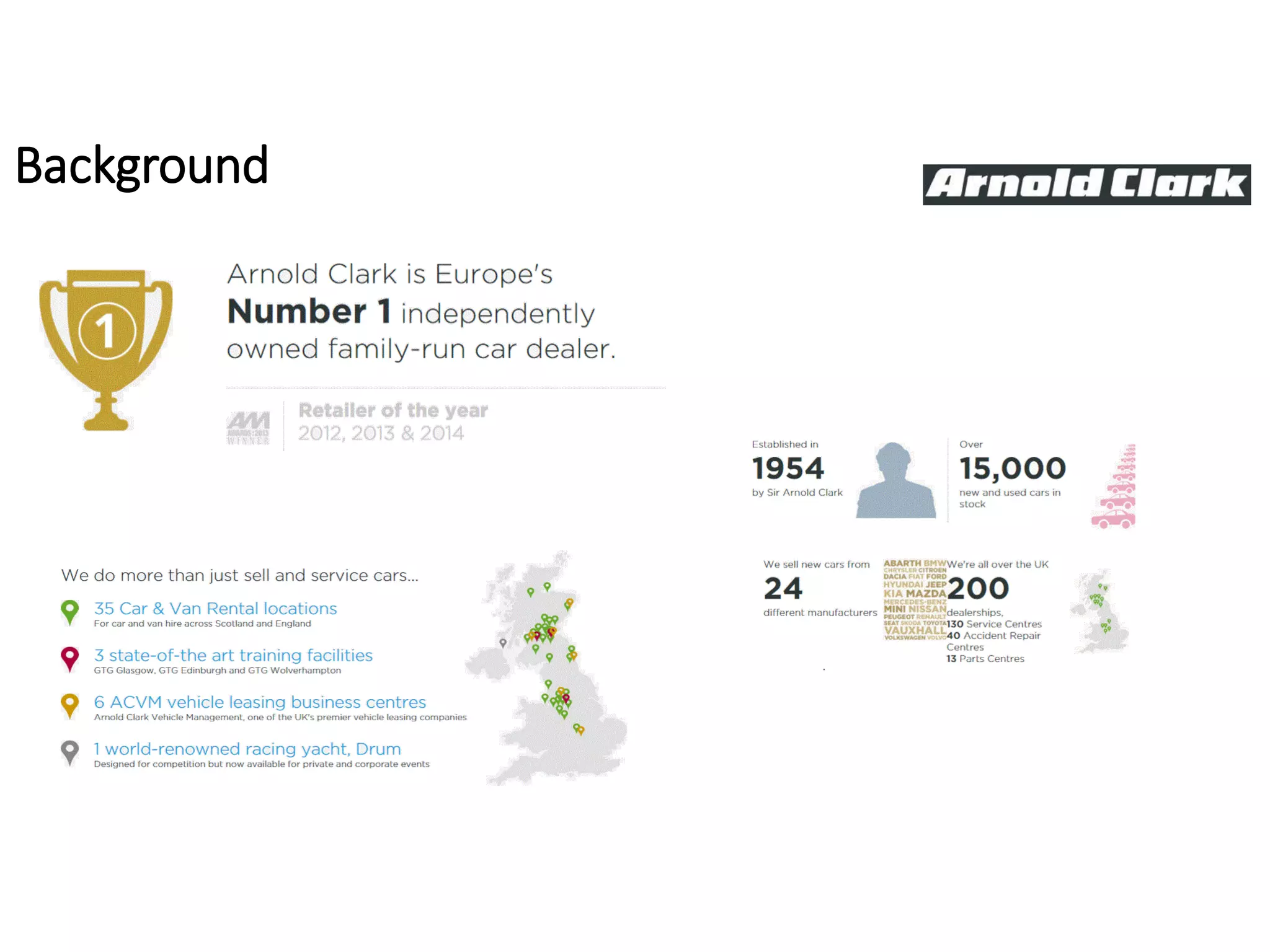
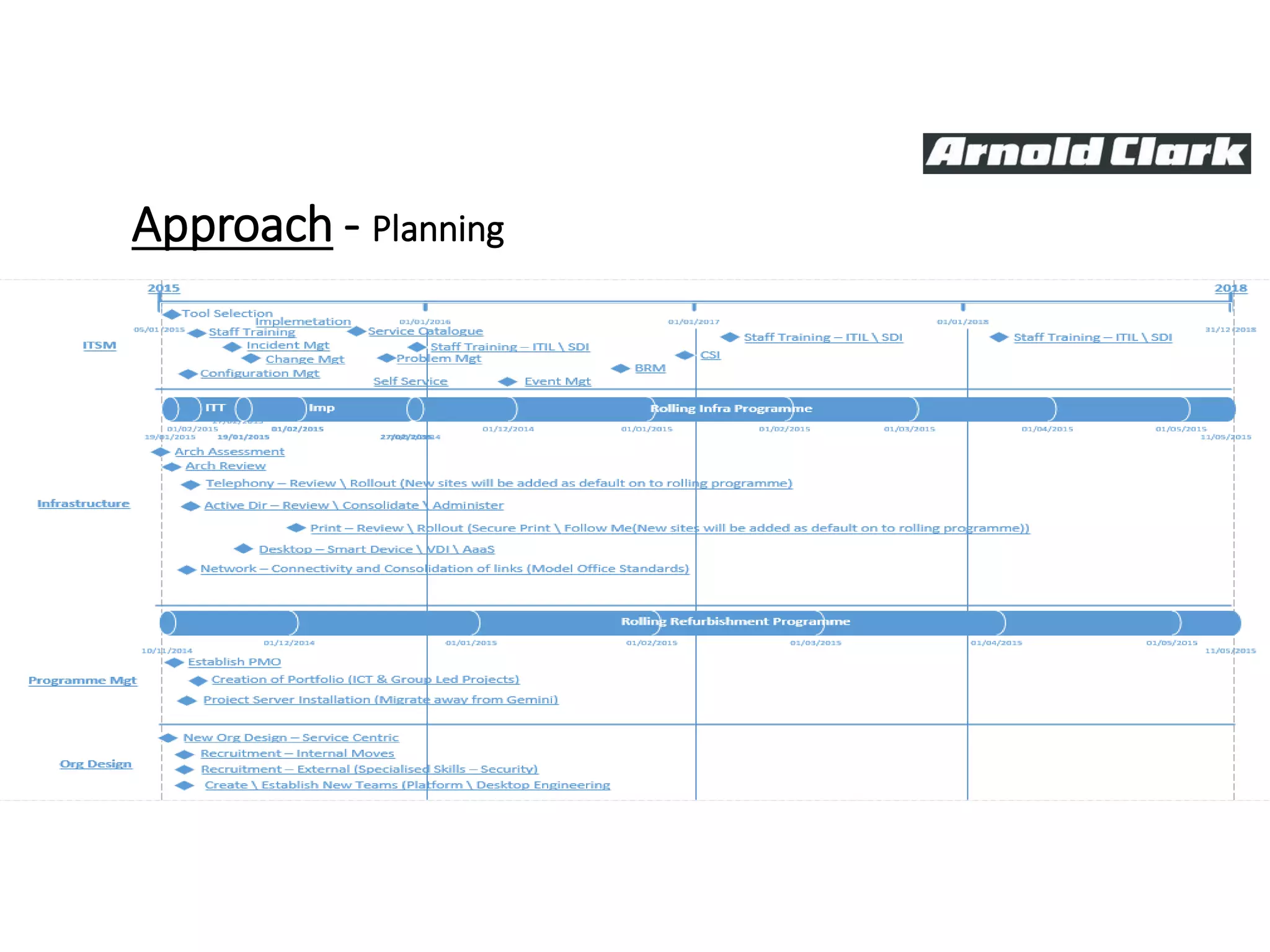
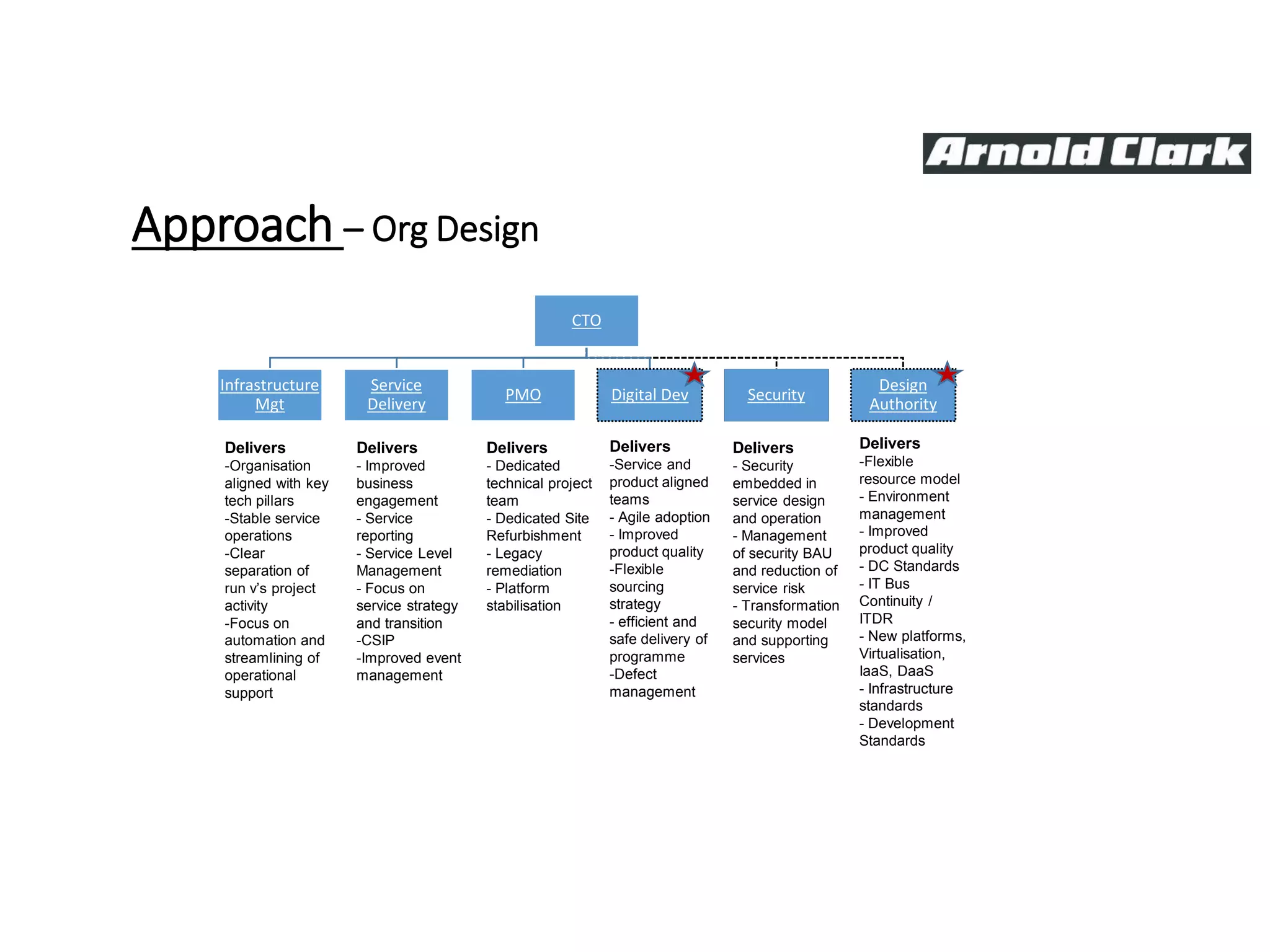
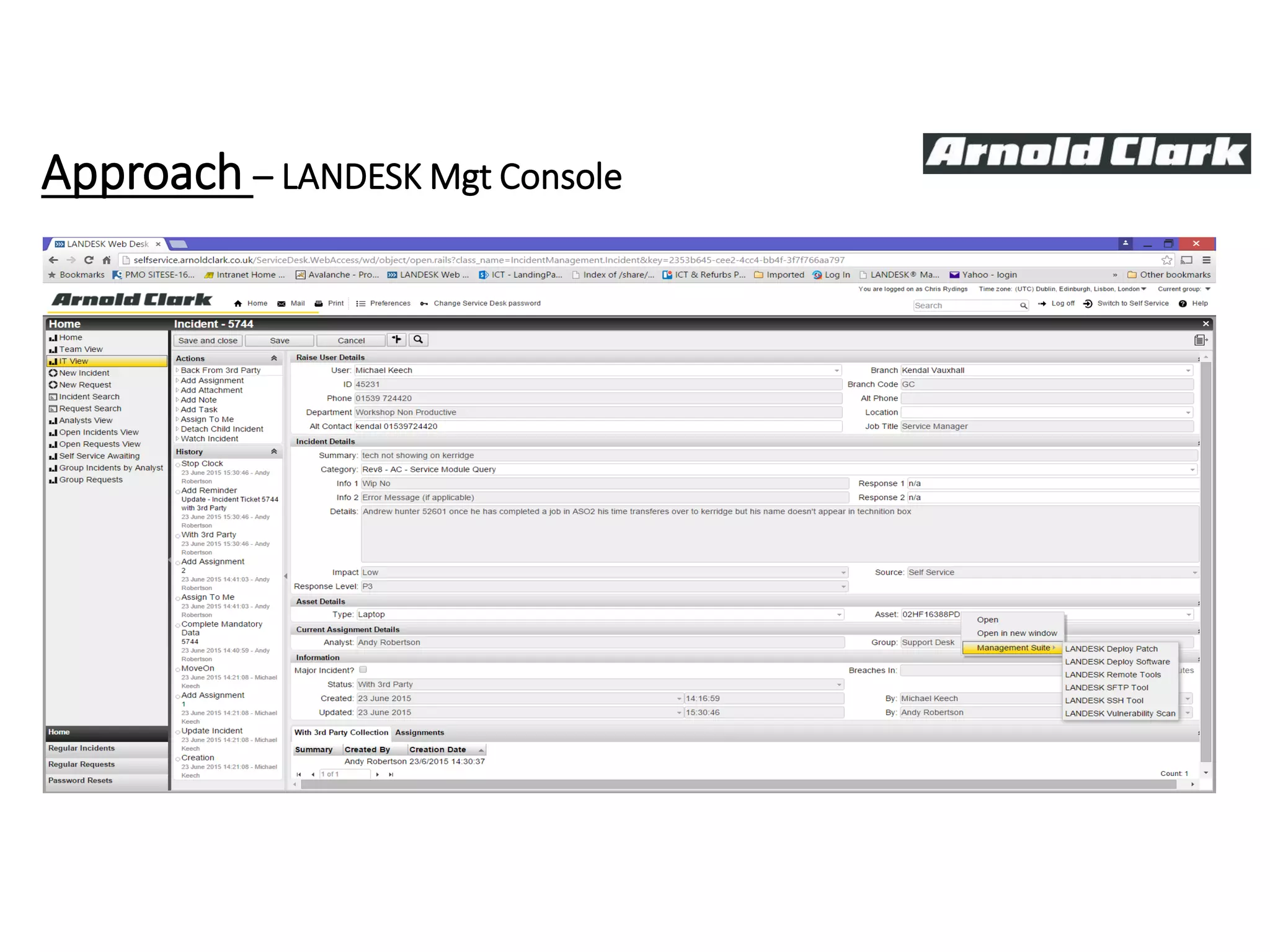
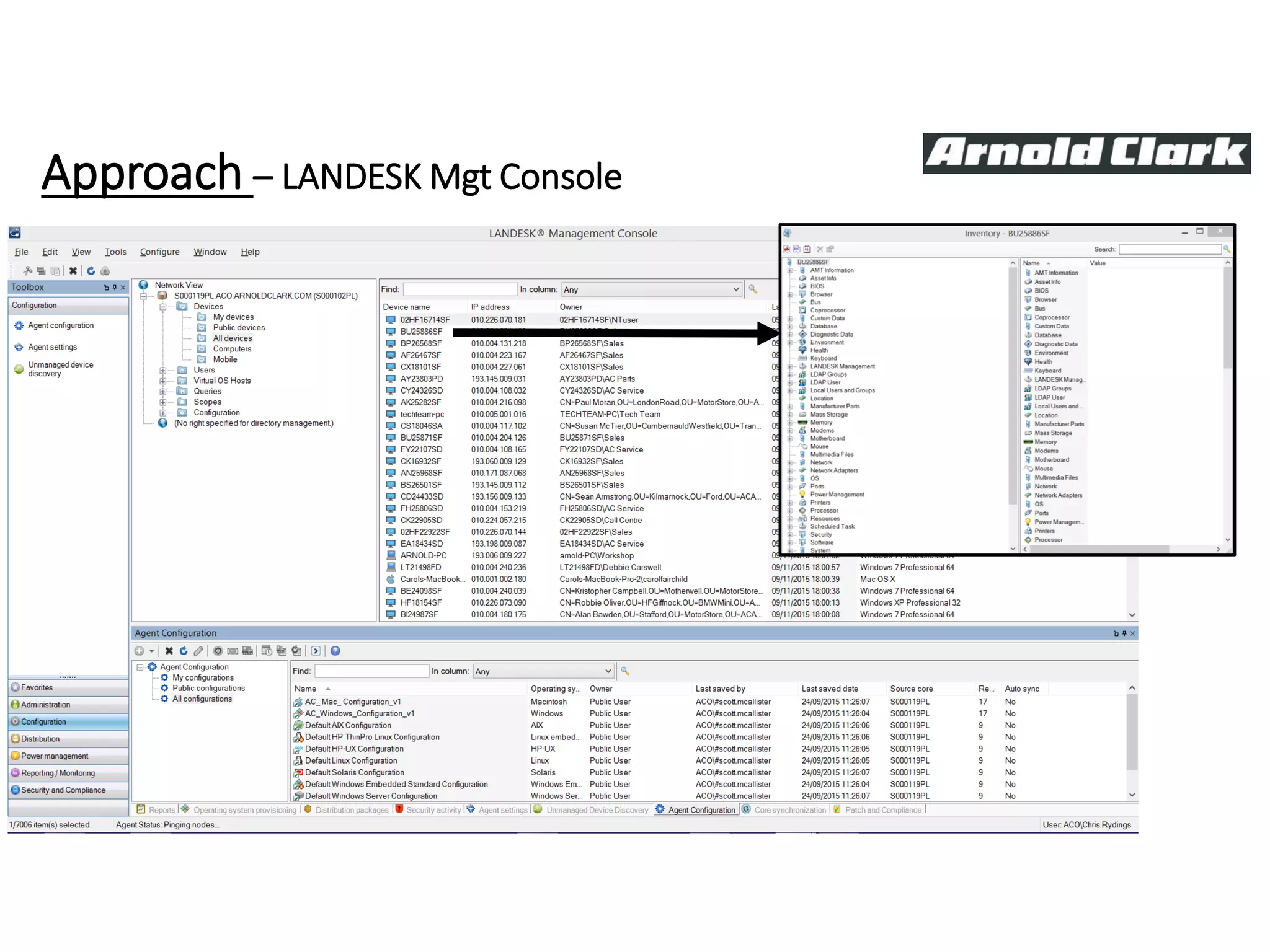
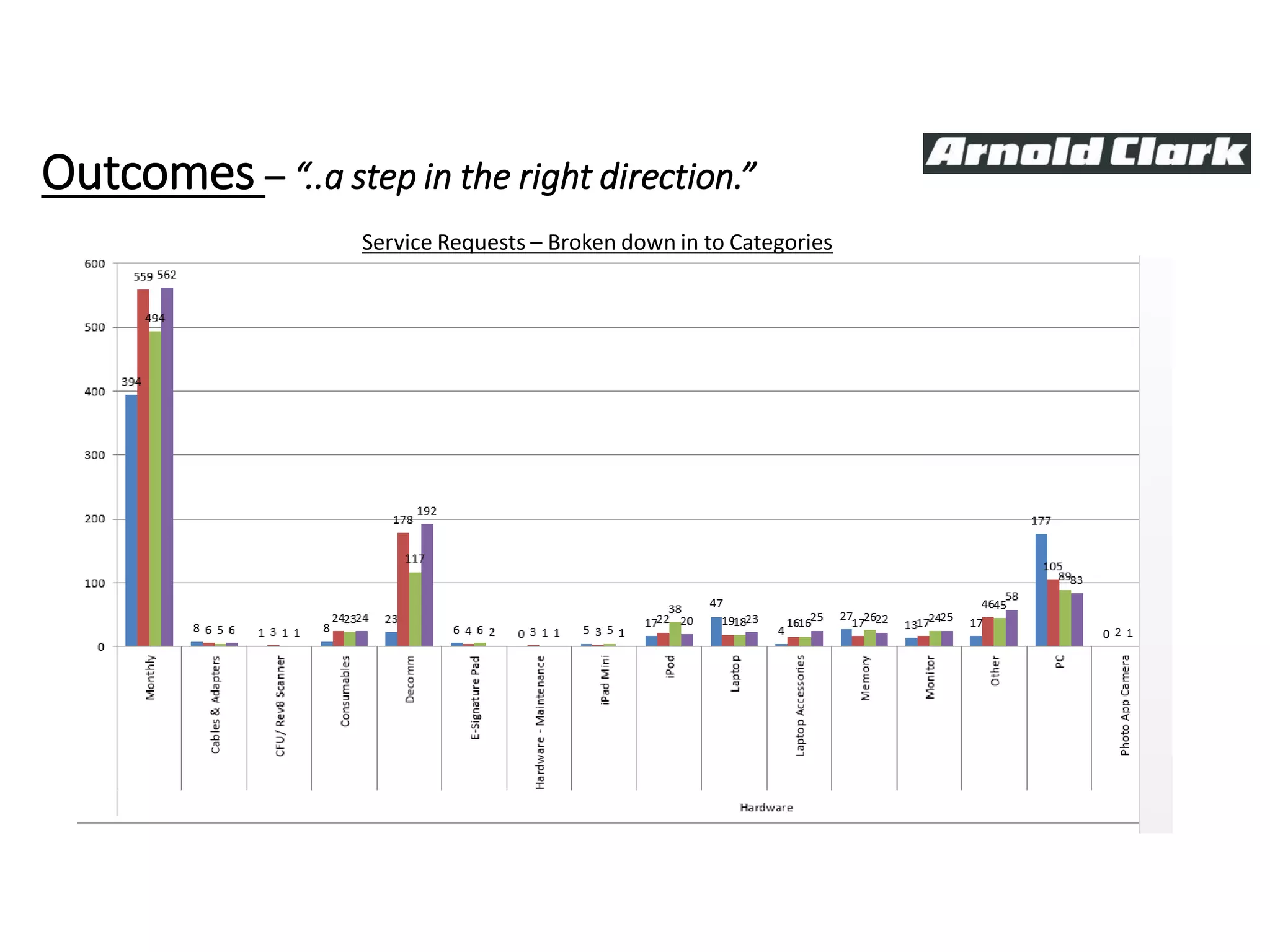
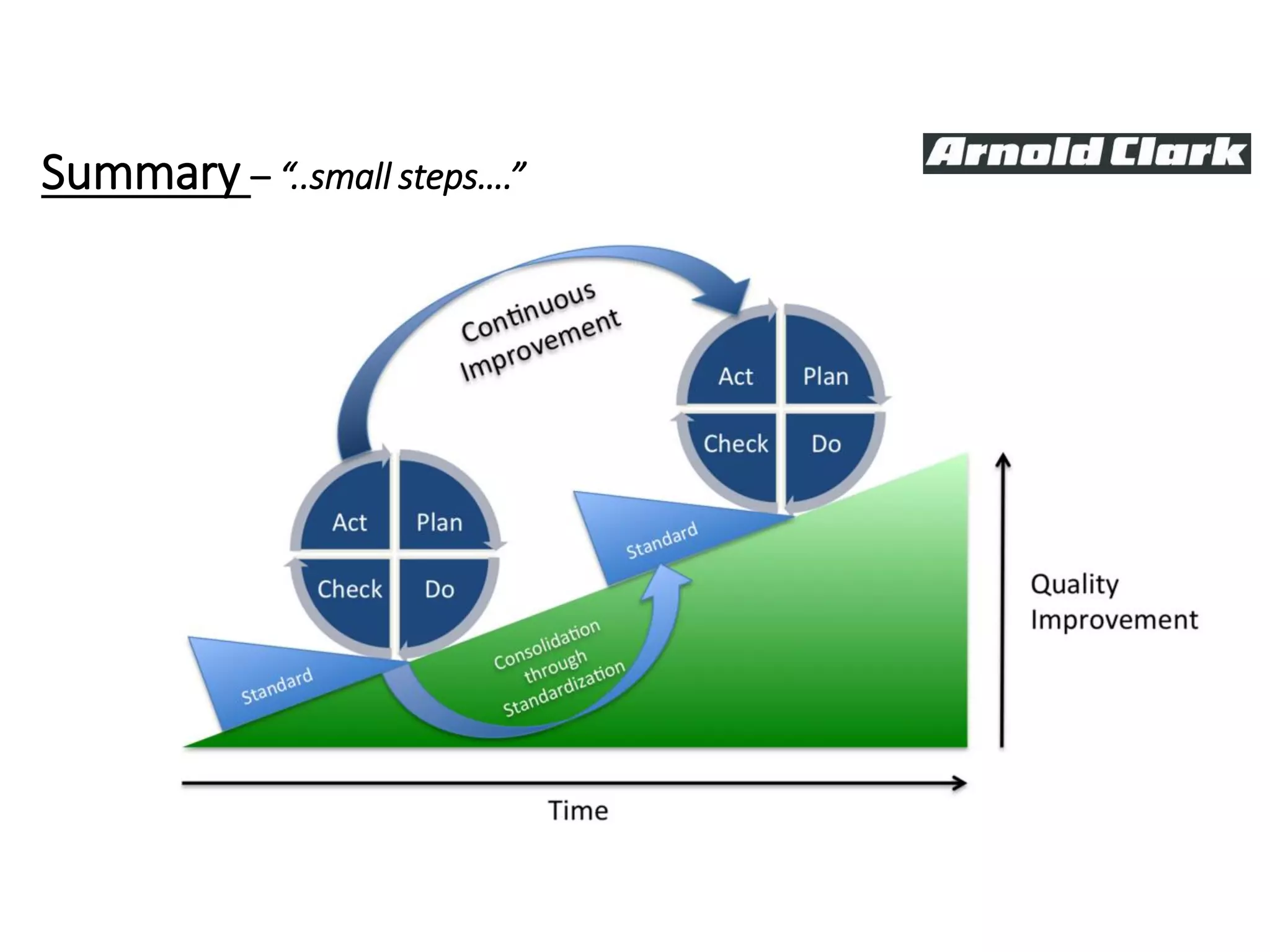
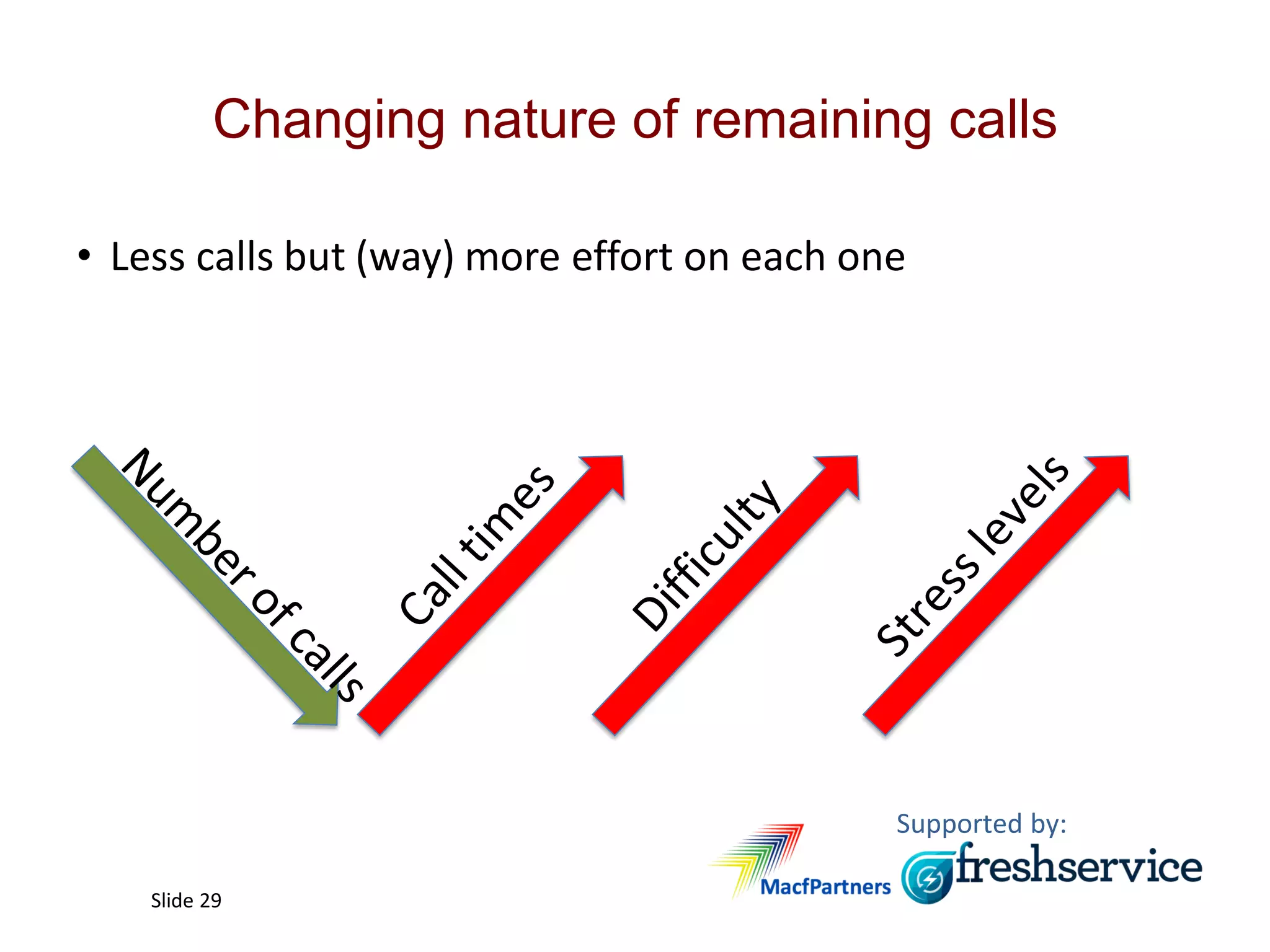
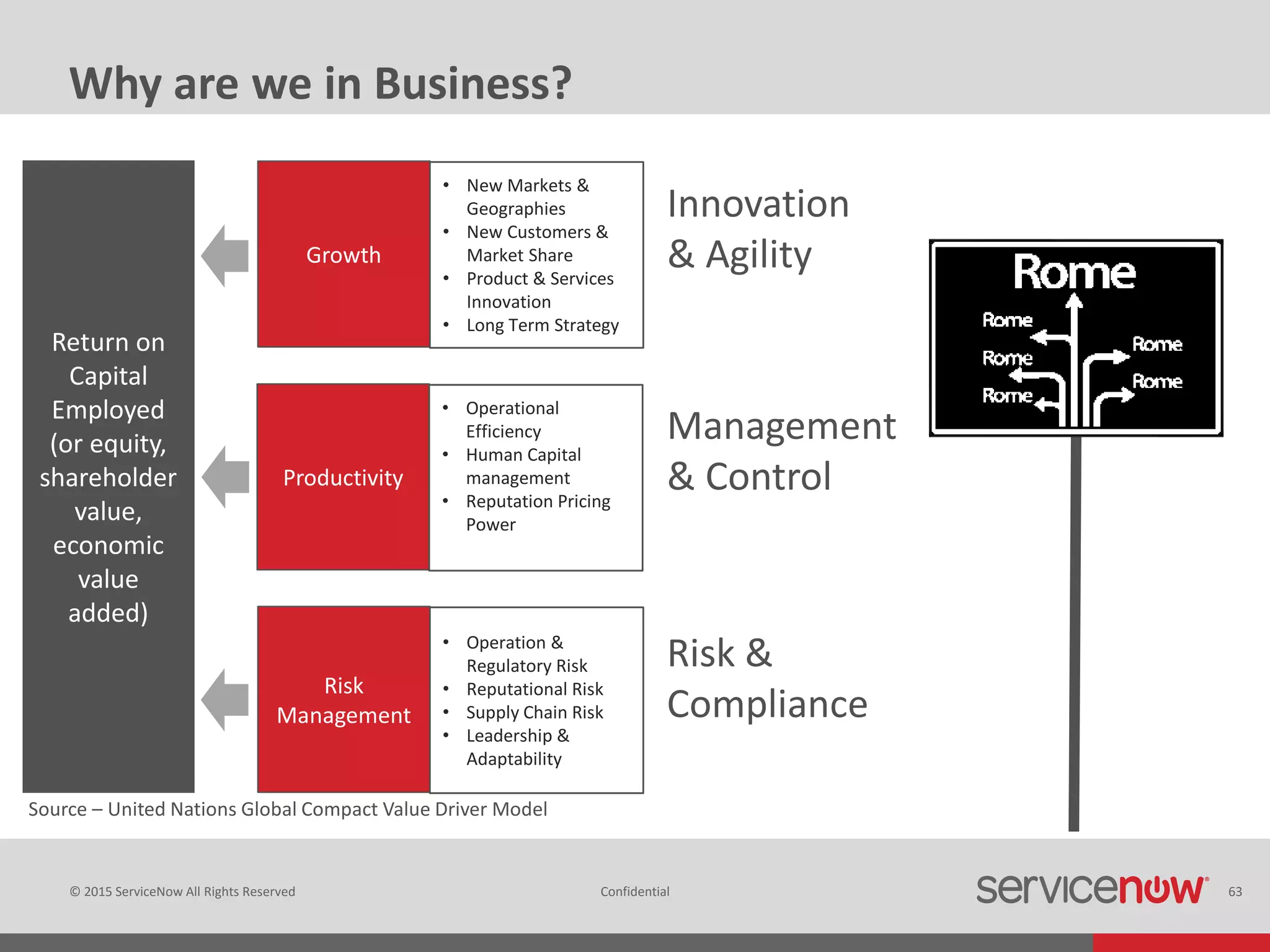
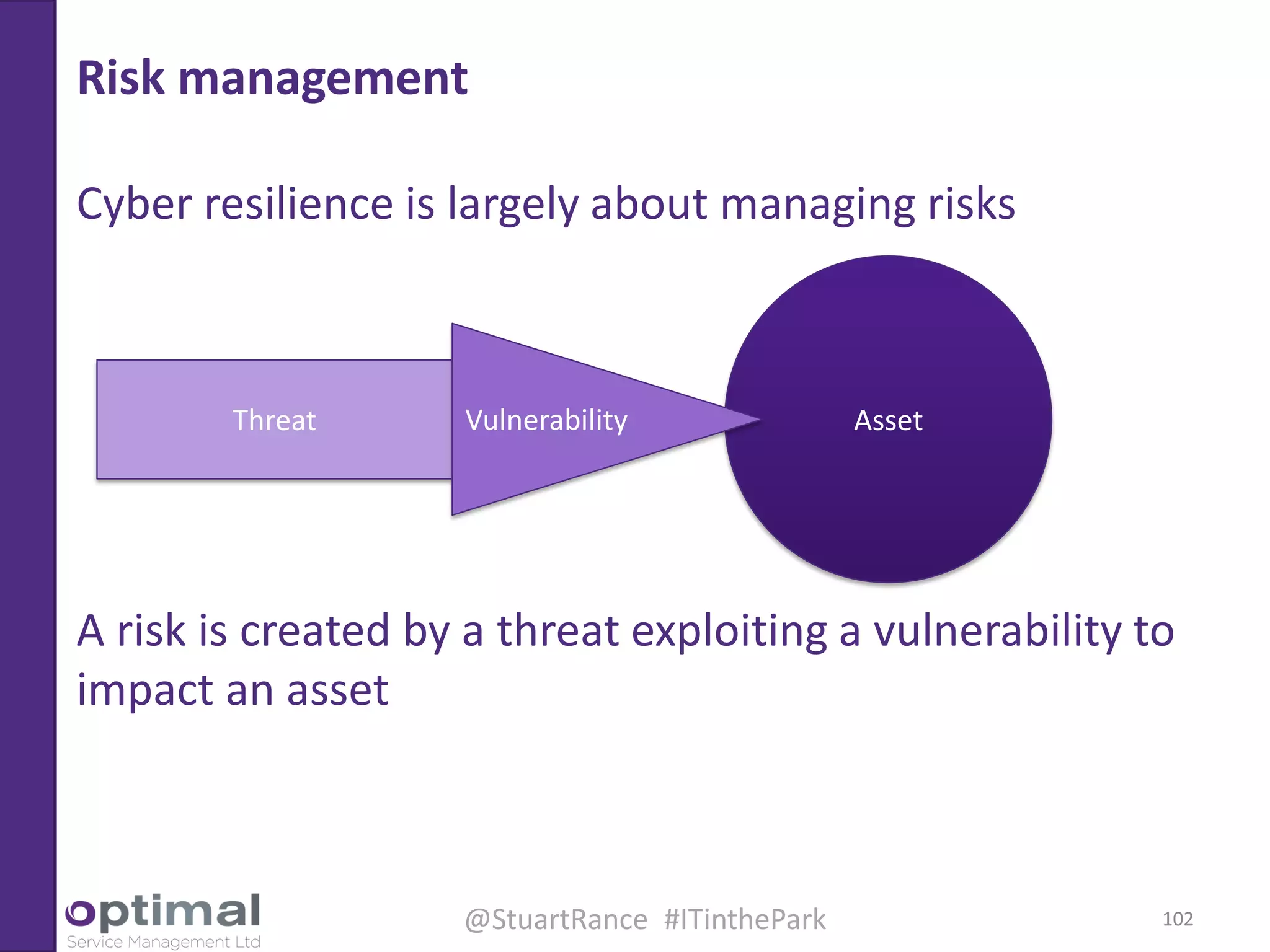
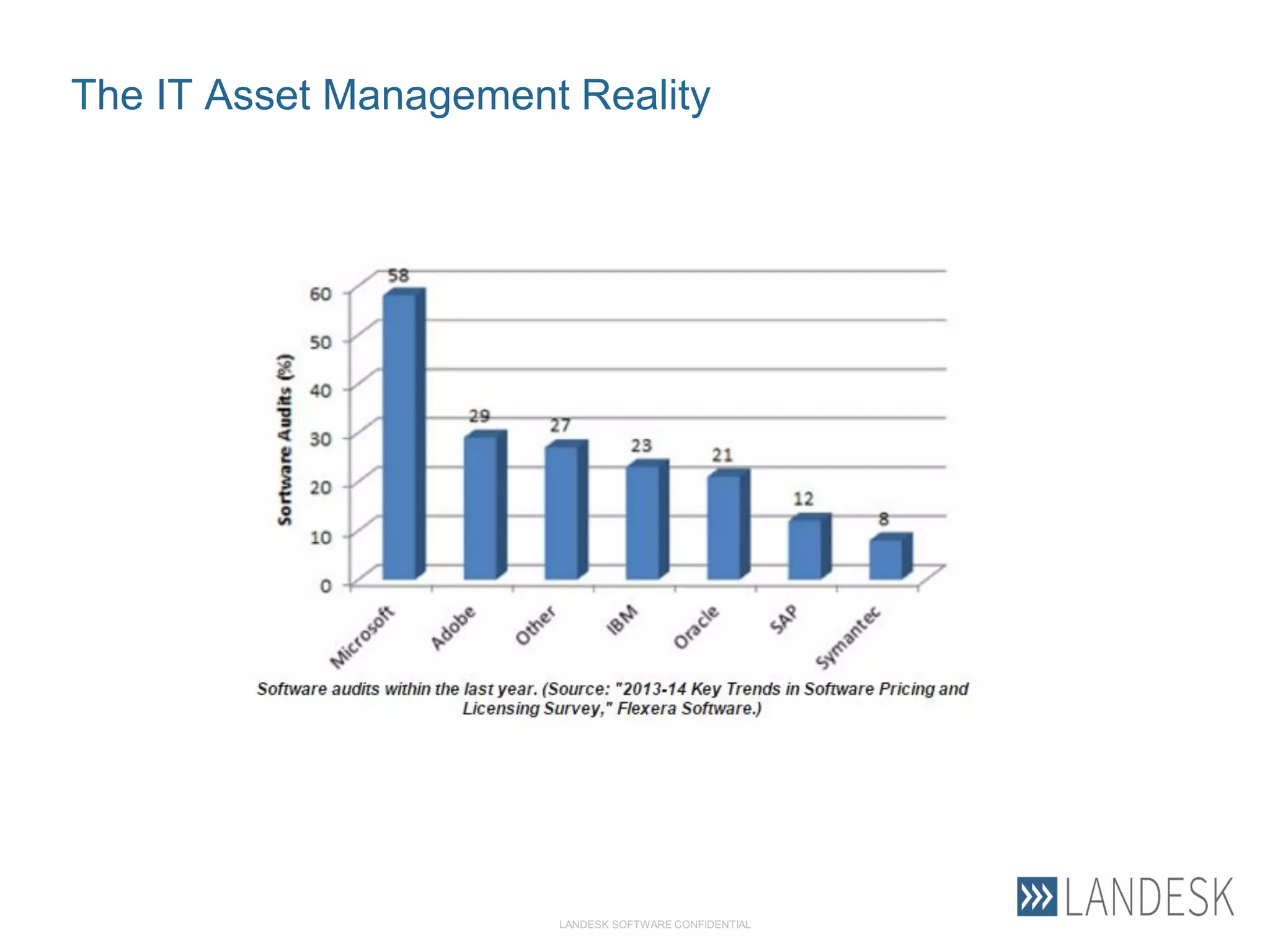
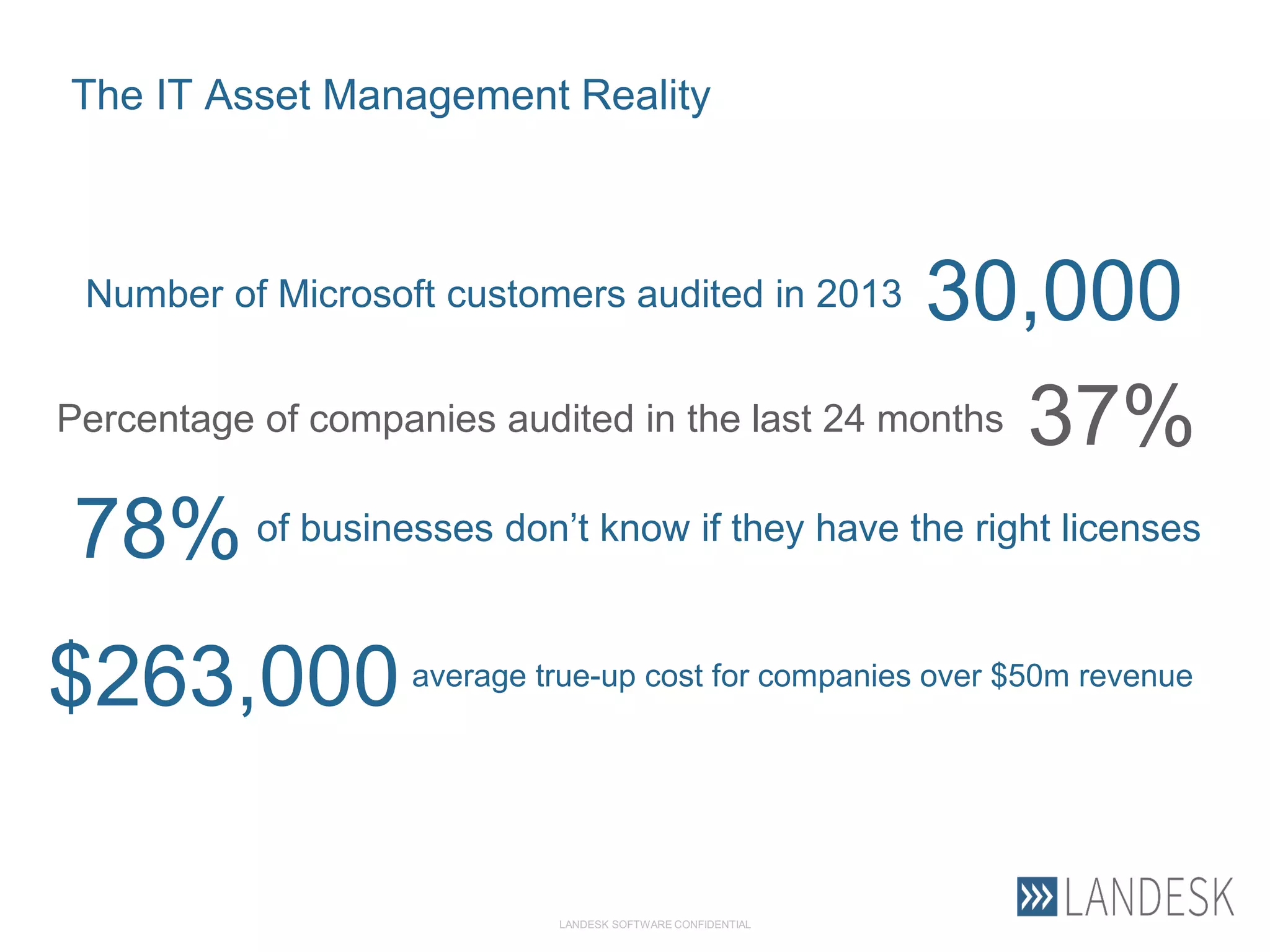
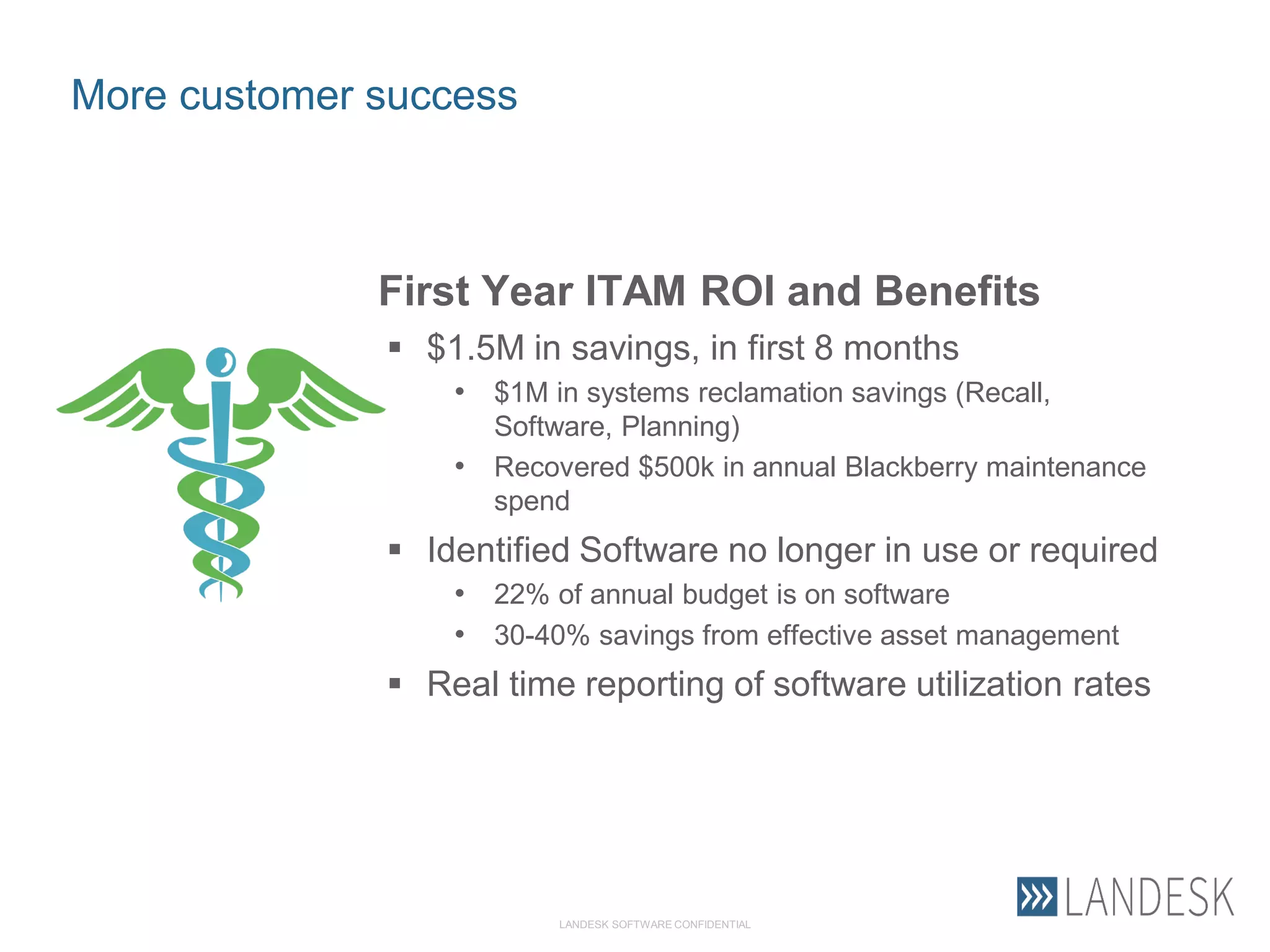
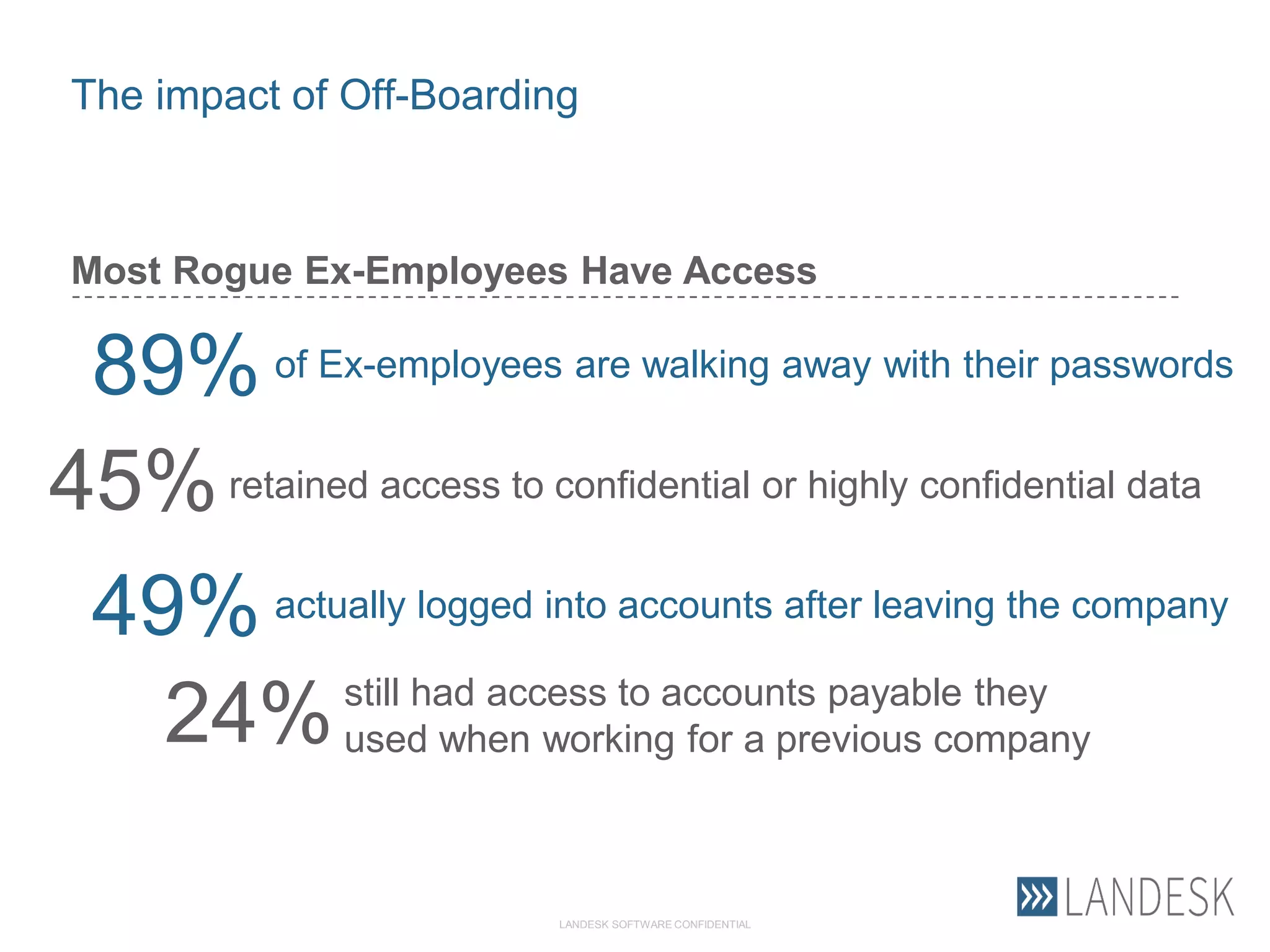
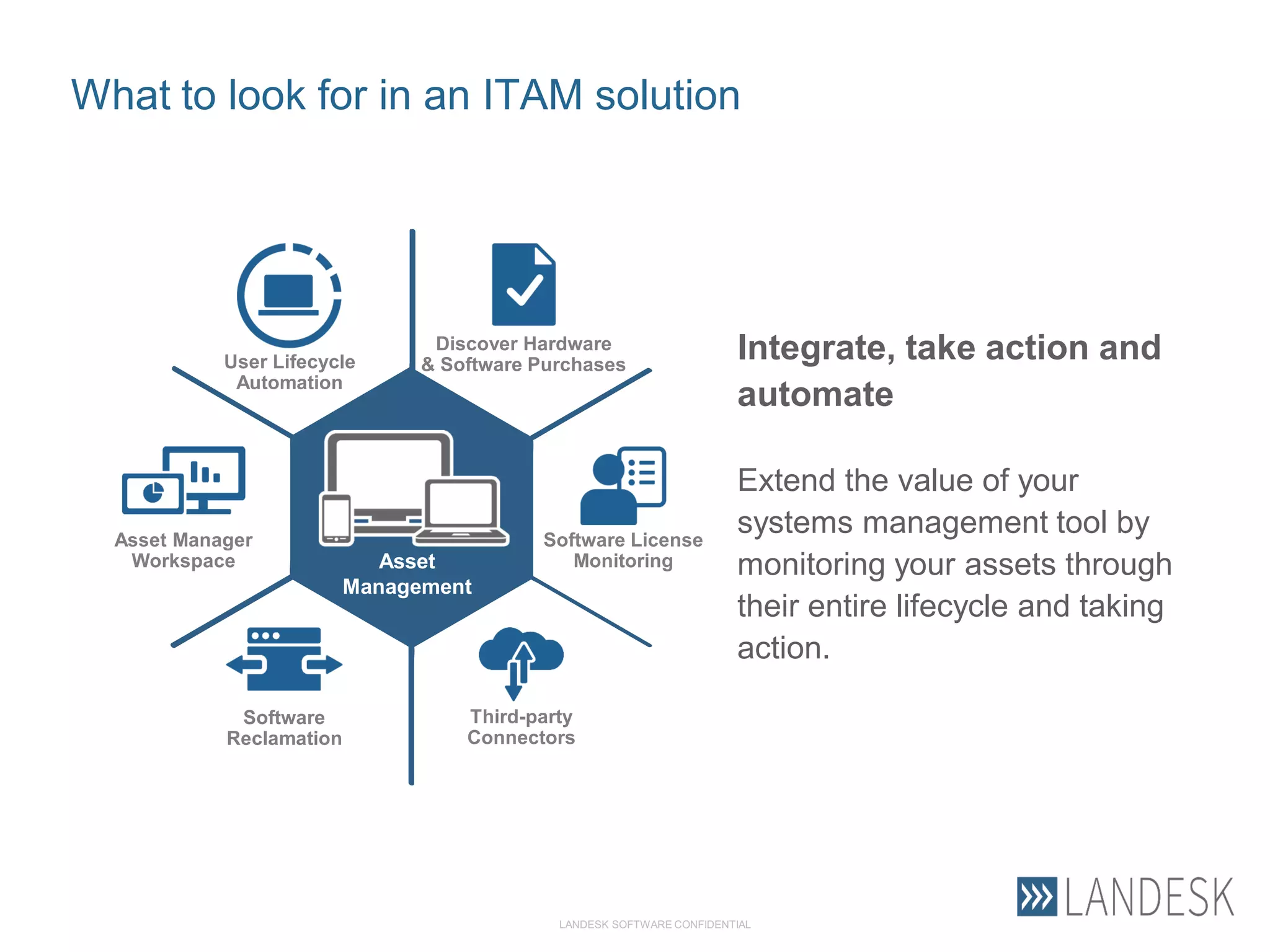
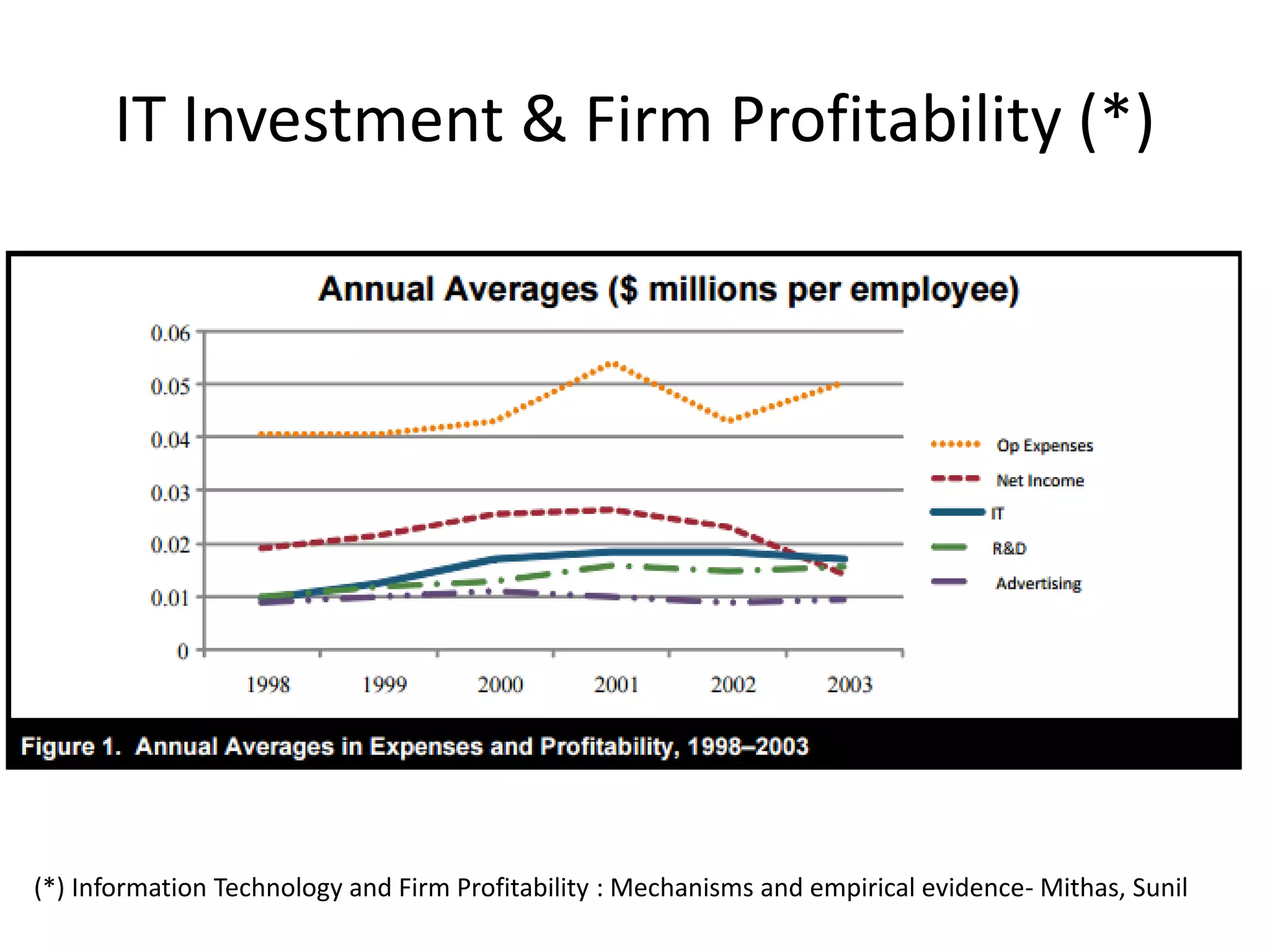
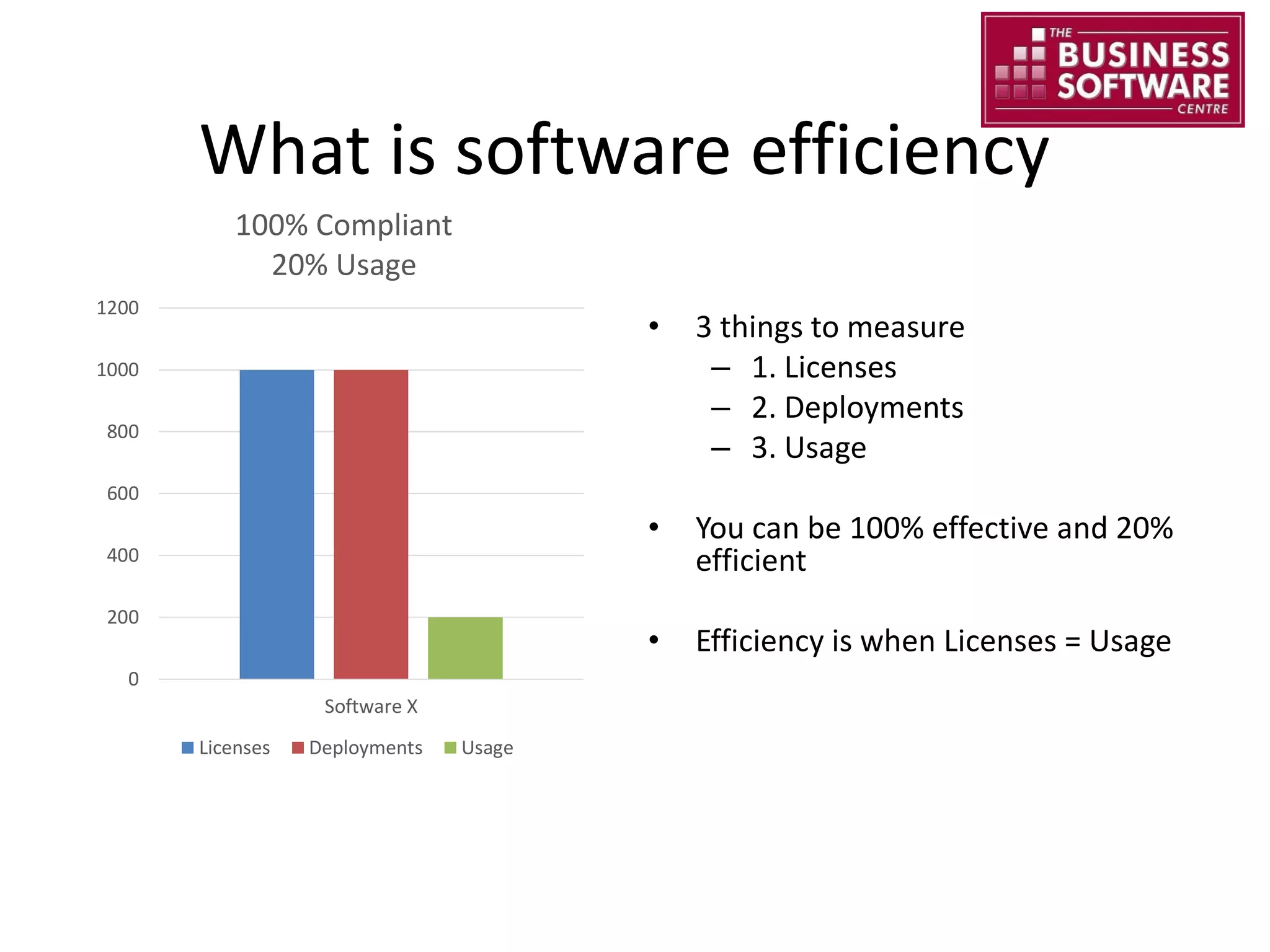
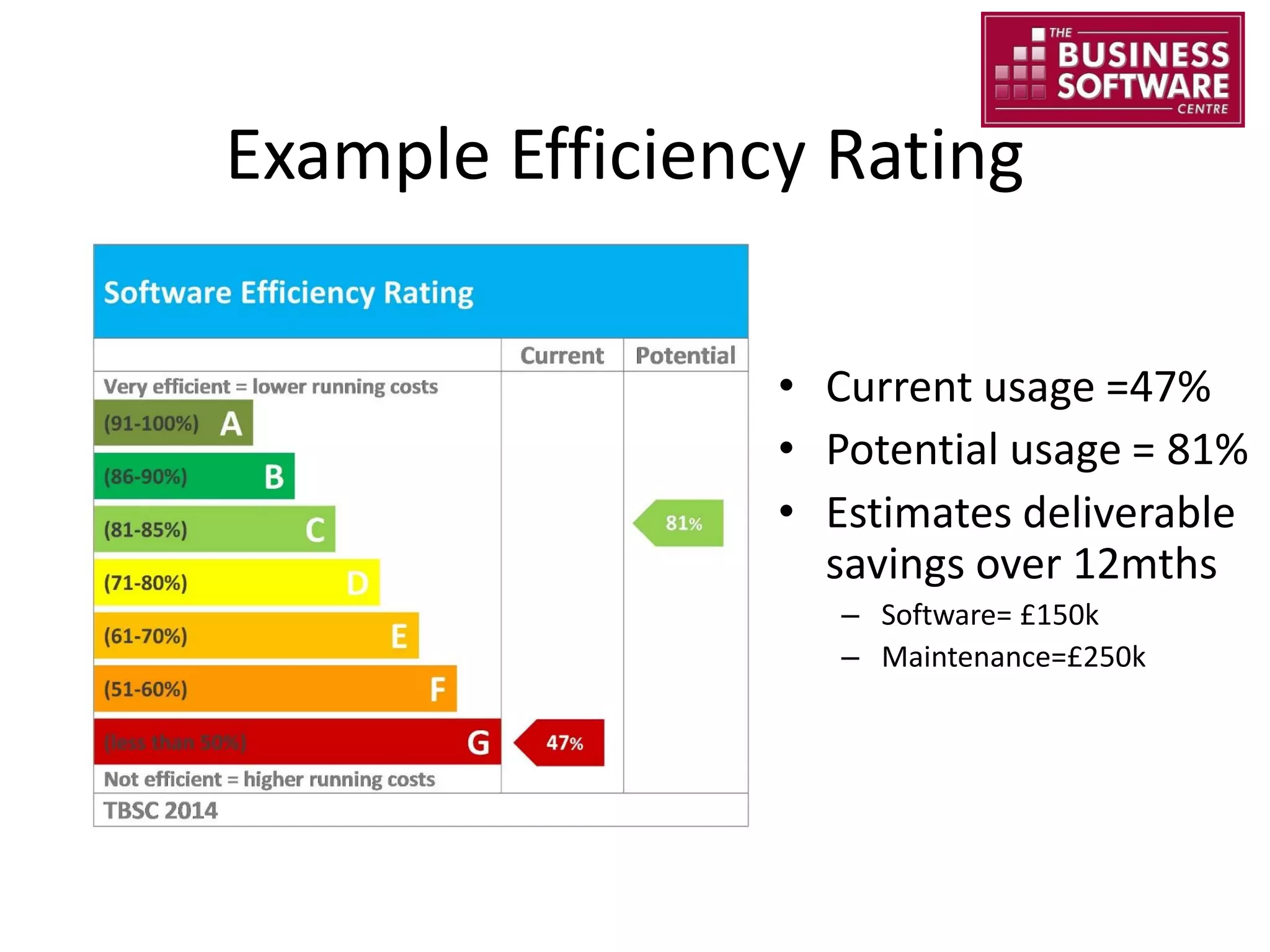
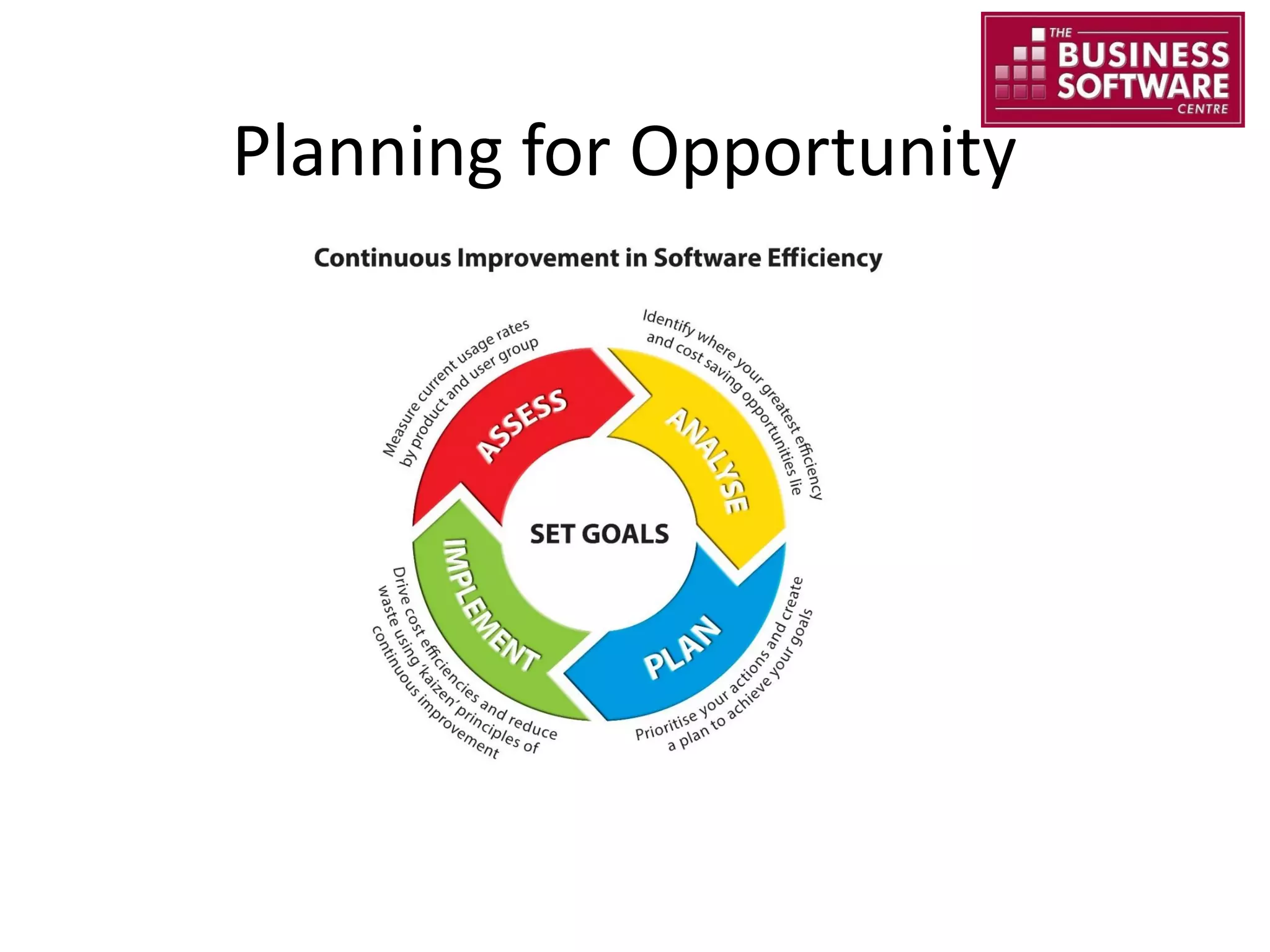
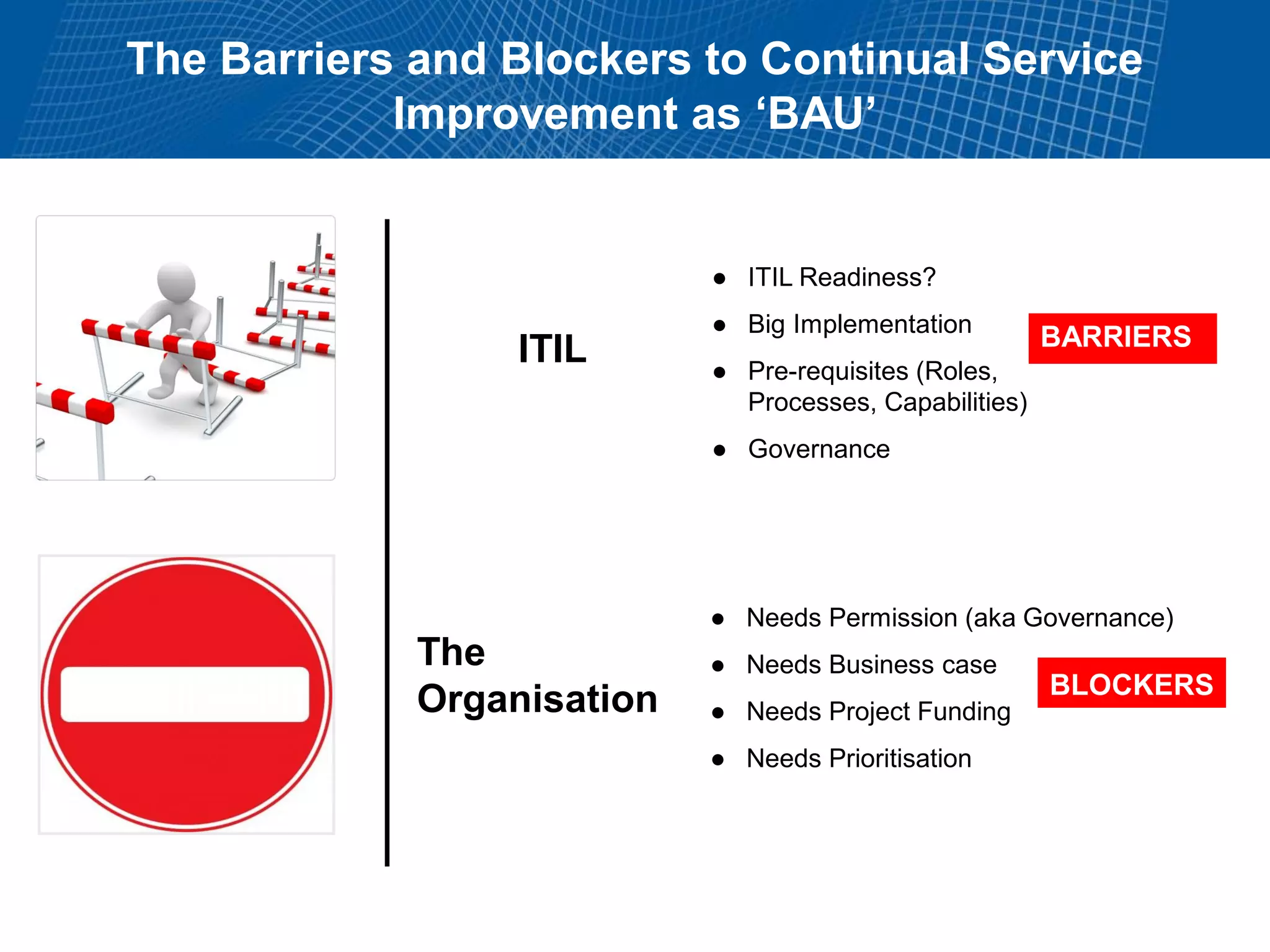
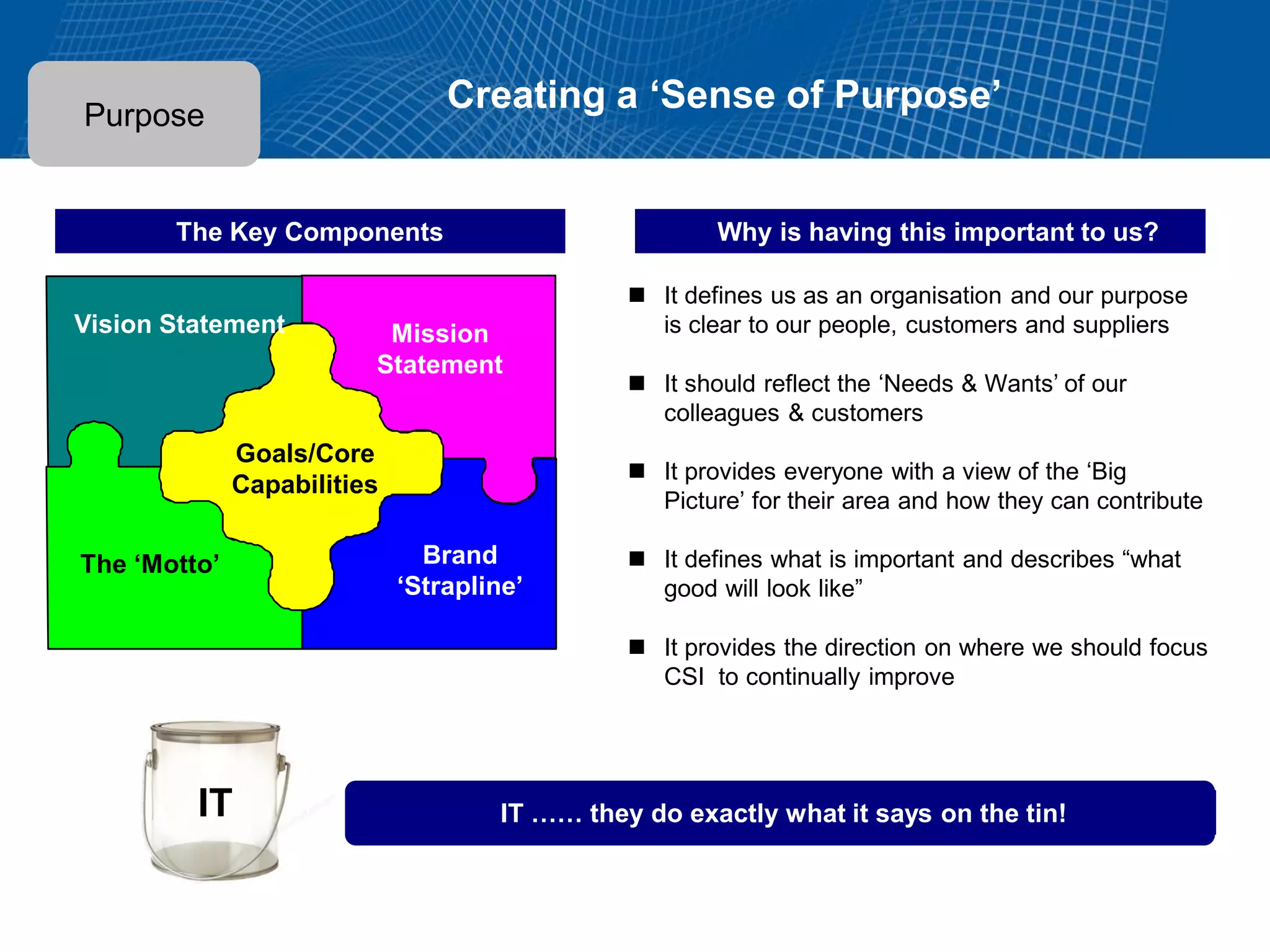
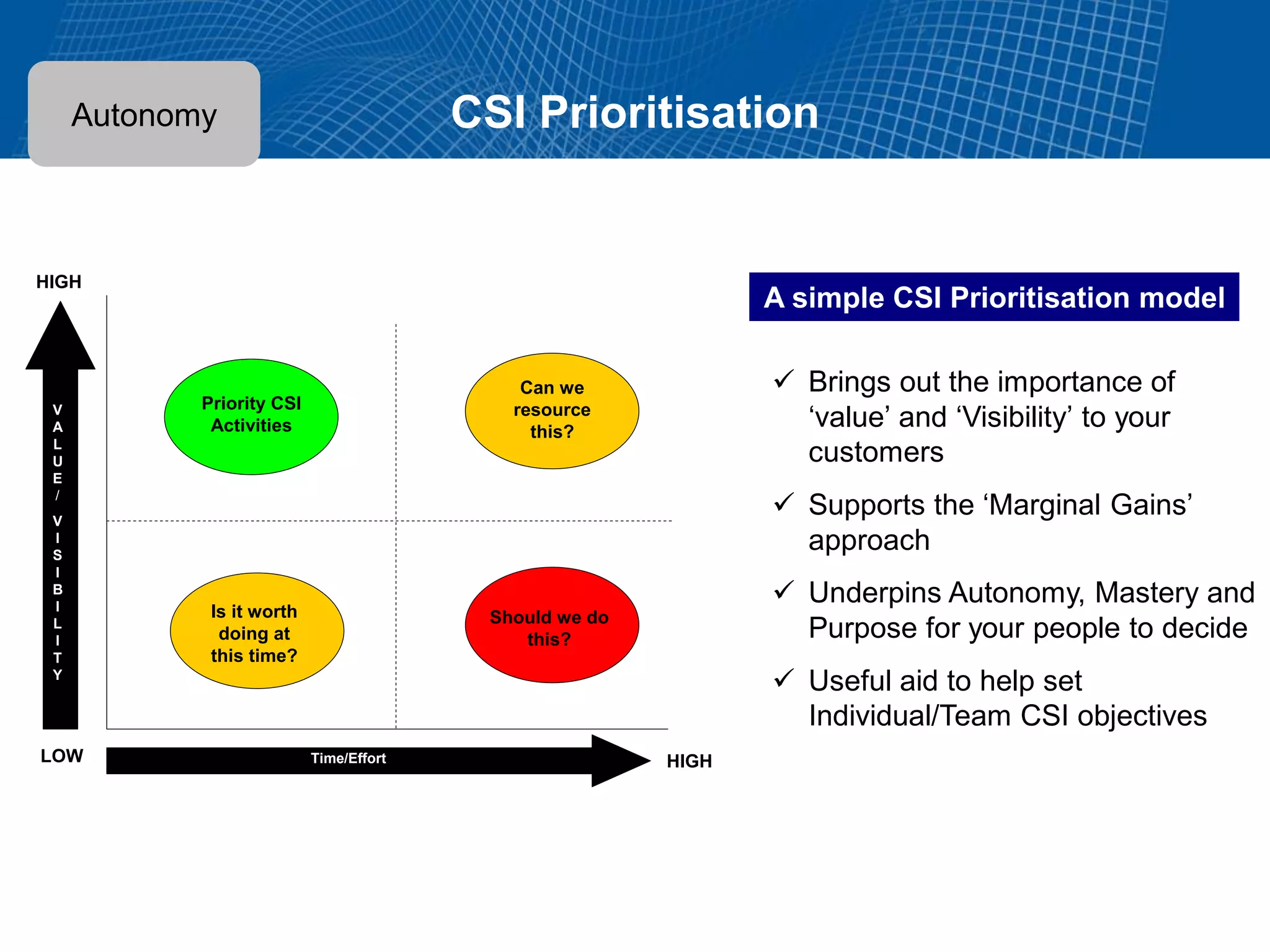
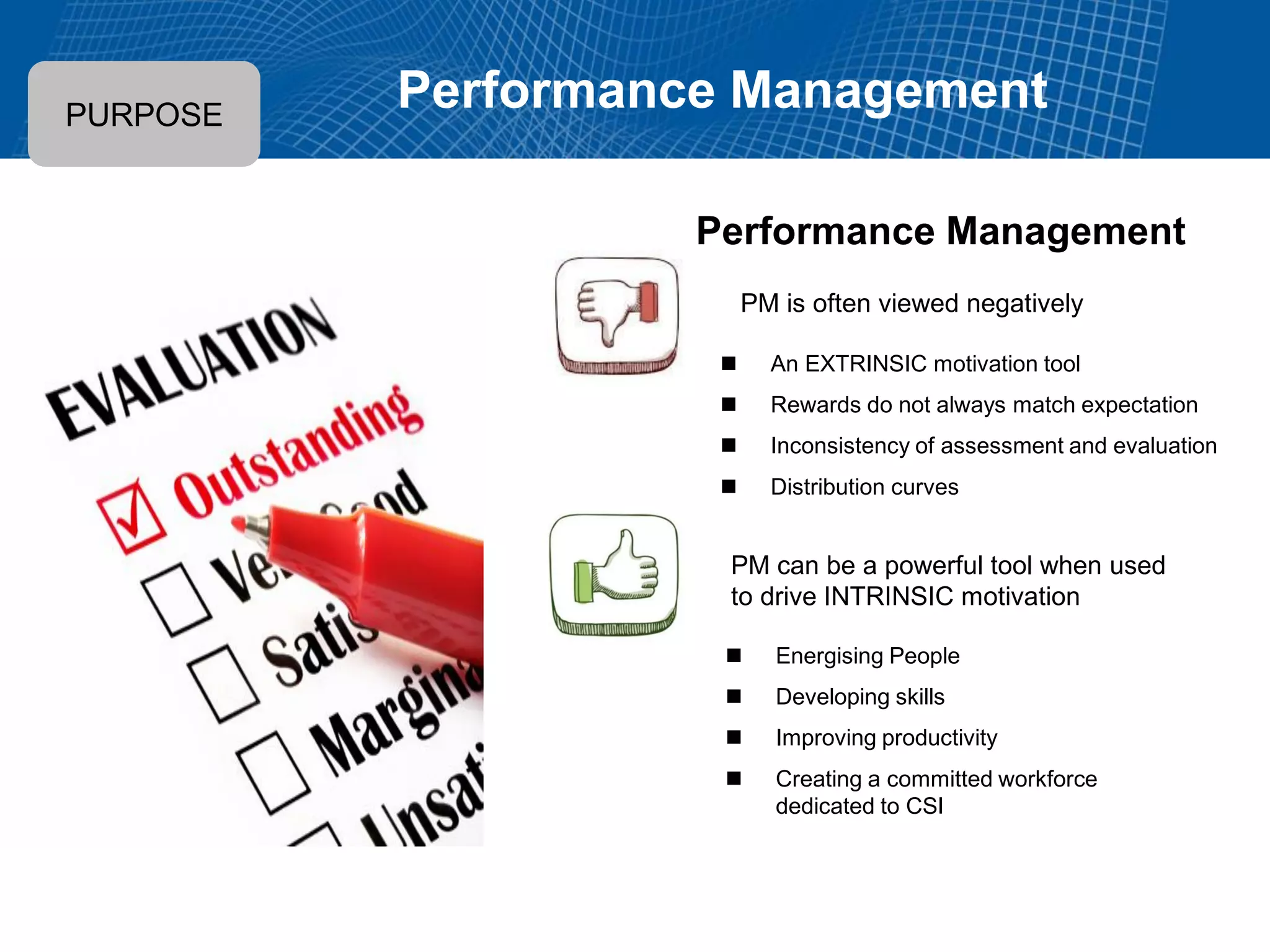
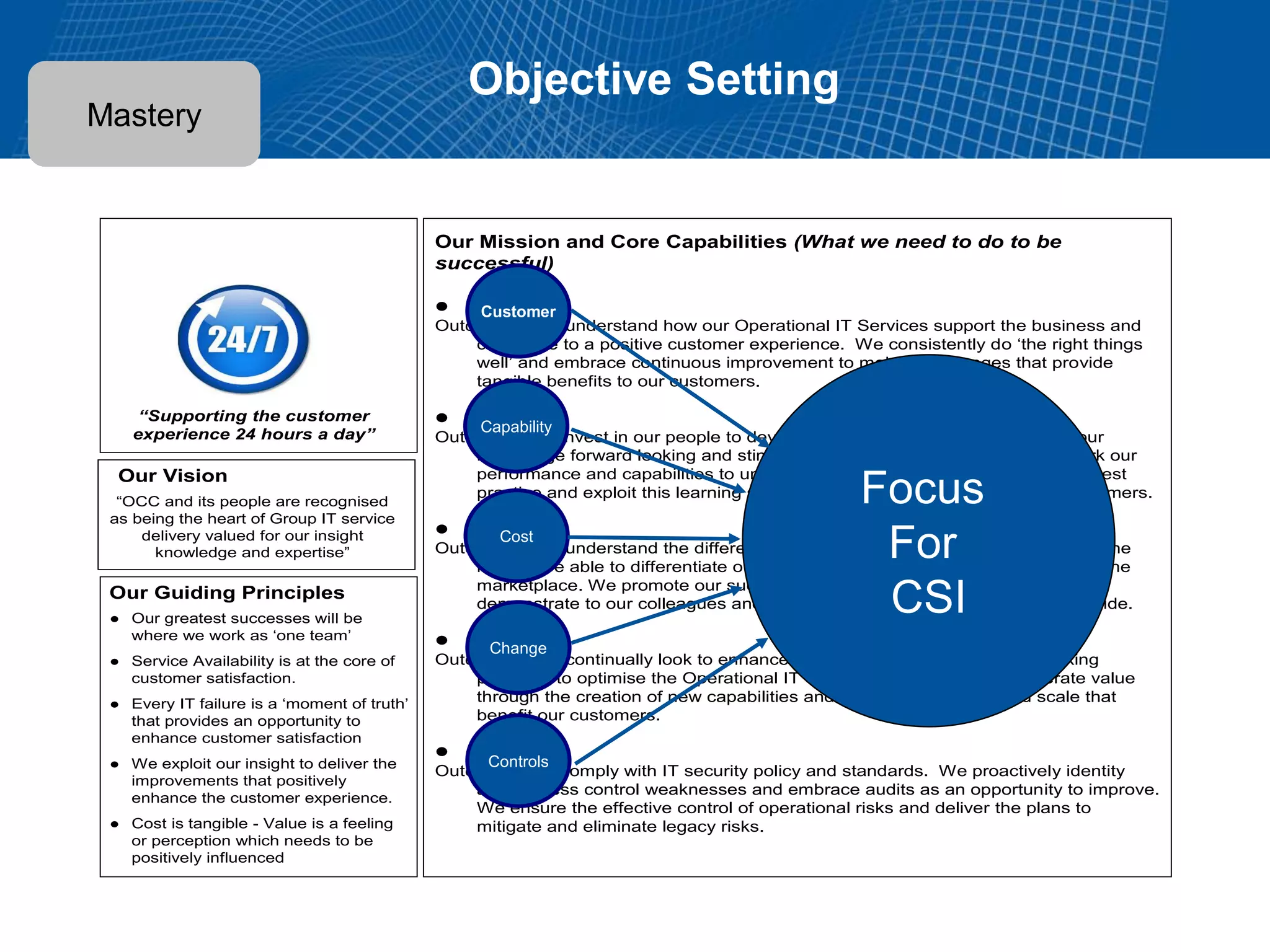
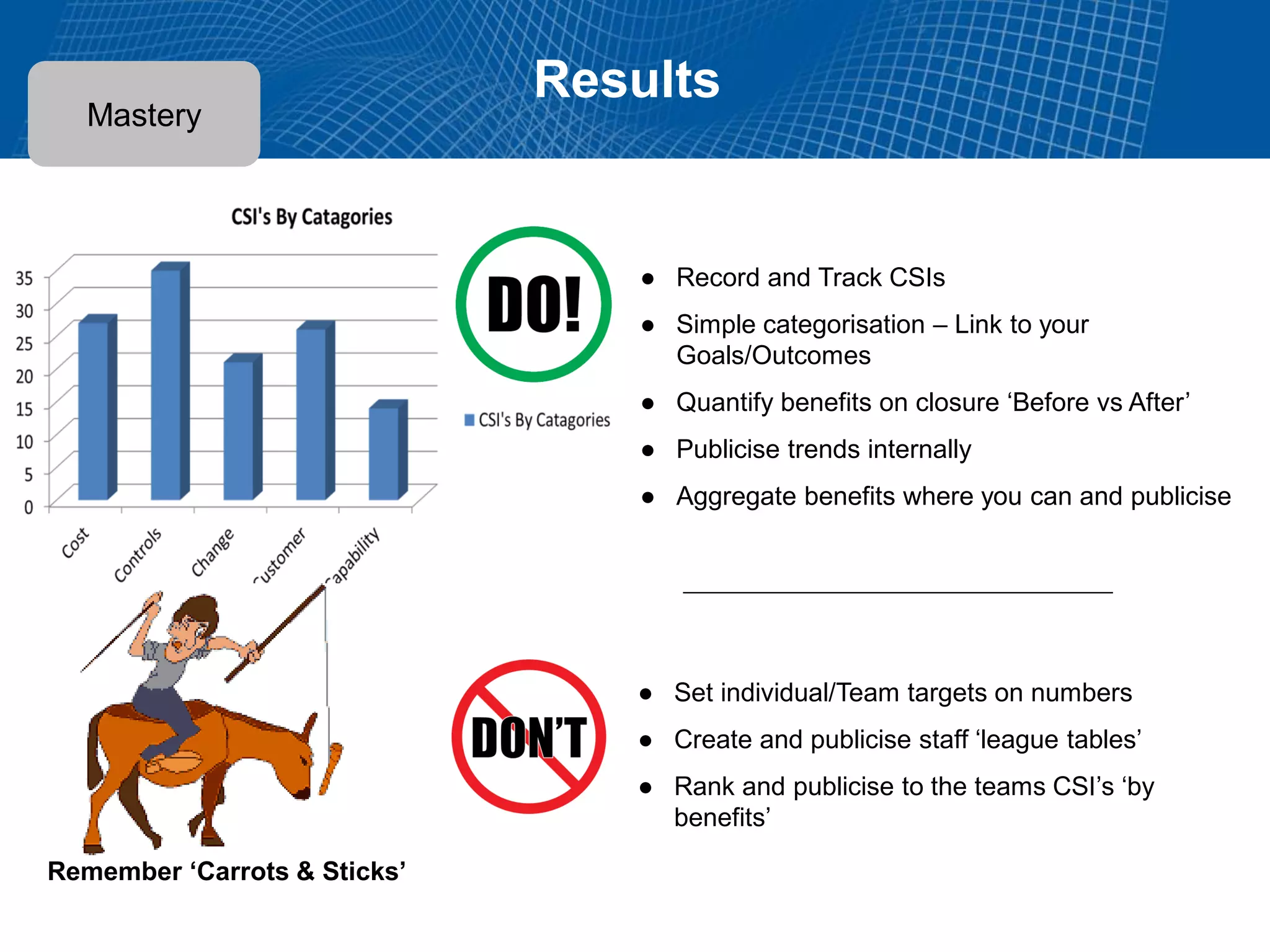
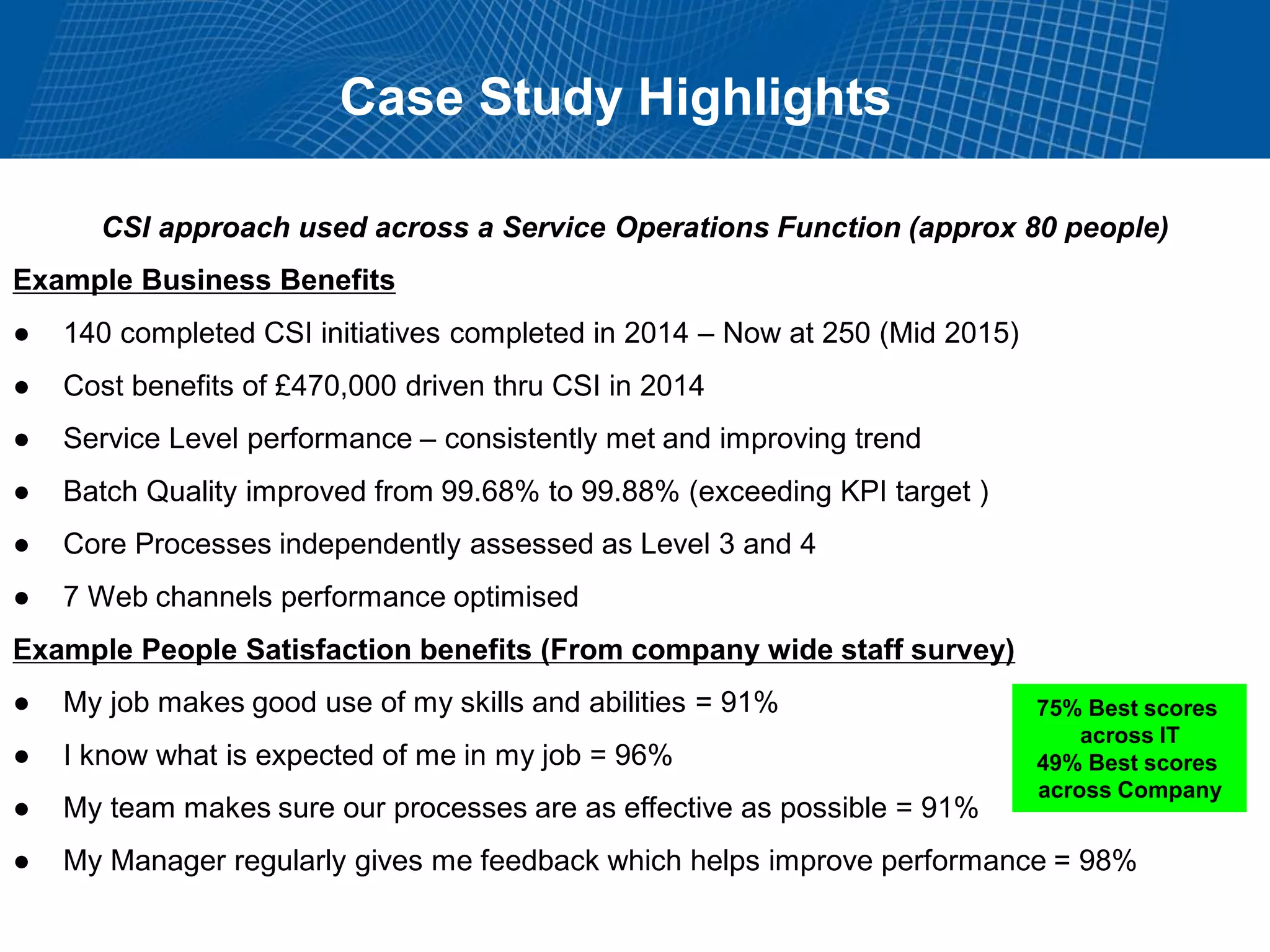
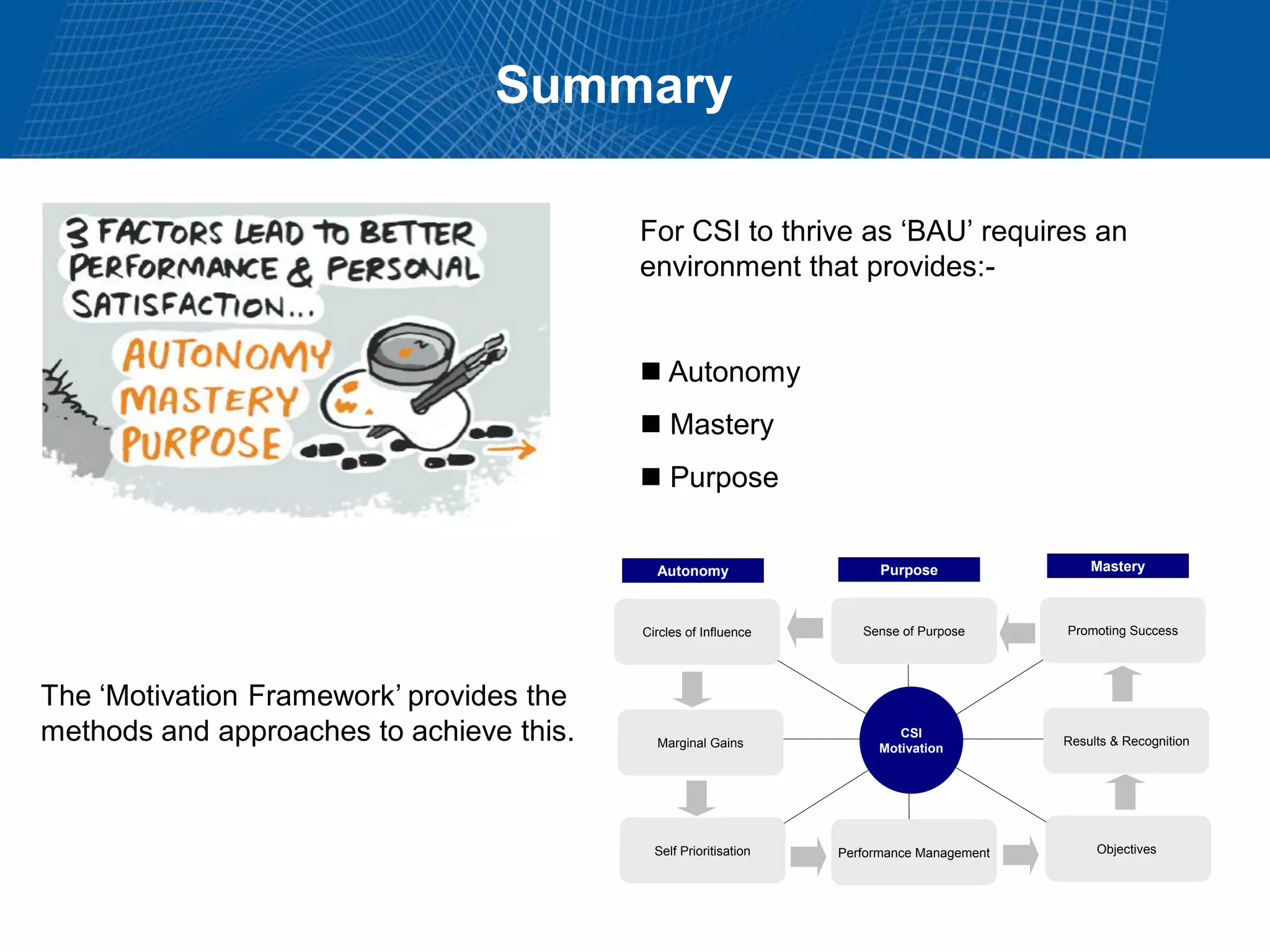
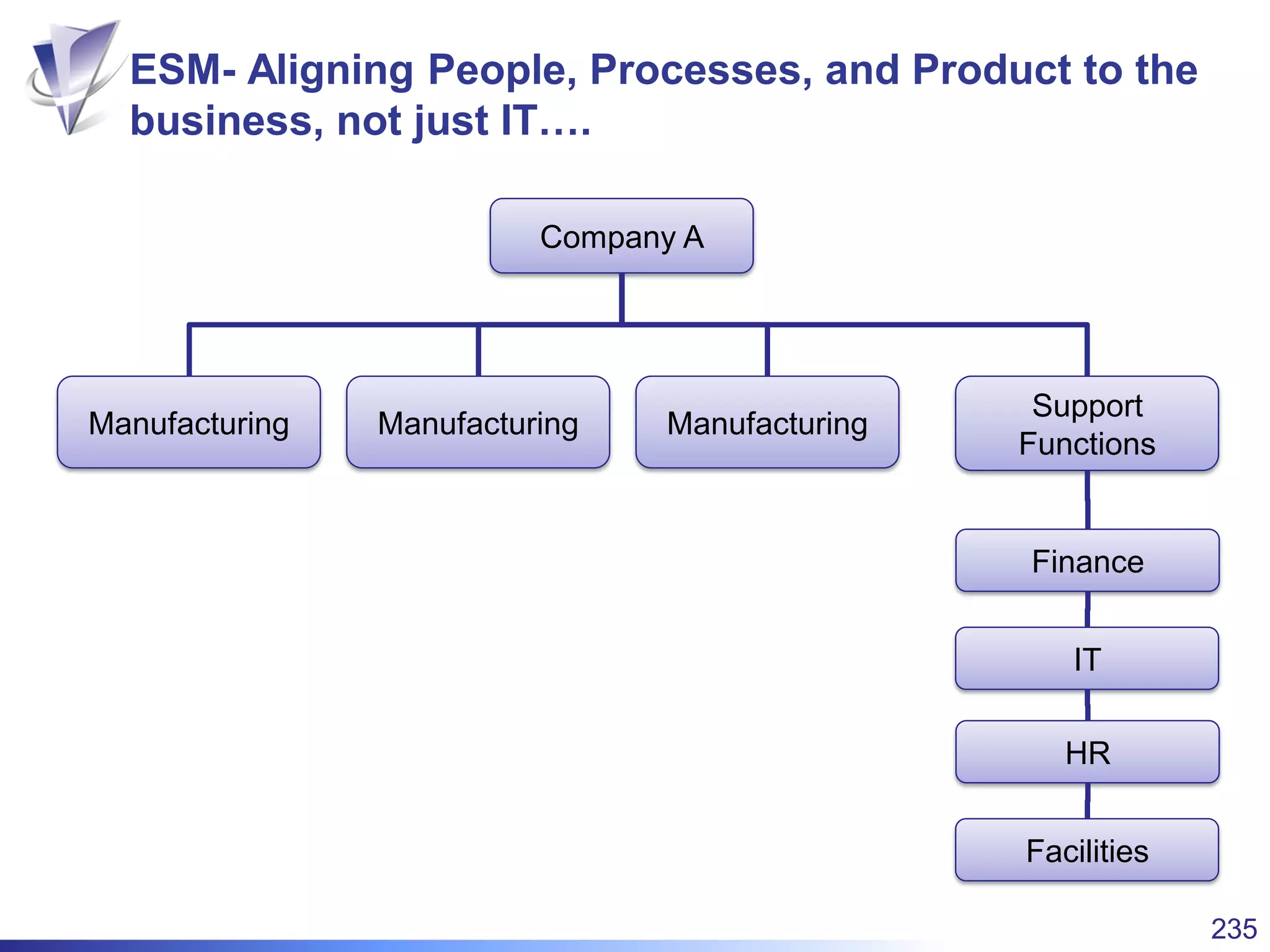
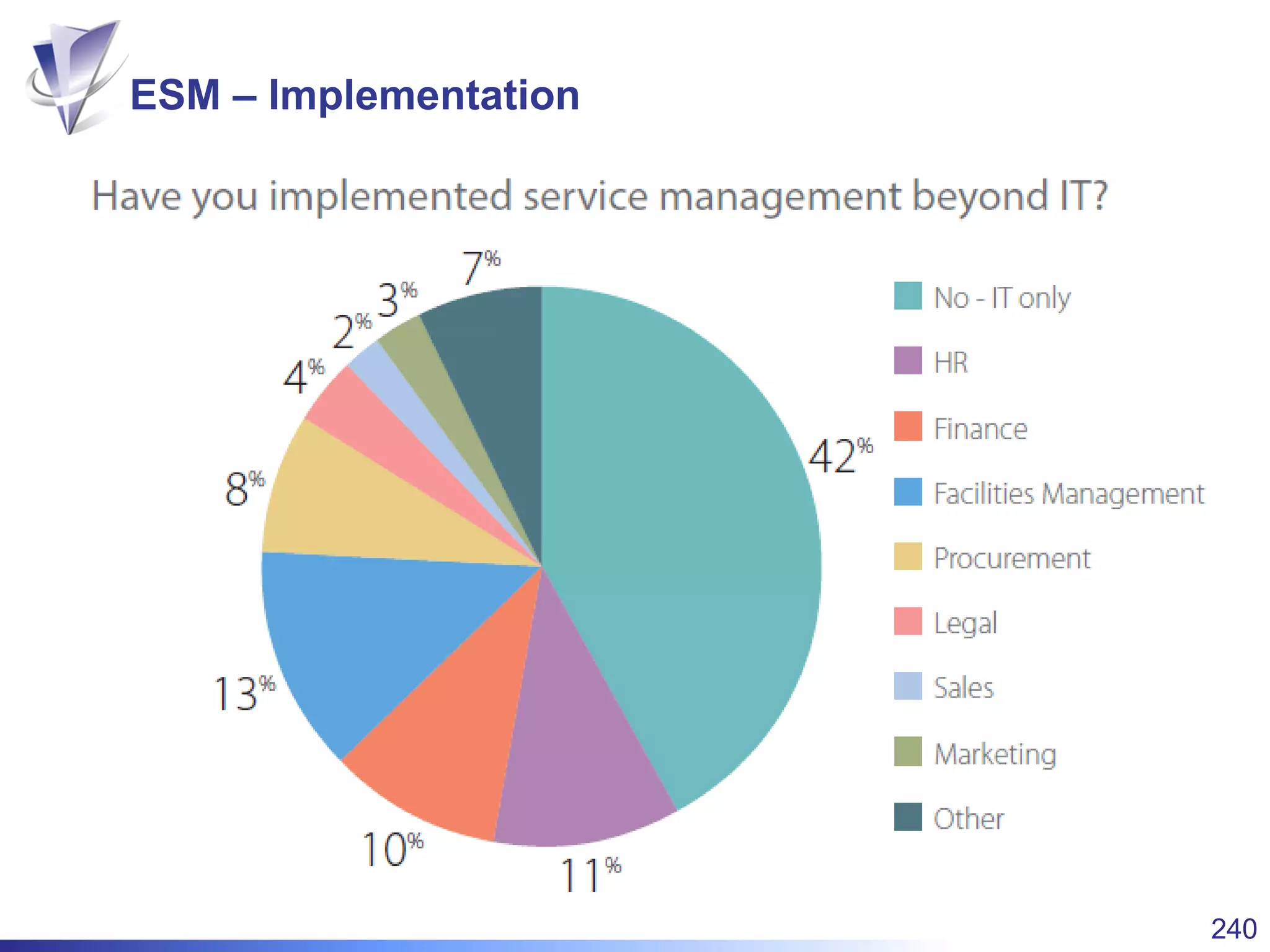
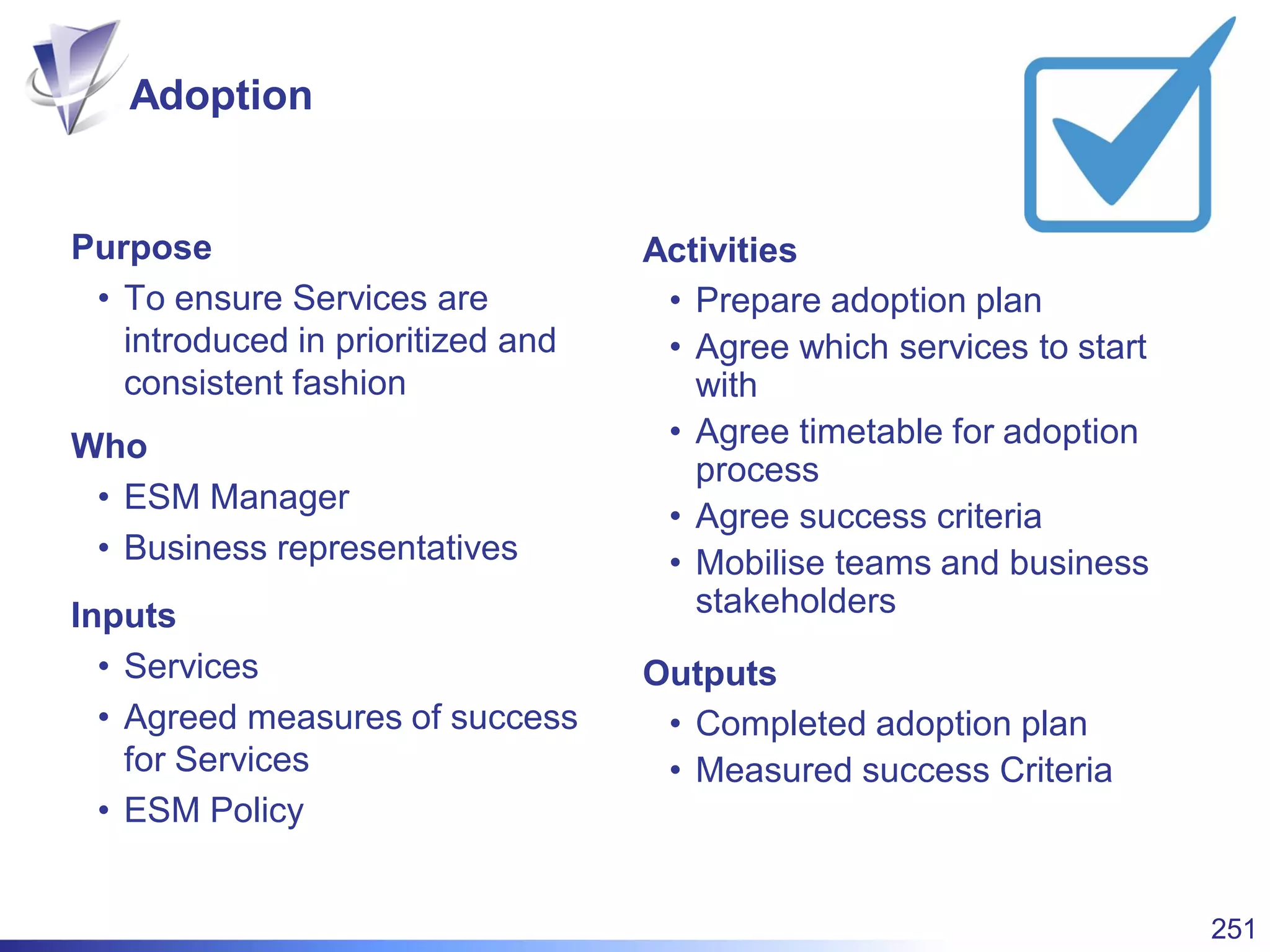
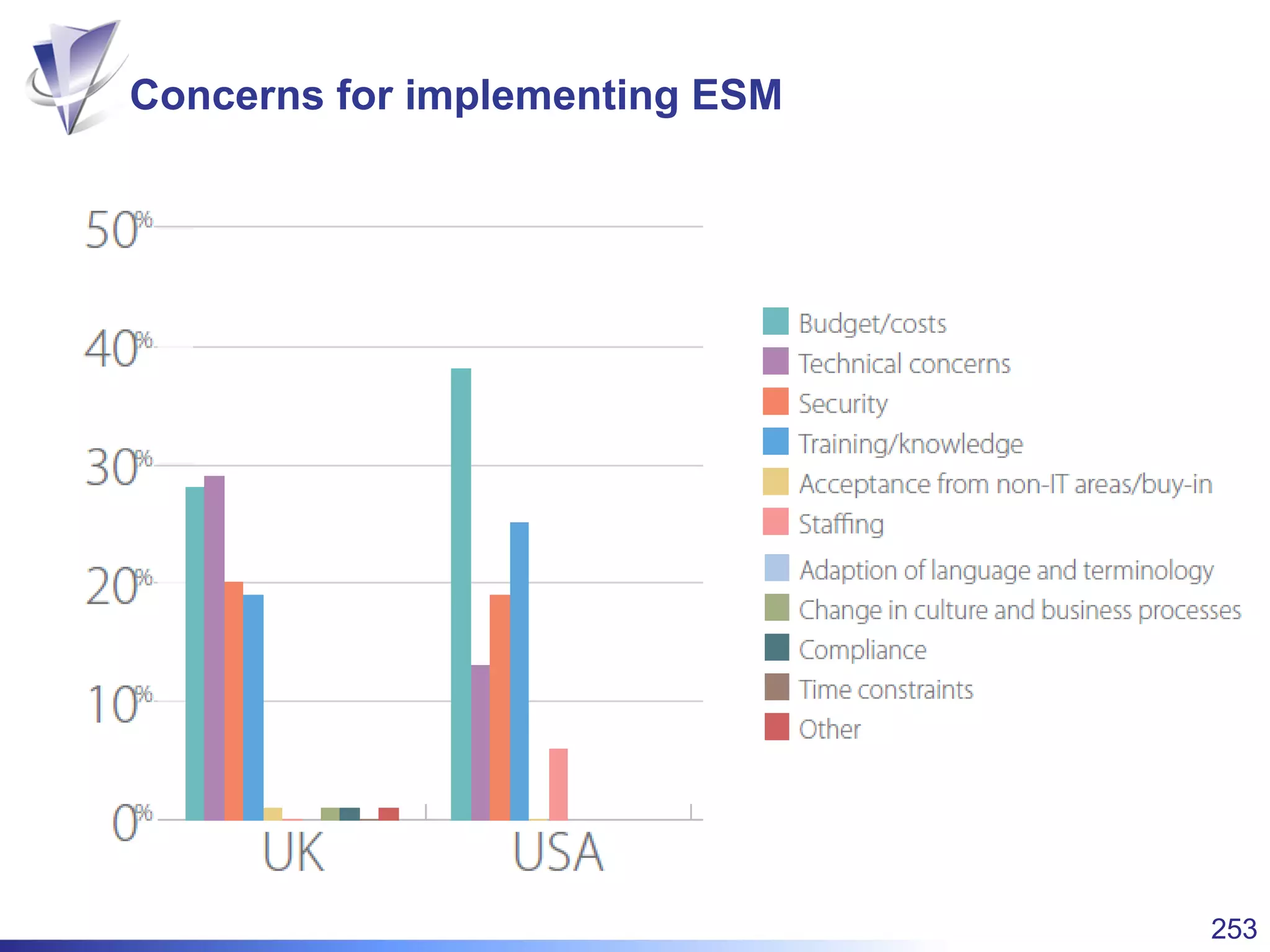
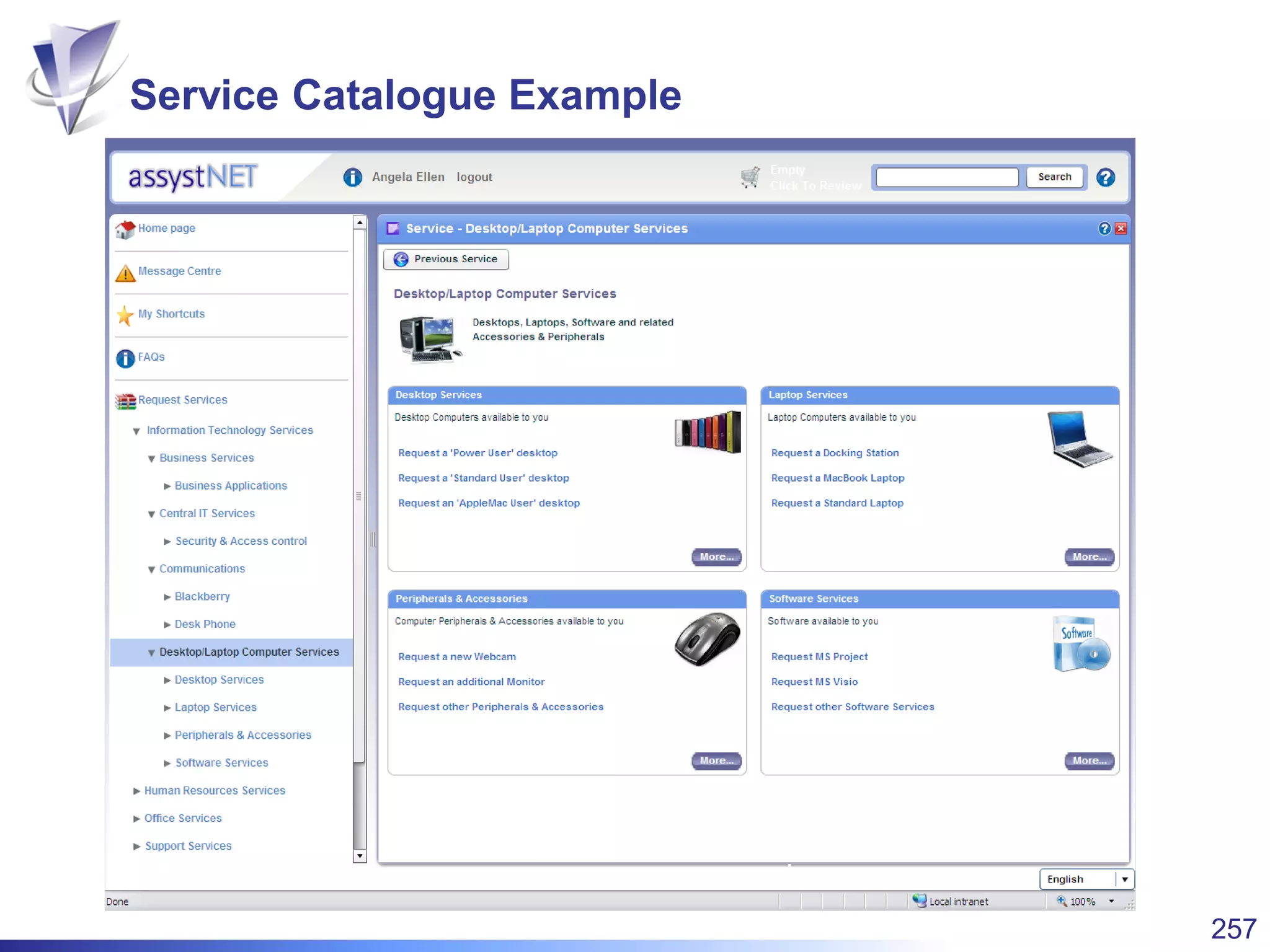
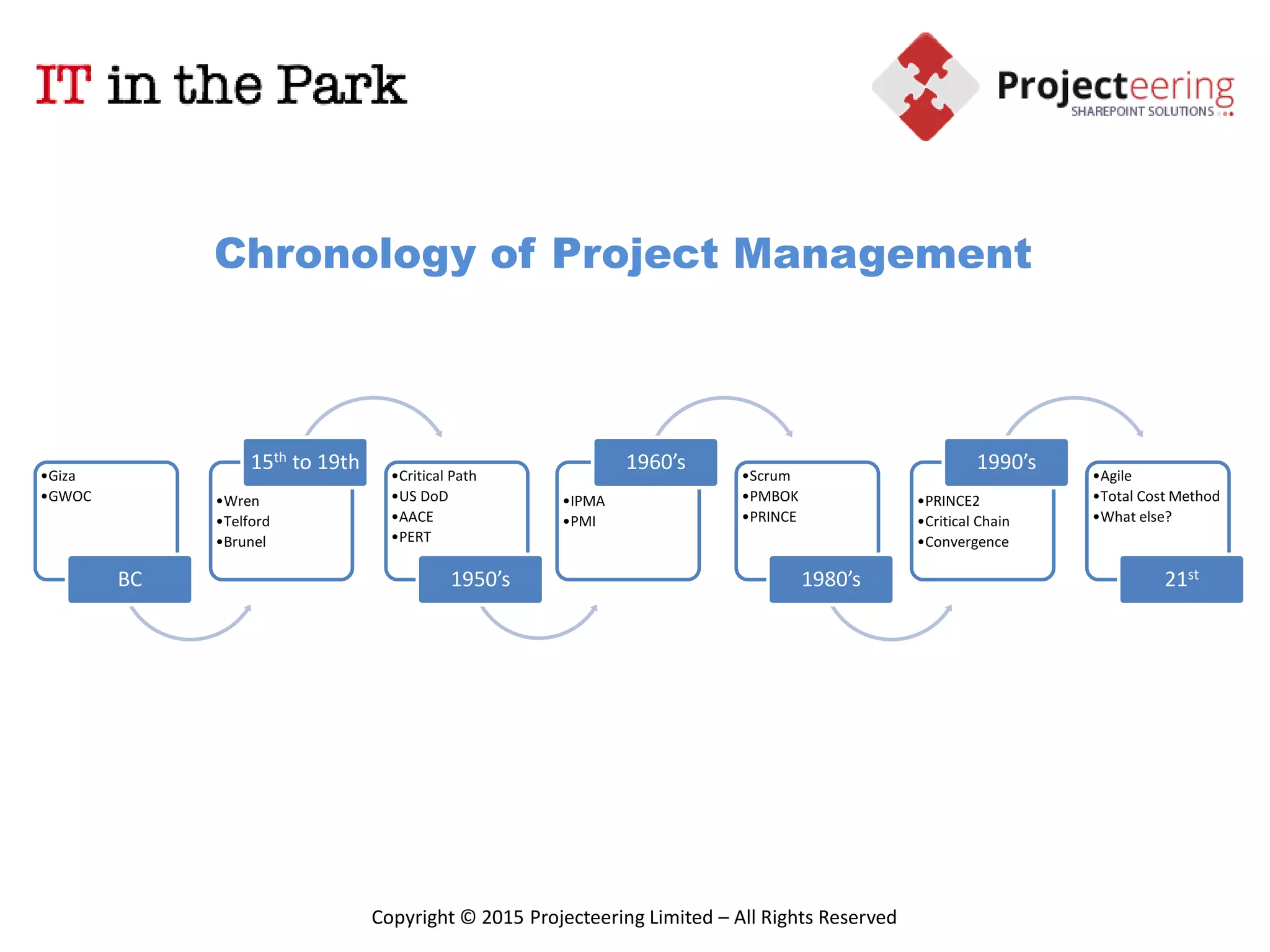
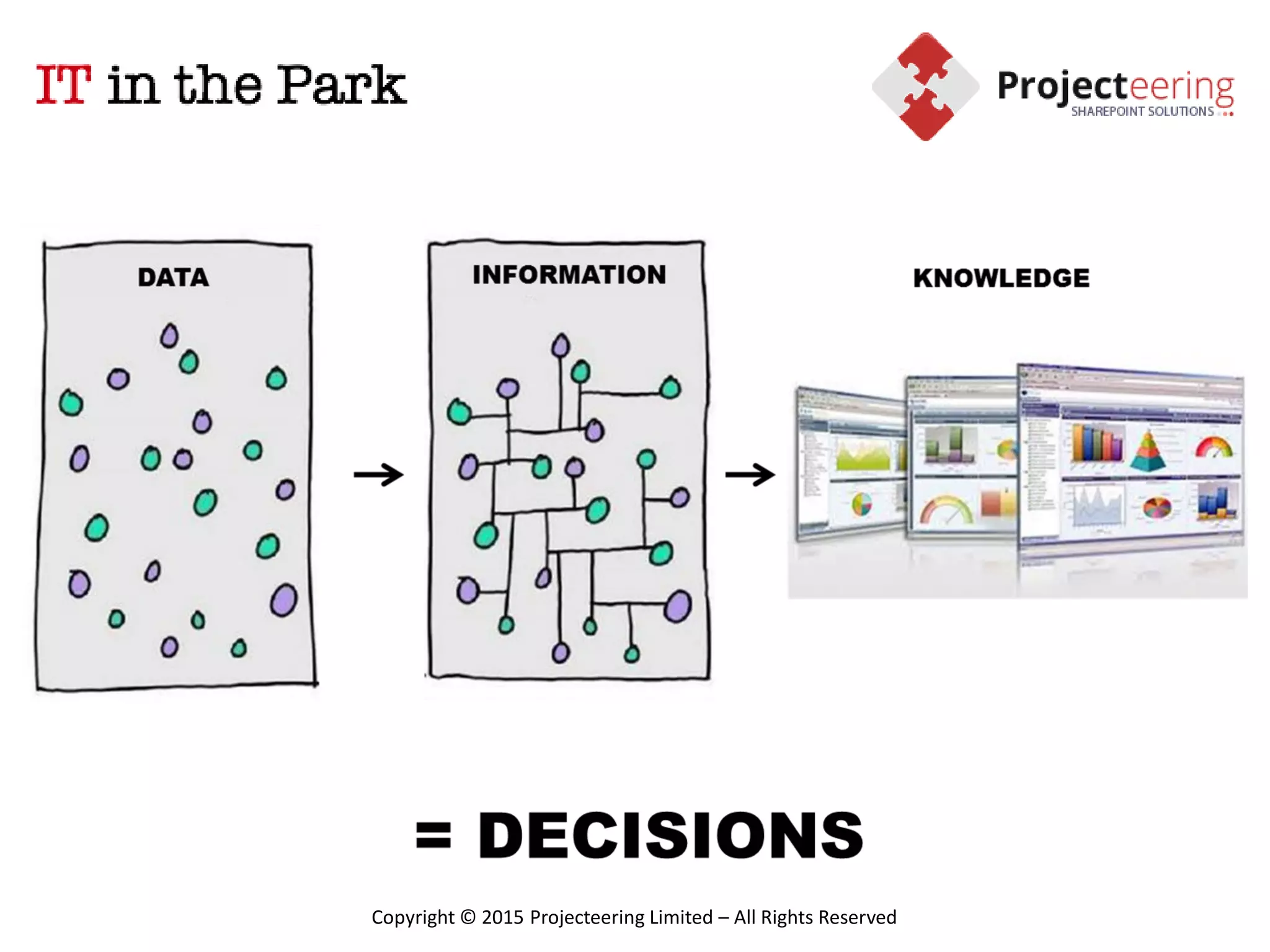
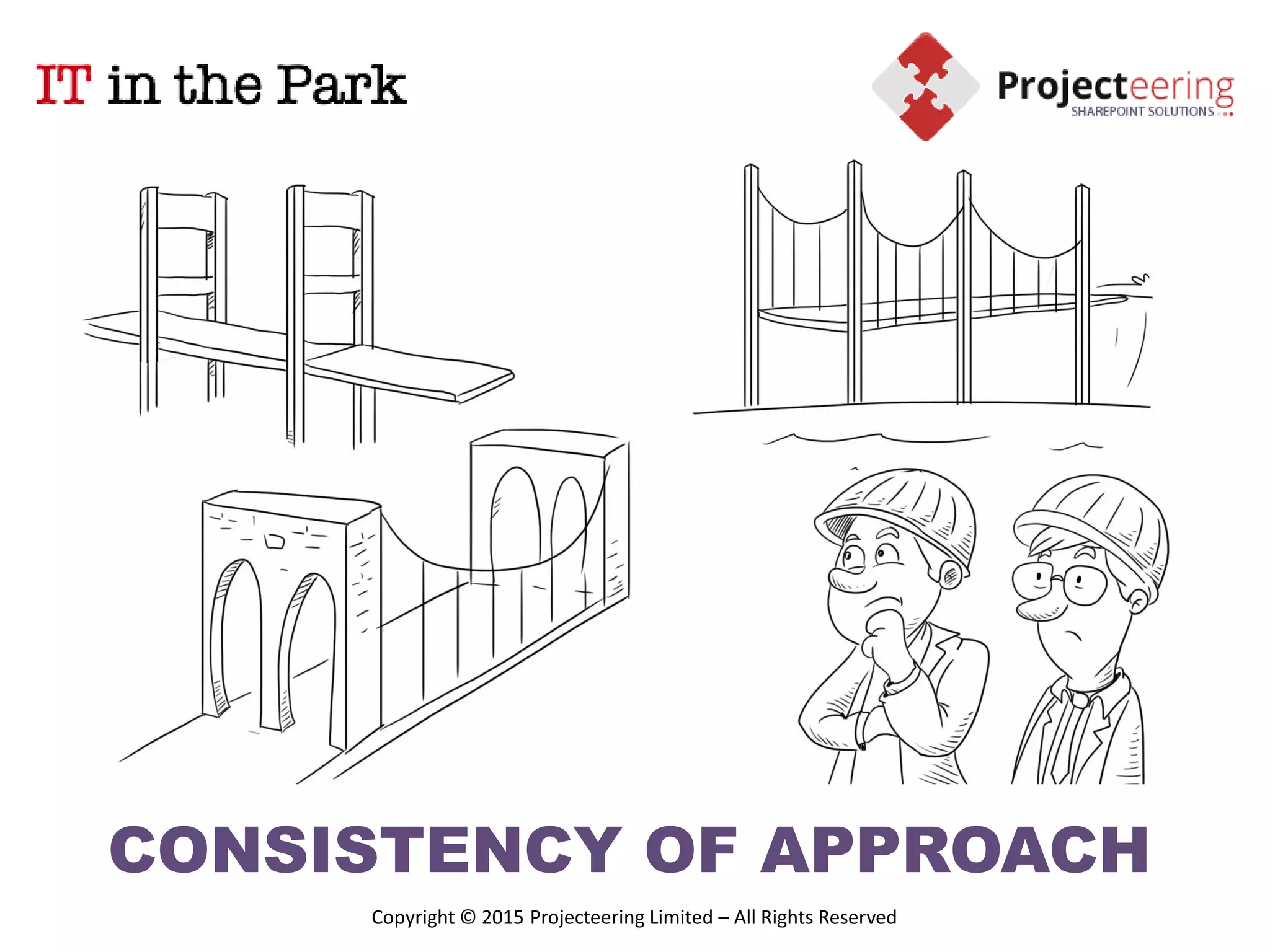
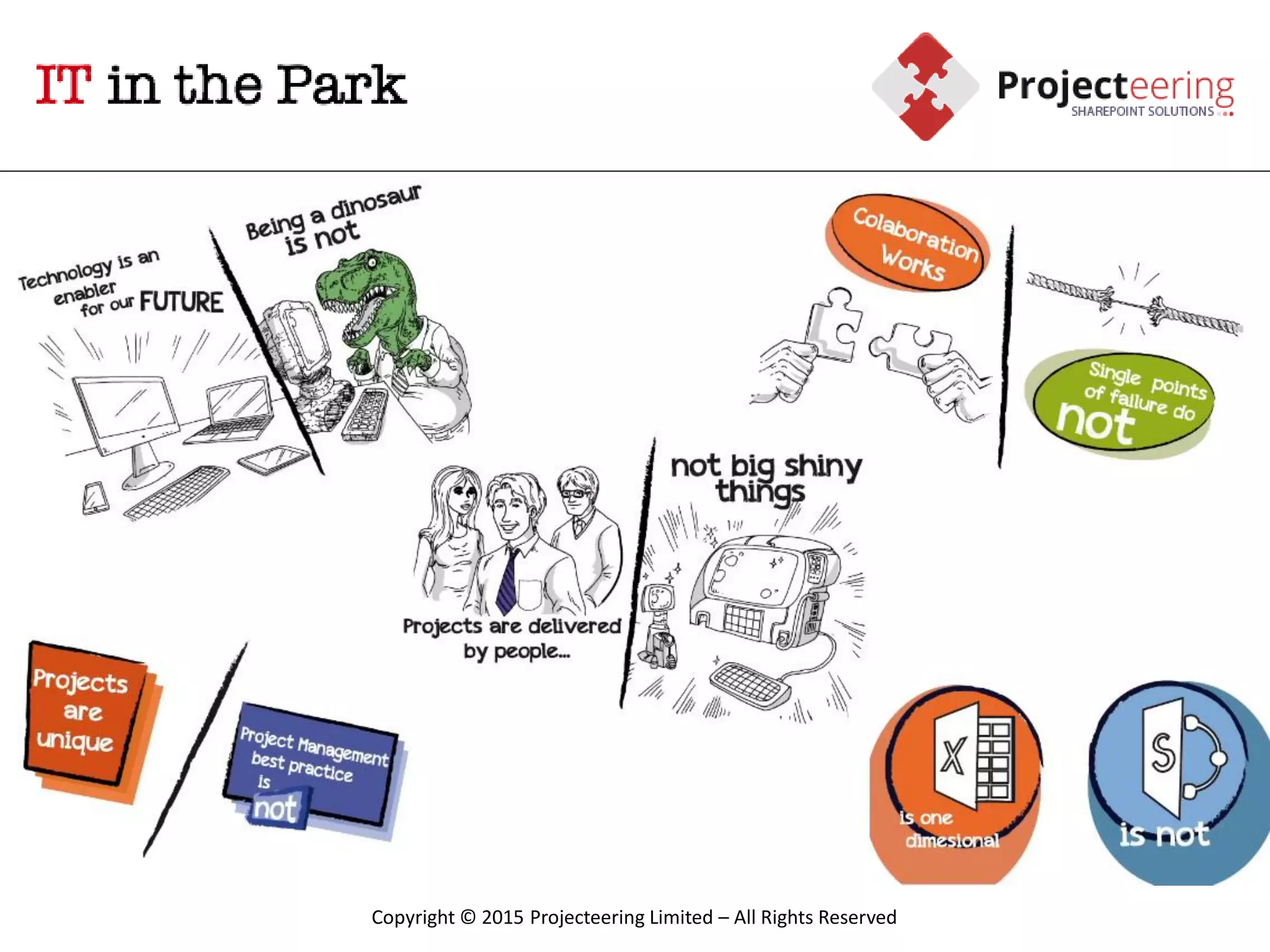
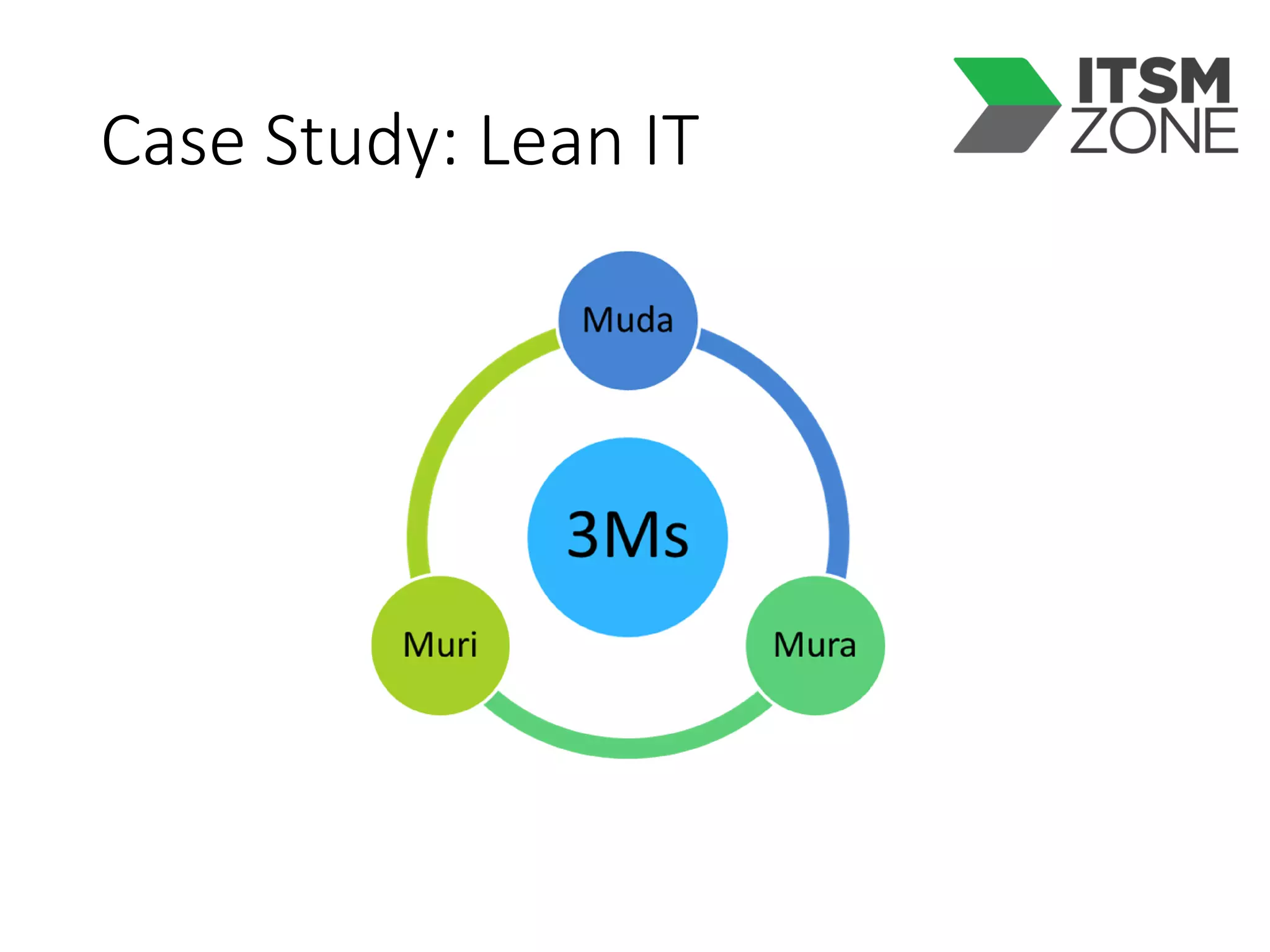
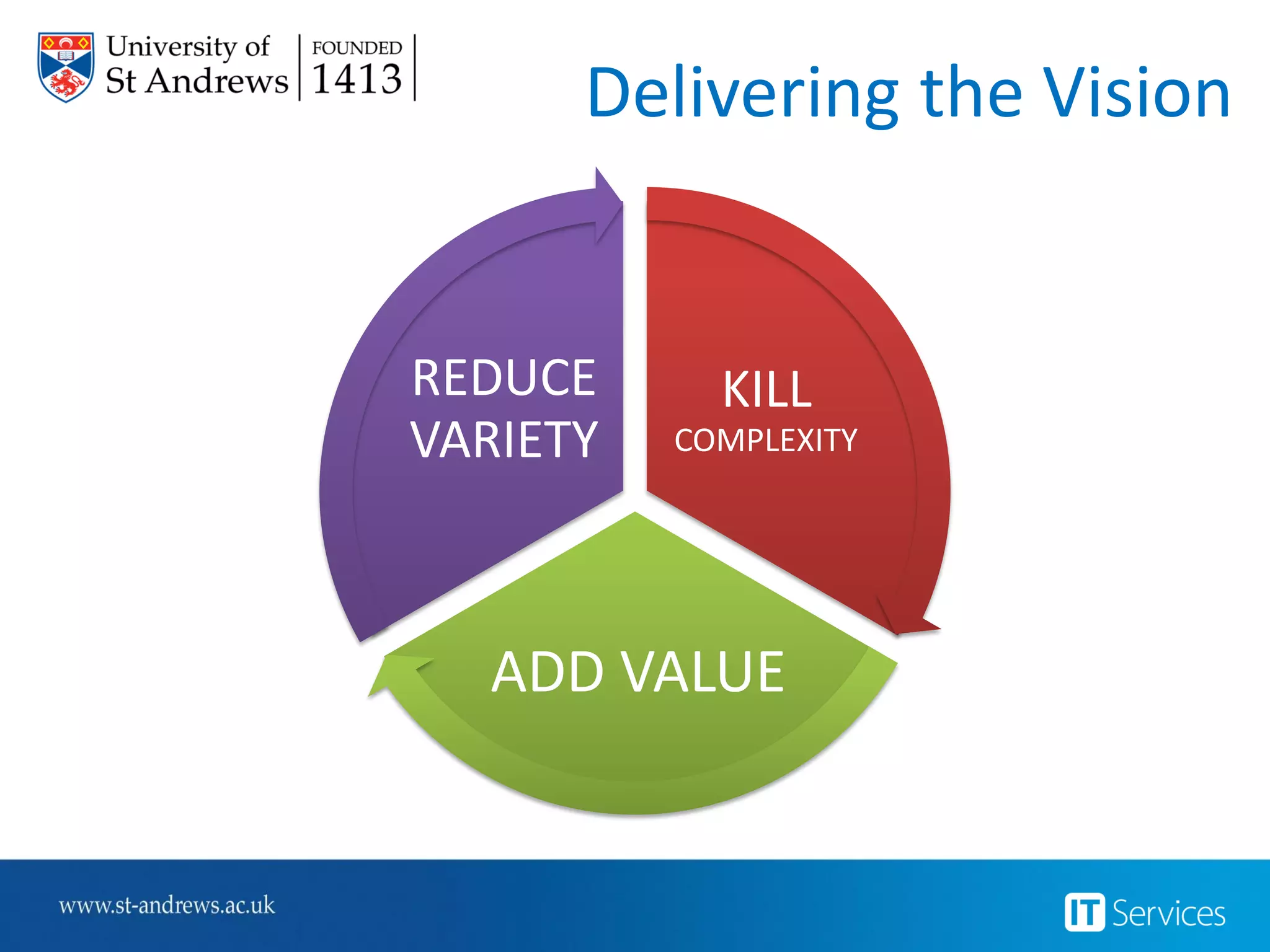
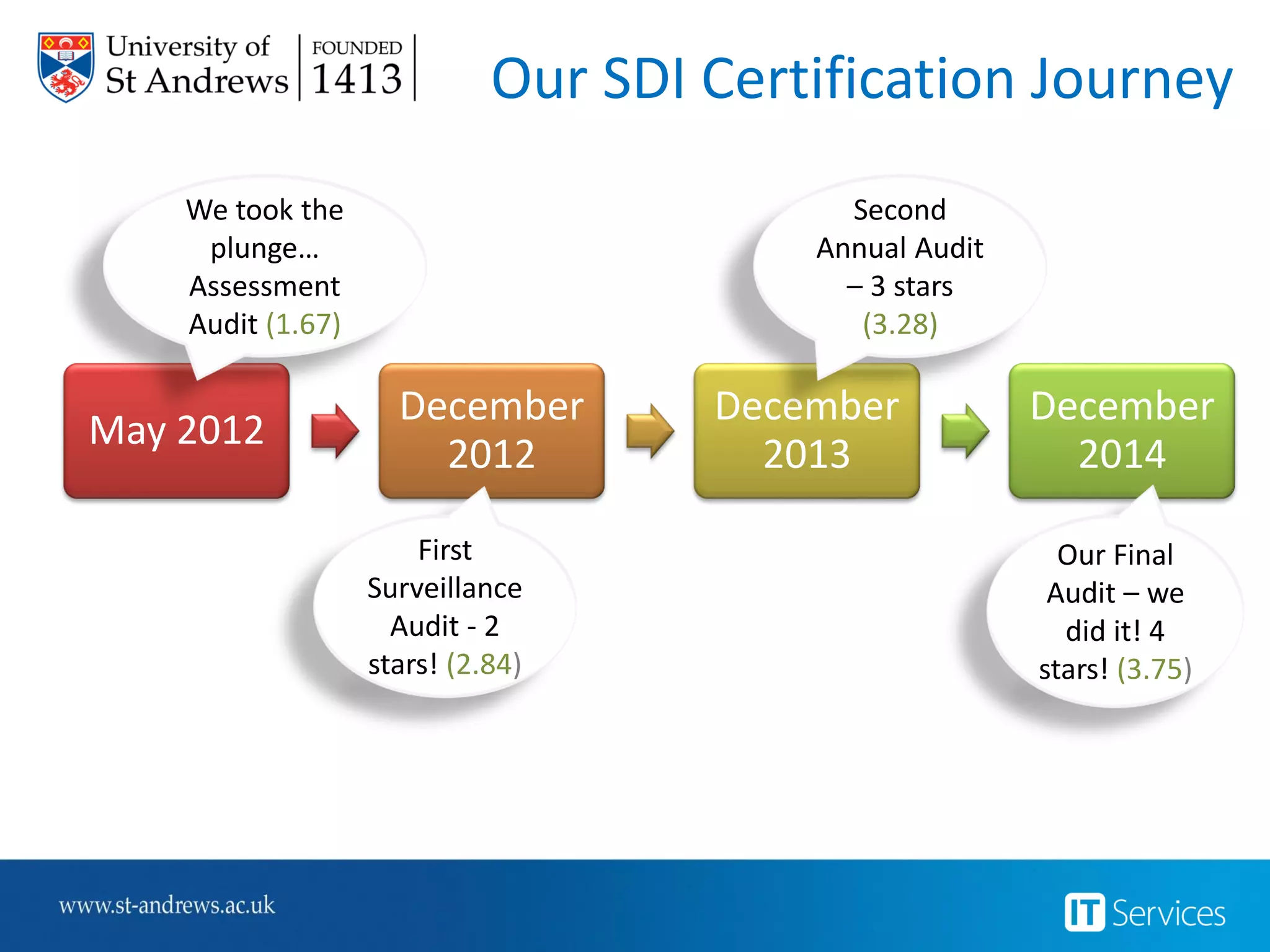
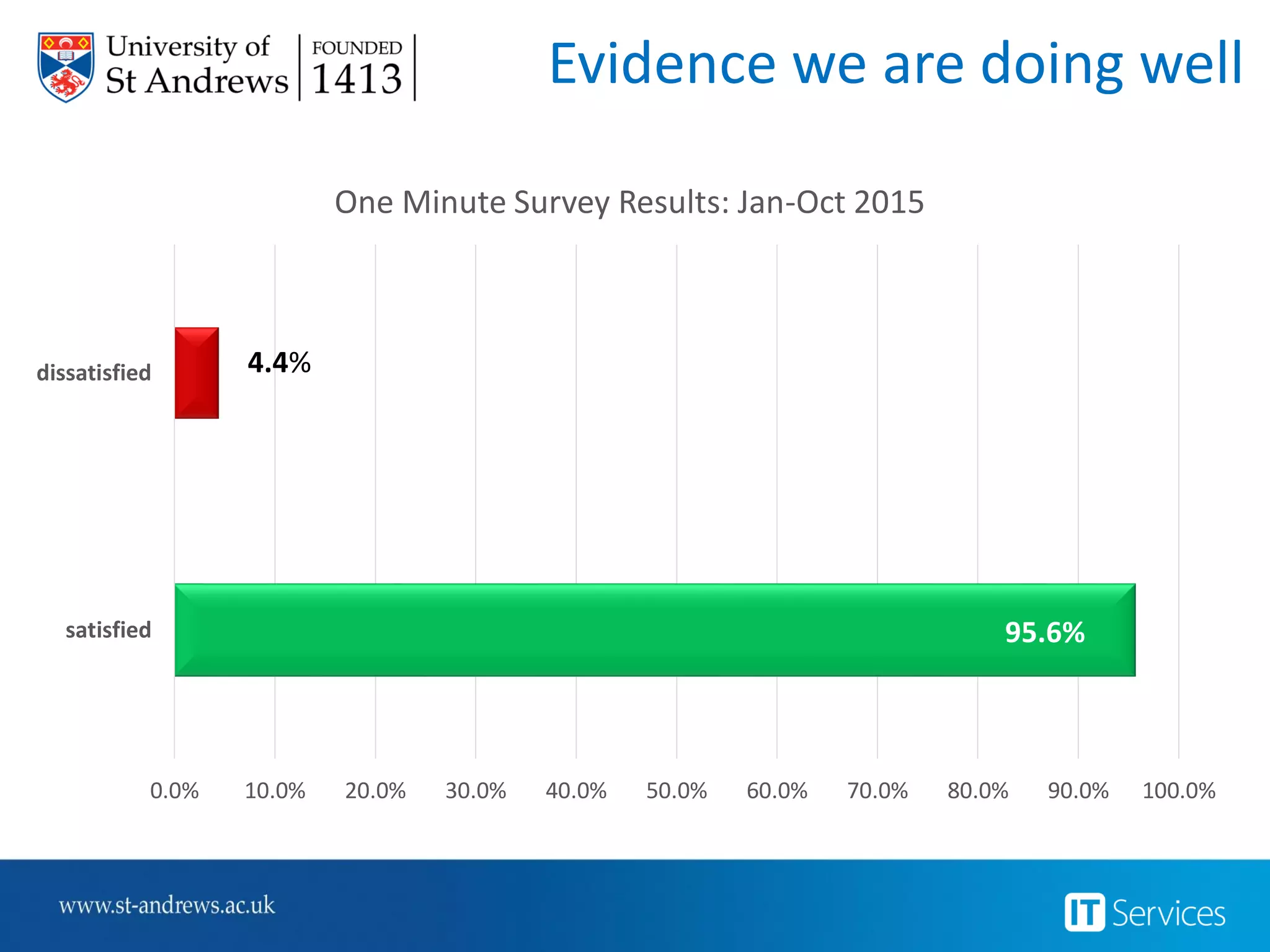
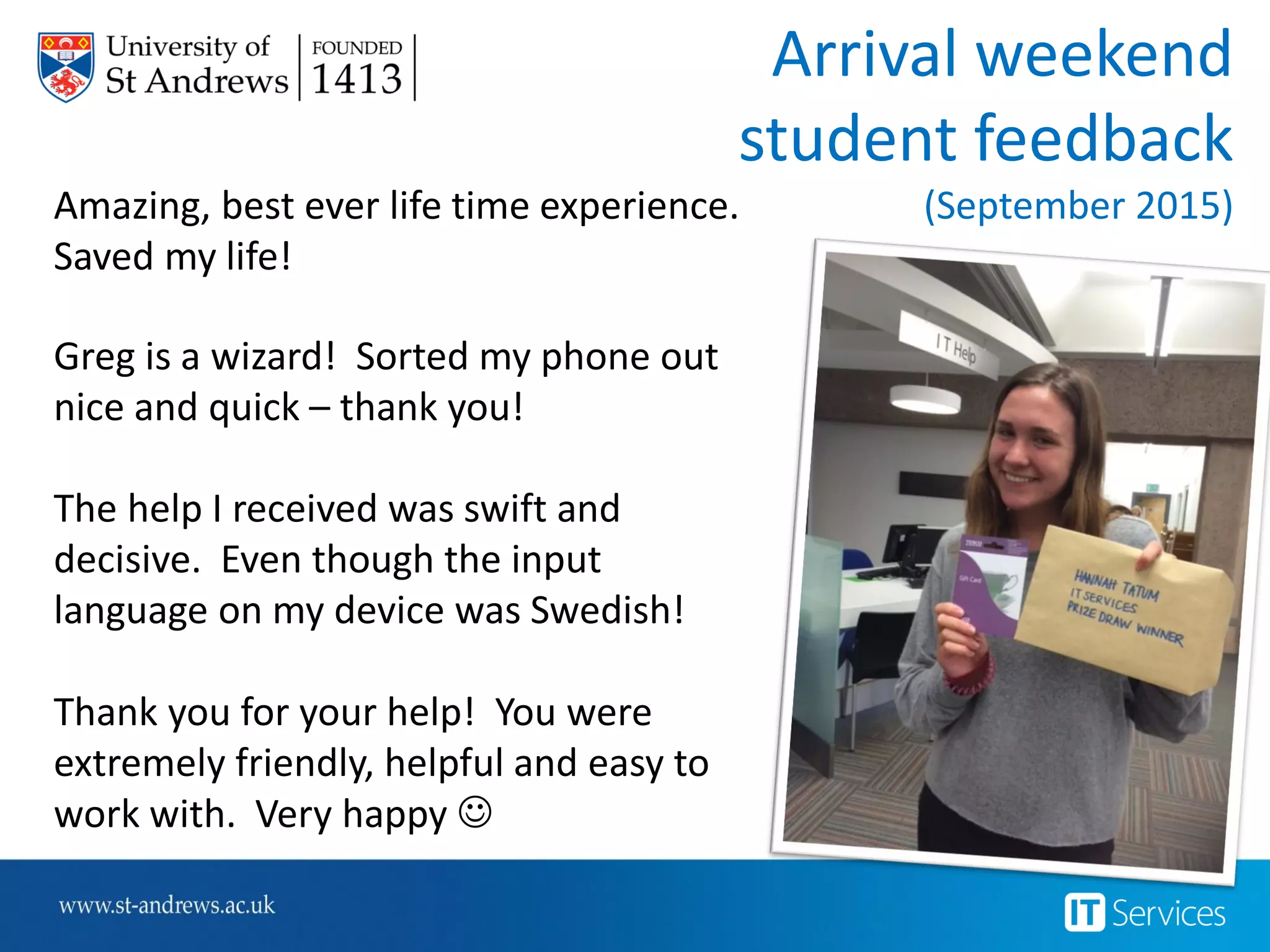
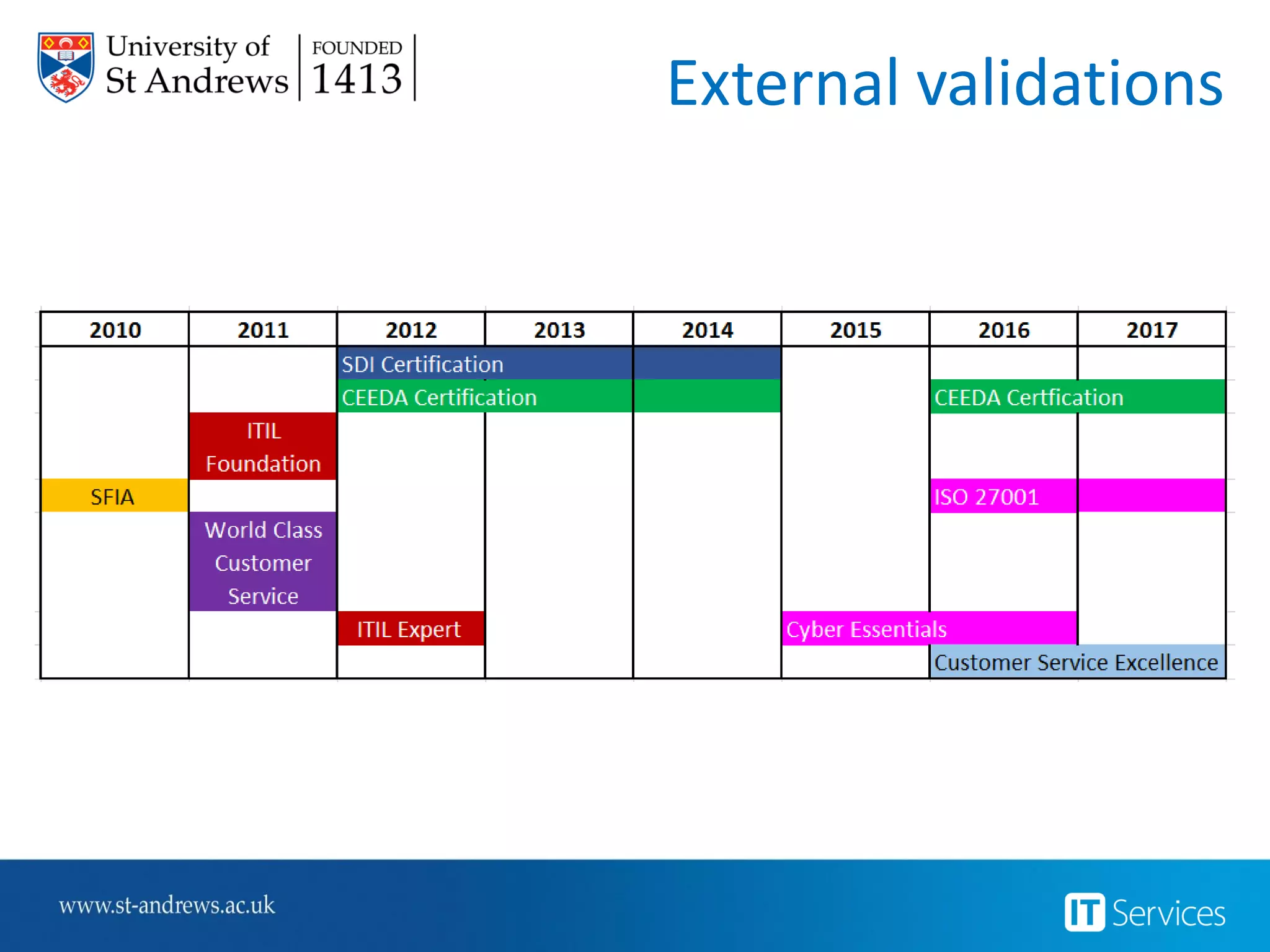
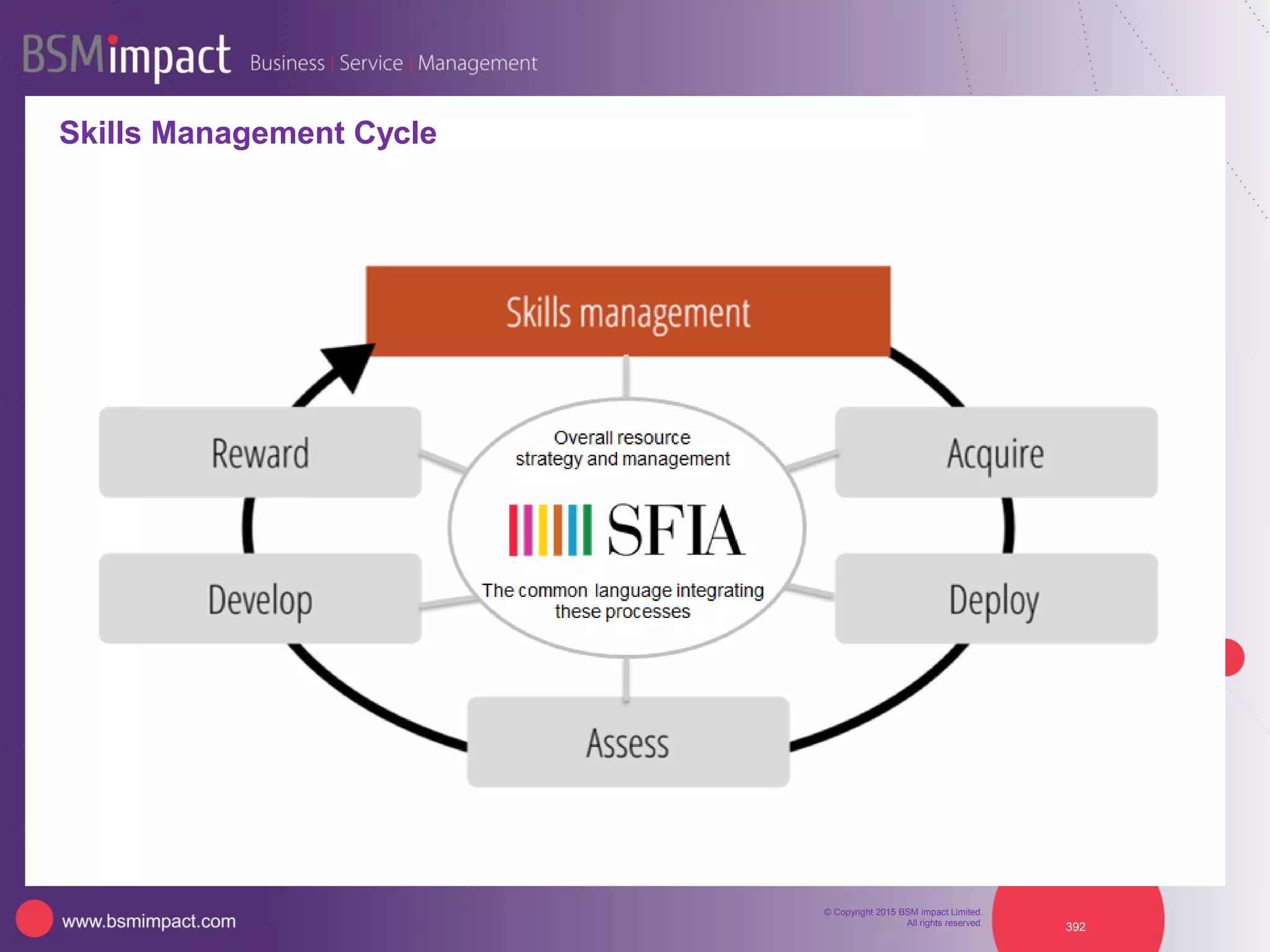
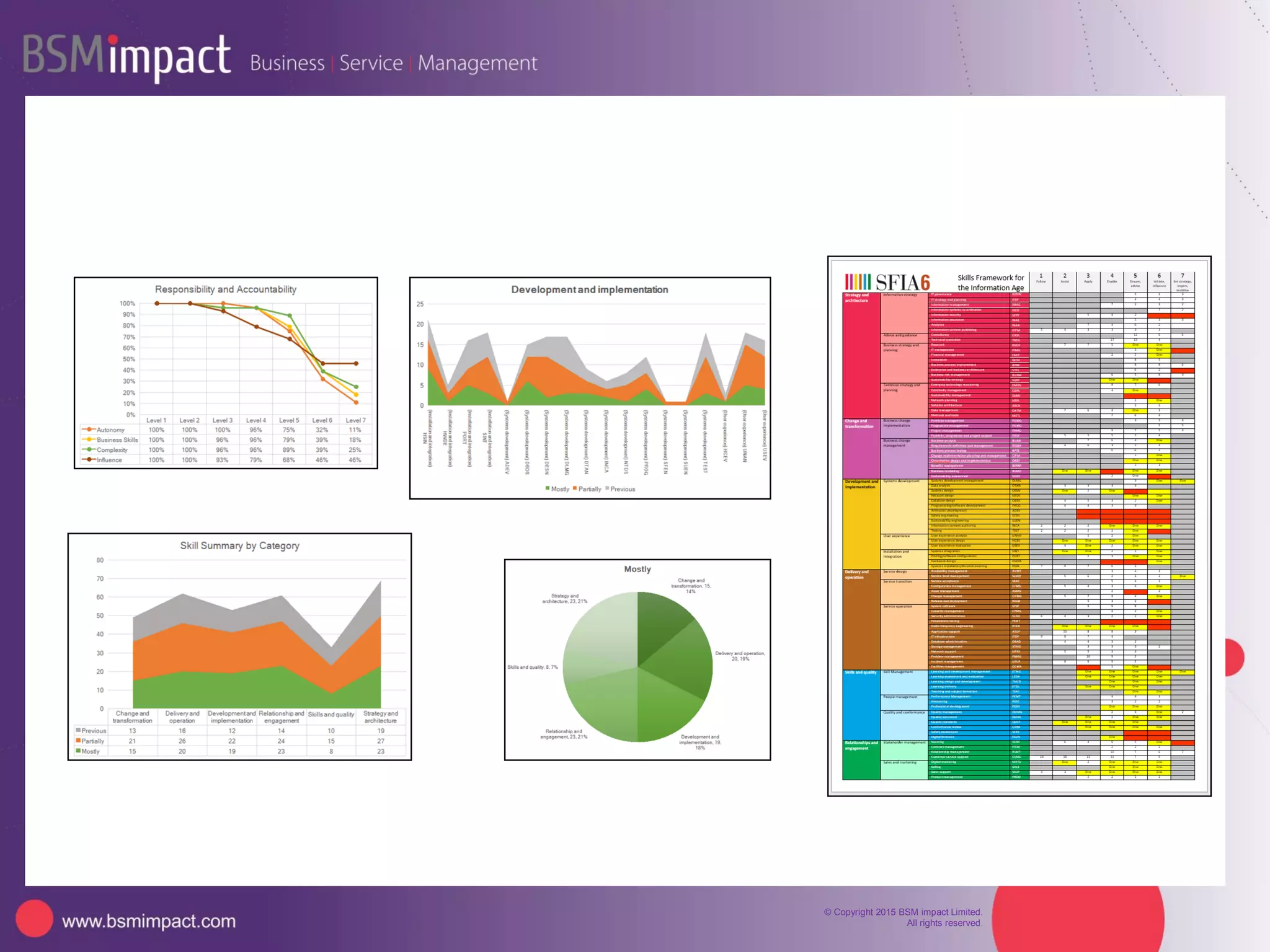
This document summarizes Christopher Rydings' presentation at #ITinthePark on lifting the bonnet on IT services at Arnold Clark Automobiles Ltd. Some key challenges Arnold Clark was facing included no adequate ticket system, uncontrolled changes, long request times, and static support resources. The approach involved implementing an IT service management framework using LANDESK, establishing a new organizational design aligned around key technology pillars, and focusing on automation, streamlining operations, and separating run and project activities. This resulted in outcomes such as breaking incidents down into categories, improved reporting, and small steps towards improved service delivery.