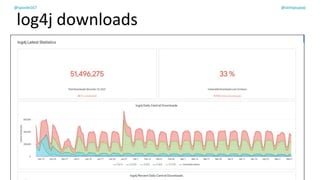
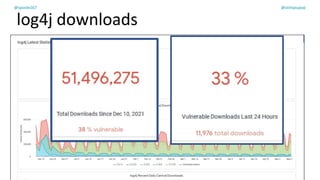
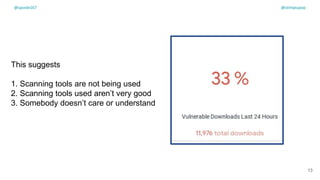
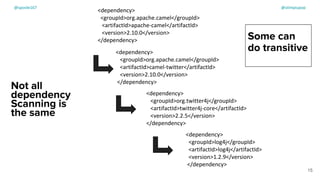
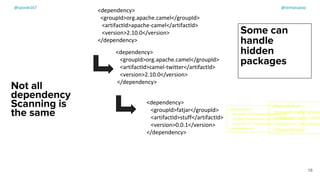
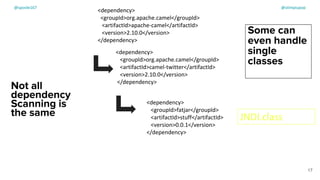
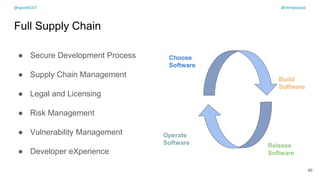
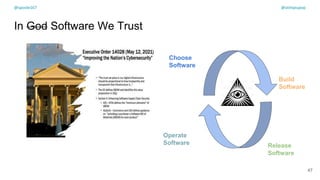
The document discusses the challenges of dependency management in modern applications that primarily rely on open-source dependencies, highlighting the vulnerabilities and the increasing sophistication of cyber threats. It emphasizes the need for better scanning tools and proactive security measures, given the rise of supply chain attacks and other malicious tactics targeting software development and deployment. Additionally, it advocates for transparency through Software Bills of Materials (SBOM) to manage risks and maintain software integrity.




















![Transparency: A Beginning
SBOM = Software Bill Of Material
[
/ˌ’sɒftweə(r) bɪl əv məˈtɪəriəl/
1. Silver Bullet for Omniscient risk Management
2. In short, it is a way to tell another party all of the software that is
used in the stack that makes up an application.
3. Similar to ingredients labels on food. They are critical to keep
consumers safe and healthy, they are somewhat standardized, but
it is a lot more exciting to grow or make the food rather than the
label.
]
48
@spoole167 @olimpiupop](https://image.slidesharecdn.com/stopsecuritybysleightofhand-221009162044-0d4feedf/85/Stop-Security-by-Sleight-Of-Hand-pptx-48-320.jpg)