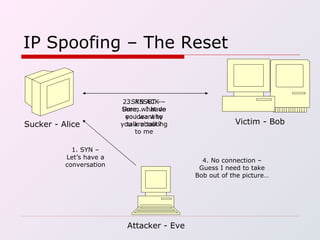
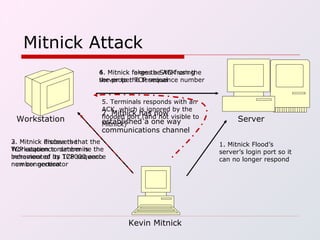
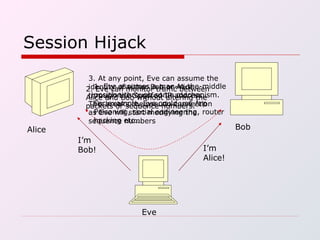
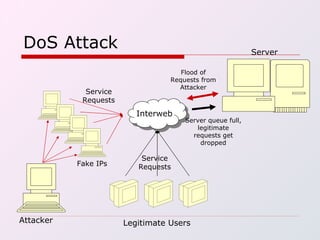
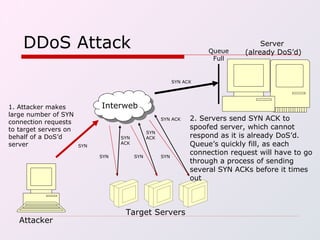
IP spoofing involves falsifying the source IP address in packets sent over the Internet in order to mask the identity of the sender. This technique can be used to carry out various types of attacks, including session hijacking, denial-of-service attacks, and man-in-the-middle attacks. While IP spoofing poses challenges for attackers due to protocols like TCP, it continues to be a threat. Defenses include more complex TCP sequence number generation, blocking spoofed IP addresses, and detecting traffic originating outside expected domains.