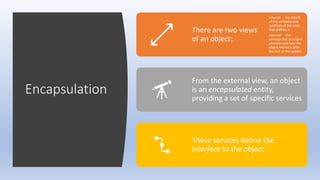
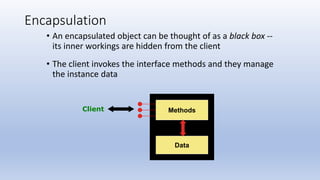
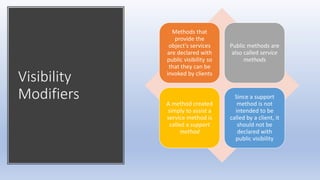
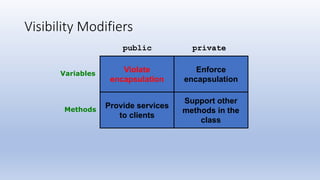
This document discusses encapsulation and visibility modifiers in Java classes. It explains that encapsulation hides a class's internal details and exposes only its public services. Instance variables should be private to enforce encapsulation. Public methods provide a class's services while private support methods assist them. Accessor and mutator methods allow controlled data access and modification. Mutators can restrict variable modifications to valid ranges.