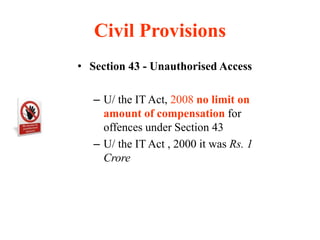
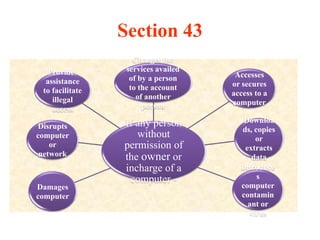
This document provides a comparative analysis of the Information Technology Act of 2000 and its amendment in 2008 in India. Some key changes introduced by the 2008 amendment include expanding the definition of electronic signatures to include technologies beyond digital signatures, increasing penalties for cybercrimes, strengthening privacy provisions and expanding the scope of offenses to include new cybercrimes like identity theft, cyber-stalking and cyber-terrorism. The amendment also granted new investigation powers to police officers and adjudication powers to specialized officers to handle cybercrime cases and disputes.