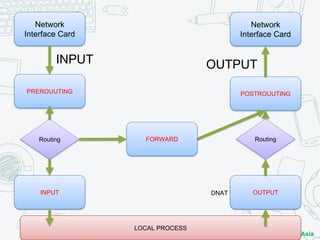
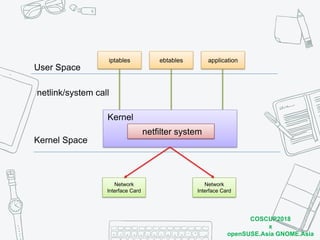
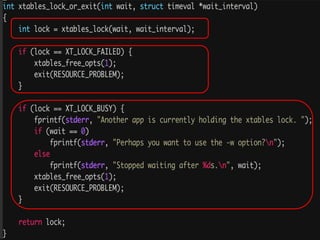
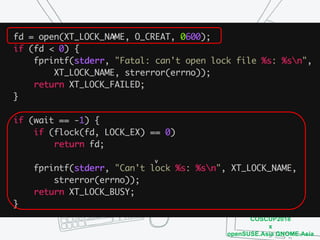
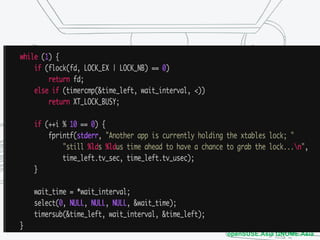
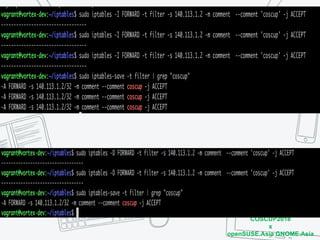
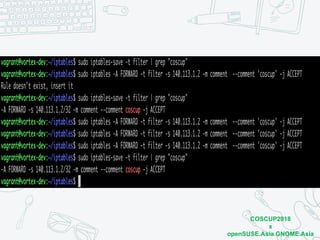
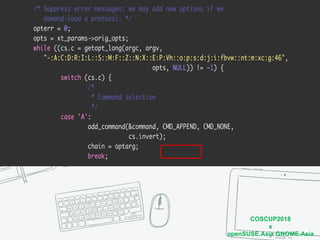
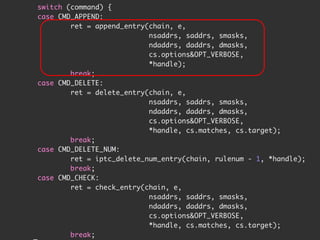
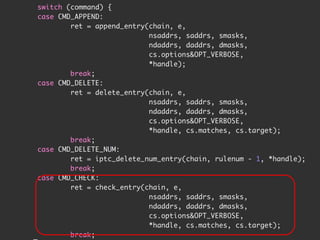
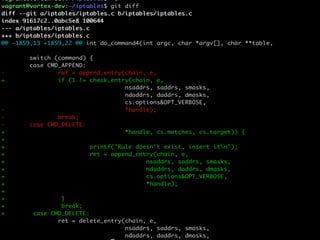
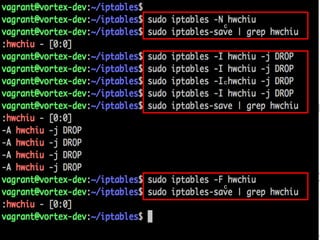
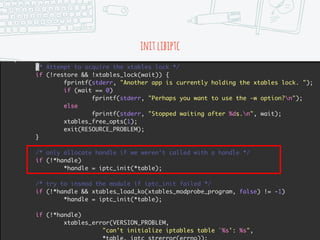
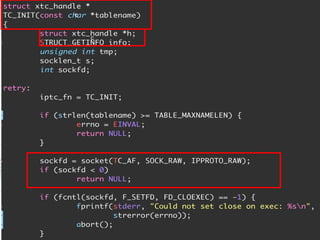
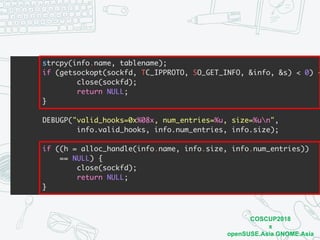
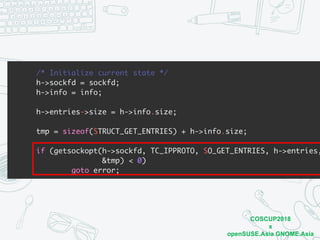
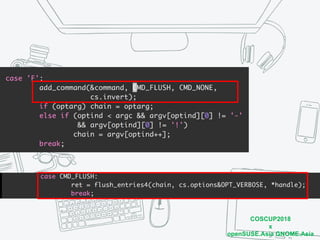
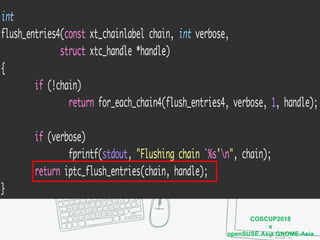
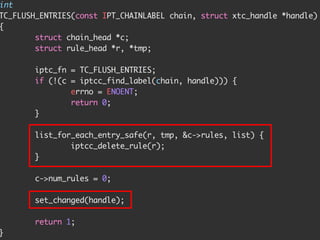
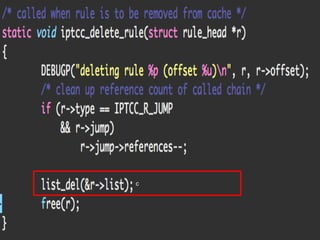
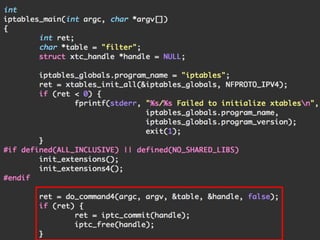
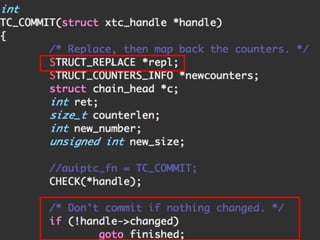
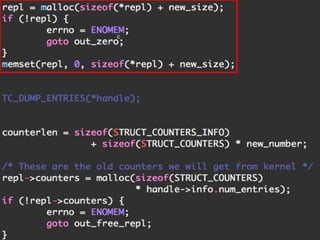
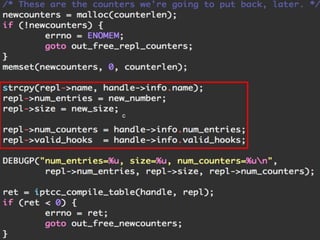
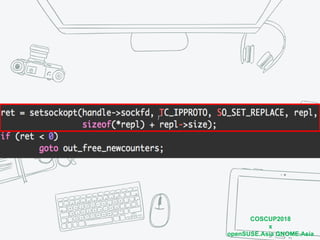
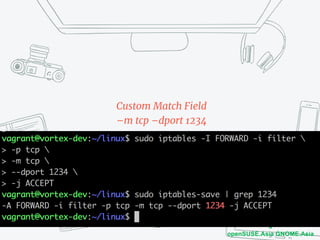
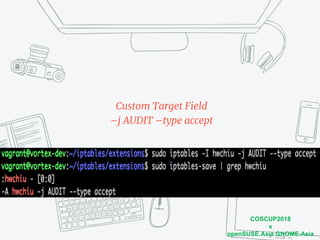
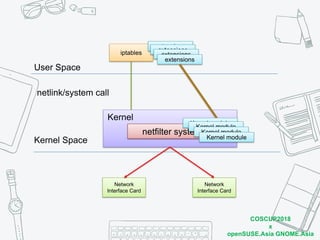
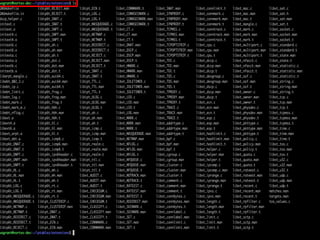
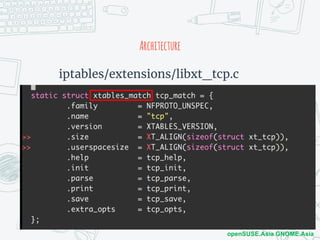
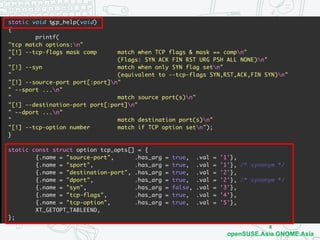
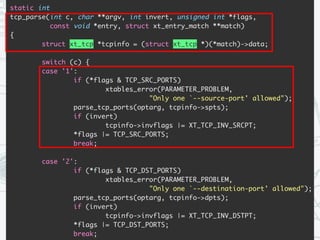
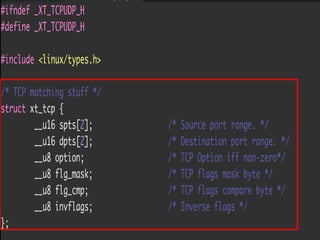
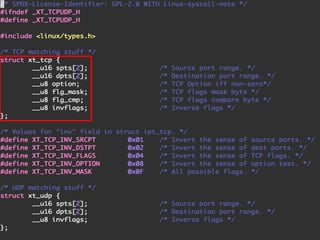
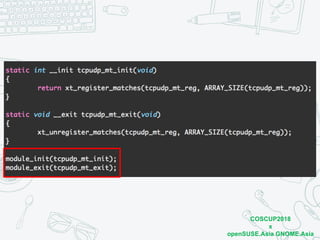
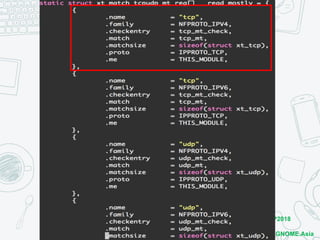
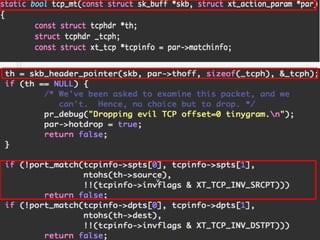
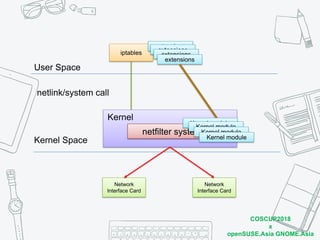
The document discusses iptables and network packet filtering. It begins with an introduction of the presenter and overview of iptables. It then covers how iptables works, including the tables, chains and communication between userspace and kernelspace. It discusses common iptables commands like flush and check. It also covers iptables extensions, how they are implemented in both userspace and kernelspace, and provides an example of custom TCP matching. The presentation aims to explain how the iptables userspace tools interact with the kernelspace netfilter system and custom extensions can be added.