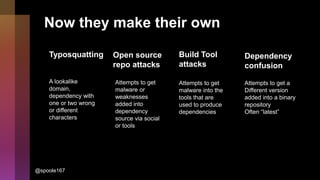
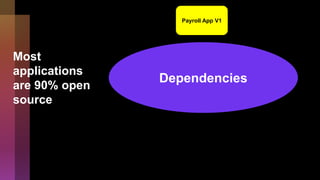
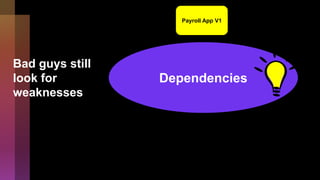
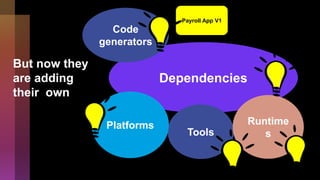
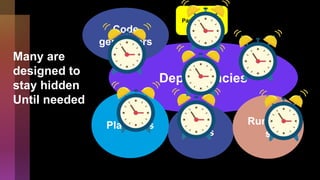
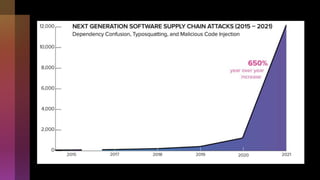
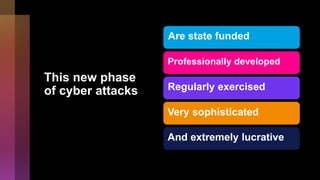
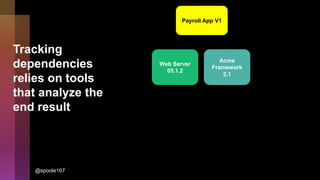
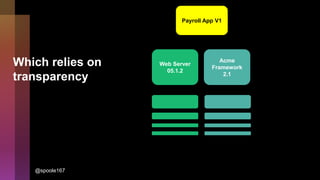
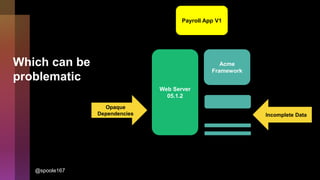
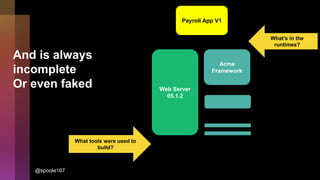
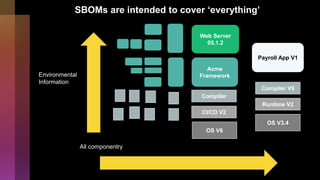
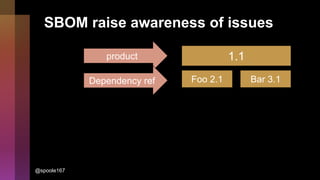
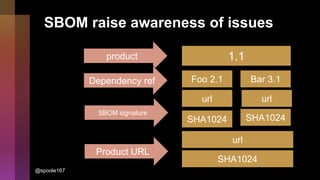
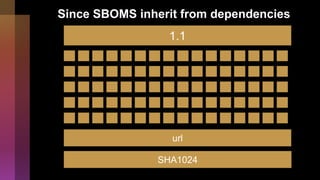
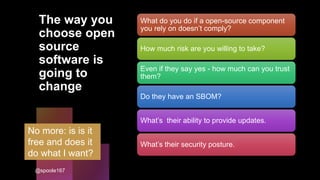
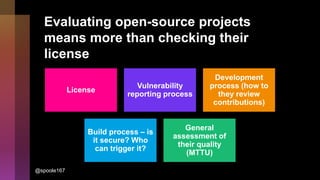
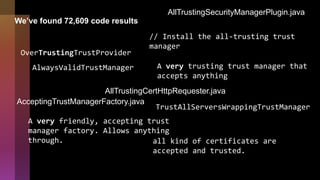
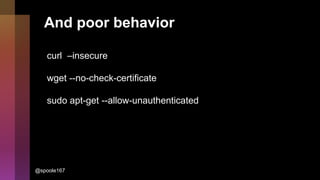
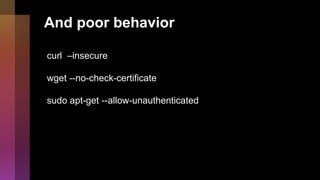
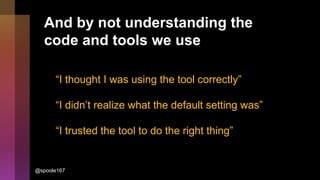
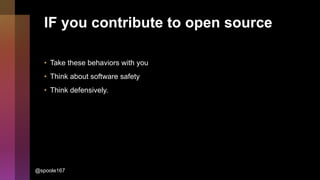
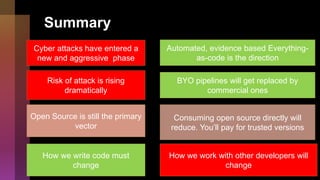
Cybercrime is becoming increasingly sophisticated and profitable, with its estimated worth reaching $6 trillion, prompting a significant shift in how developers must approach software security. The focus is moving towards automating vulnerability assessments and ensuring software supply chain integrity through practices like Software Bill of Materials (SBOM). Developers are urged to adopt a defensive coding mindset, evaluate open-source dependencies critically, and prepare for an era where evidence-based trust in software production will be essential.