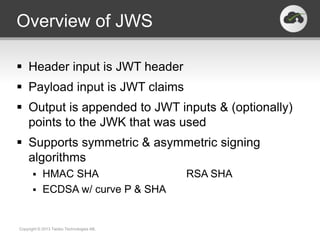
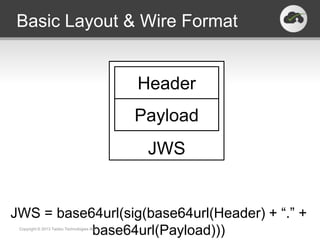
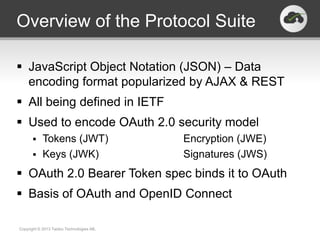
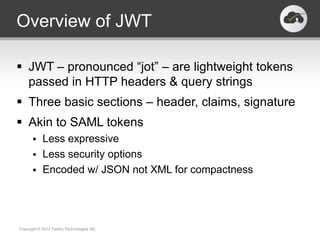
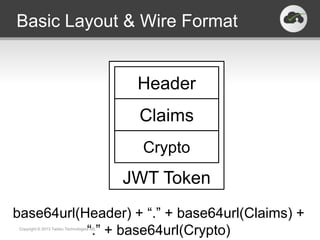
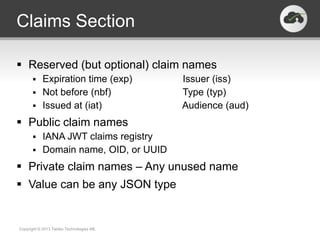
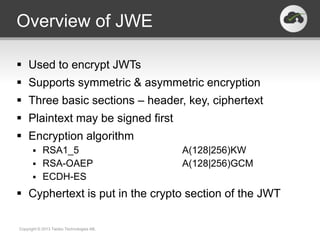
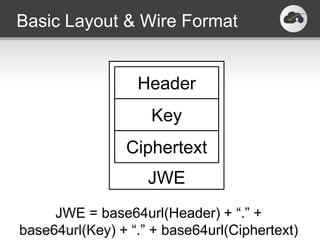
The document discusses the JSON-based Identity Protocol Suite, which defines standards for JSON Web Tokens (JWTs), JSON Web Encryption (JWE), JSON Web Keys (JWK), and JSON Web Signatures (JWS). JWTs are compact tokens passed in HTTP that contain claims and can be signed or encrypted. JWE defines how to encrypt JWTs using symmetric or asymmetric encryption. JWK defines public key representations in JSON. JWS defines how to digitally sign JWTs using symmetric or asymmetric signatures. These standards are defined by the IETF and provide a common way to securely transmit identity and authorization data.

![JWK Example
{“keyvalues” : {“algorithm” : “RSA”,
[ “modulus” : “…”,
{“algorithm” : “EC”, “exponent” : “…”,
“curve” : “P-256”, “keyid” : “…”}
]
“x” : “…”,
}
“y” : “…”,
“use” : “encryption”,
“keyid” : “1”},
Copyright © 2013 Twobo Technologies AB.](https://image.slidesharecdn.com/jwt-130305011253-phpapp01/85/The-JSON-based-Identity-Protocol-Suite-9-320.jpg)