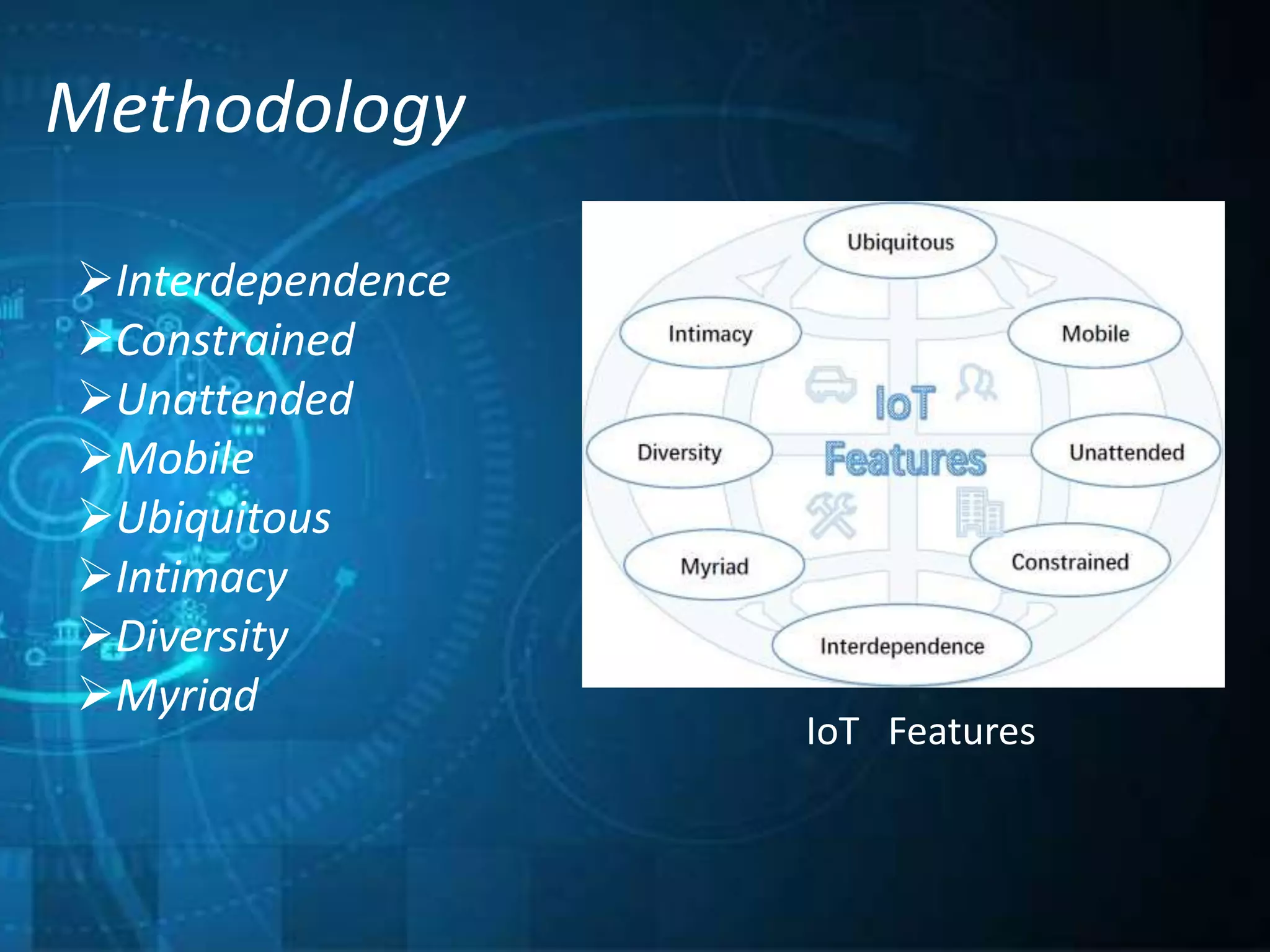
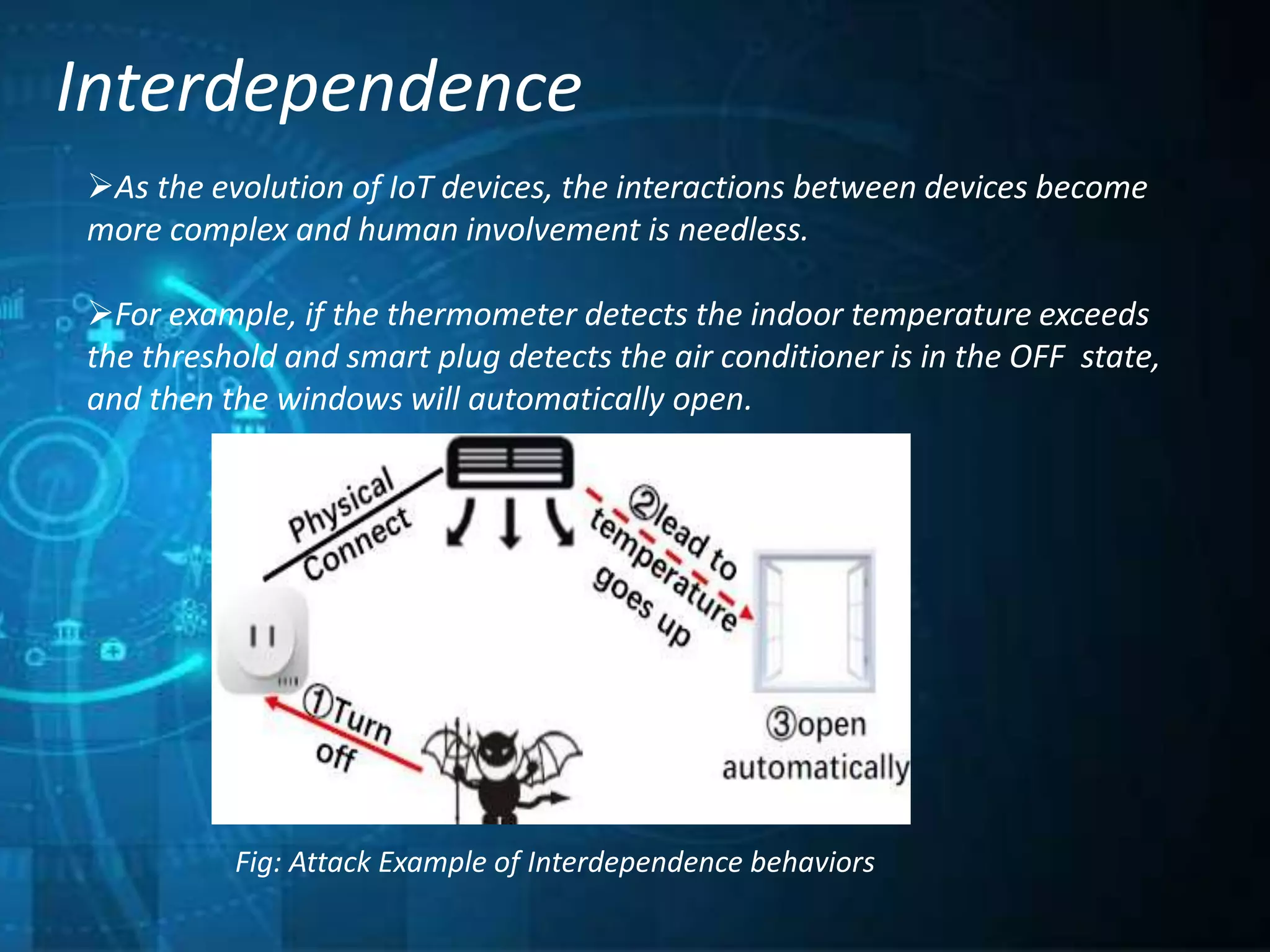
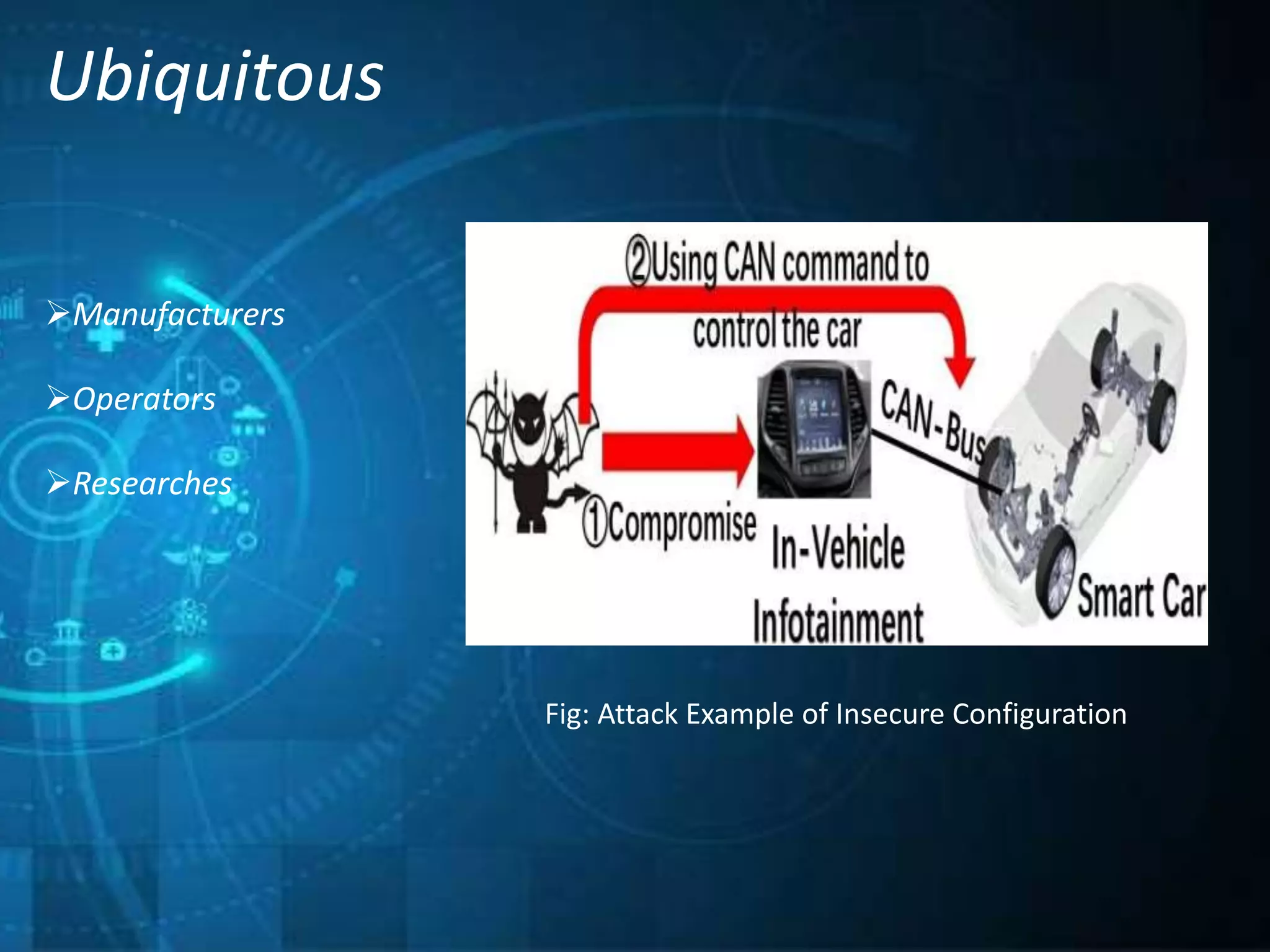
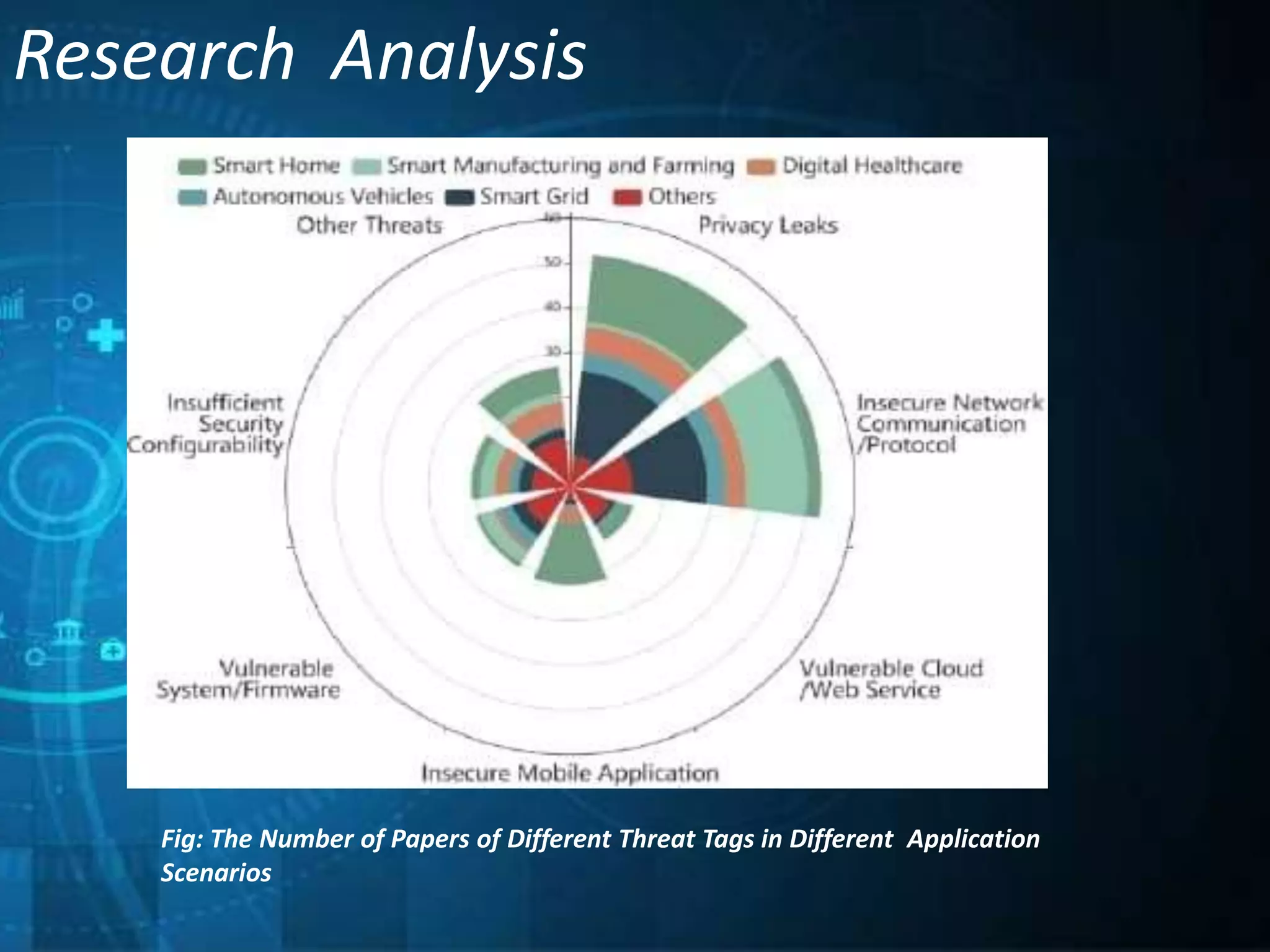
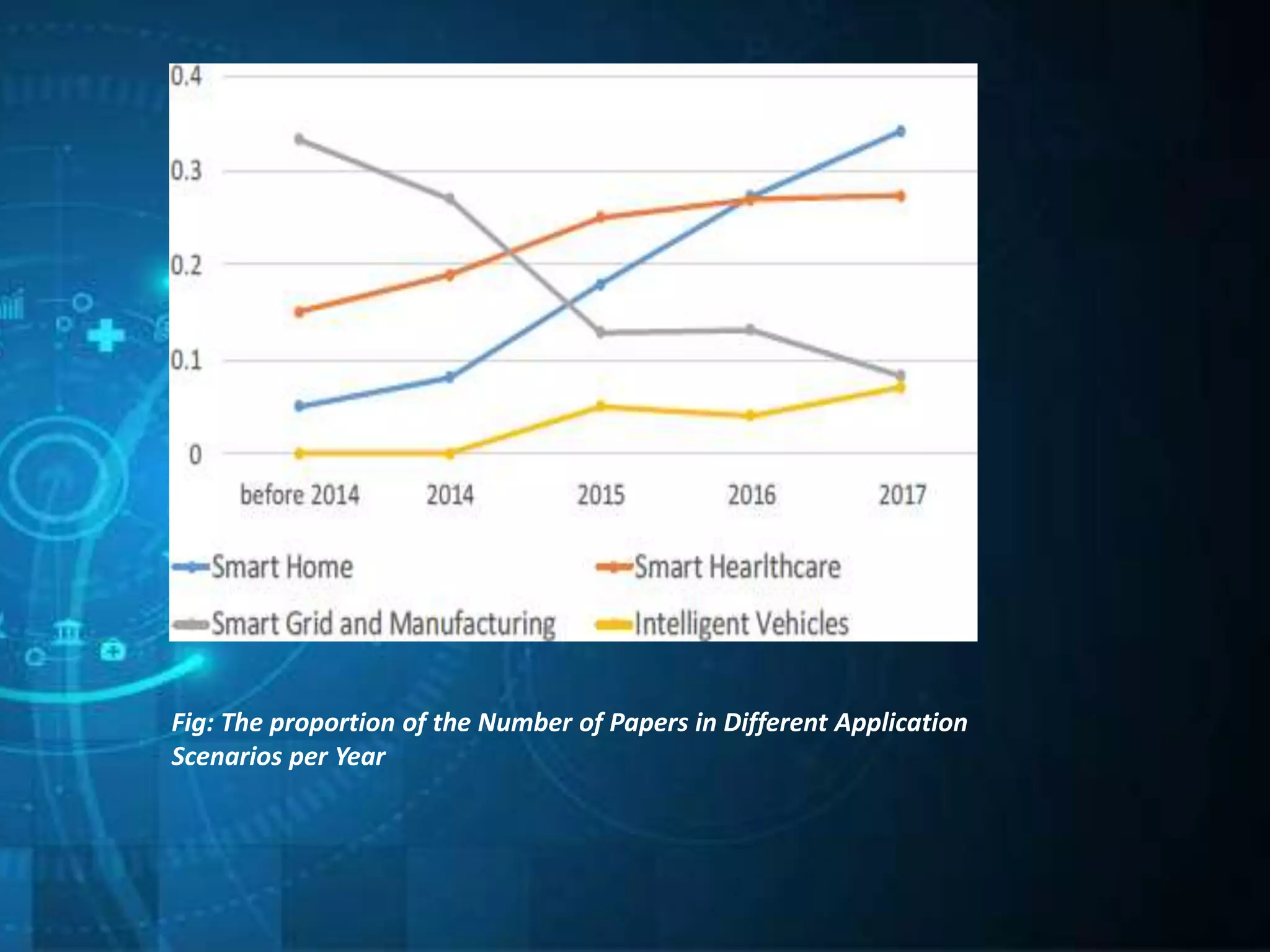
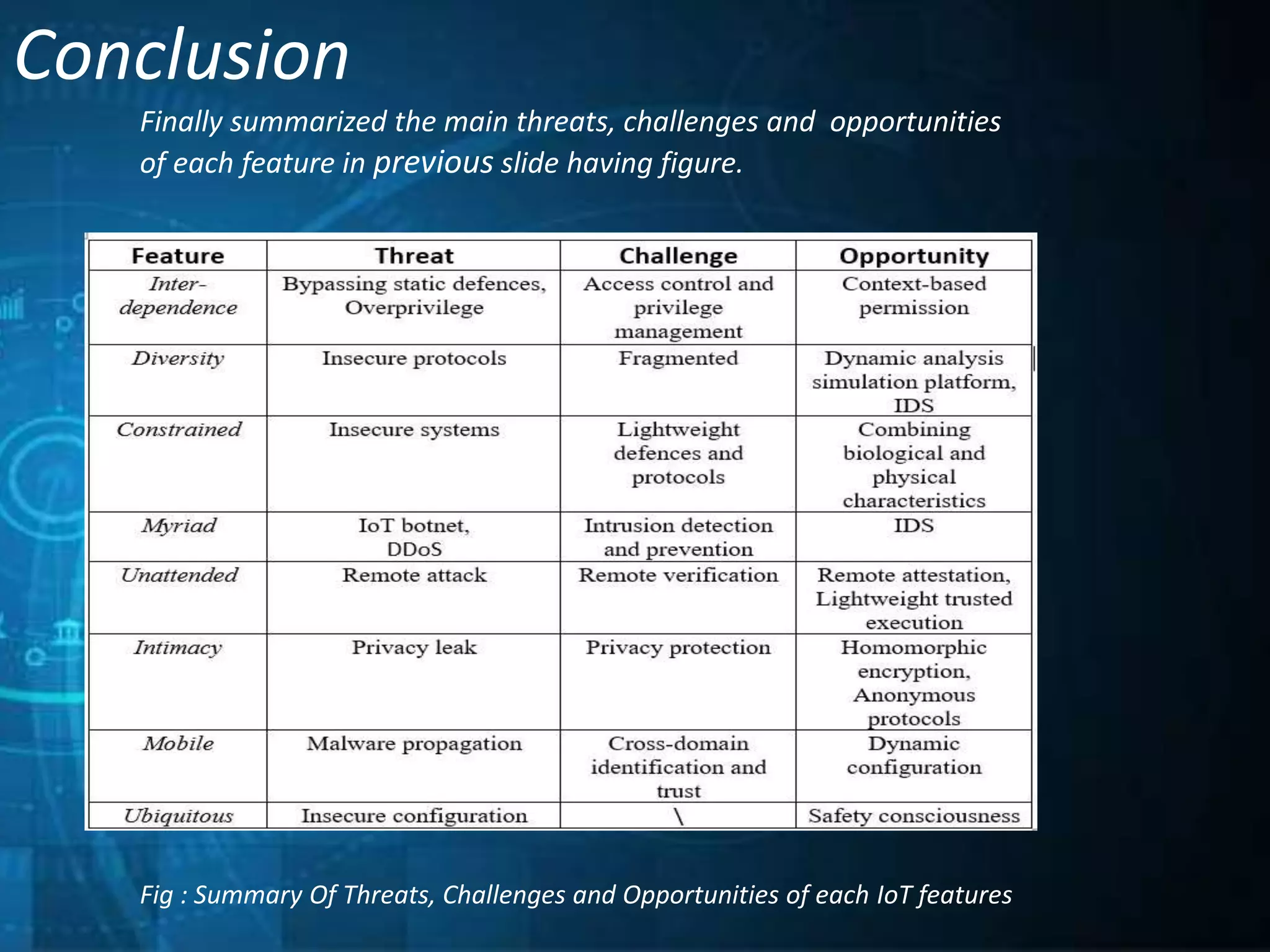
This document outlines a technical seminar presentation on the effect of new Internet of Things (IoT) features on security and privacy. It discusses various IoT features like interdependence, constrained resources, unattended operation, mobility, ubiquity, intimacy with devices, and the myriad of devices and data. It analyzes research on security threats in different IoT application scenarios and years. The document also covers advantages and disadvantages of IoT, examples applications, and concludes by summarizing threats, challenges and opportunities of each discussed IoT feature.