The document discusses best practices for securing APIs using JSON Object Signing and Encryption (JOSE) methods. It presents various authentication techniques, message validation, and encryption strategies to enhance security and reduce code complexity, demonstrating this through a case study of the Launchkey API. Ultimately, it argues that JOSE provides a more standardized and effective approach to API security, including cryptographic mechanisms and better integration with middleware.





































![@adam_englander
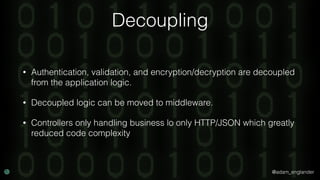
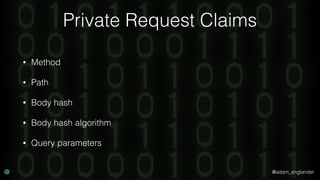
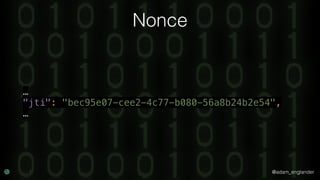
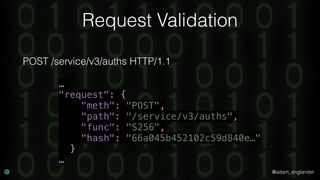
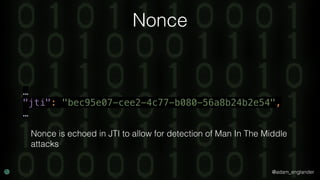
JWT Creation Example
$jwt = (new JWTCreator(new Signer(['RS512'])))->sign(
[
'iat' => time(),
'exp' => time() + 5,
'jti' => 'abc123',
],
['alg' => 'RS512'],
JWKFactory::createFromKeyFile(
'./private.key'
)
);](https://image.slidesharecdn.com/confoo2017-dontloosesleep-secureyourrest-171204210330/85/Con-Foo-2017-Don-t-Loose-Sleep-Secure-Your-REST-54-320.jpg)
![@adam_englander
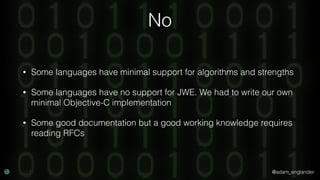
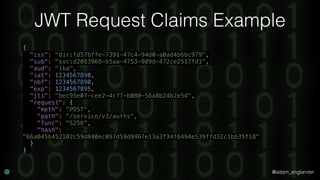
JWT Validation Example
$checkerManager = new CheckerManager();
$checkerManager->addClaimChecker(new IssuedAtChecker());
$jwtLoader = new JWTLoader(
$checkerManager,
new Verifier(['RS512'])
);
$keySet = new JWKSet();
$keySet->addKey(JWKFactory::createFromKeyFile(
'./public.key'
));
$jws = $jwtLoader->load($jwt, $keySet);
$jwtLoader->verify($jws, $keySet);](https://image.slidesharecdn.com/confoo2017-dontloosesleep-secureyourrest-171204210330/85/Con-Foo-2017-Don-t-Loose-Sleep-Secure-Your-REST-55-320.jpg)


![@adam_englander
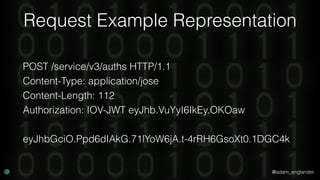
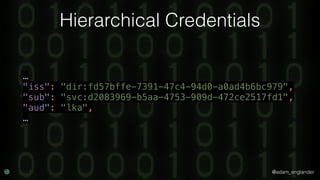
JWE Encryption Example
$encrypted = JWEFactory::createJWEToCompactJSON(
"Hello World!",
JWKFactory::createFromKeyFile(
'./public.key'
),
[
'enc' => 'A256CBC-HS512',
'alg' => 'RSA-OAEP-256',
'zip' => 'DEF',
]
);](https://image.slidesharecdn.com/confoo2017-dontloosesleep-secureyourrest-171204210330/85/Con-Foo-2017-Don-t-Loose-Sleep-Secure-Your-REST-58-320.jpg)
![@adam_englander
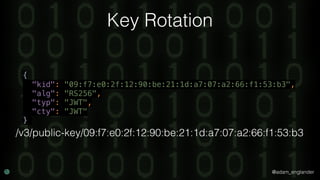
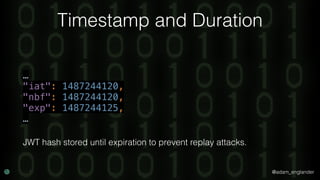
JWE Decryption Example
$decrypted = (new Loader)->loadAndDecryptUsingKey(
$encrypted,
JWKFactory::createFromKeyFile(
'./private.key'
),
['RSA-OAEP-256'], // Acceptable algs
['A256CBC-HS512'] // Acceptable encs
);](https://image.slidesharecdn.com/confoo2017-dontloosesleep-secureyourrest-171204210330/85/Con-Foo-2017-Don-t-Loose-Sleep-Secure-Your-REST-59-320.jpg)