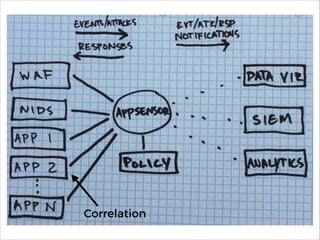
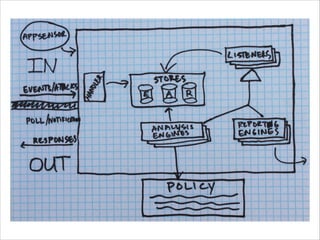
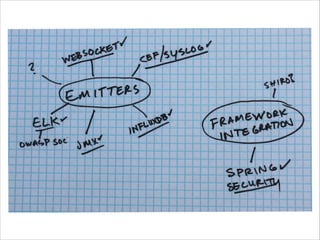
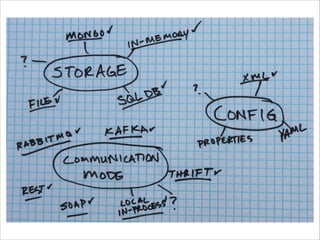
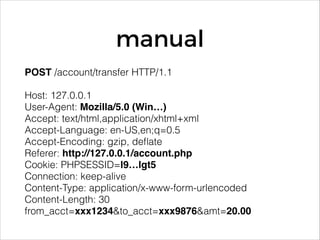
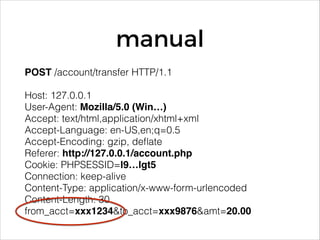
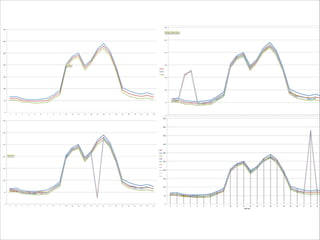
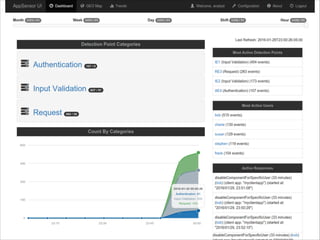
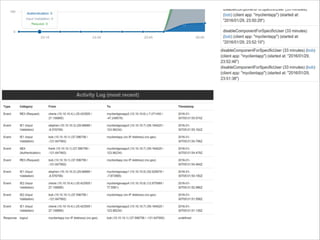
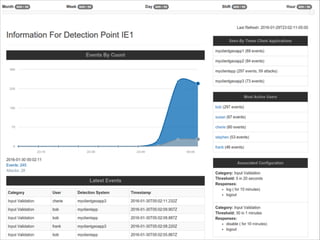
The document discusses the evolution and current state of application security, emphasizing the need for modern secure applications to proactively defend against attackers. It outlines both the challenges developers and security professionals face due to rapid technological changes and proposes the integration of real-time event detection and automated response mechanisms in applications to enhance security. It also highlights future directions for the AppSensor project and invites community contributions.






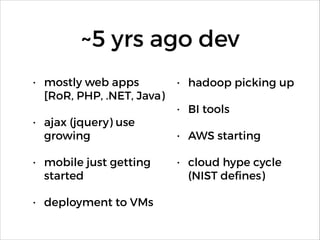
![~now dev
• JS everywhere
• functional / rx programming
• cloud everything
• ci/cd
• nosql / CAP light
• containers
• big data
• stream processing
• config management
• iot
• beacons [usage, ads,
errors, performance]
• actors/csp
• microservices
• cqrs / event sourcing
• mobile](https://image.slidesharecdn.com/appsensormeltondevnexus2016-160217015435/85/AppSensor-Near-Real-Time-Event-Detection-and-Response-DevNexus-2016-8-320.jpg)
![~now dev
• JS everywhere
• functional / rx programming
• cloud everything
• ci/cd
• nosql / CAP light
• containers
• big data
• stream processing
• config management
• iot
• beacons [usage, ads,
errors, performance]
• actors/csp
• microservices
• cqrs / event sourcing
• mobile
1 .. * of [scale, speed, cloud, lack of environmental access]](https://image.slidesharecdn.com/appsensormeltondevnexus2016-160217015435/85/AppSensor-Near-Real-Time-Event-Detection-and-Response-DevNexus-2016-9-320.jpg)



![last ~5 yrs security
• 3rd party libs (dep-check)
• bug bounties
• sast / dast evolve (ZAP)
• iast / rasp
• http security headers
• automatic encoding (JXT)
• *-monkey -NetflixOSS
• bdd-security/gauntlt
• ci/cd plugins
• 2fa
• osquery
1 .. * of [scale, speed, cloud, lack of environmental access]](https://image.slidesharecdn.com/appsensormeltondevnexus2016-160217015435/85/AppSensor-Near-Real-Time-Event-Detection-and-Response-DevNexus-2016-13-320.jpg)




![catching defects
• what do dev/qa do for functionality?
• test [unit, integration, system, manual, tools]
• what do attackers do for security?
• test [automated tools, manual]](https://image.slidesharecdn.com/appsensormeltondevnexus2016-160217015435/85/AppSensor-Near-Real-Time-Event-Detection-and-Response-DevNexus-2016-24-320.jpg)

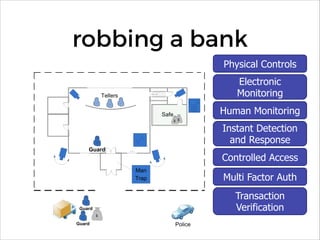
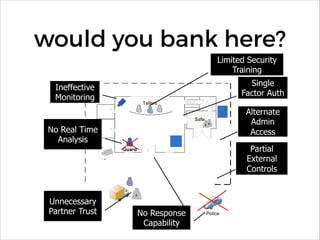



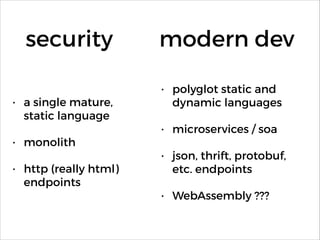


![having to deal with [scale,
speed, cloud, lack of
environmental access]..
!
..this as of now incomplete
transition..
!
..represents an enormous
opportunity for security](https://image.slidesharecdn.com/appsensormeltondevnexus2016-160217015435/85/AppSensor-Near-Real-Time-Event-Detection-and-Response-DevNexus-2016-35-320.jpg)