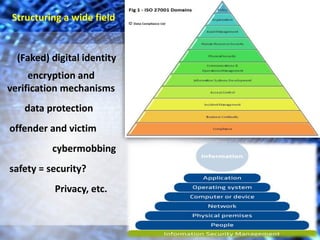
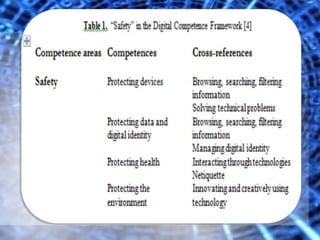
This document discusses information security as a key competence that should be taught in education frameworks and curricula. It outlines several frameworks that reference information security concepts, including protecting confidentiality, integrity, authenticity, availability, and reliability of information. The document proposes implementing information security education through learning tasks and a planning grid for lower secondary education. It argues that information security is ubiquitous and important for students to learn about given humans' vulnerability in the digital world.






![Further (External) Initiatives
Throughout Europe
Saferinternet (A), Klicksave (D), …
[Saferinternet-Day]](https://image.slidesharecdn.com/istanbul-issep2014-140919044202-phpapp02/85/Istanbul-issep2014-10-320.jpg)




