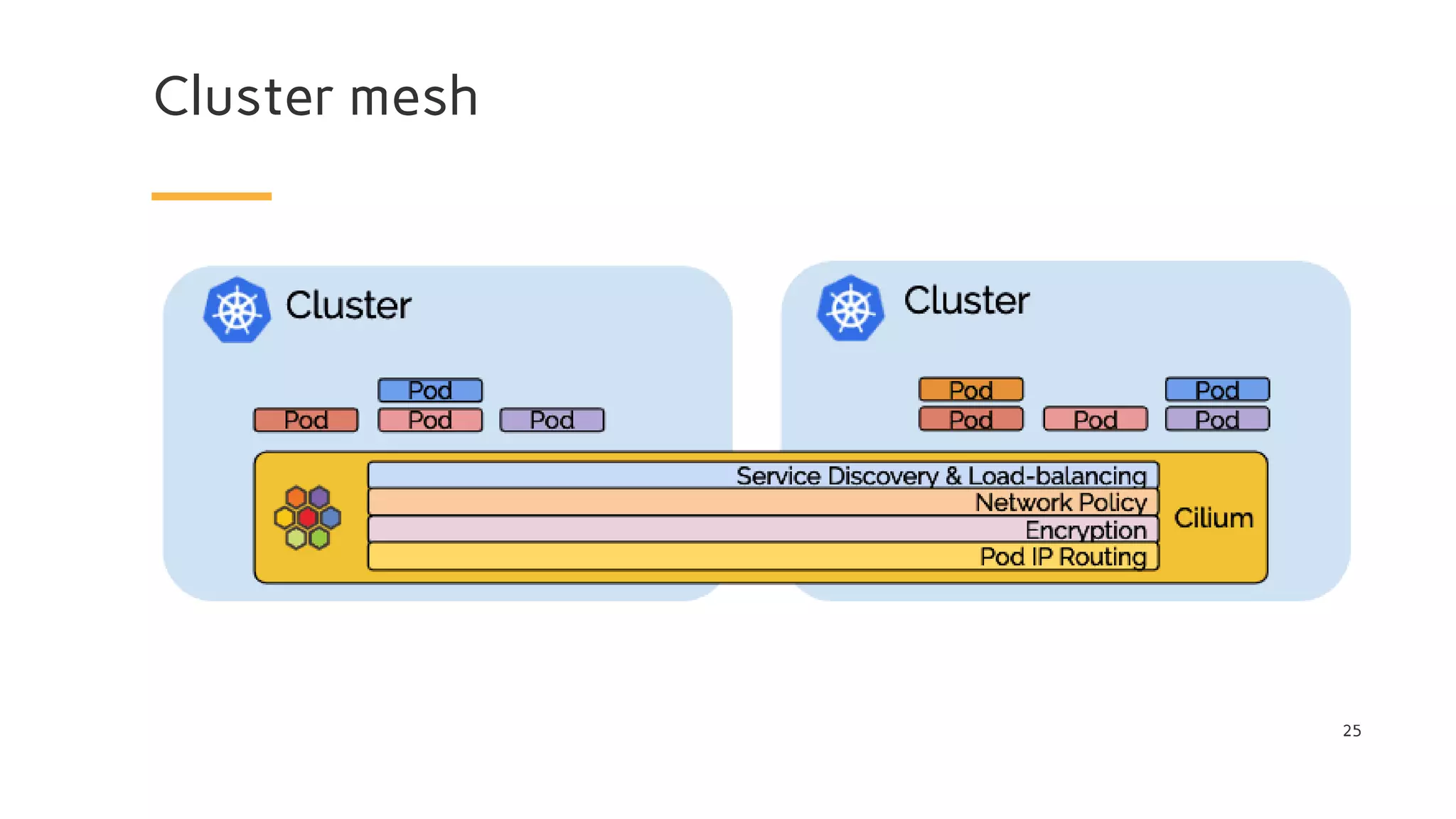
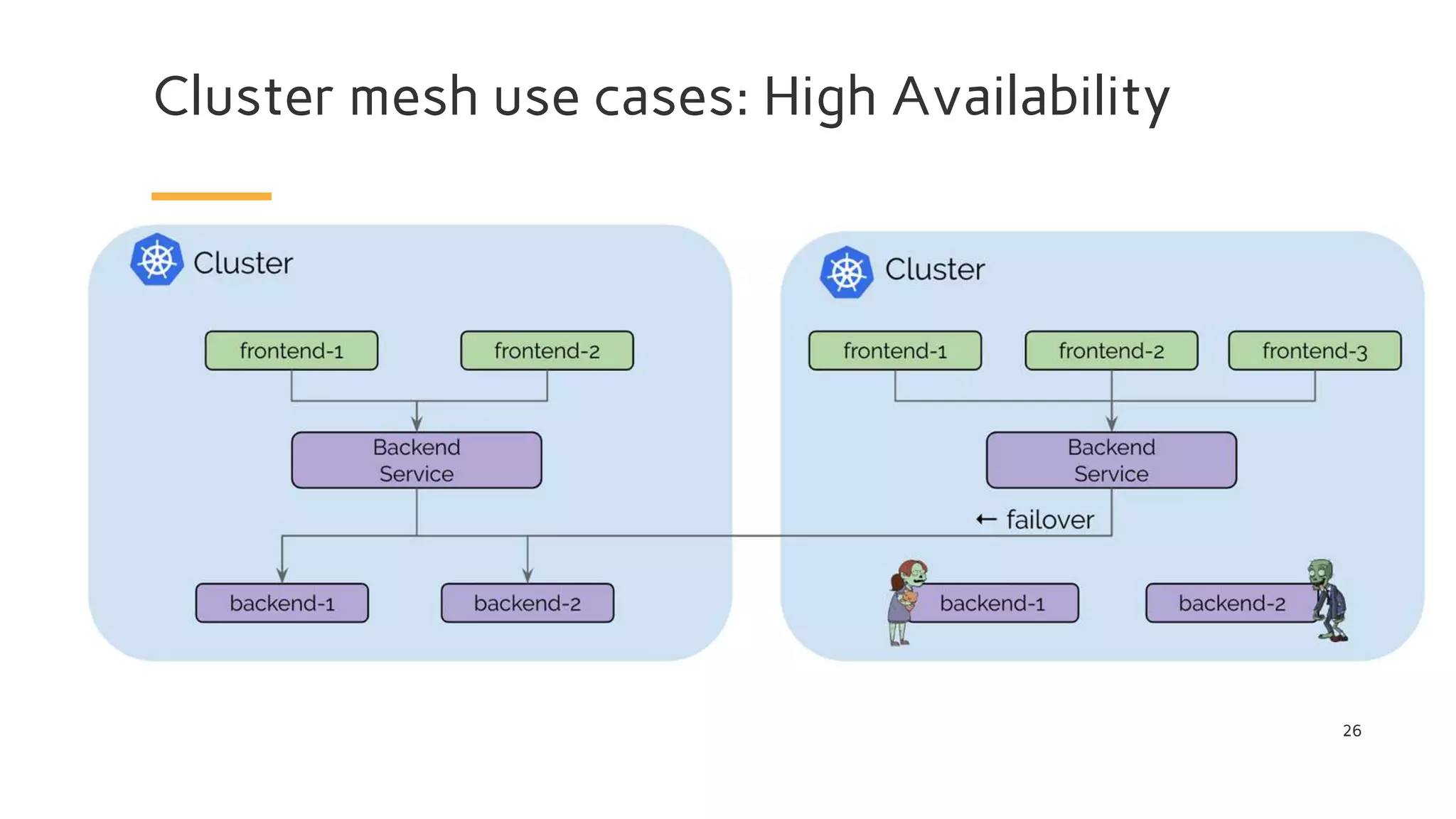
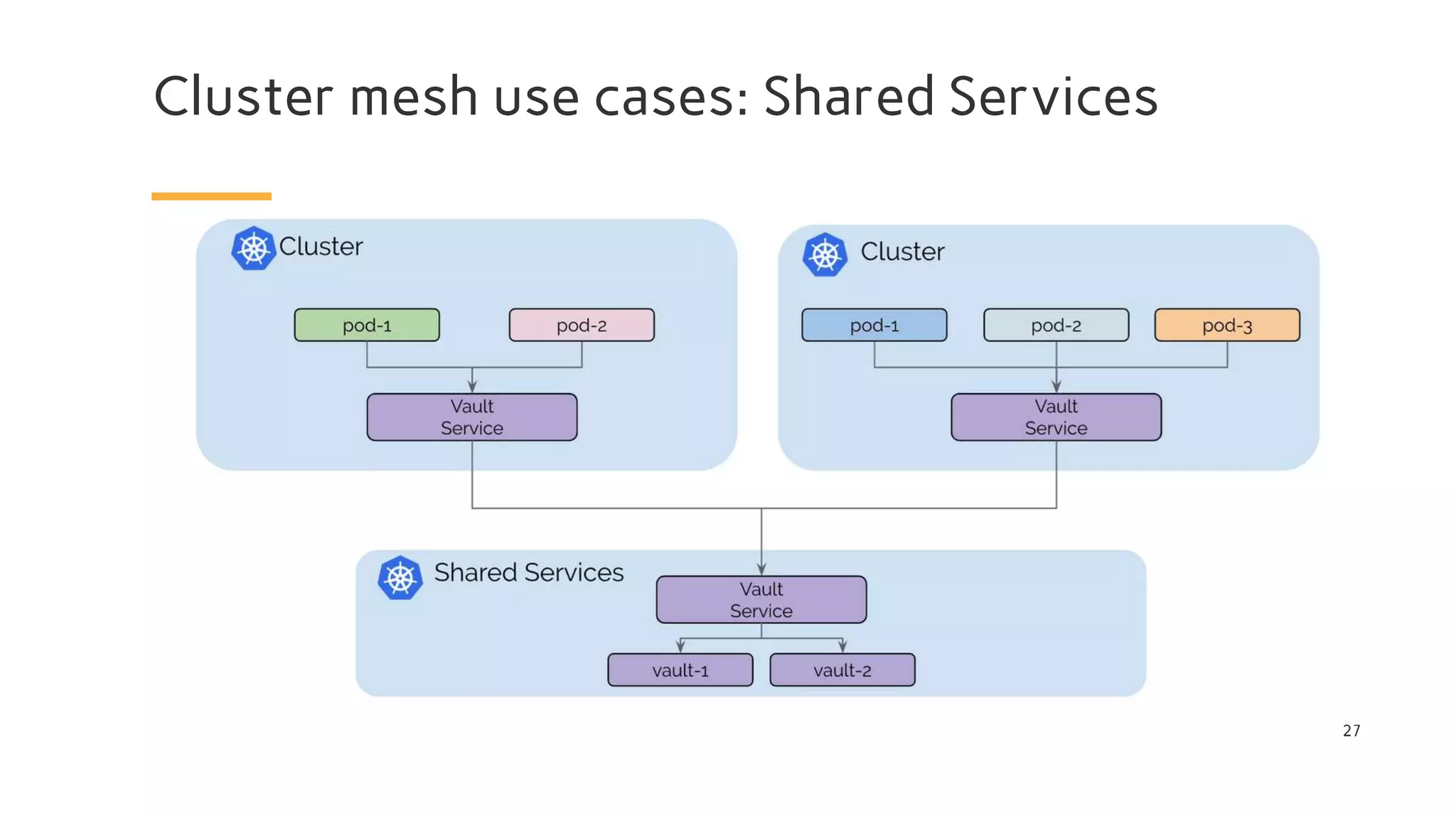
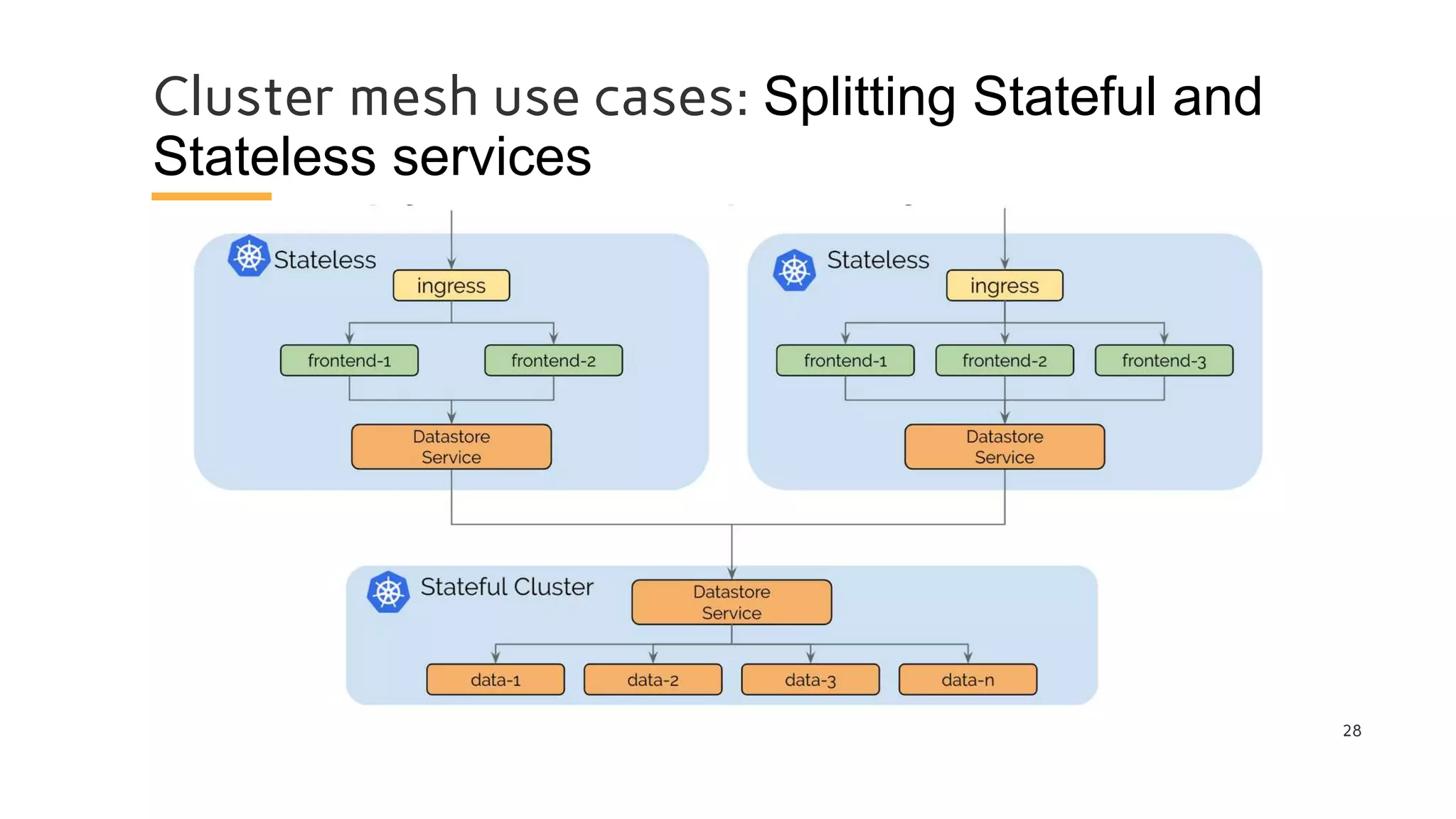
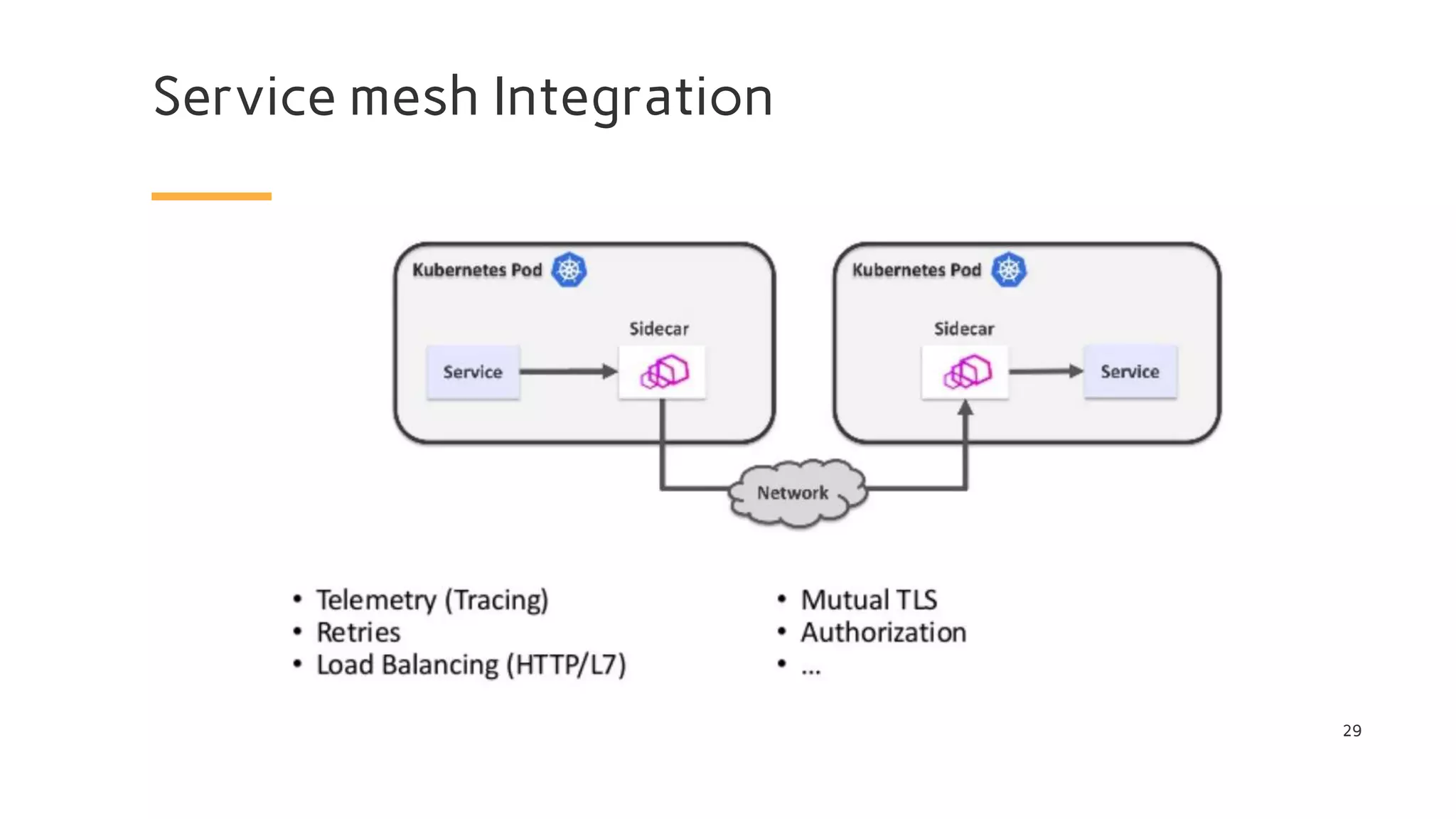
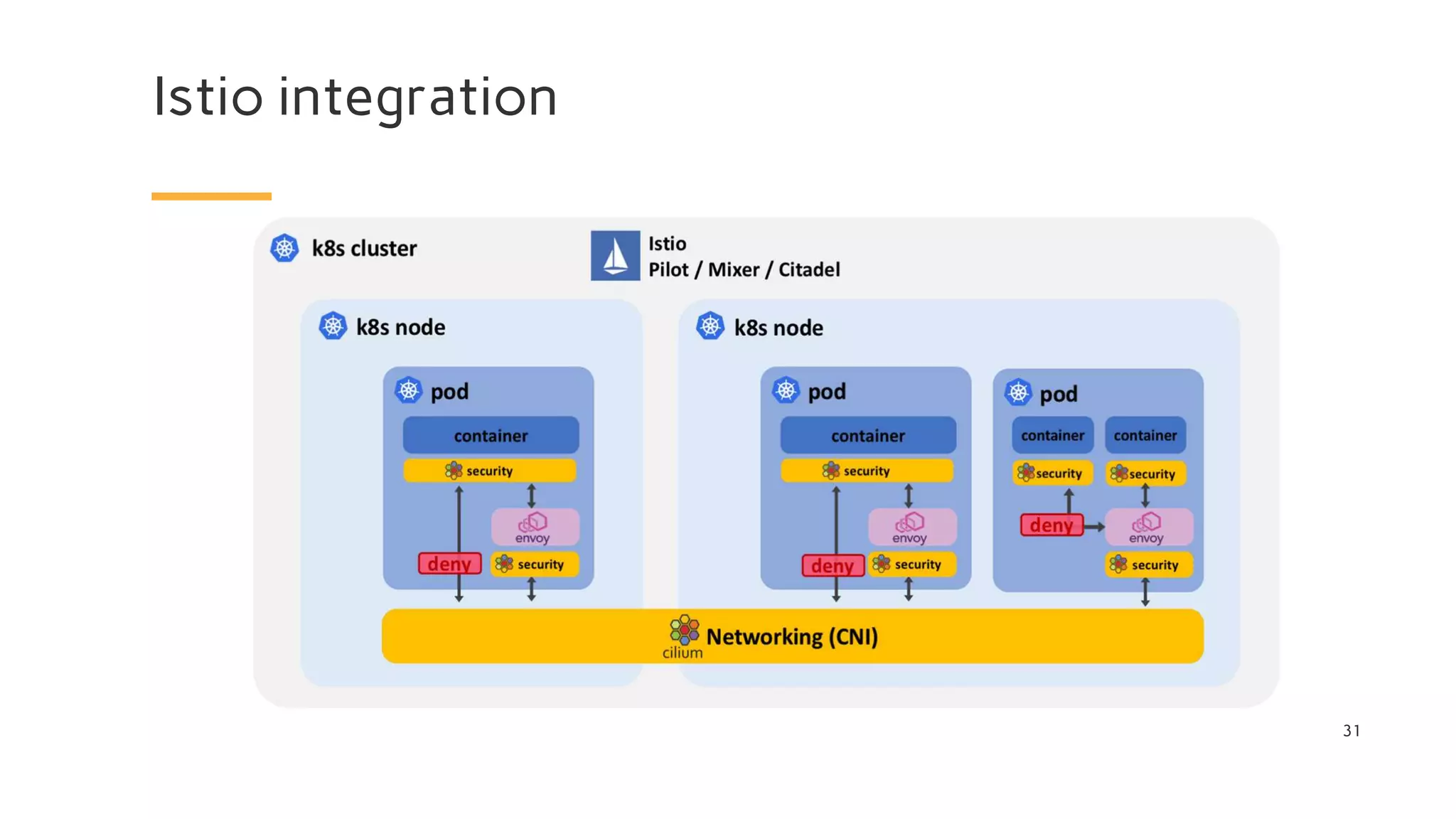
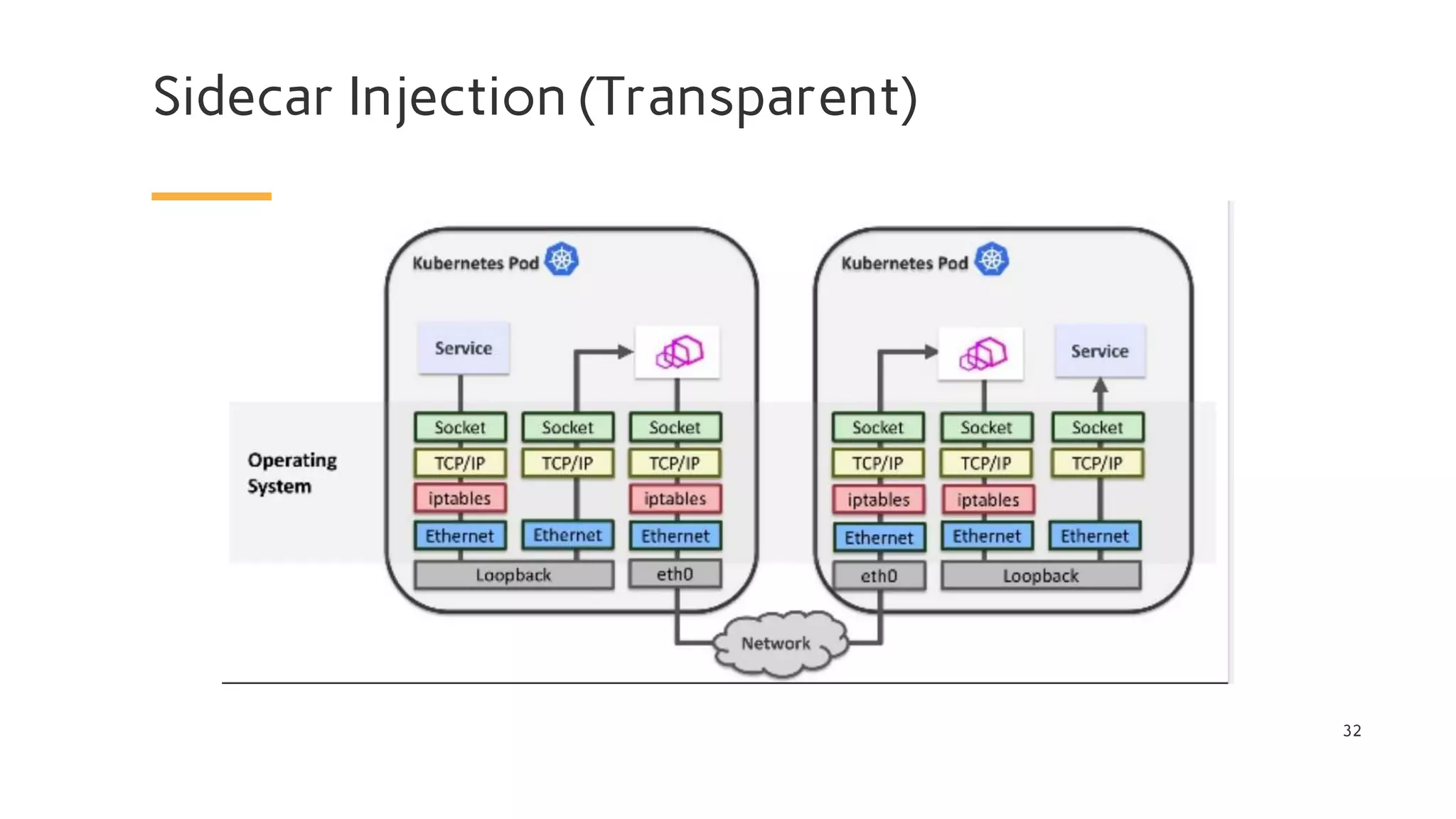
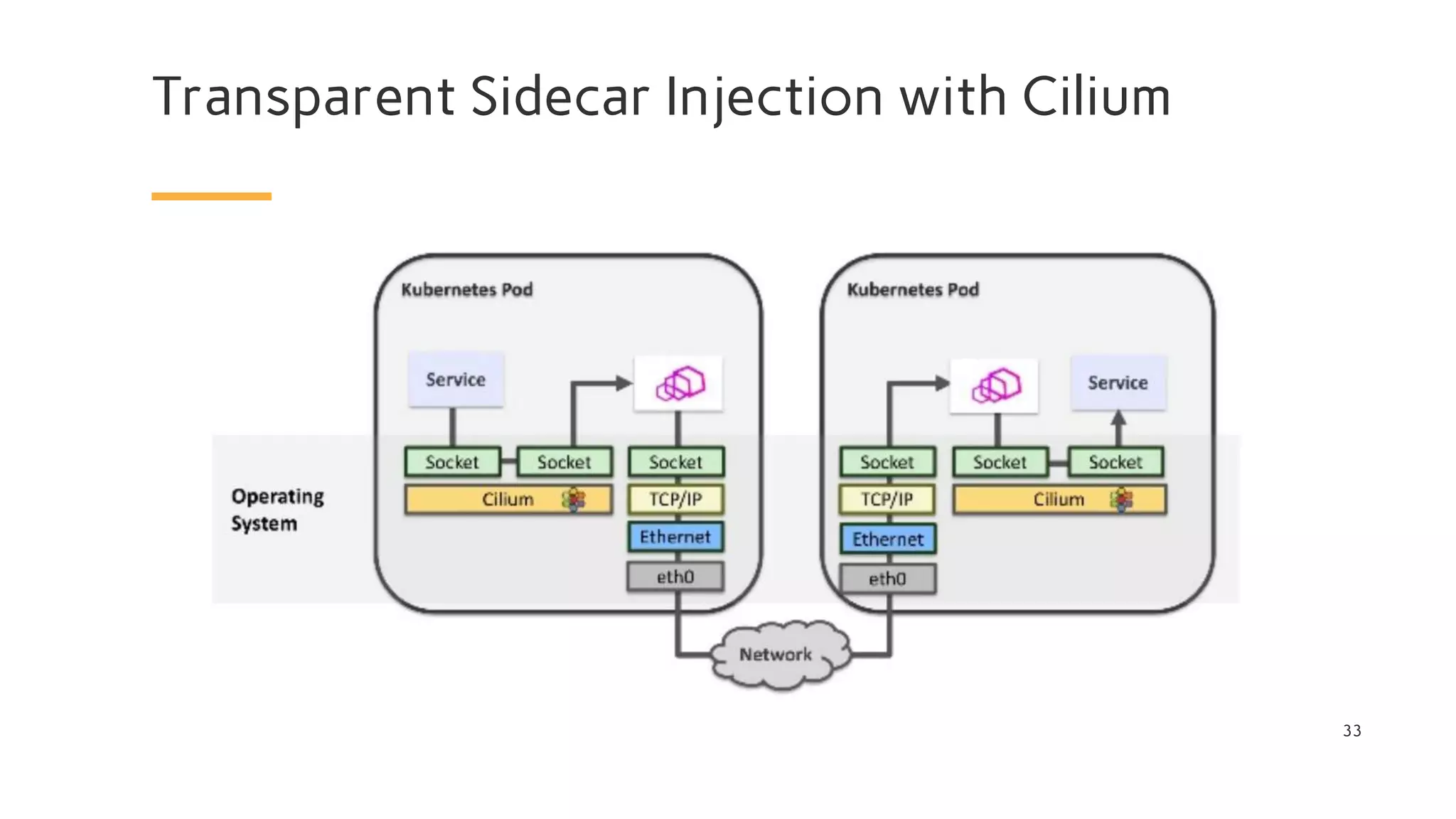
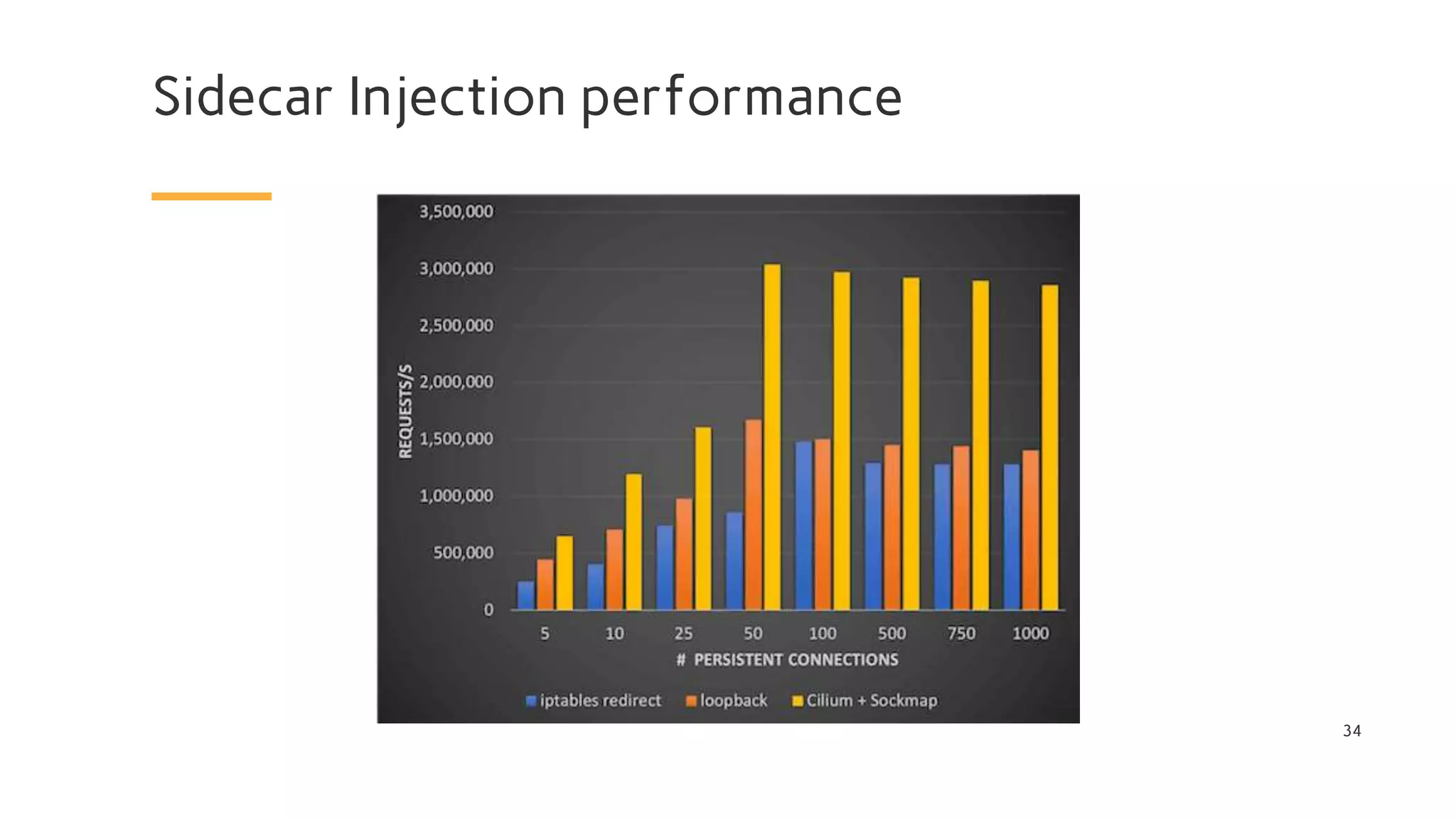
The document discusses Cilium, a network security solution for microservices that integrates with Istio and leverages BPF for enhanced performance and visibility. It details features such as identity-based security, multi-cluster connectivity, and the limitations of various Cilium map types. Additionally, it highlights Cilium's role as a CNI plugin and its capabilities in service mesh integration and load balancing.