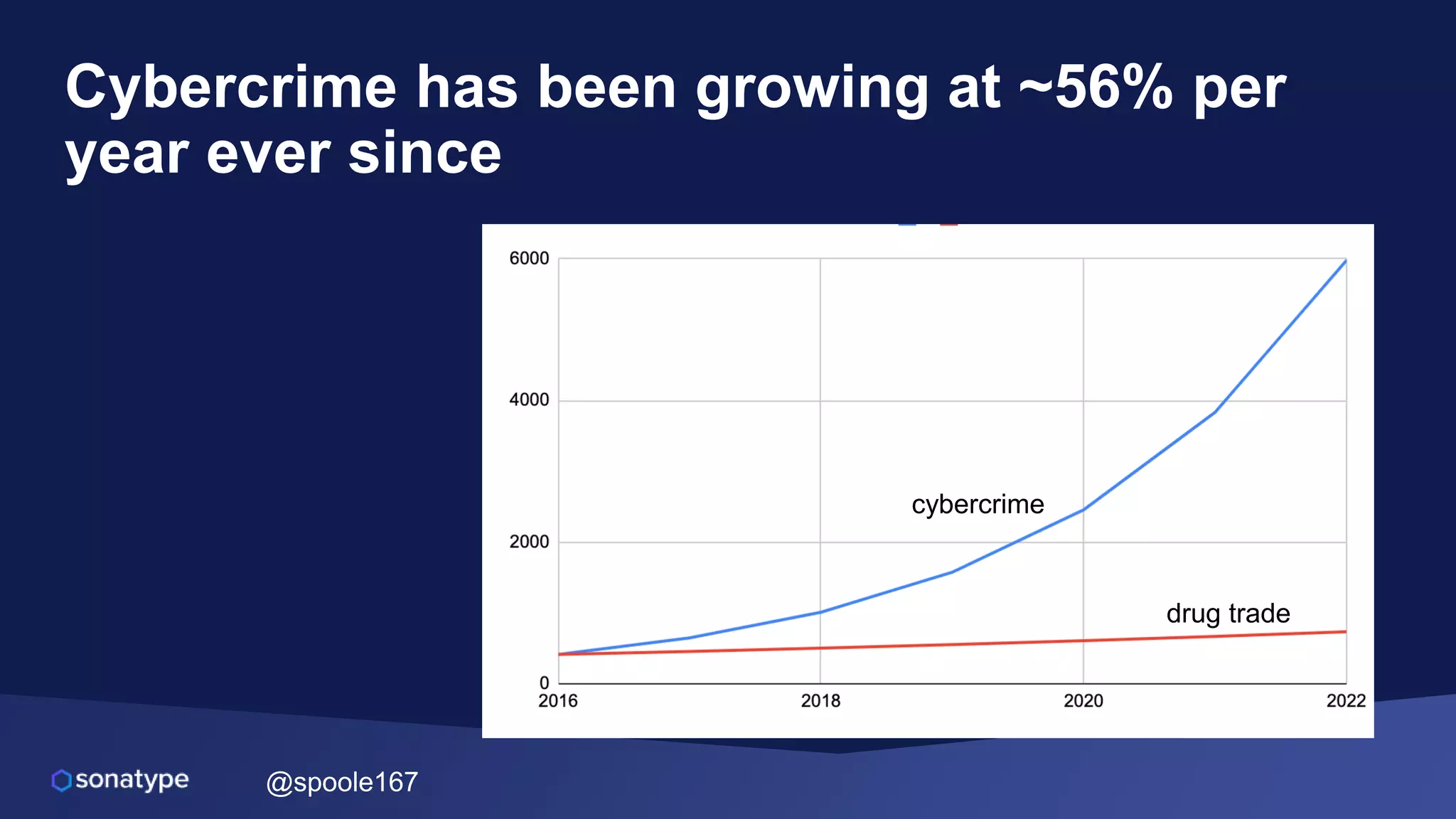
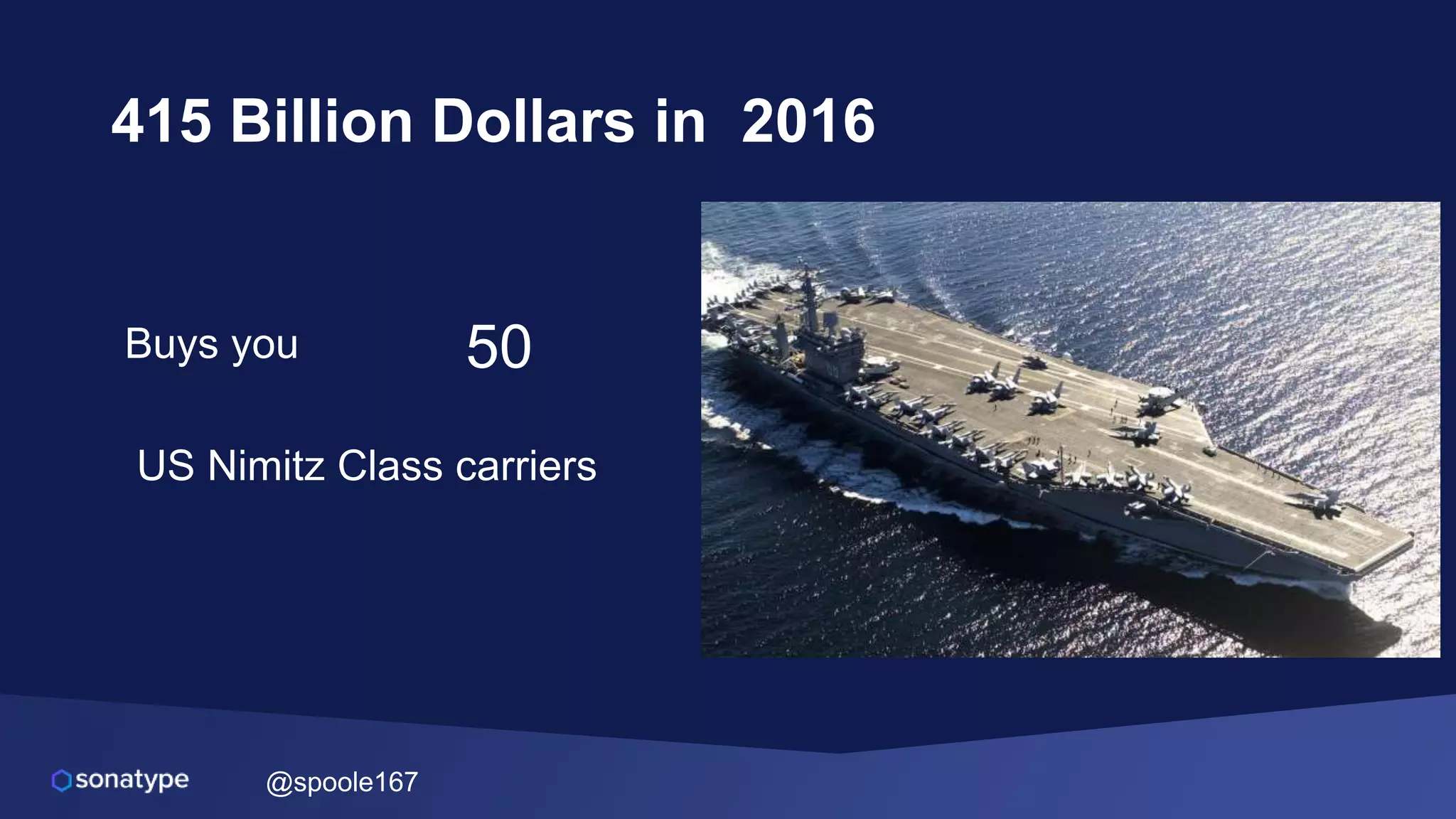
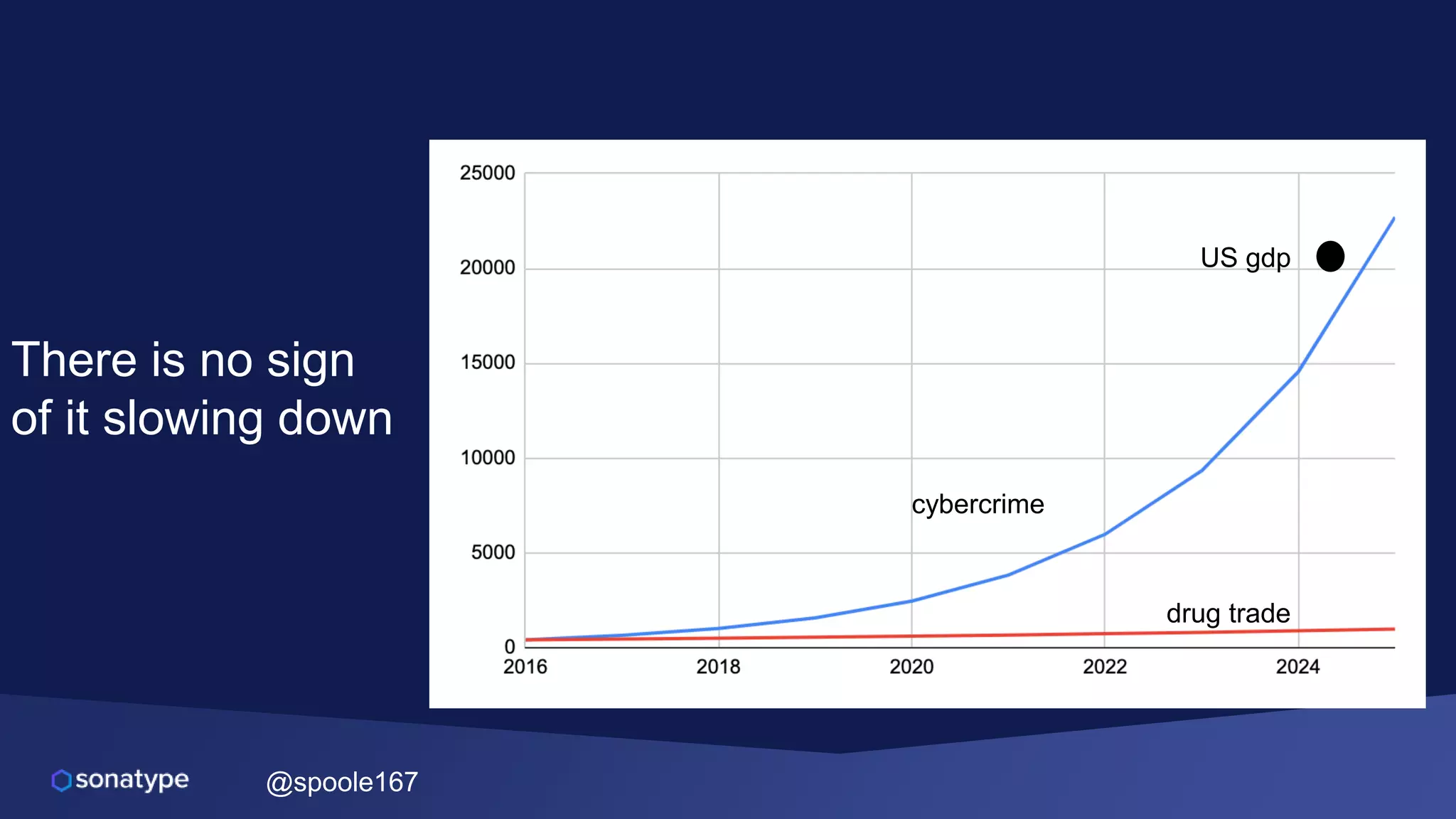
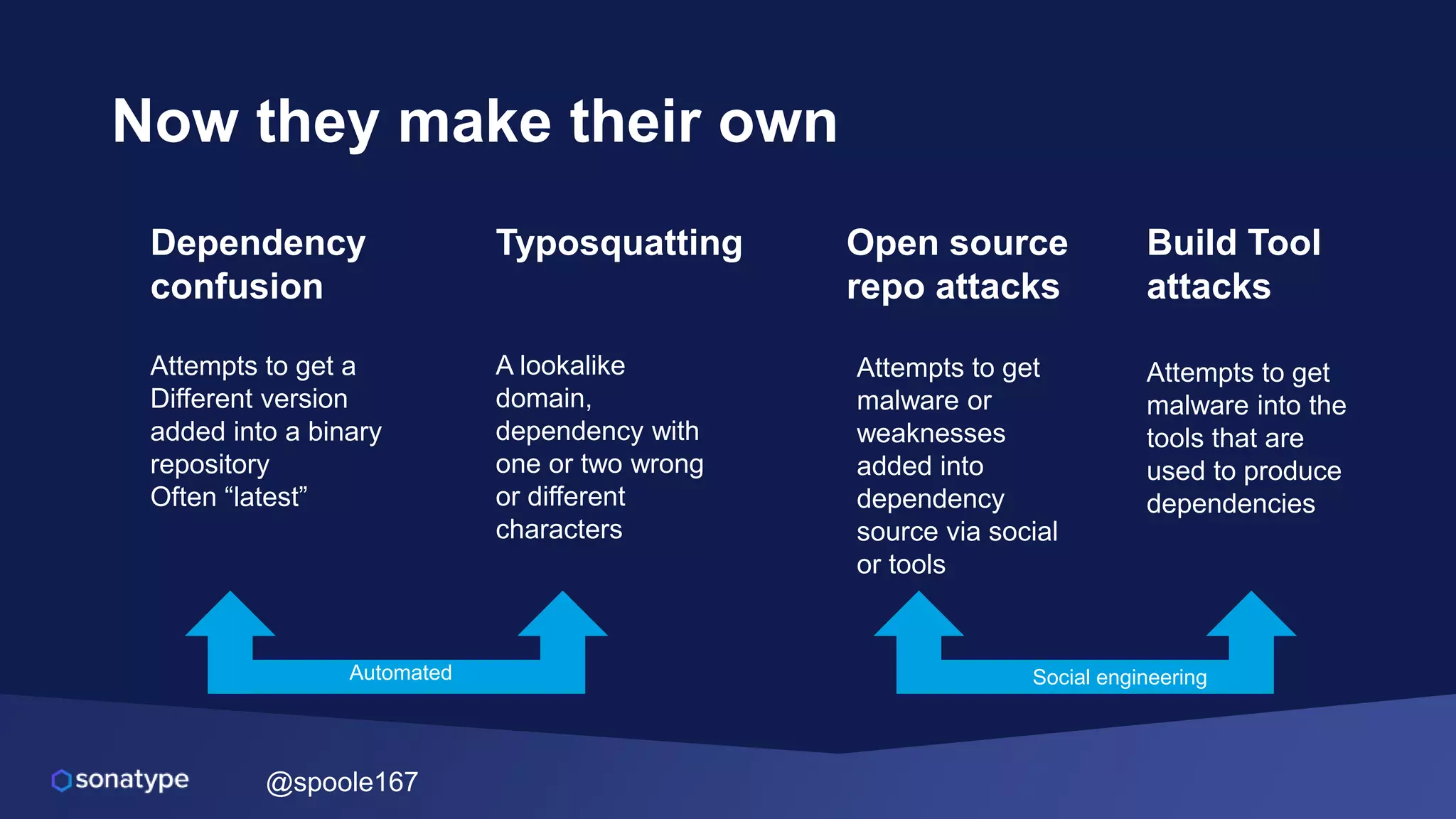
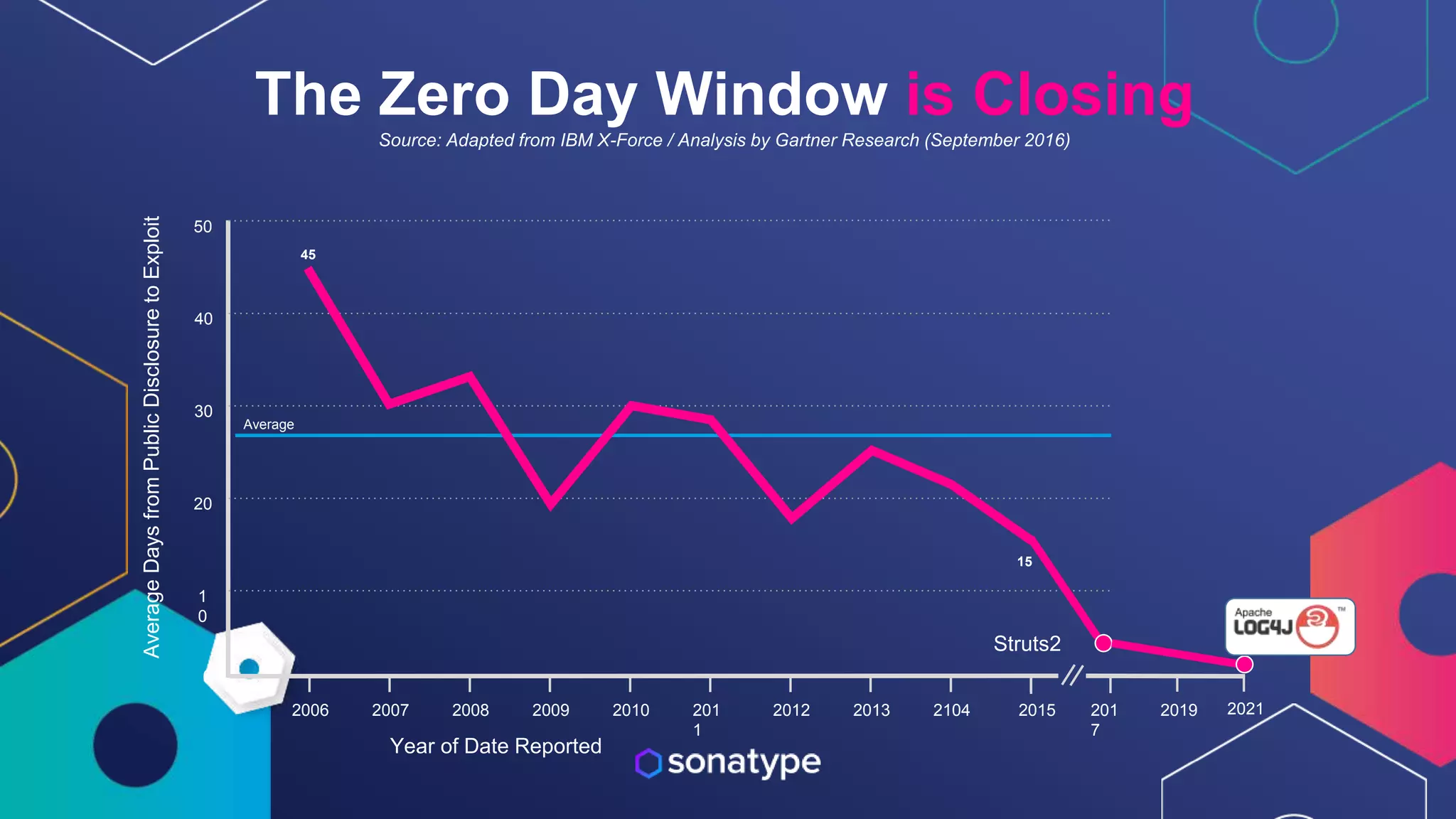
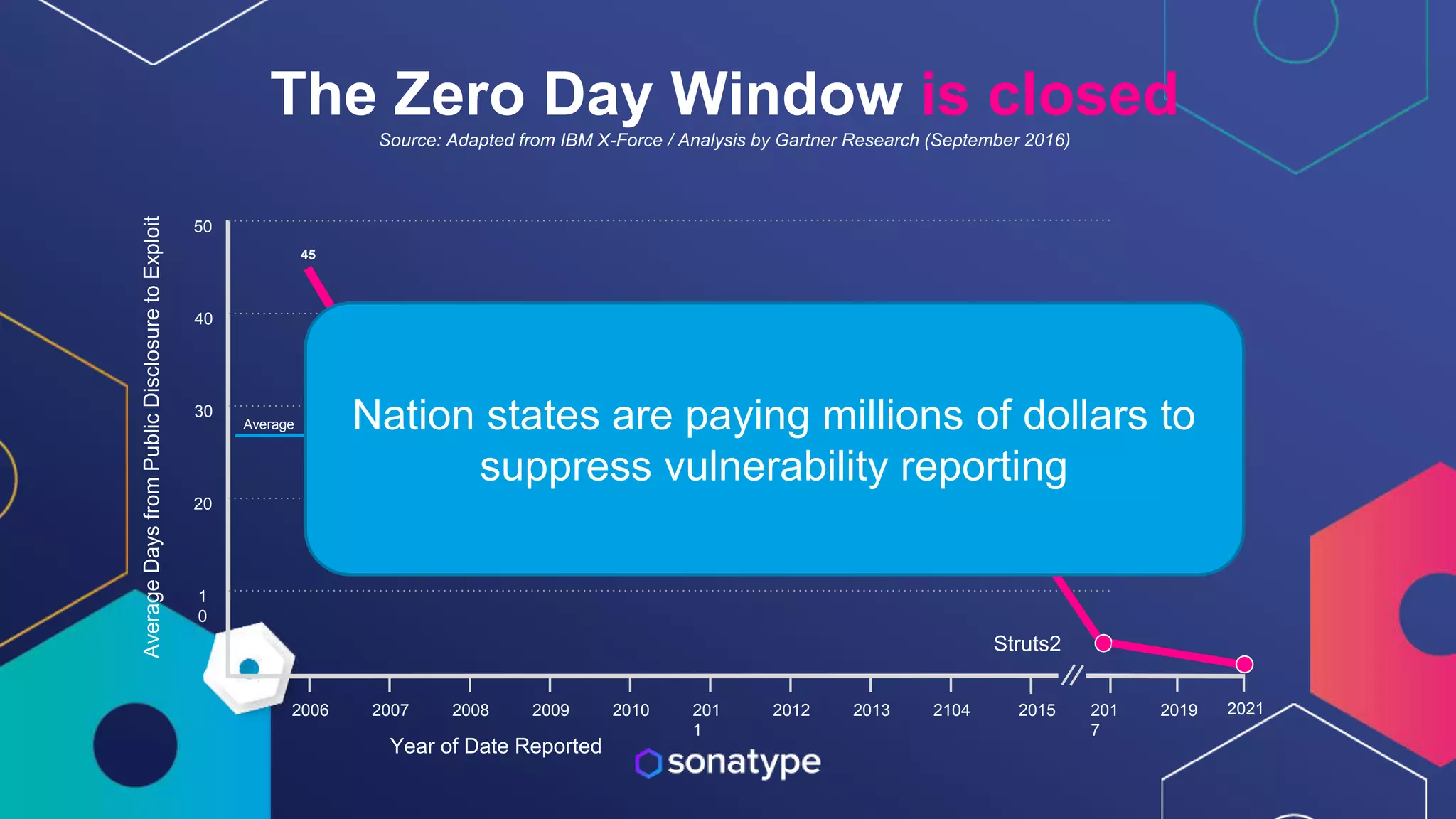
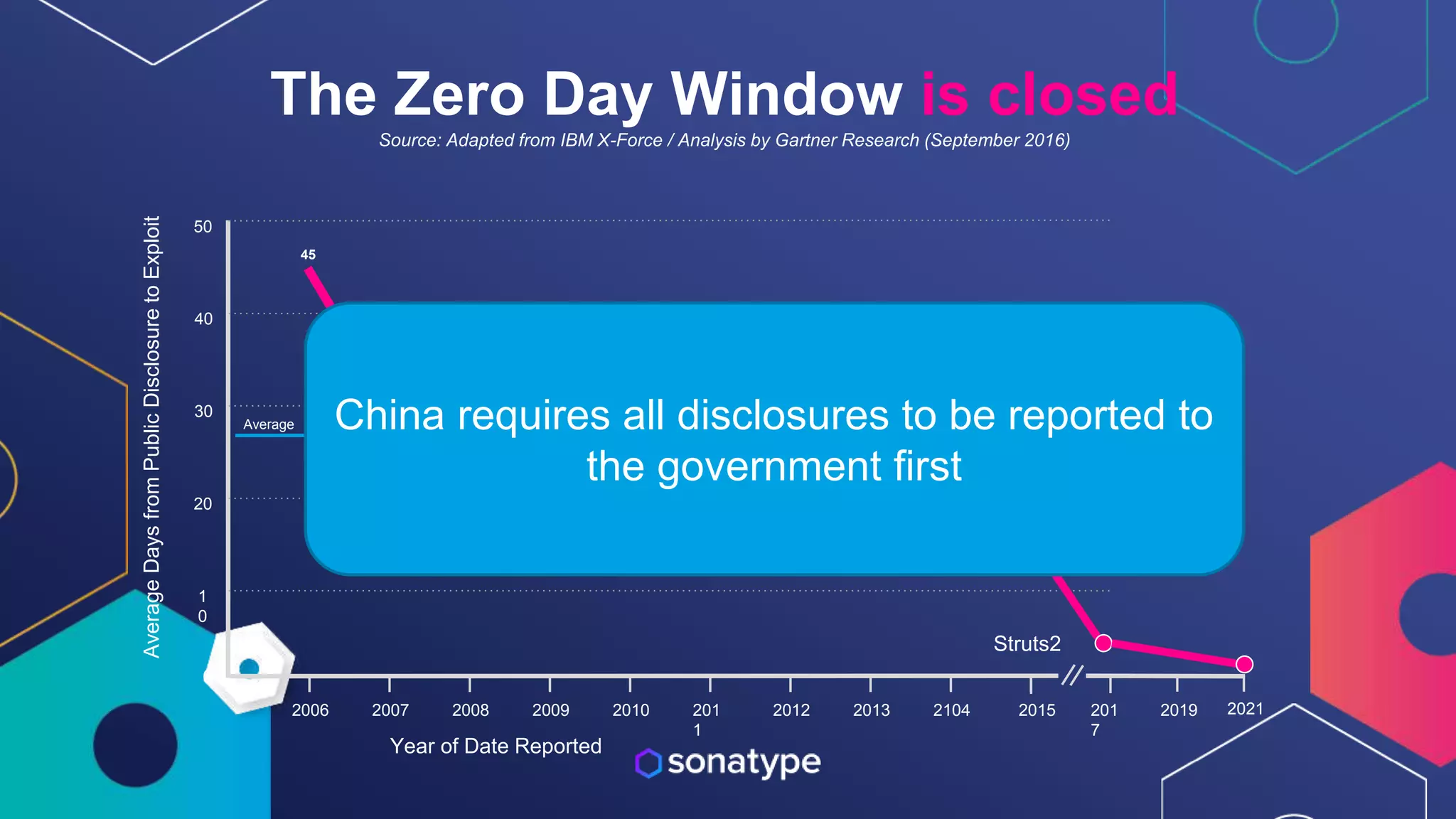
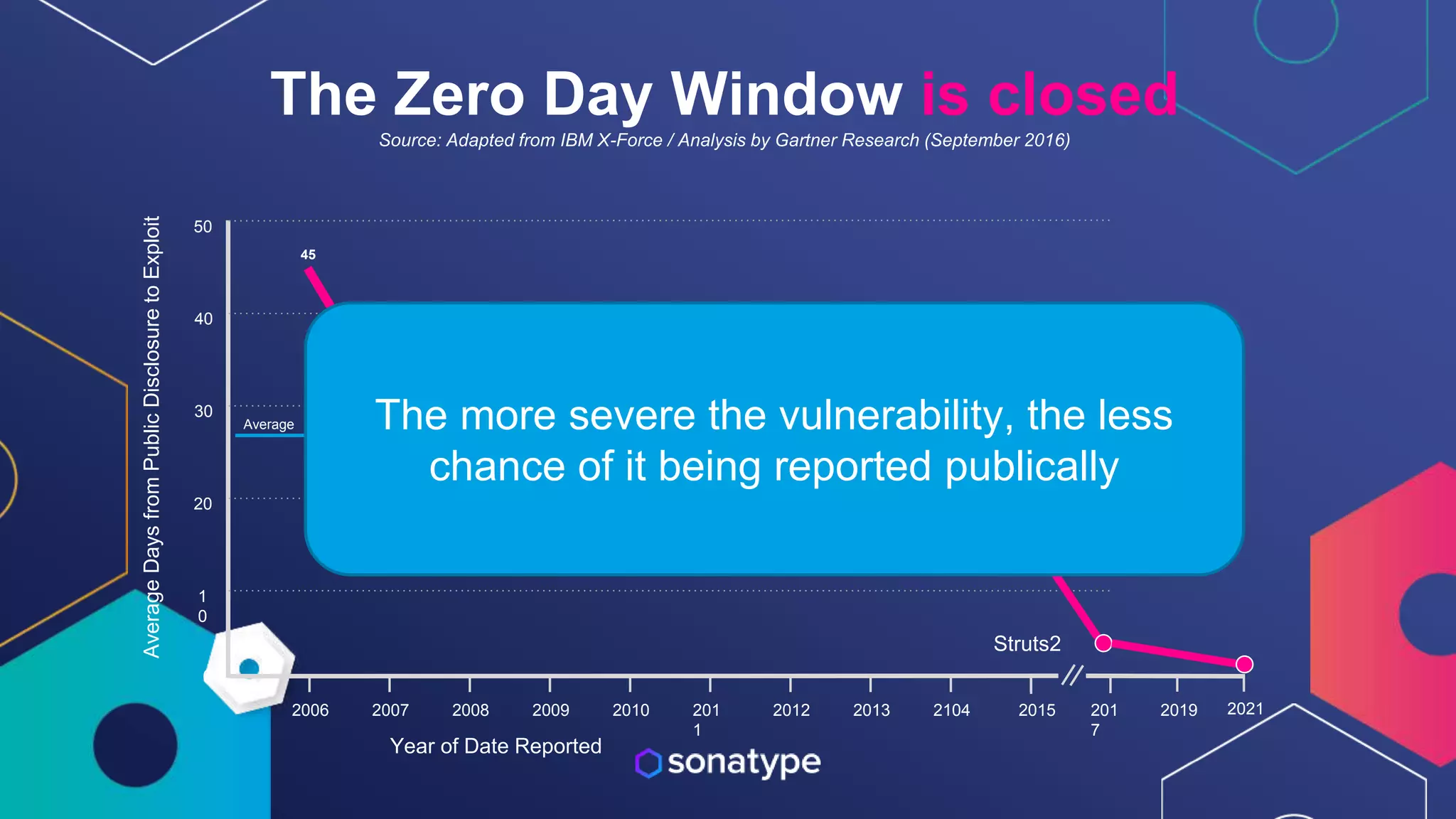
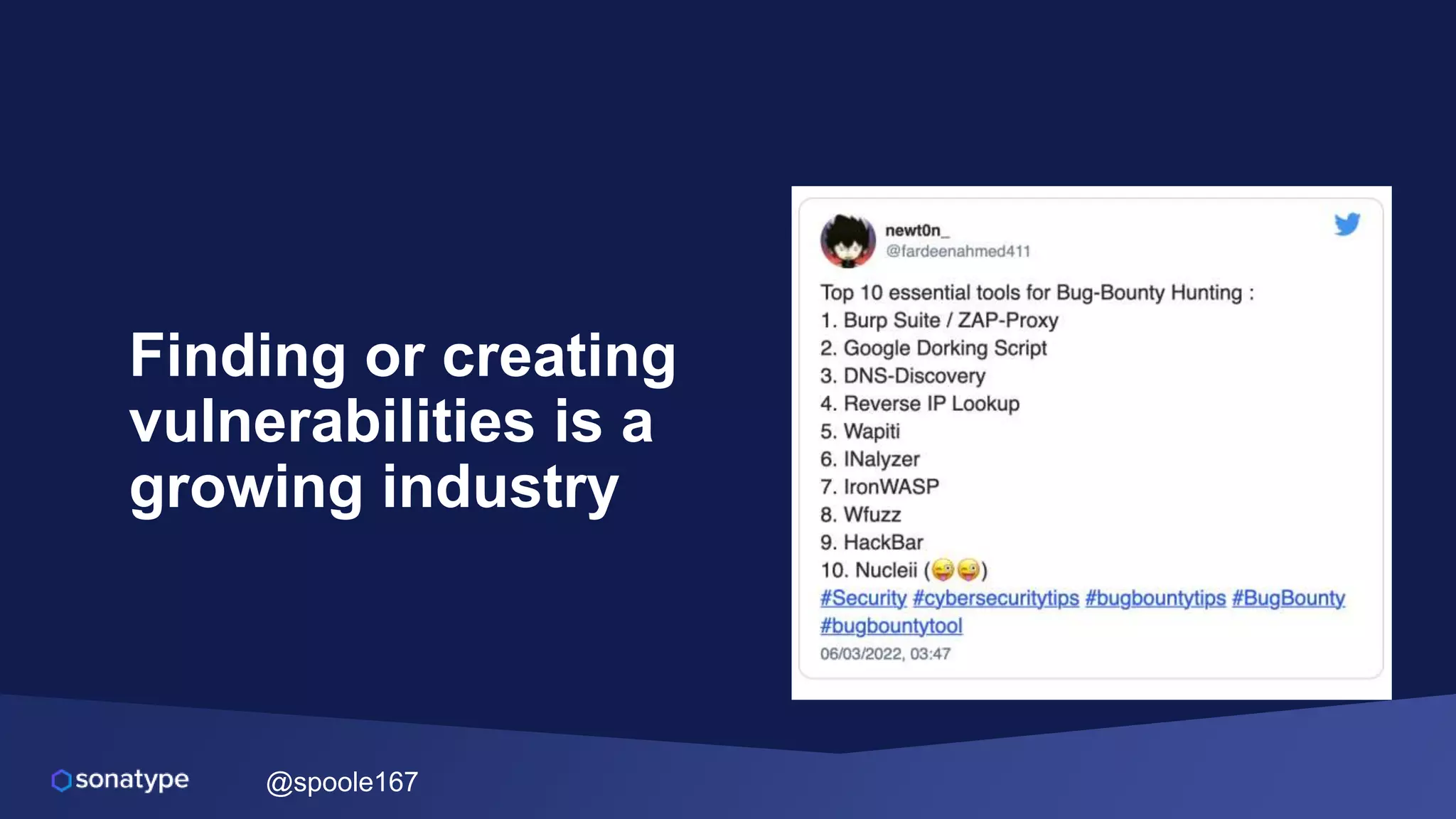
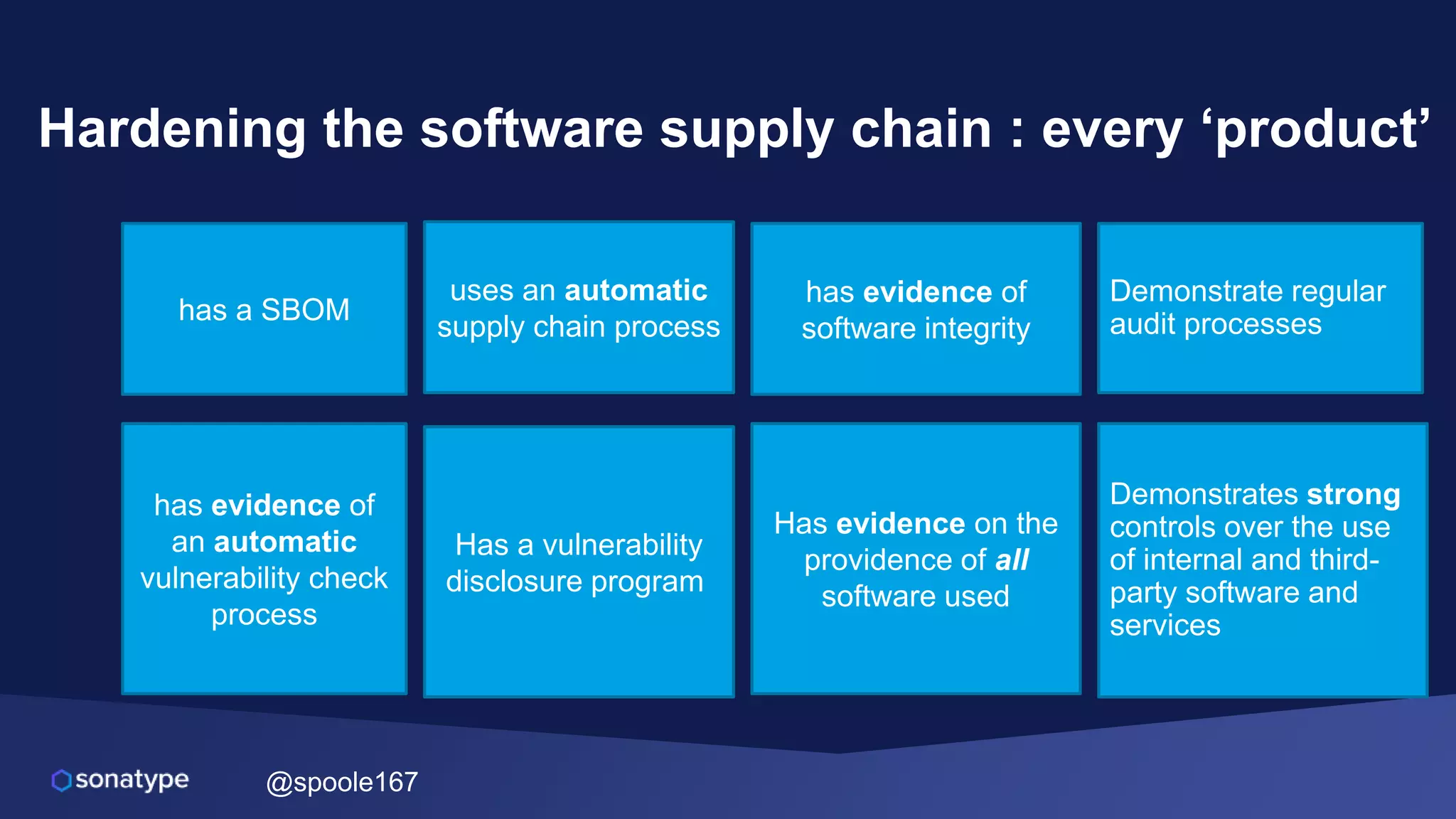
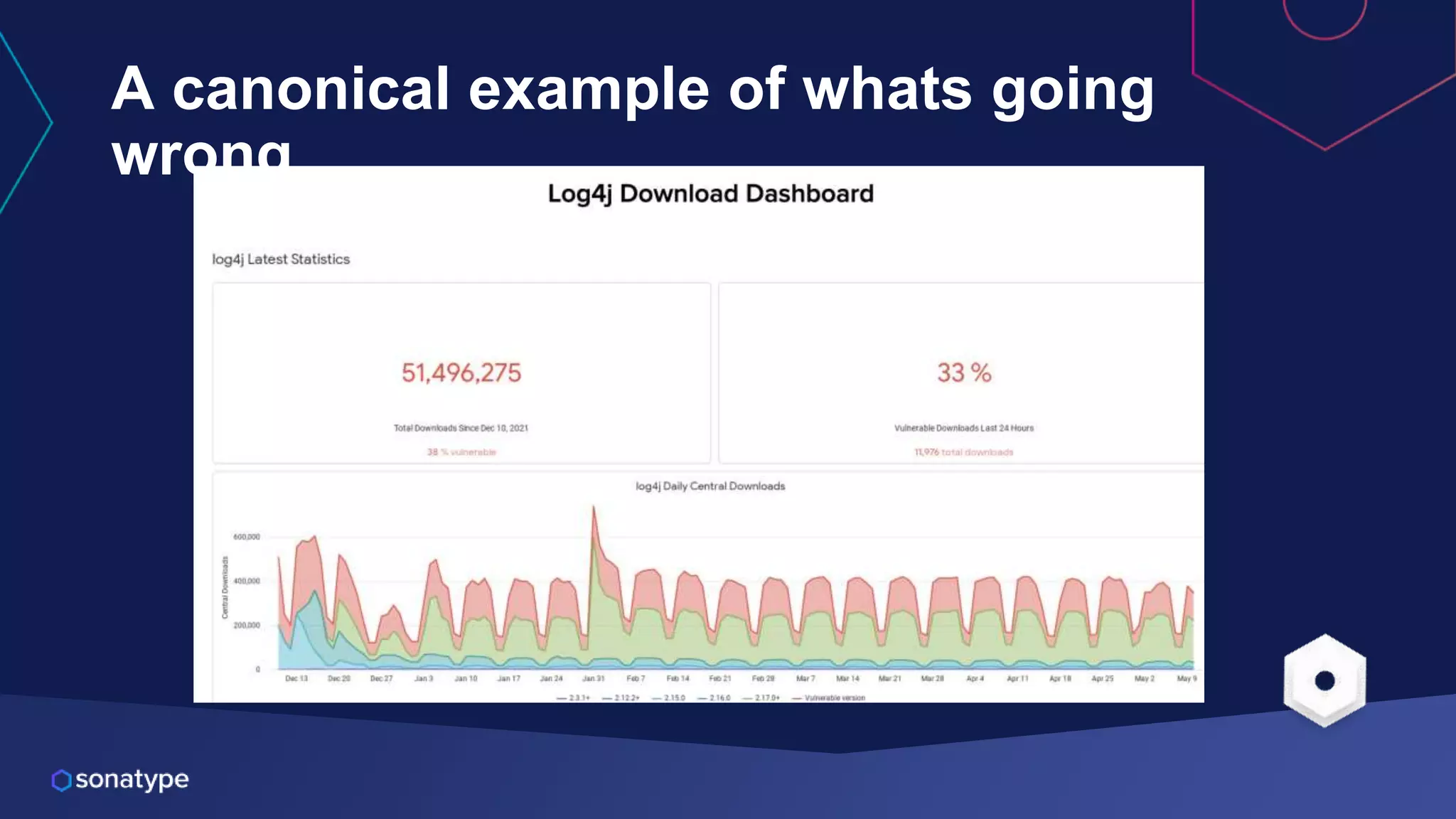
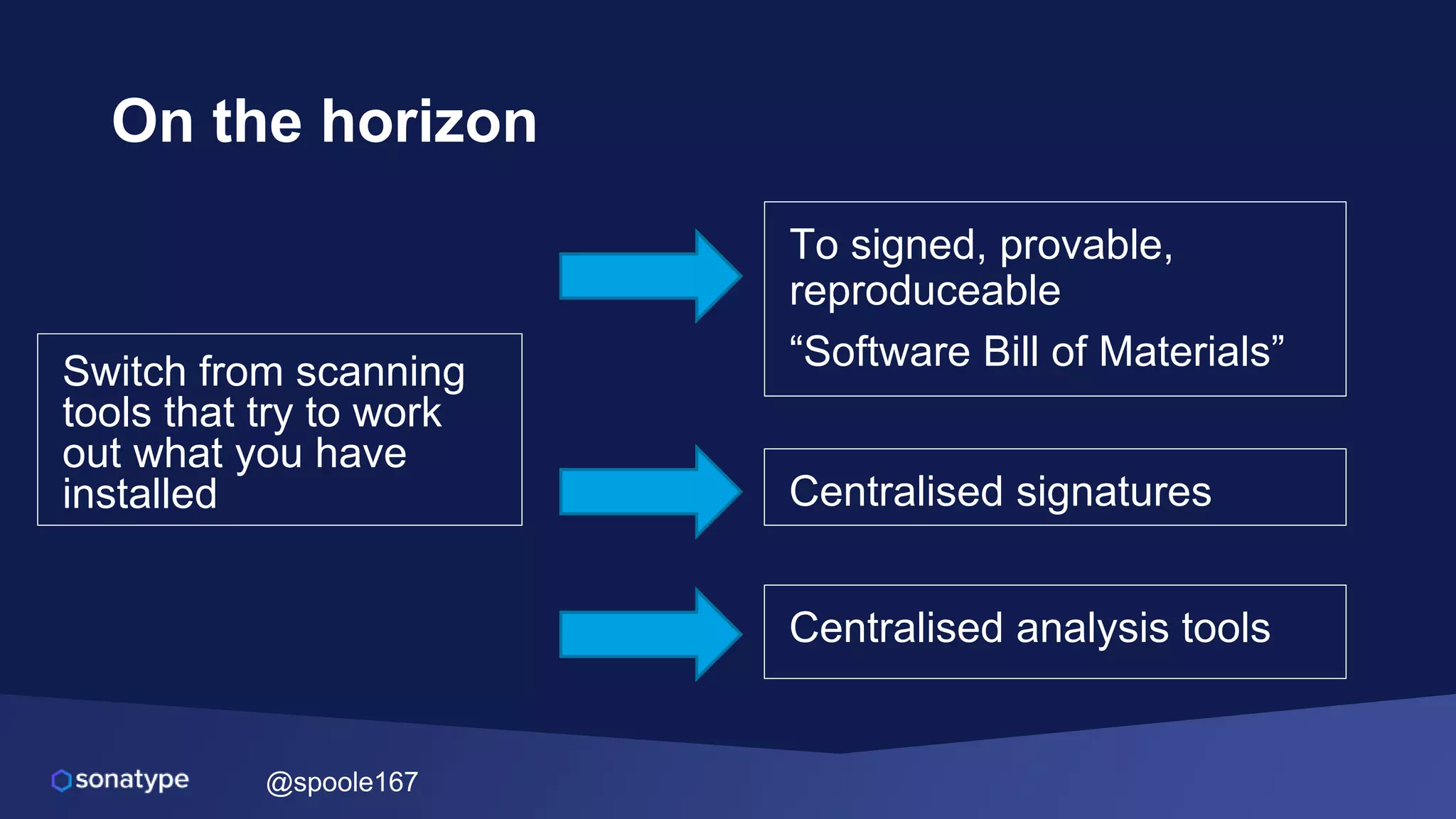
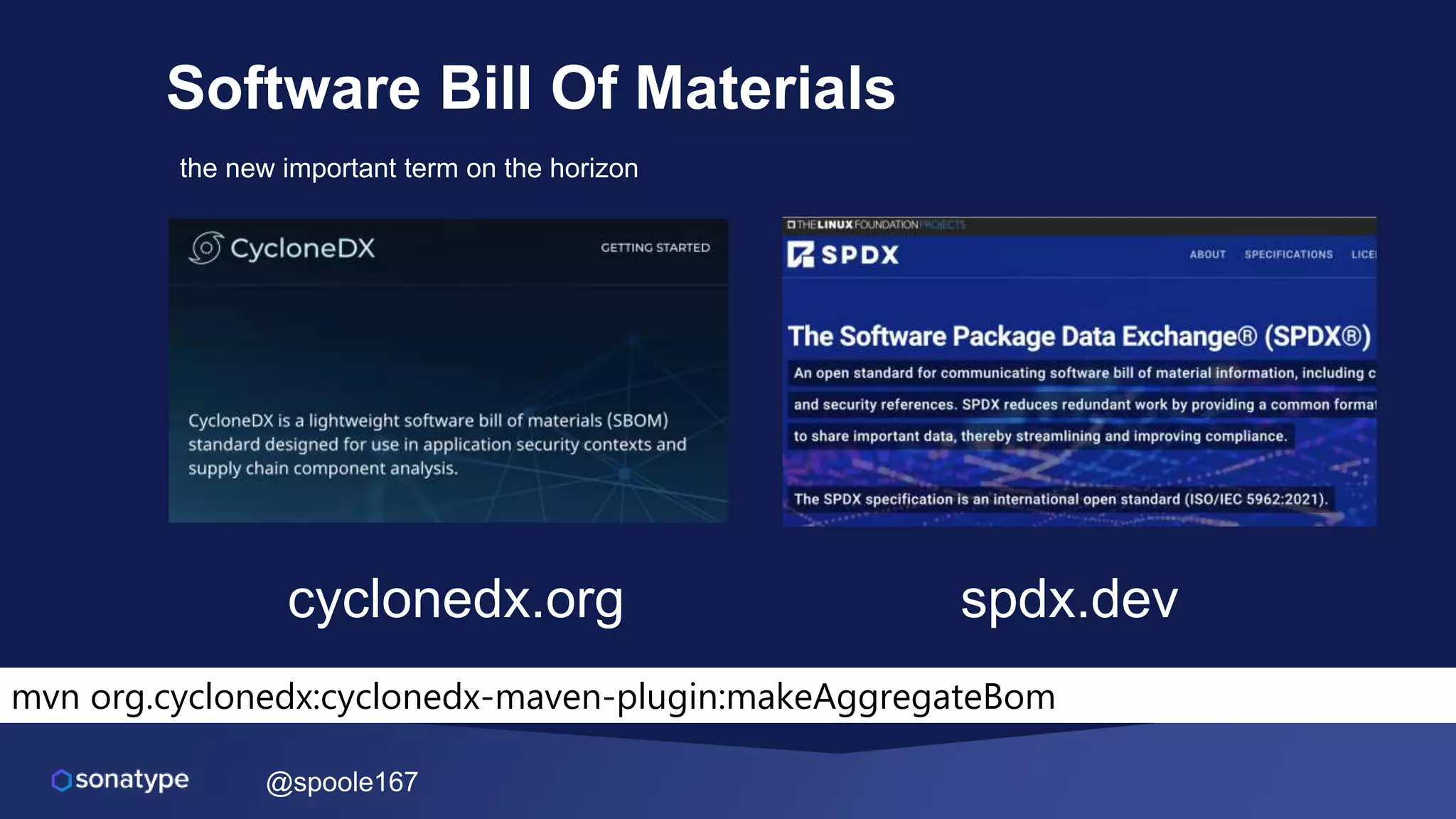
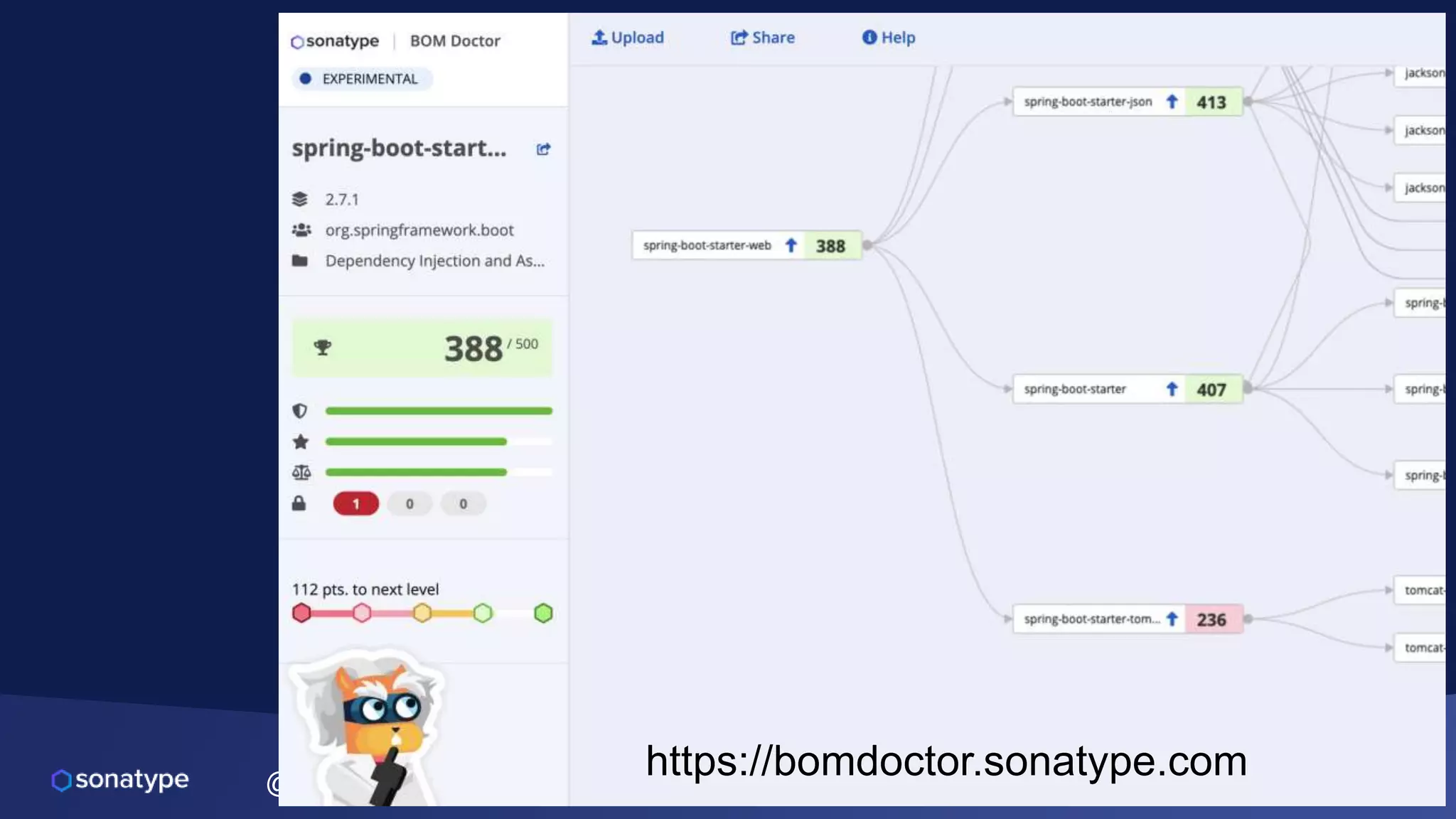
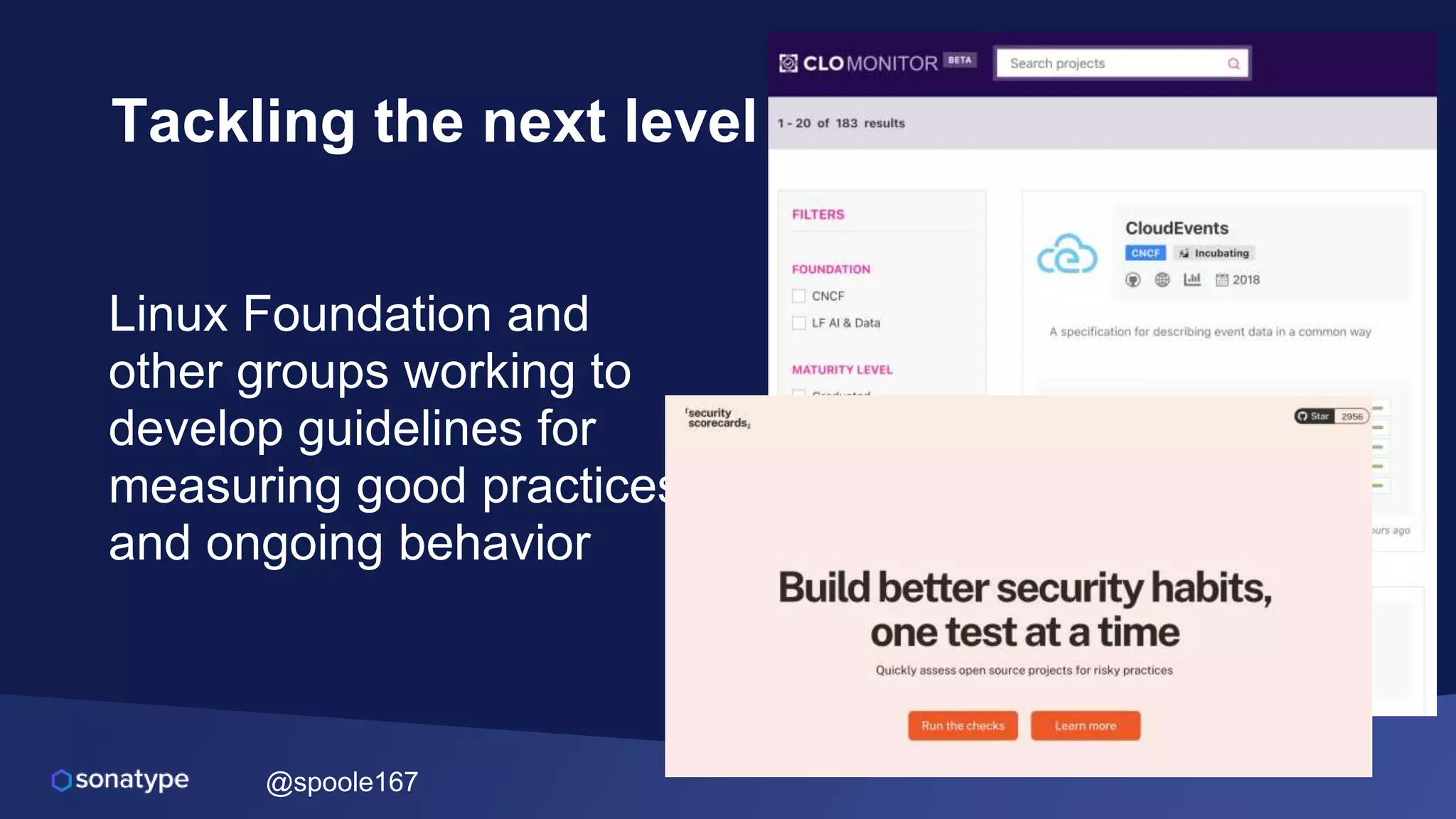
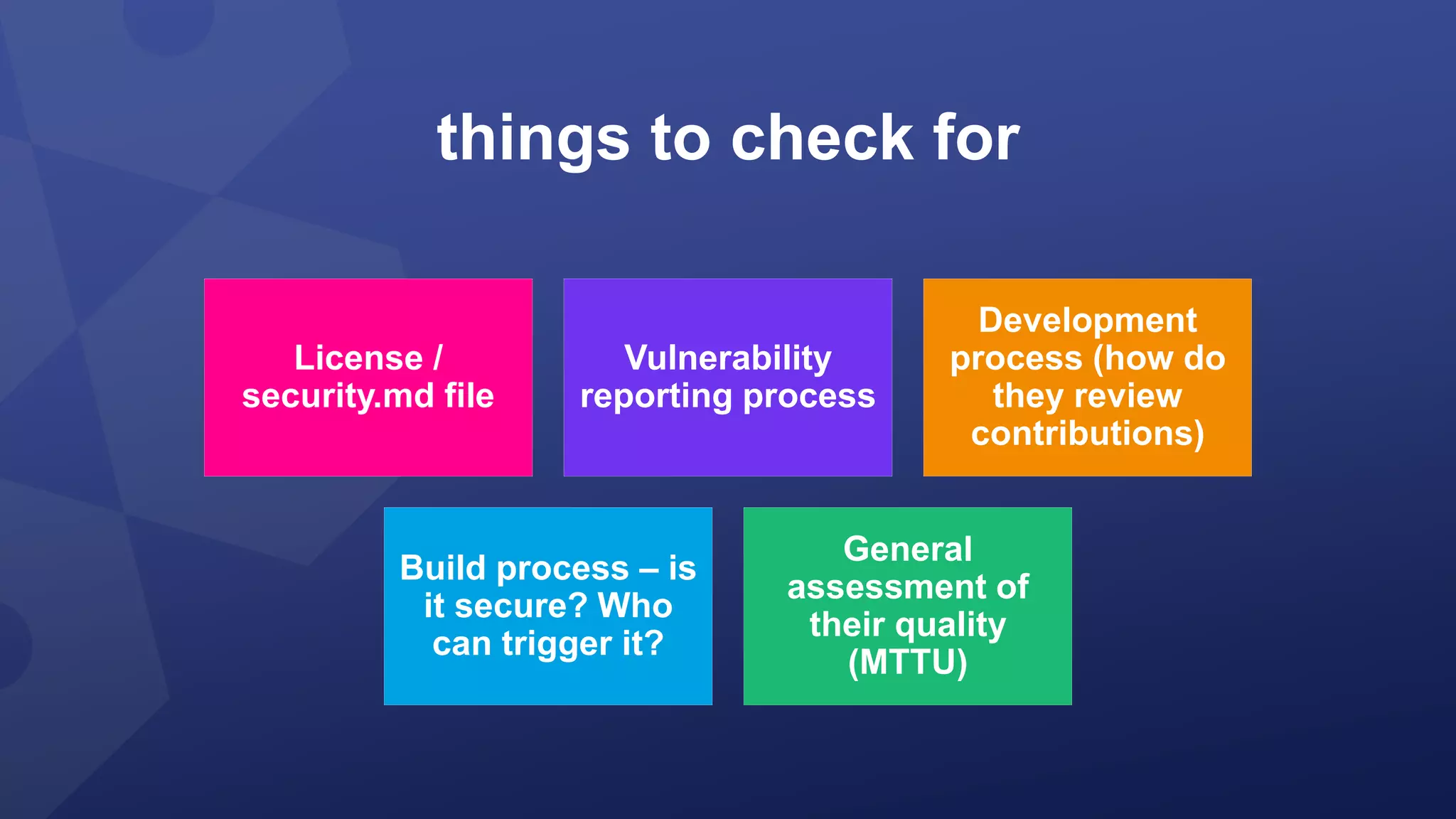
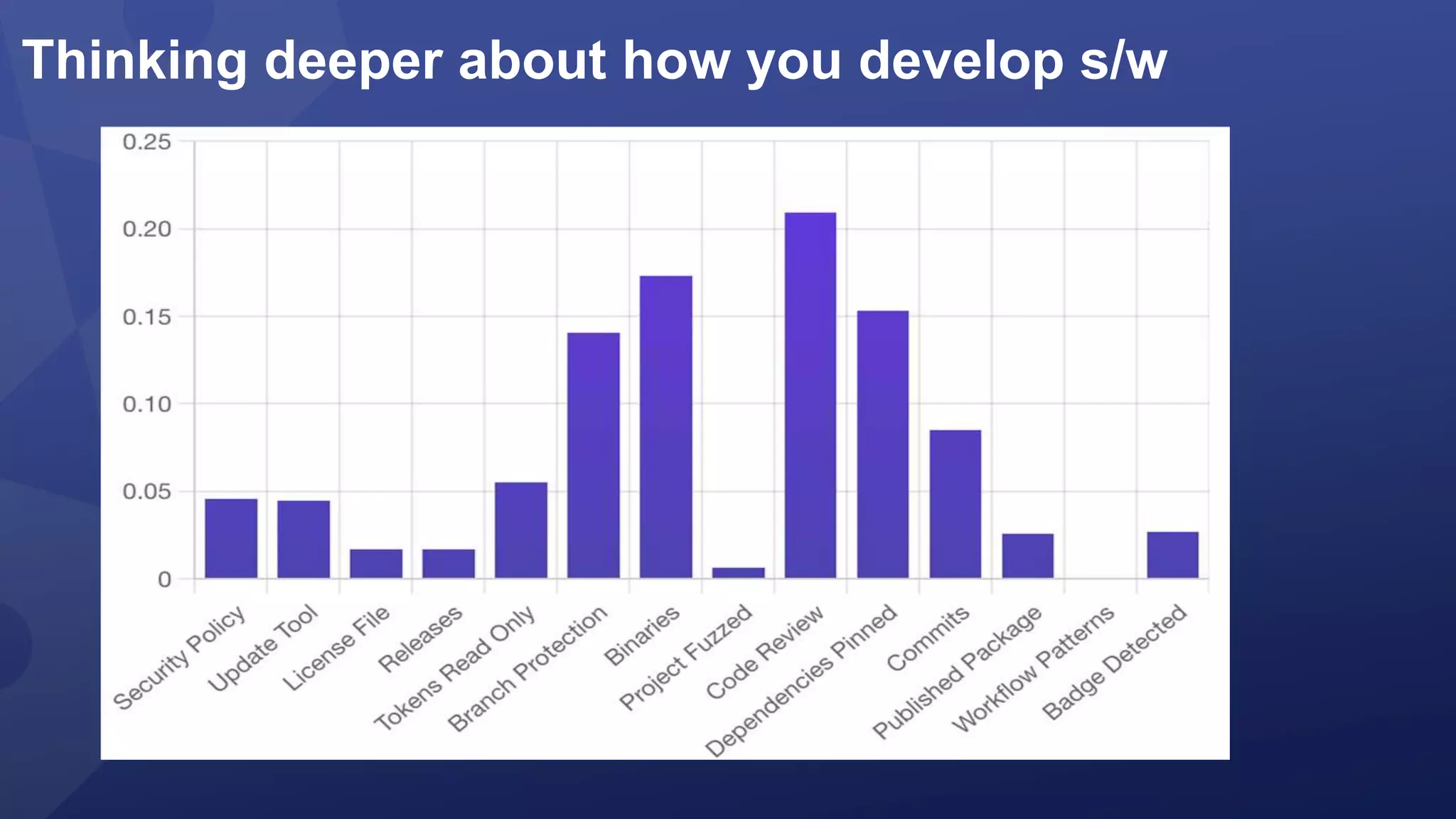
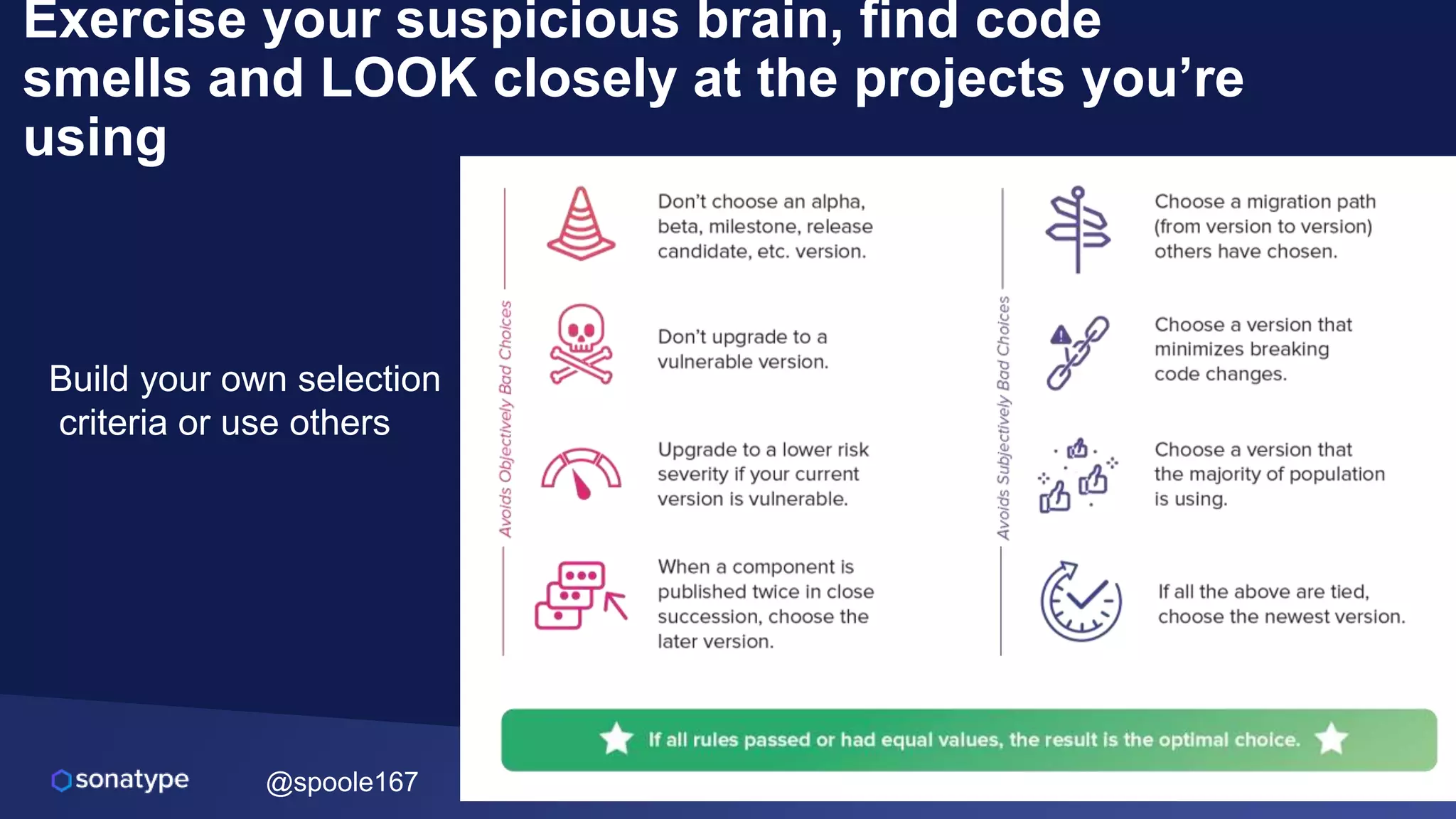
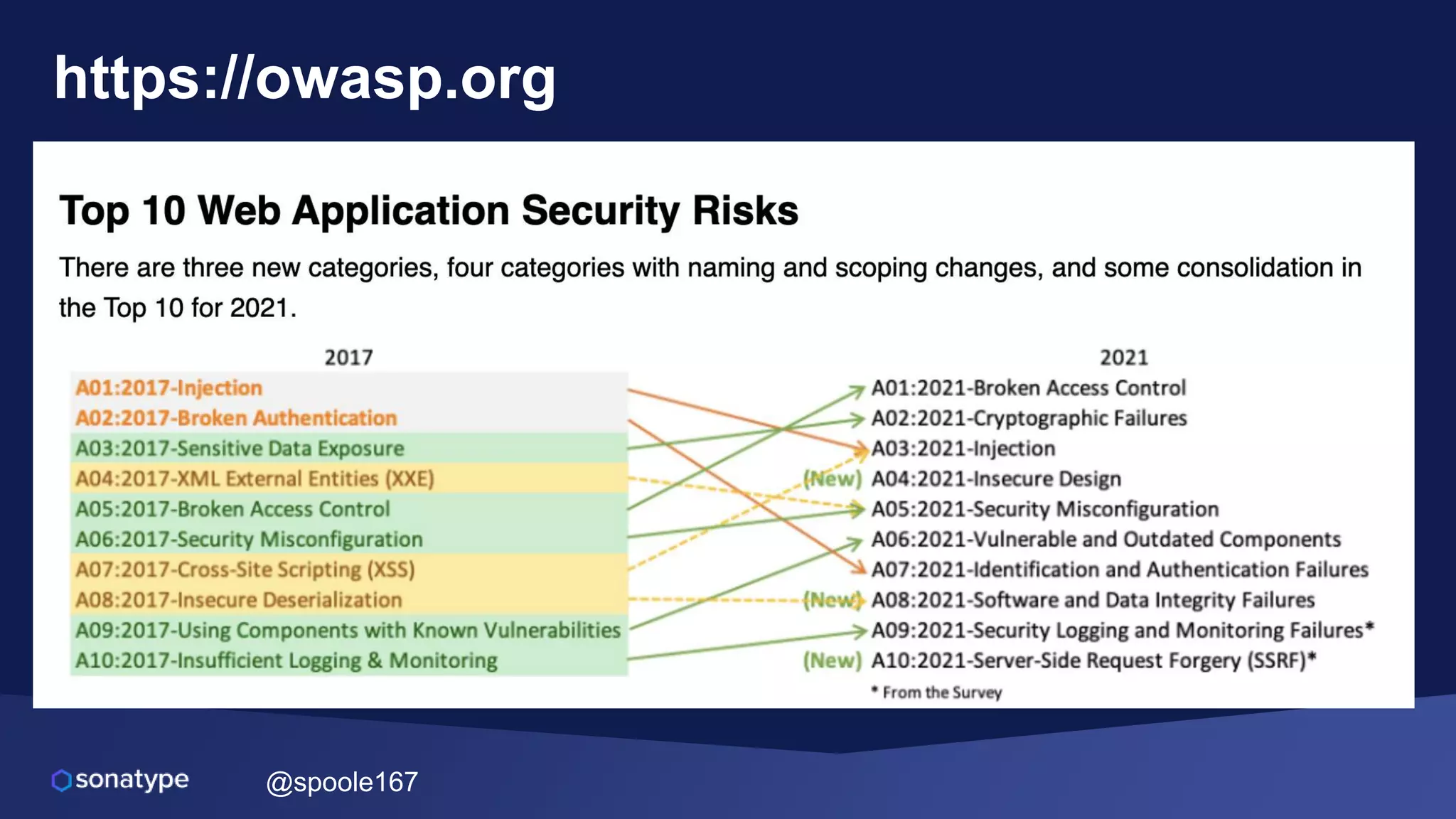
This document discusses the evolving threats from cybercrime and importance of securing the software supply chain. It notes that cybercrime now costs over $6 trillion annually, similar to the global GDP of major countries. Attacks have become more sophisticated using techniques like supply chain compromises and exploiting vulnerabilities before they are publicly known. Developers are urged to carefully select open source components based on security practices like using SBOMs and rapid patching. The talk recommends following secure development principles and keeping educated on improving tools that can help harden applications and their supply chains.