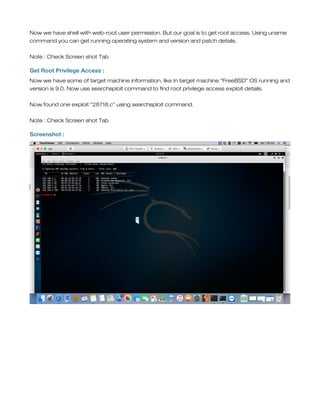
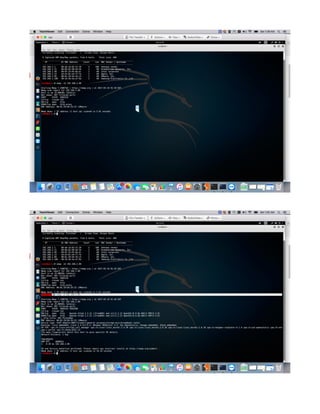
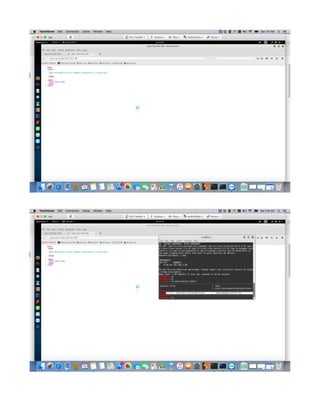
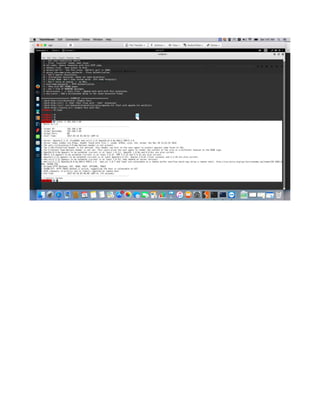
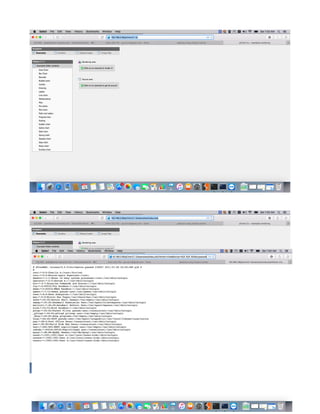
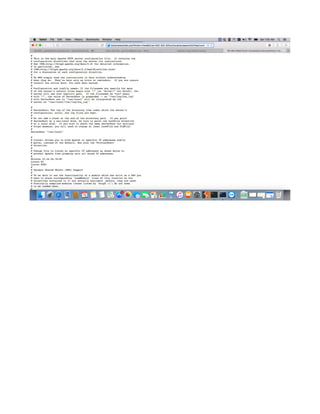
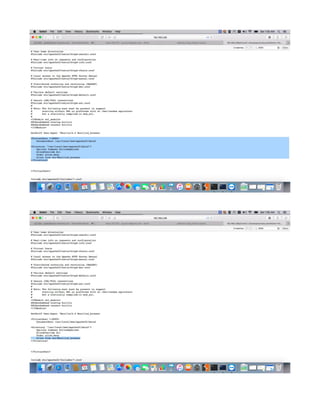
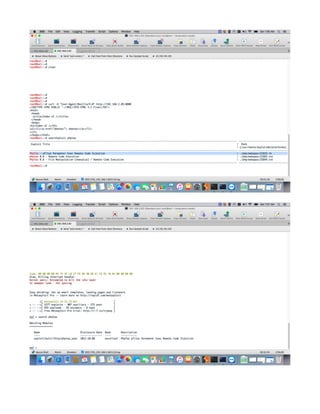
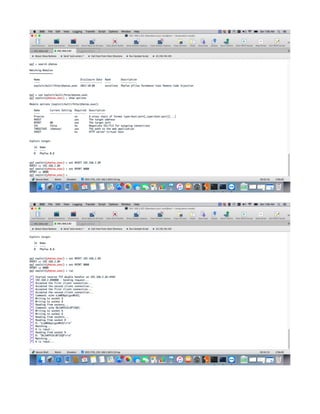
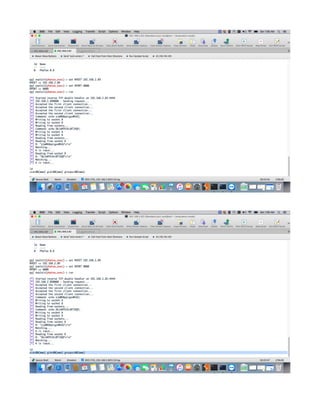
This document provides a tutorial on exploiting the Kioptrix 2014 (#5) vulnerable machine, targeted at beginners in information security. It includes instructions for setting up the virtual machine, discovering IP addresses, and finding vulnerabilities in the web applications hosted on the machine, specifically focusing on Local File Inclusion (LFI) vulnerabilities. The process culminates in obtaining root access through exploiting a vulnerability in the FreeBSD operating system running on the target machine.