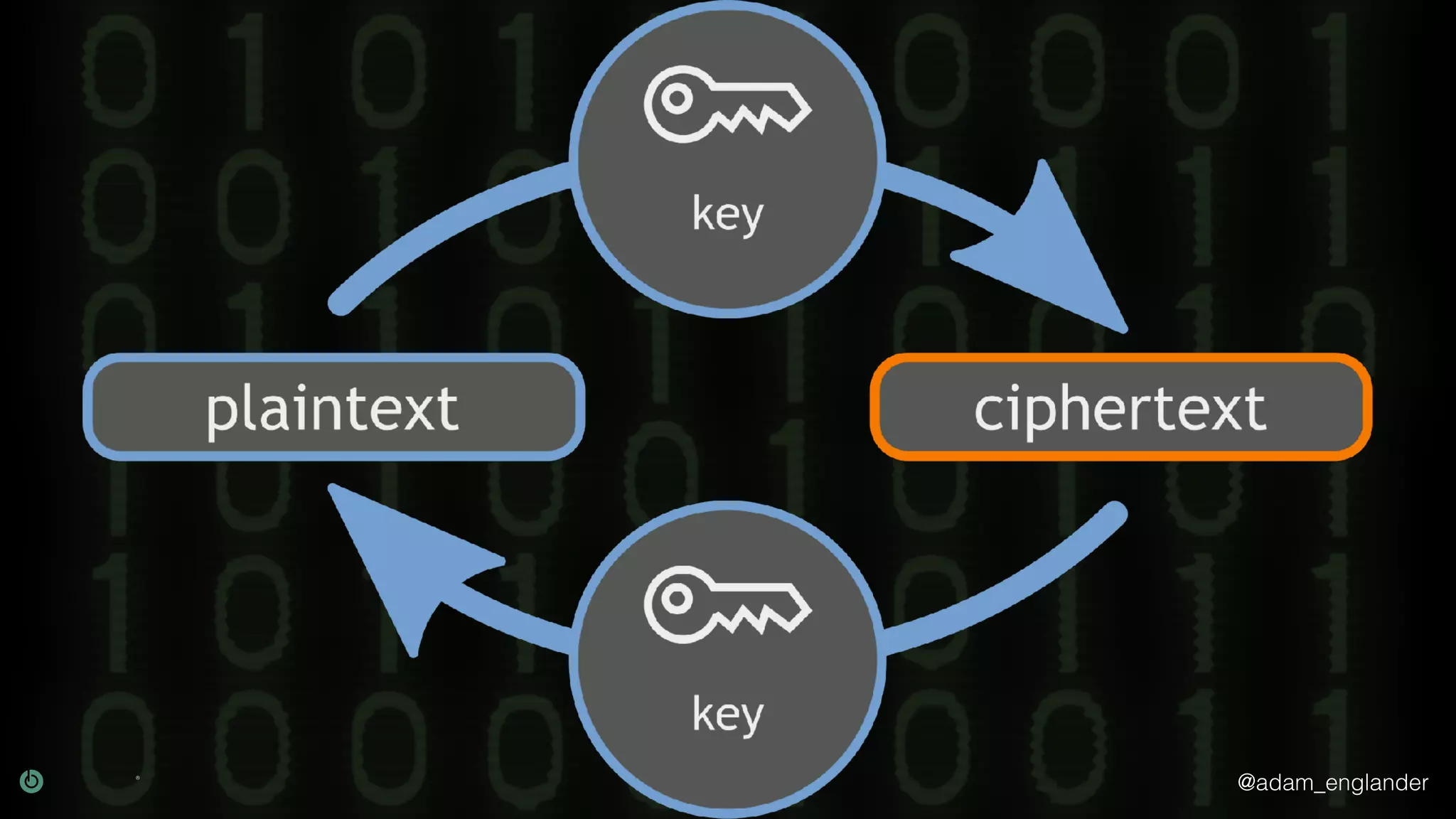
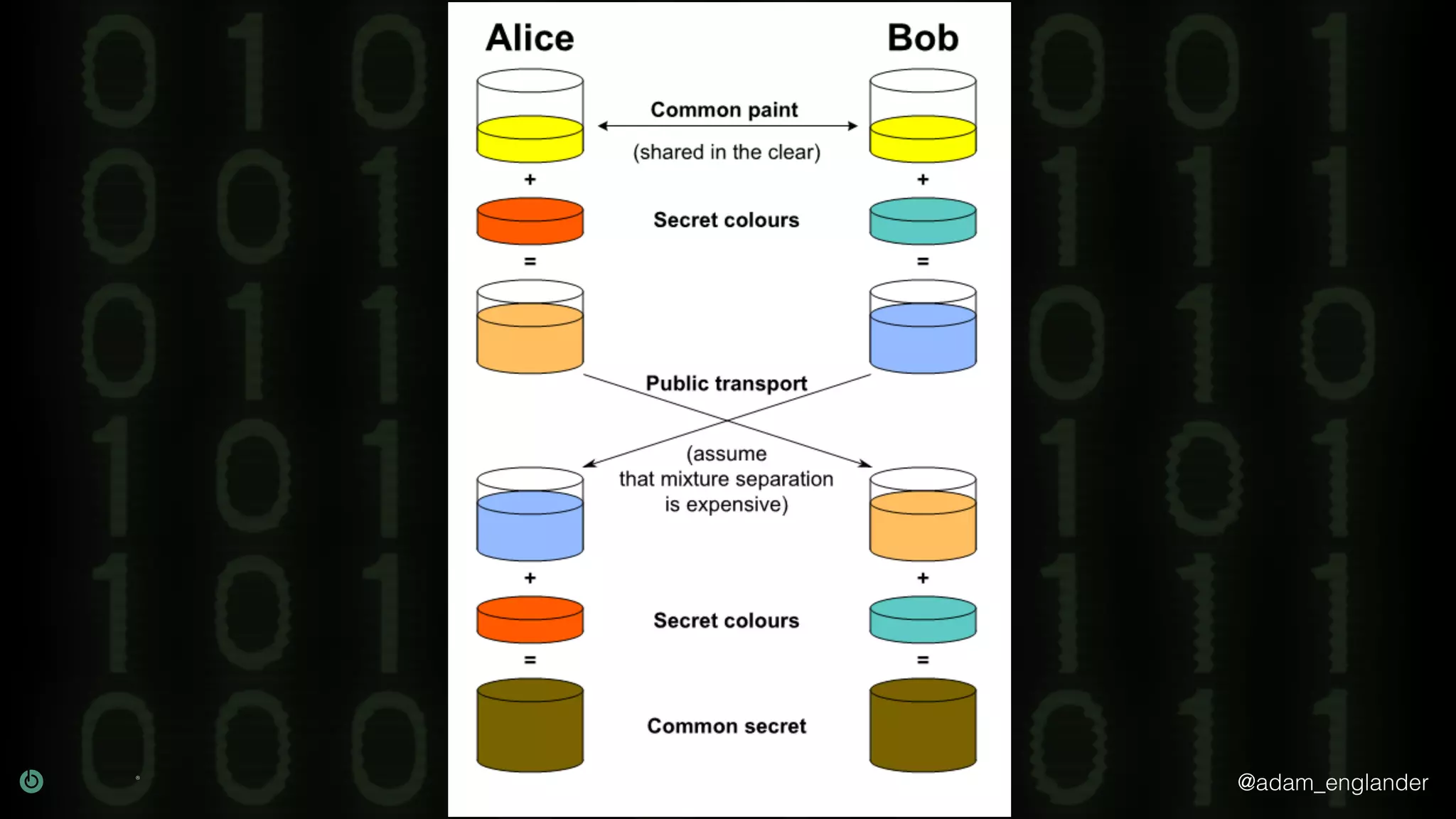
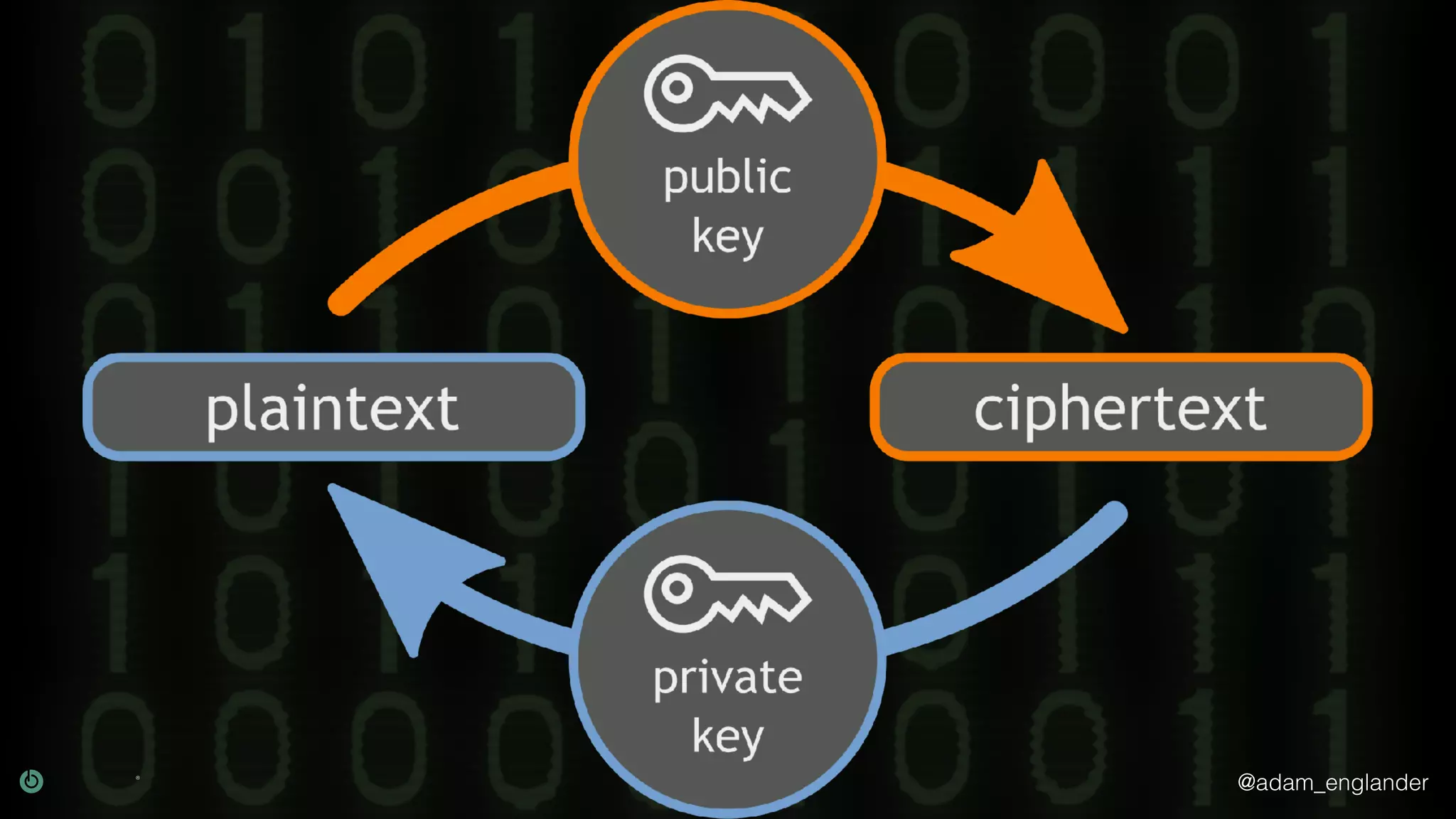
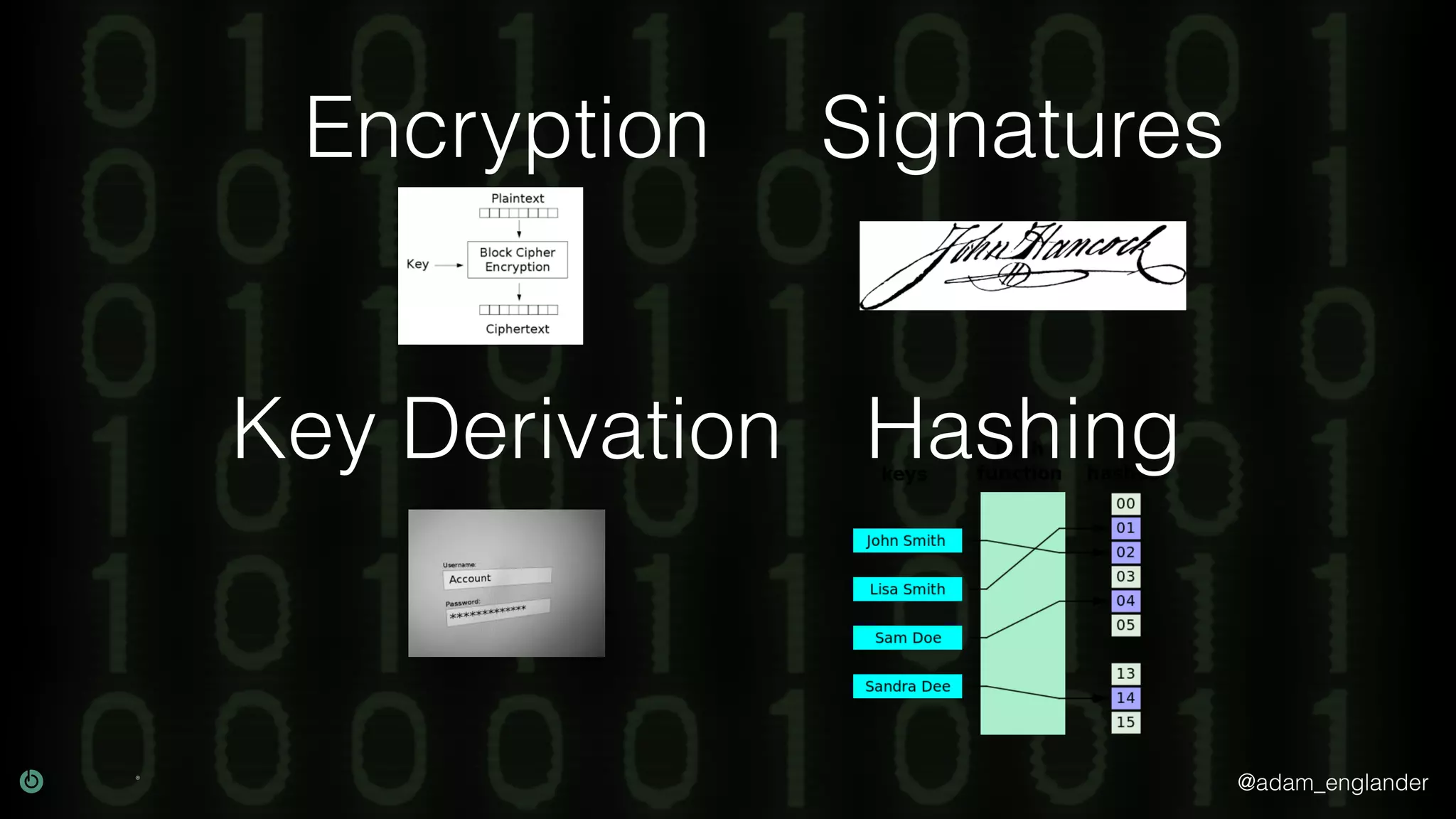
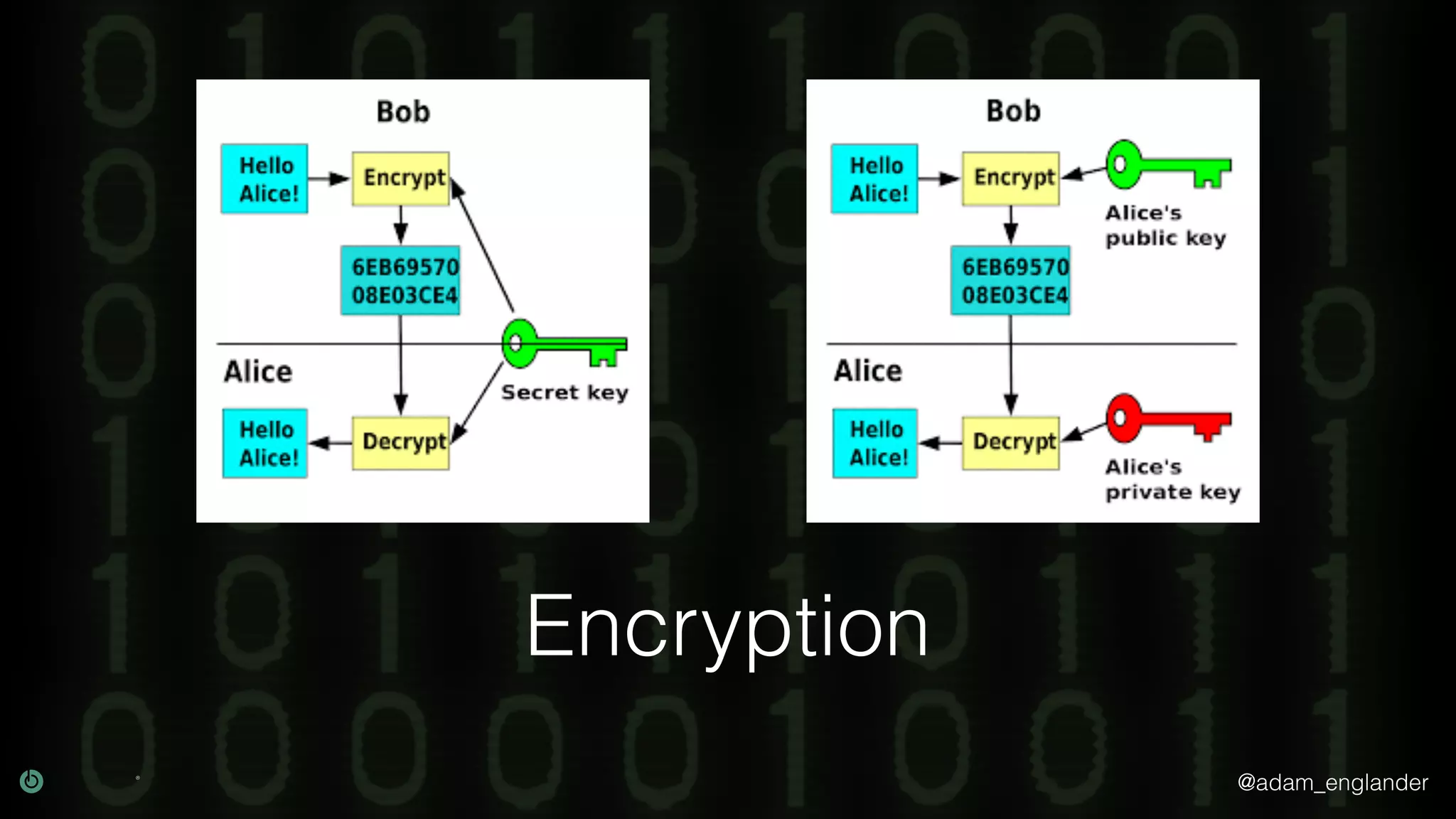
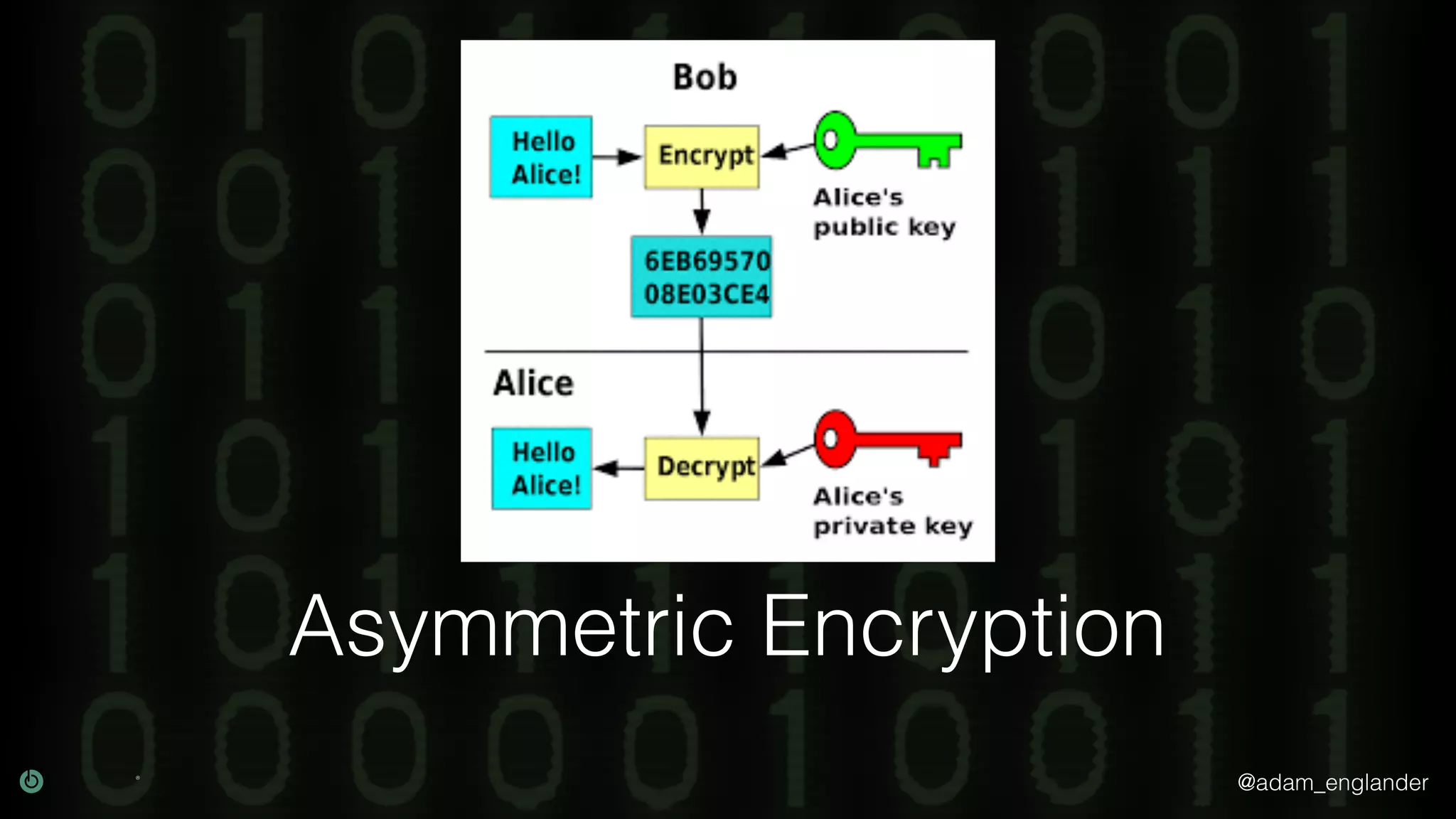
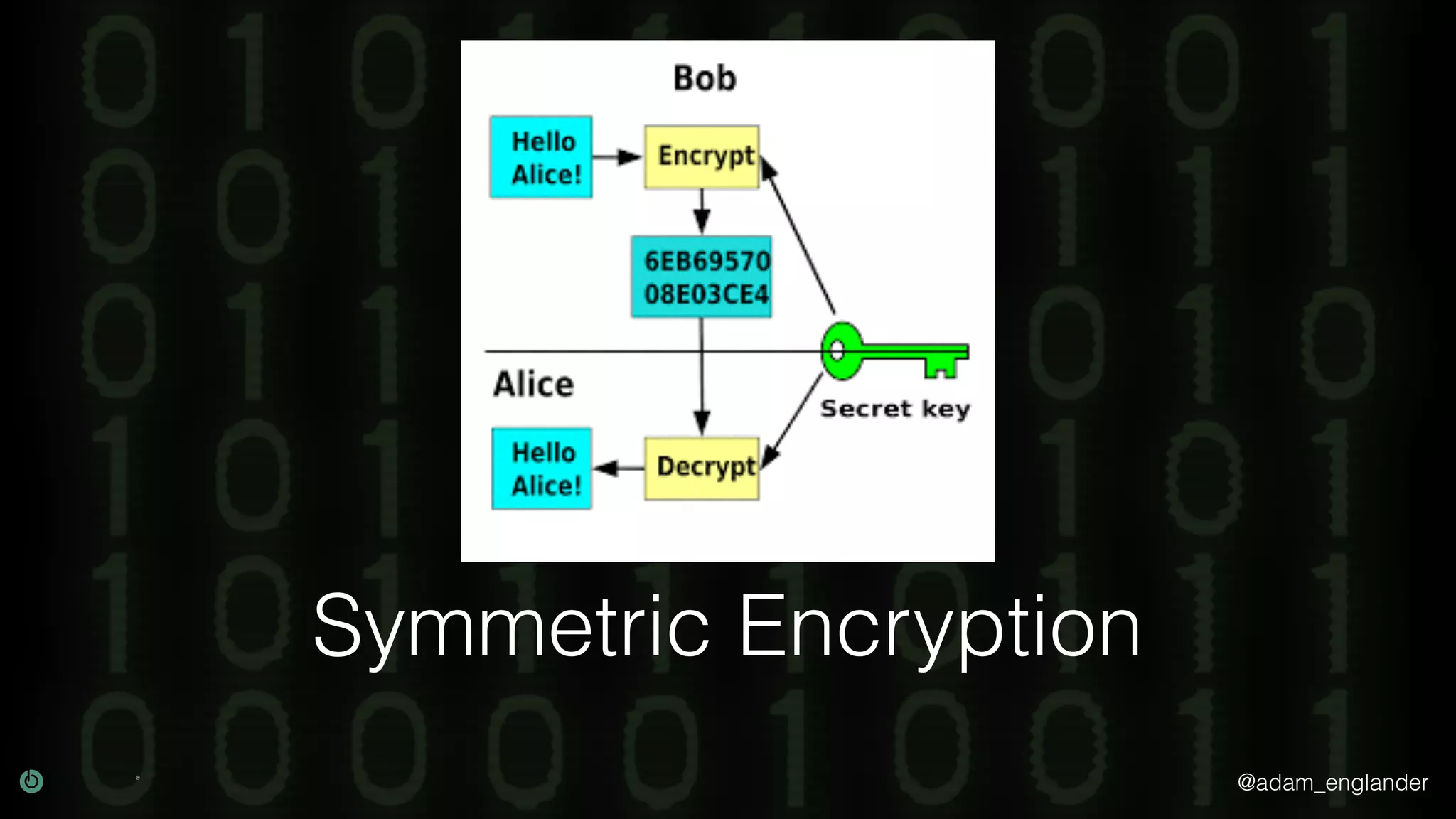
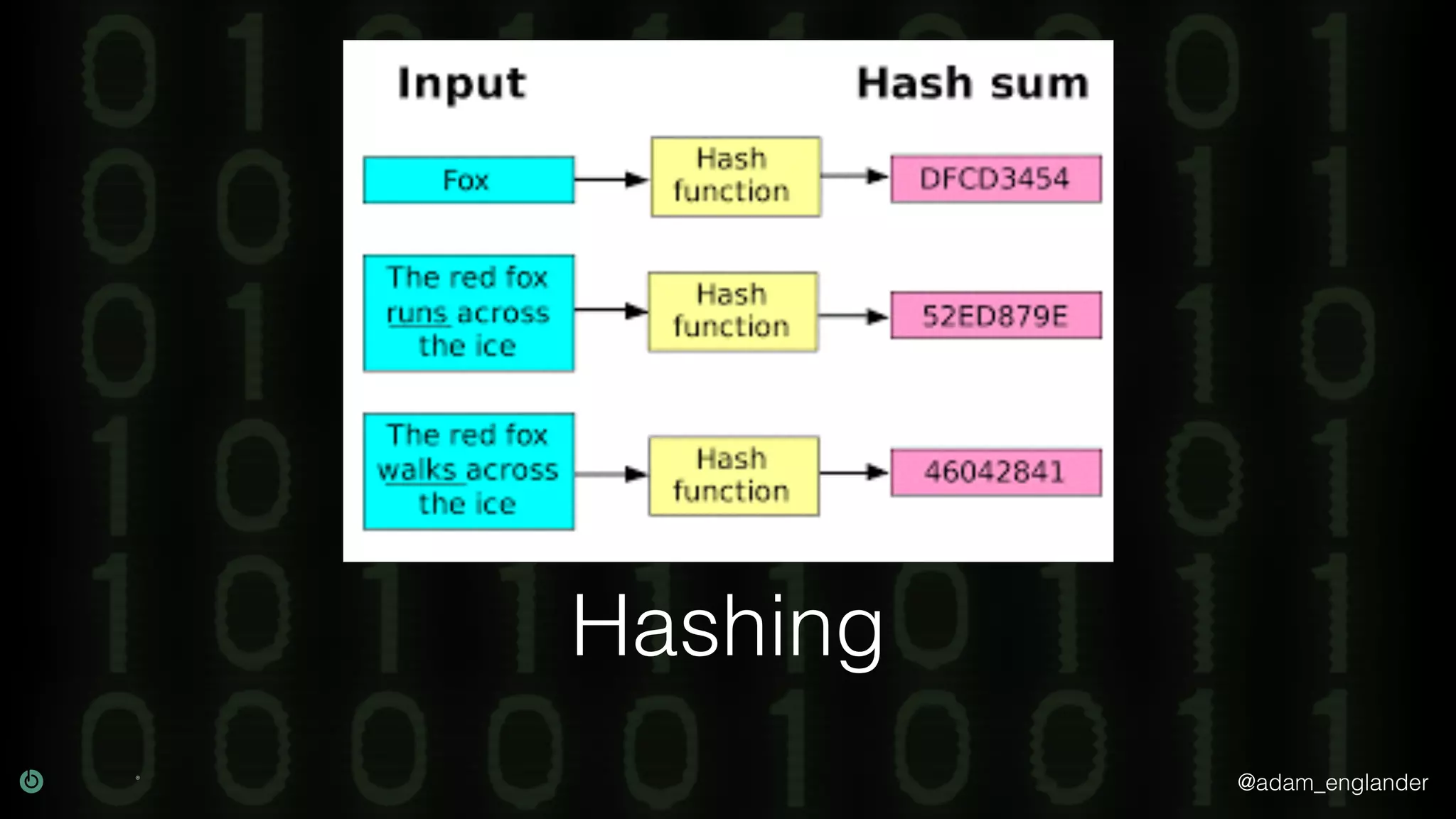
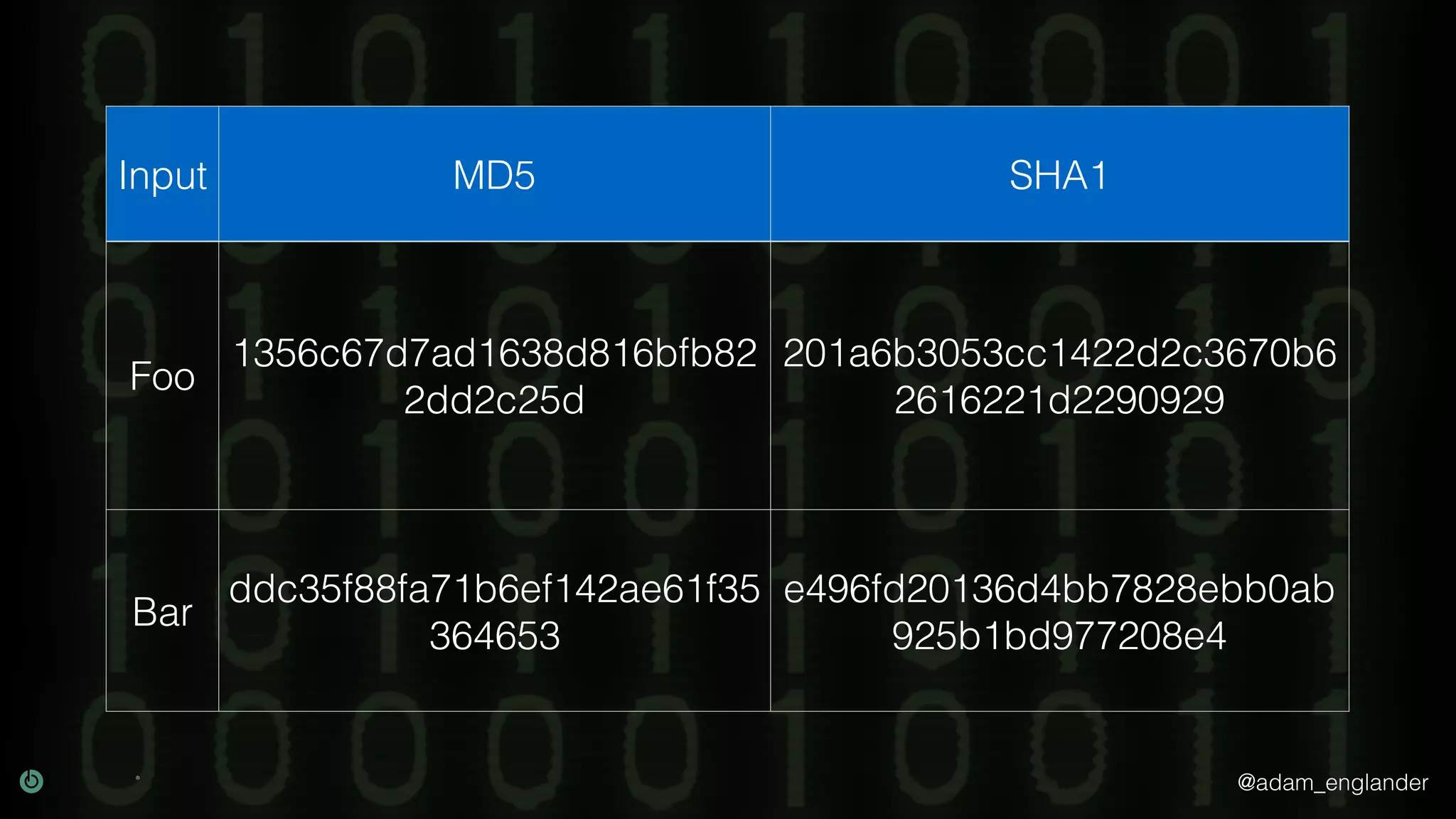
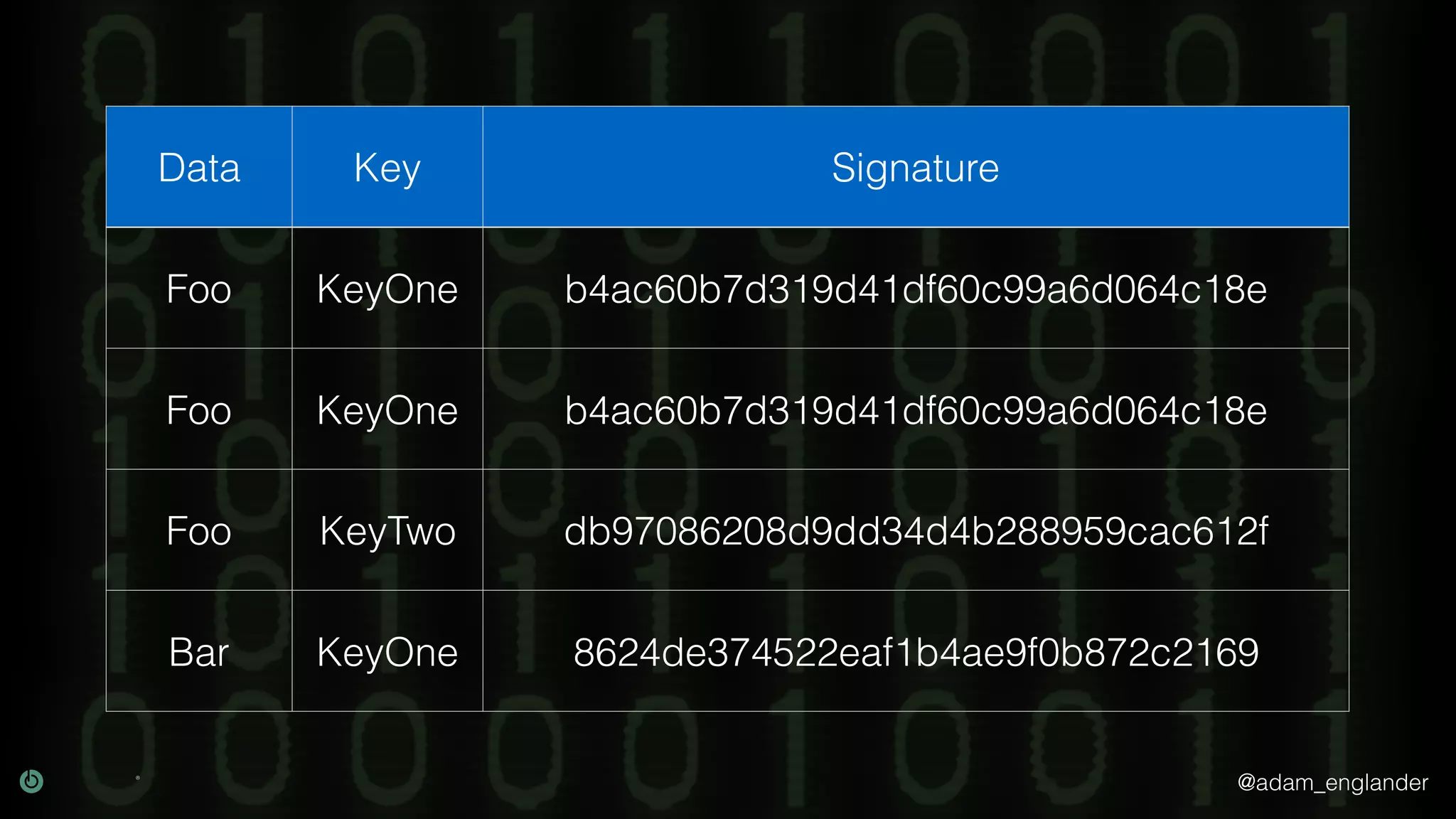
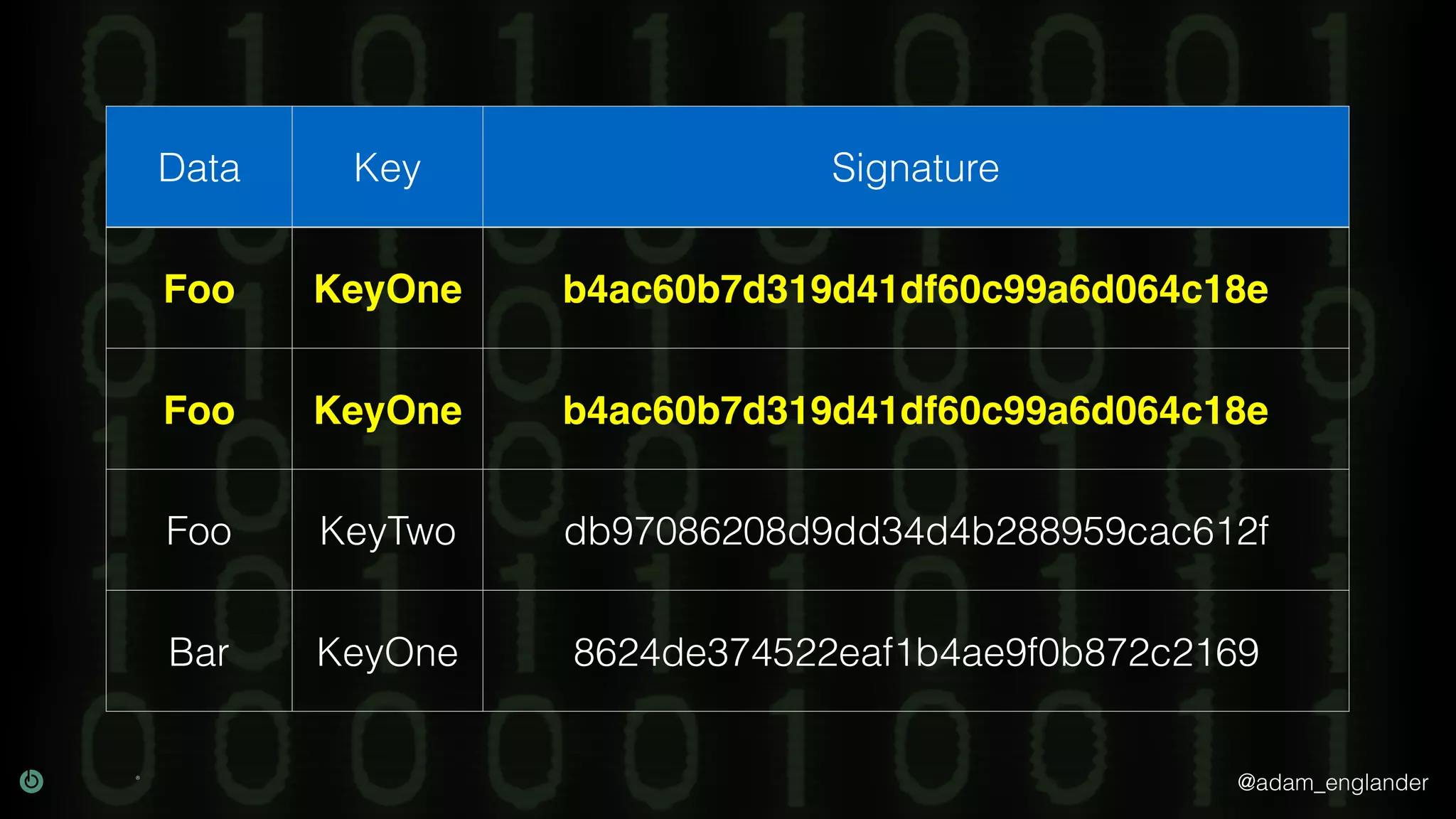
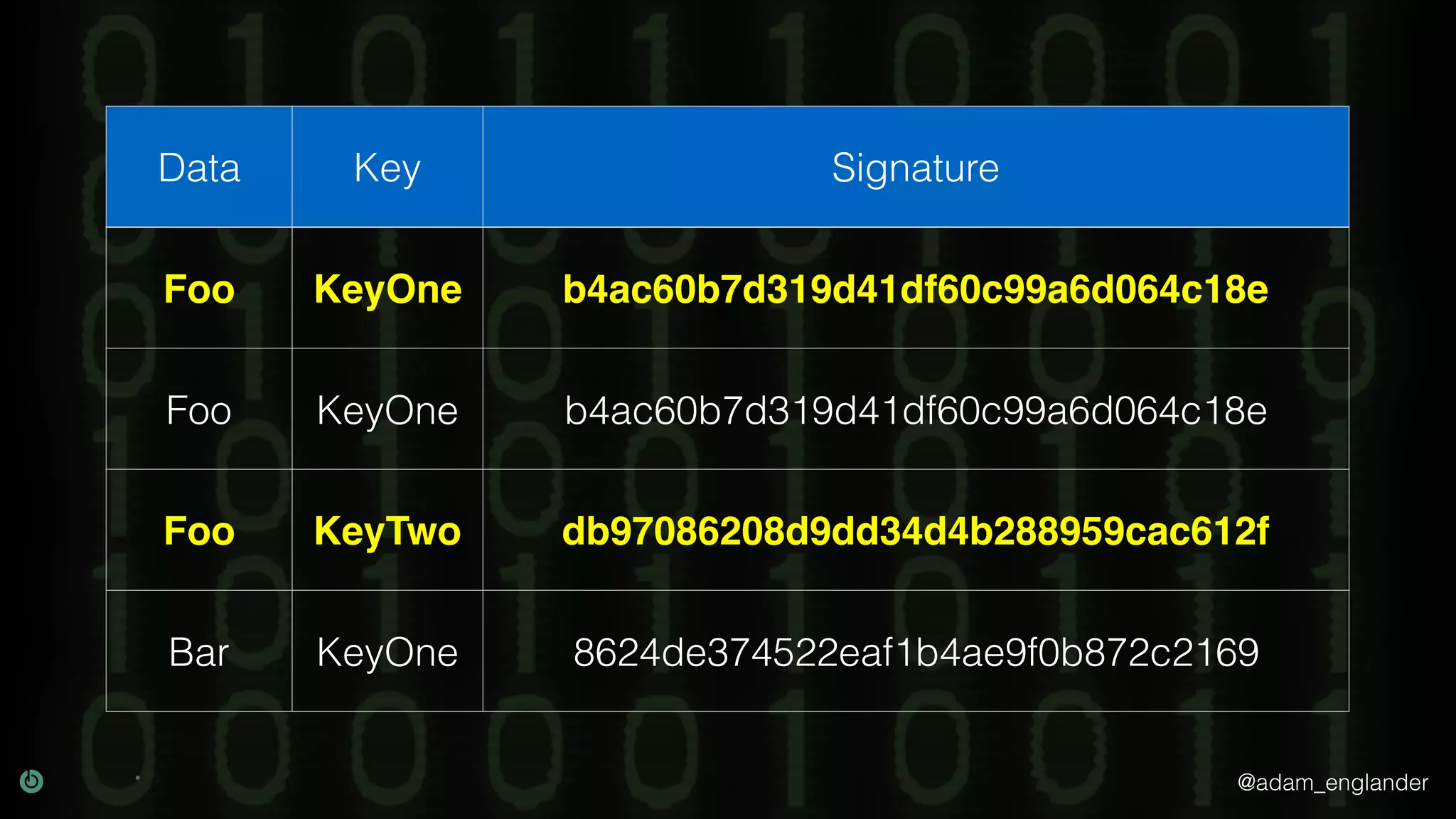
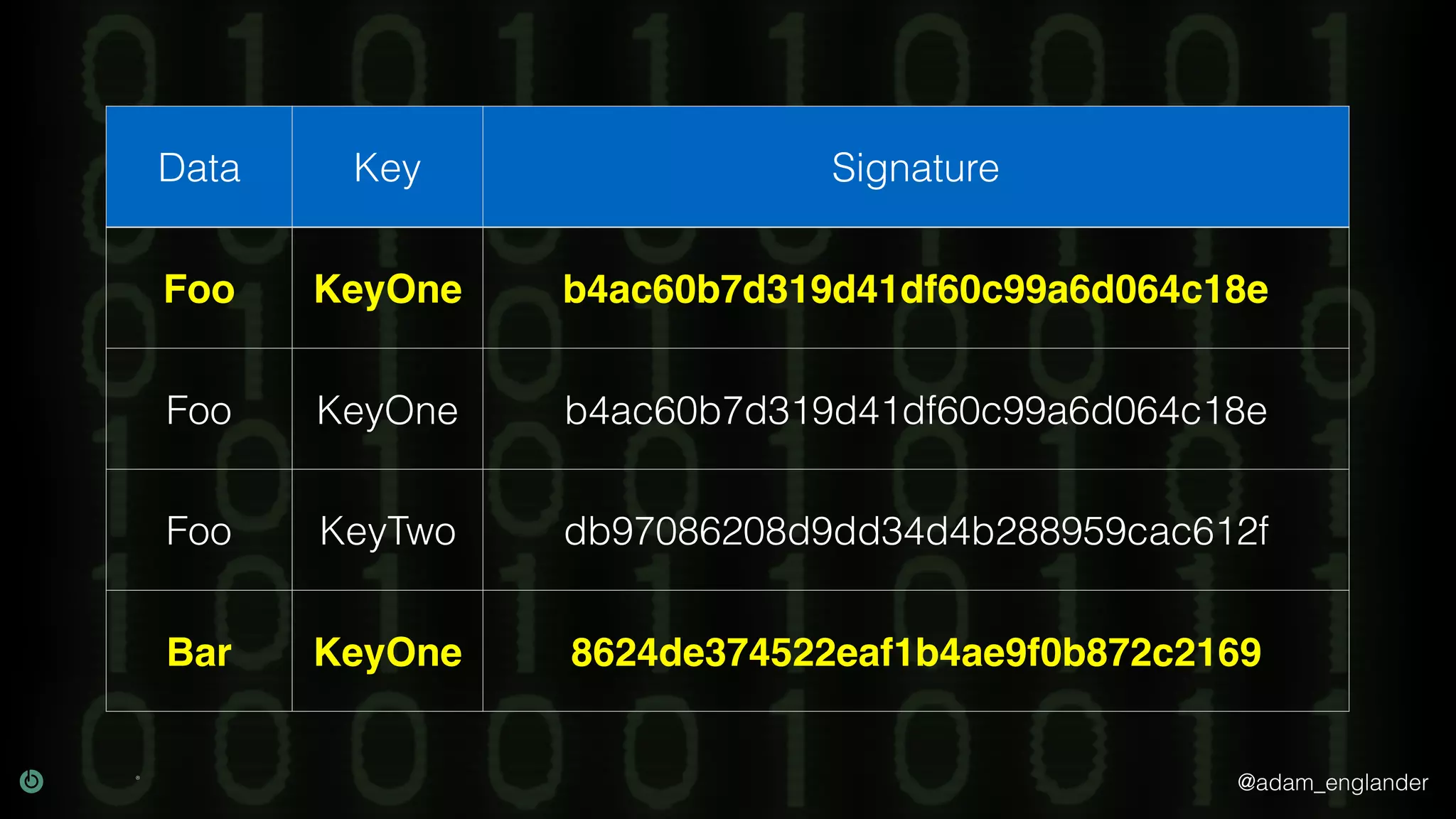
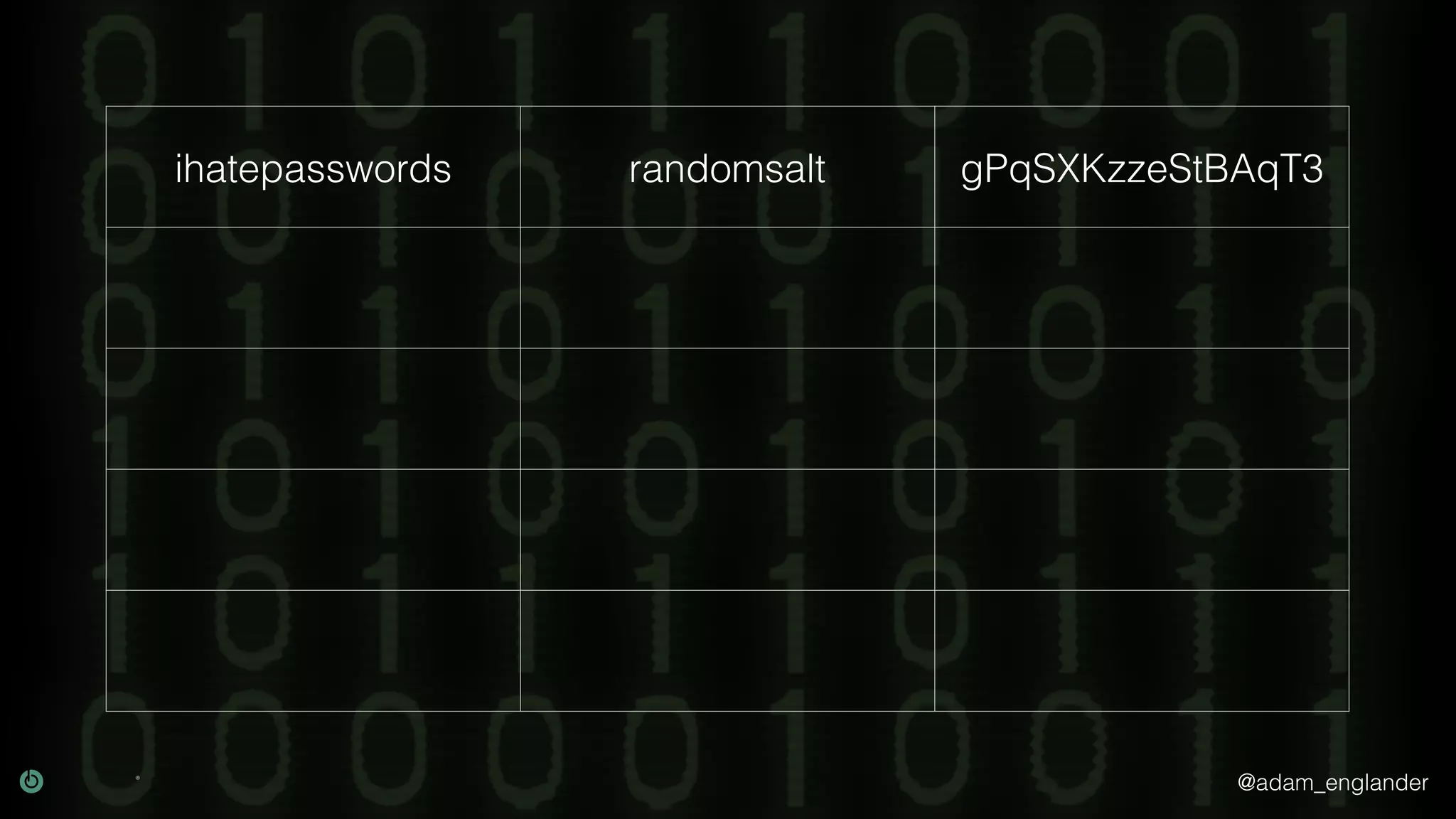
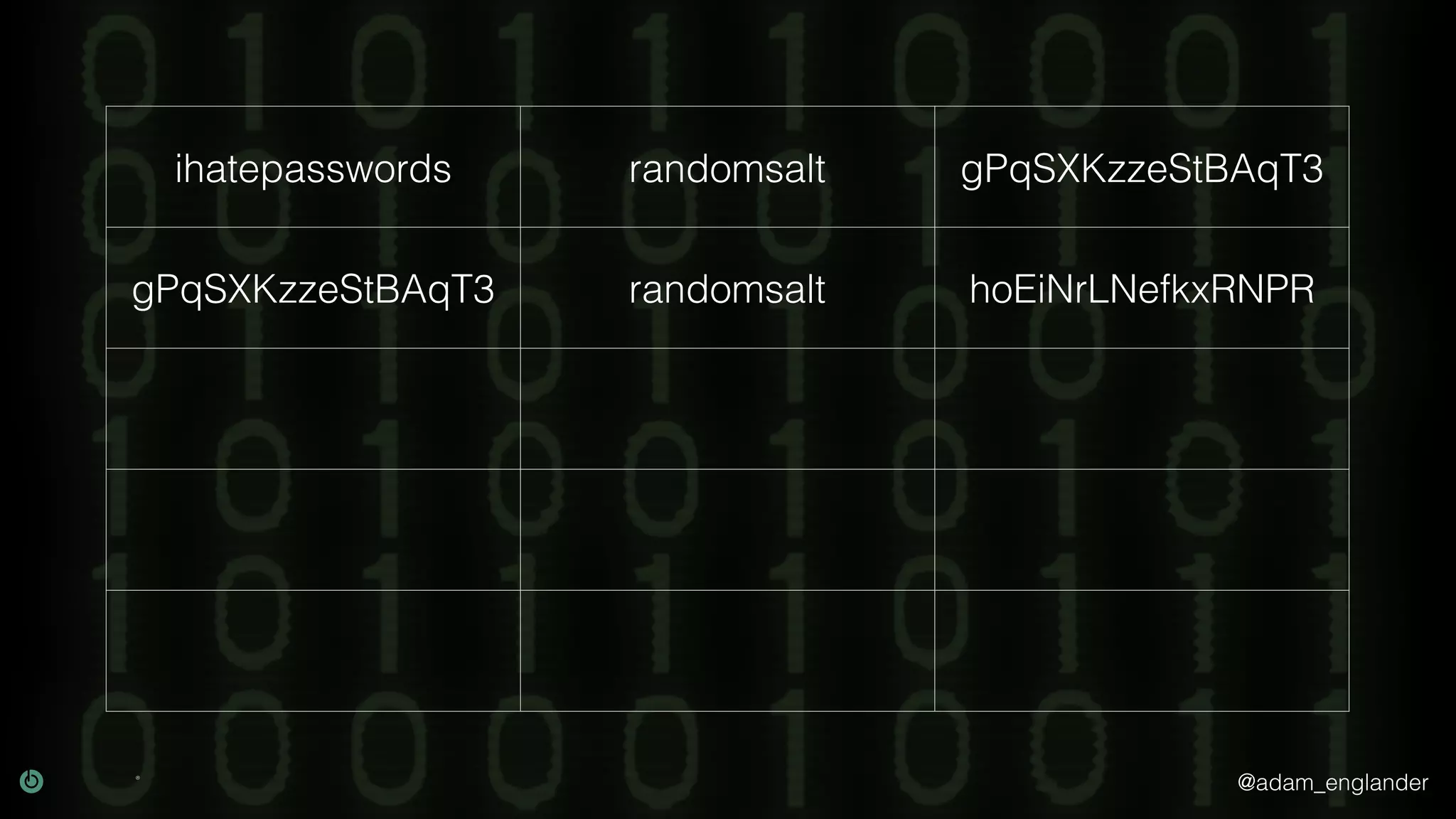
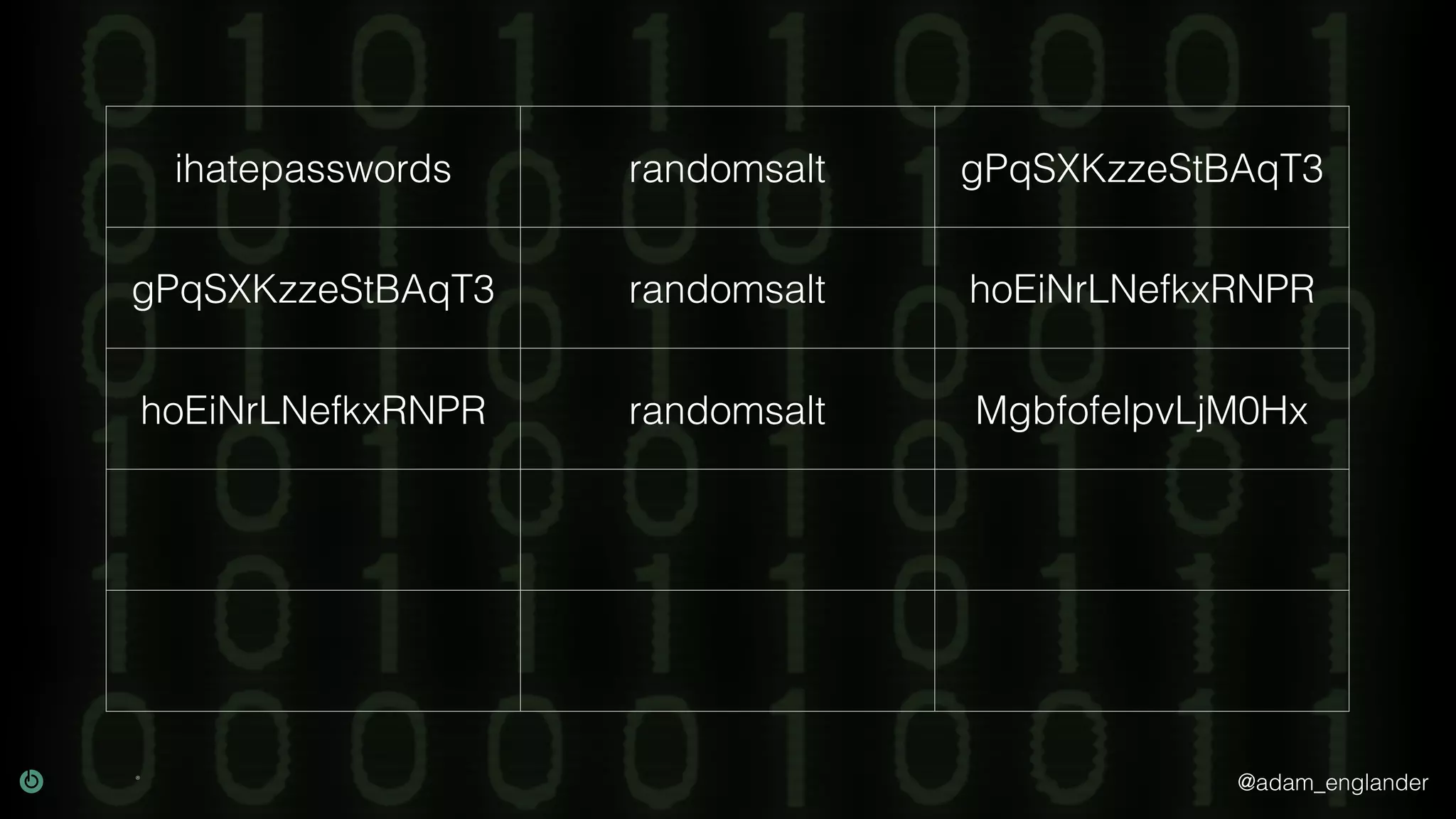
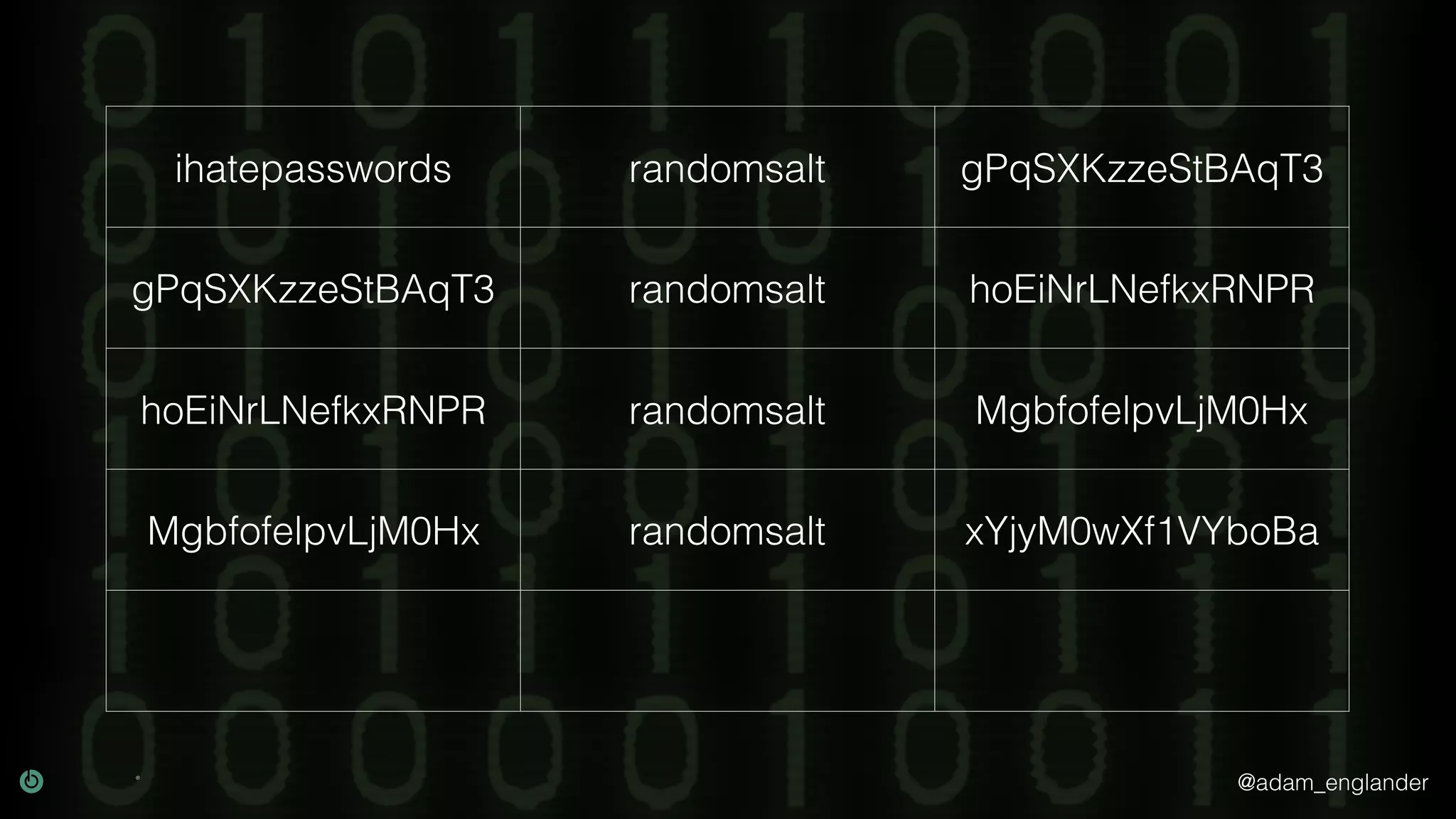
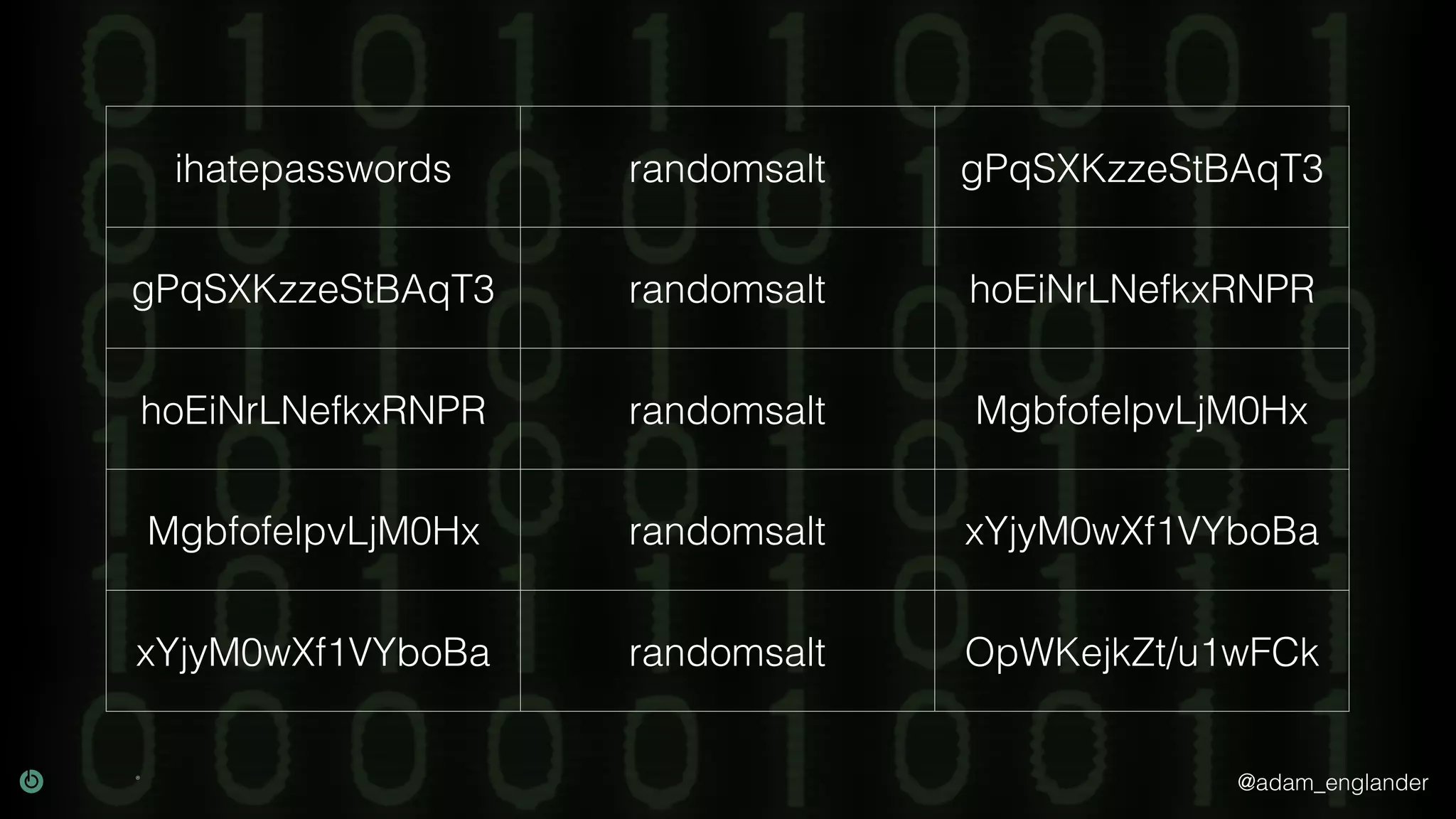
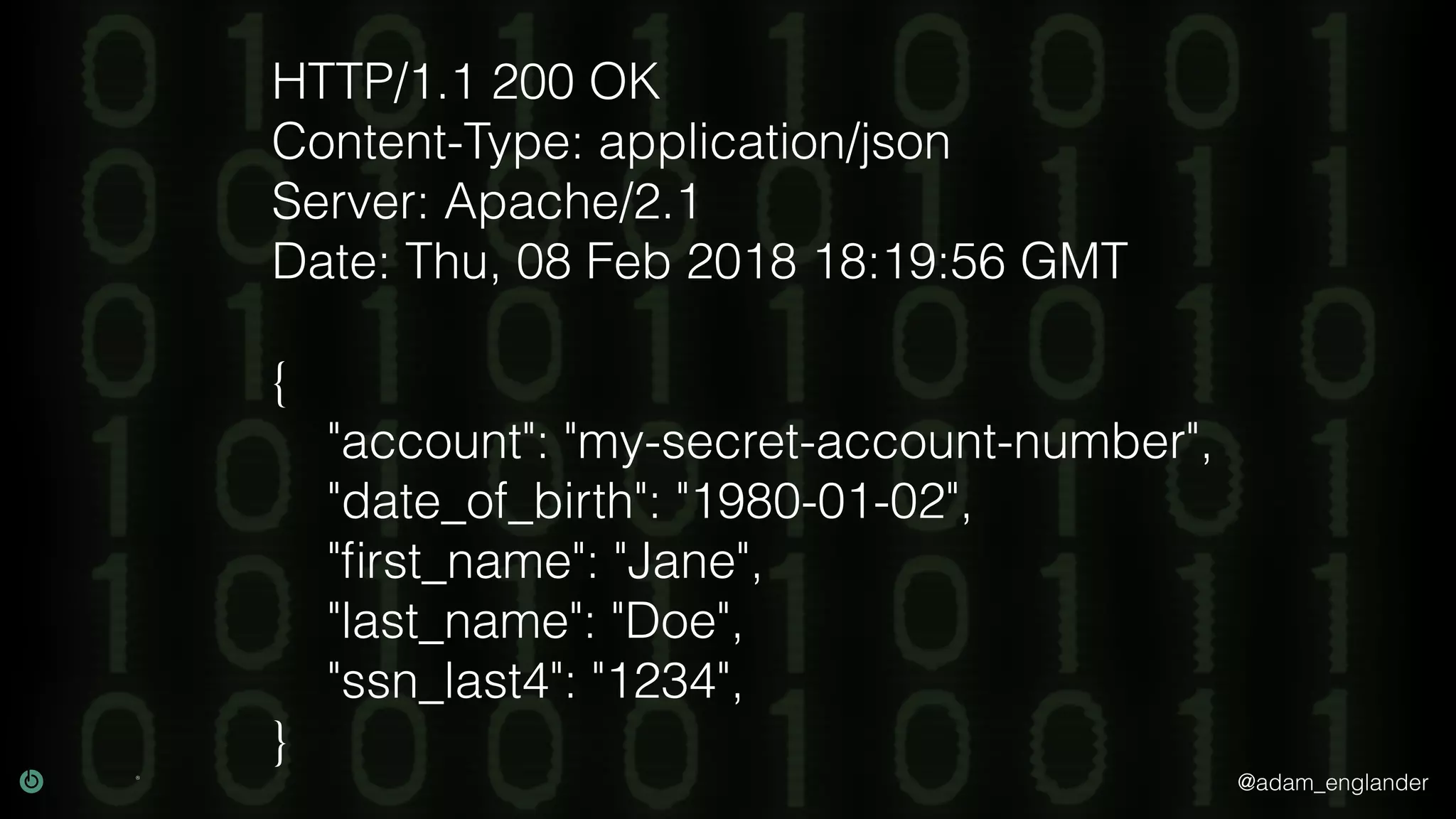
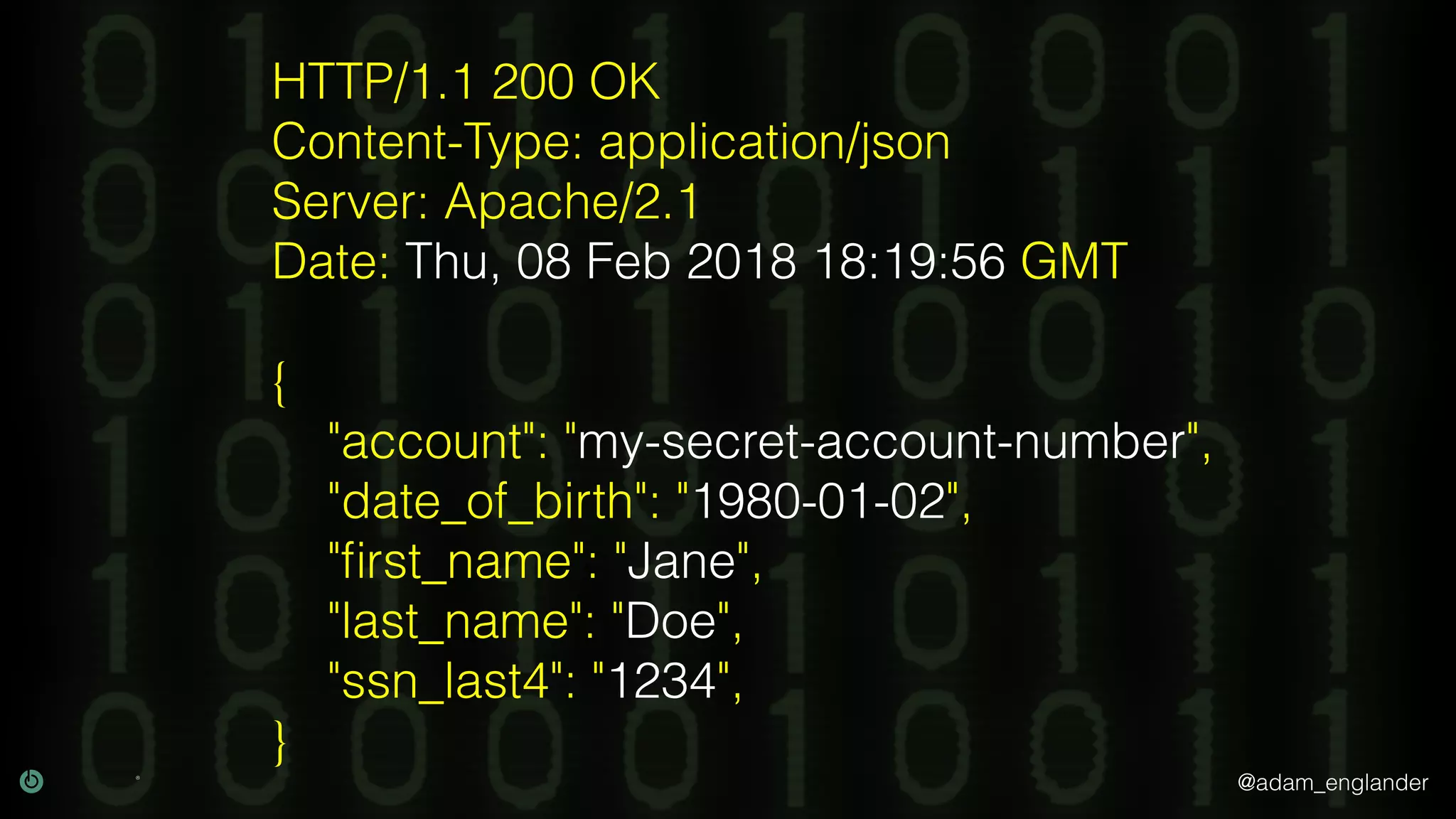
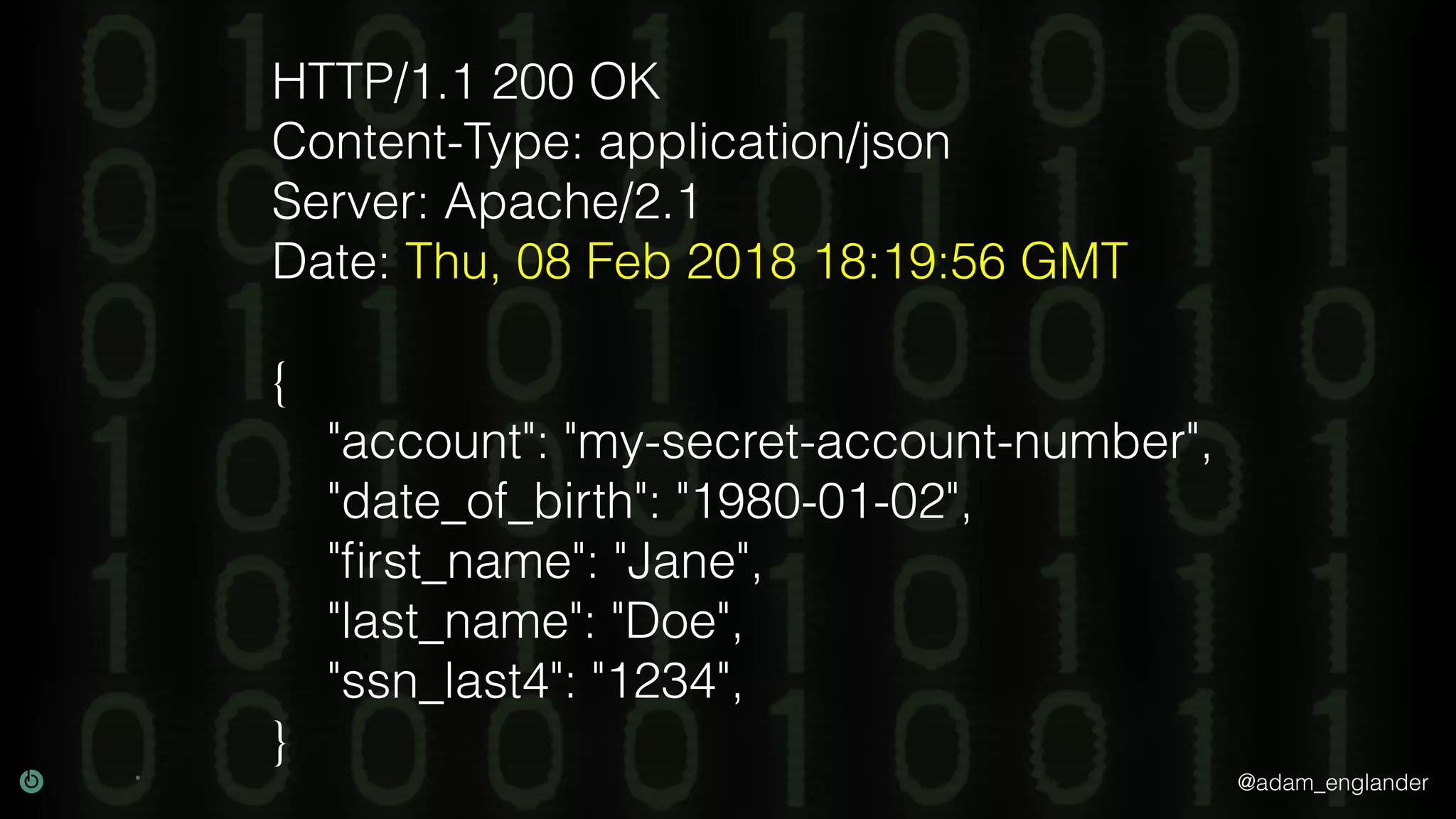
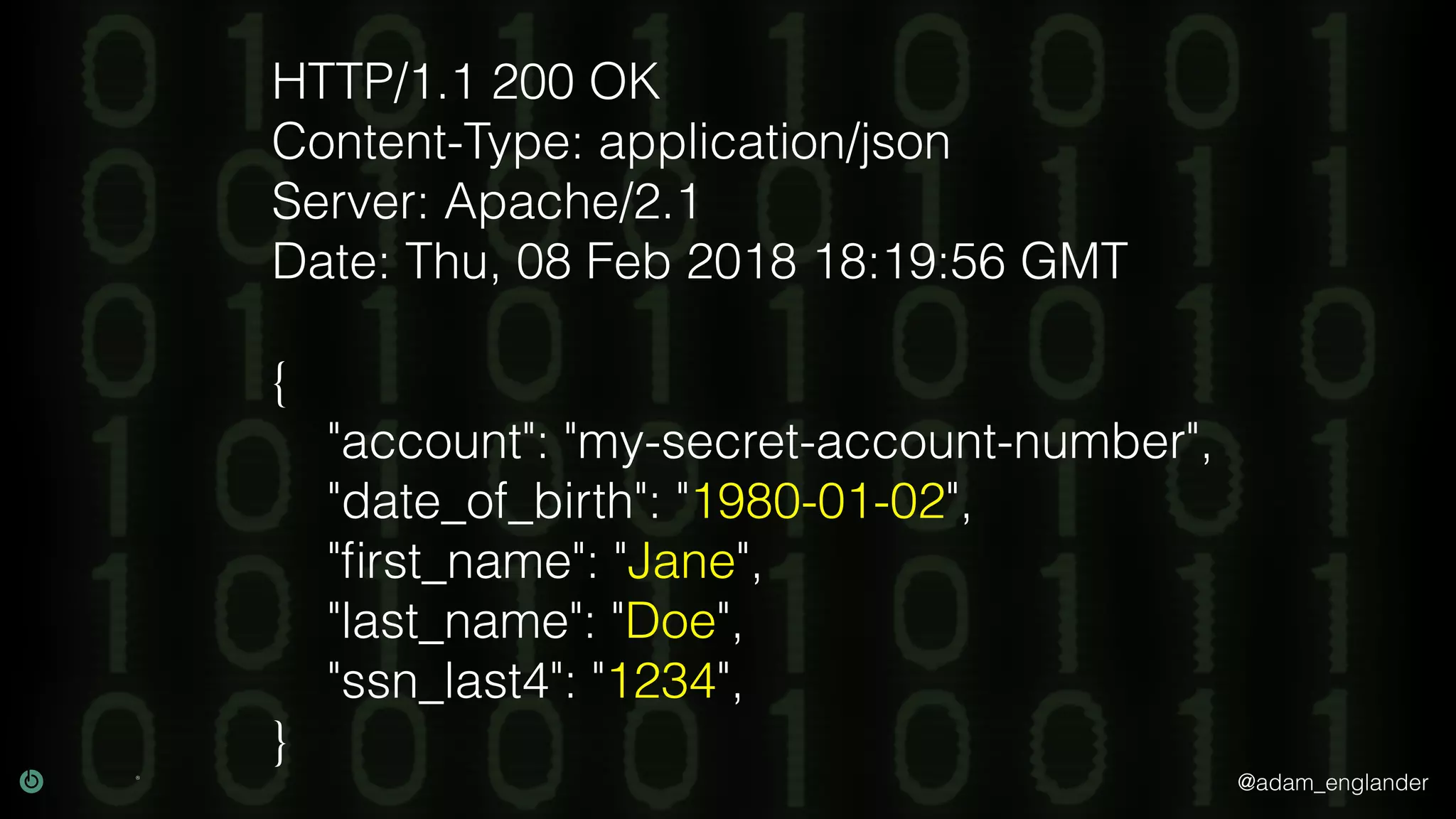
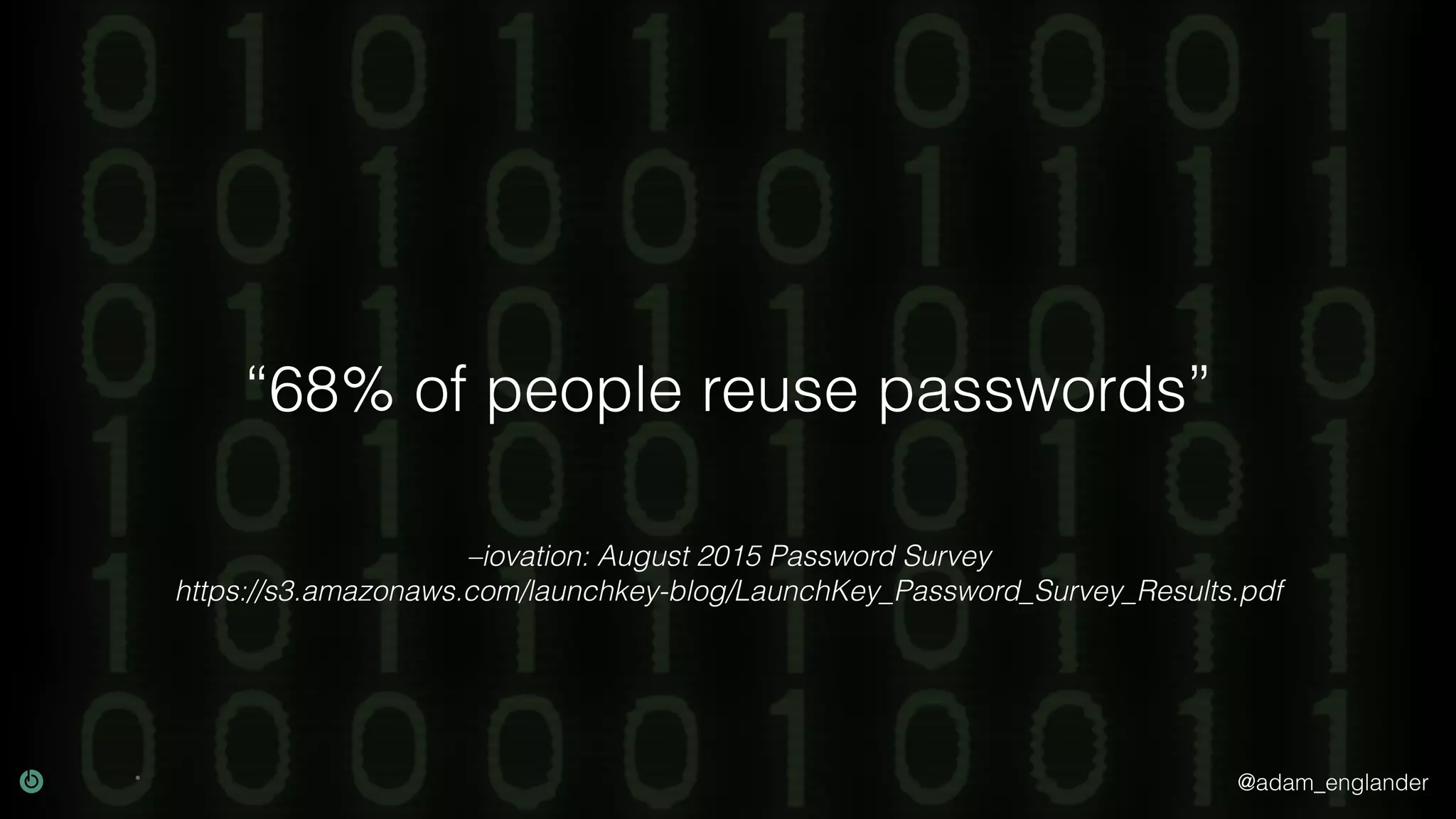
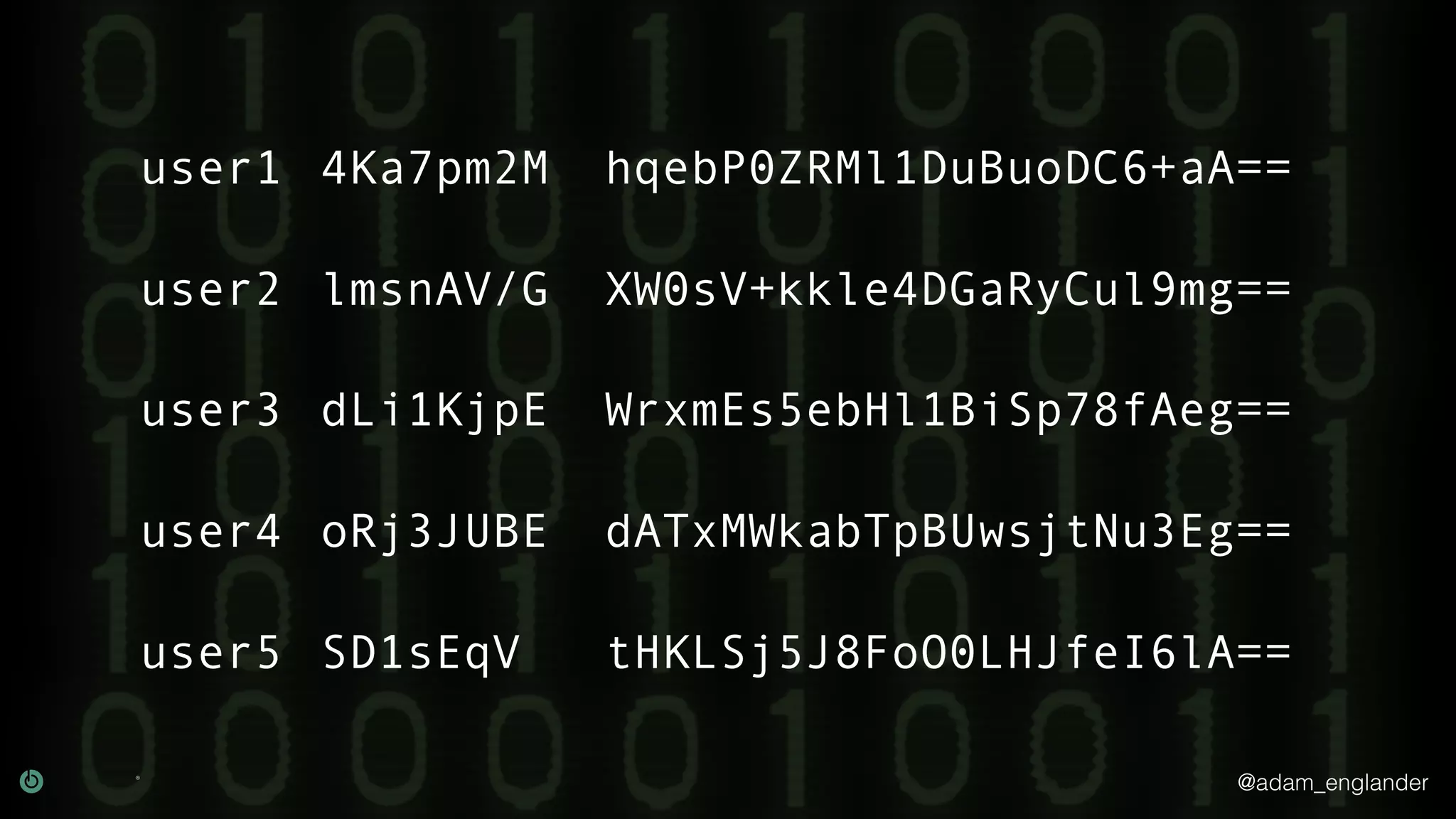
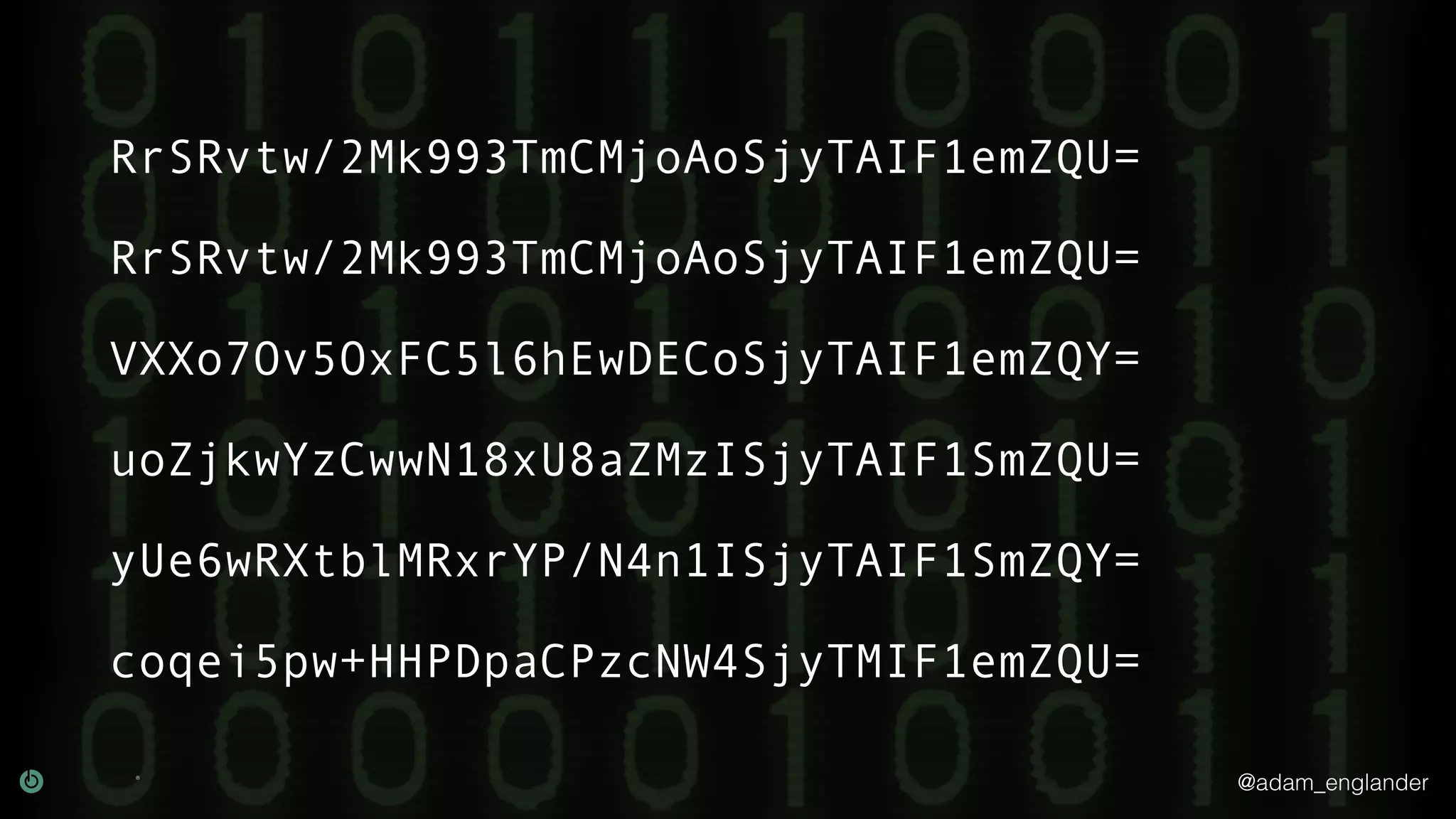
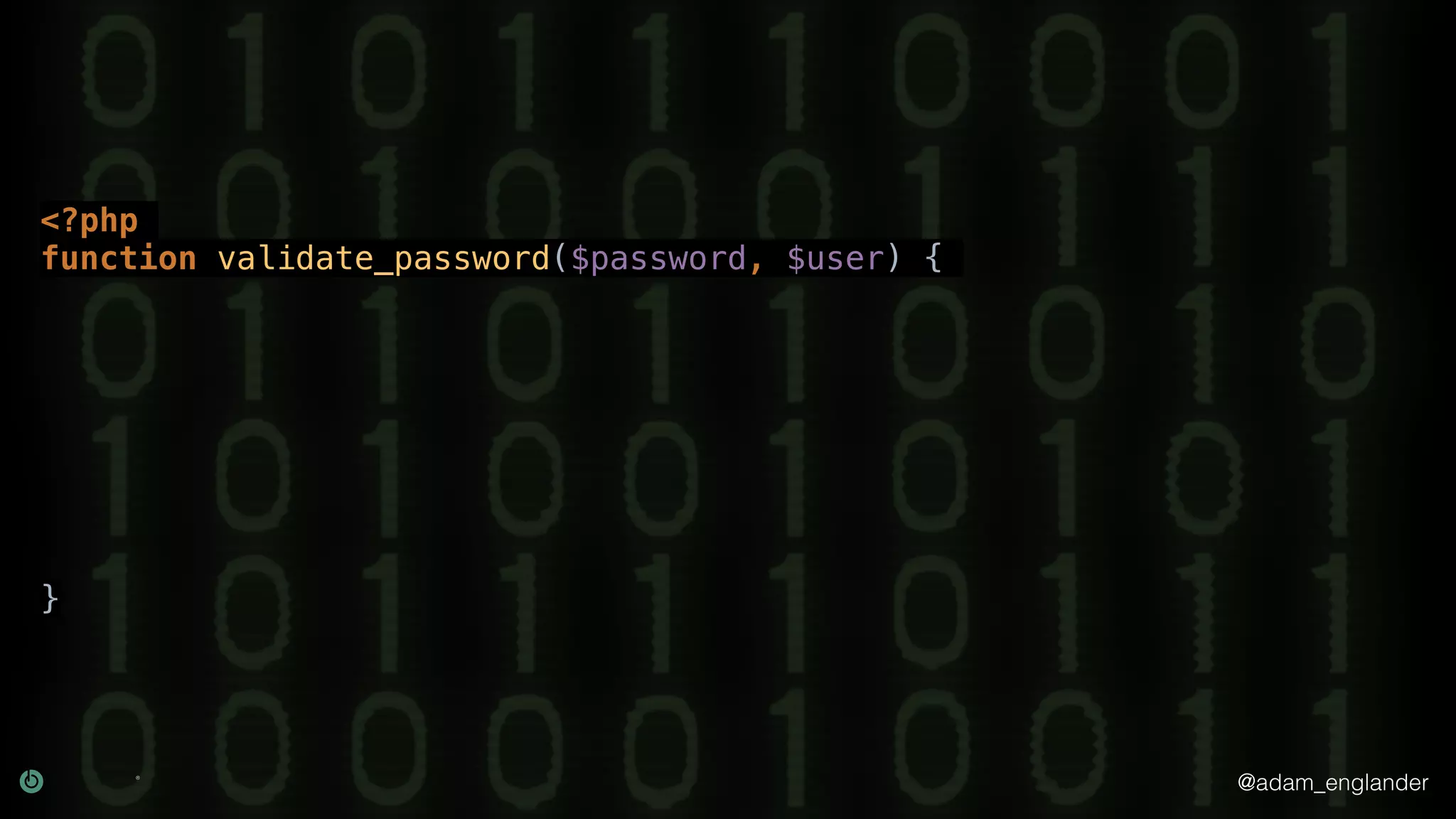
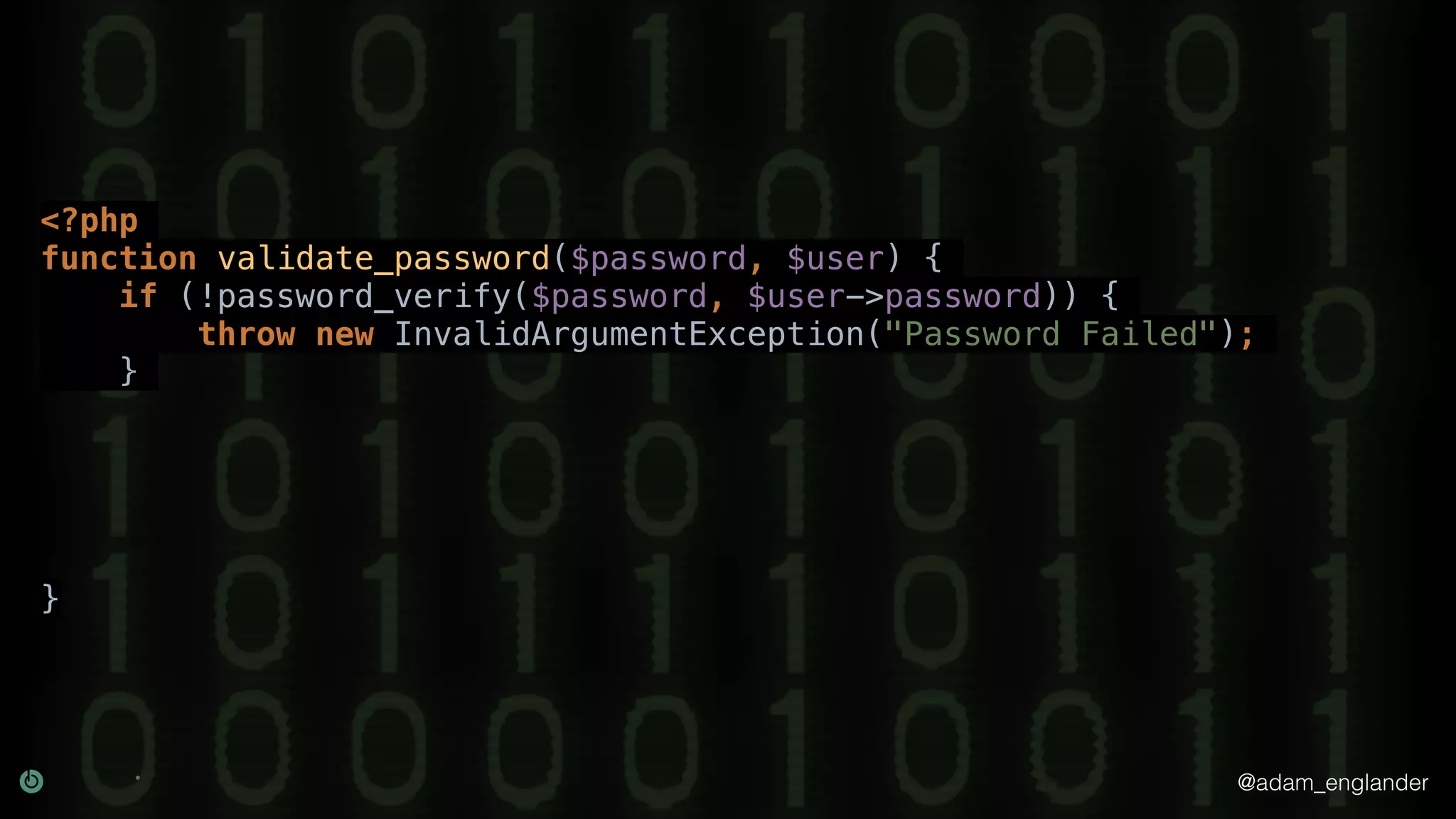
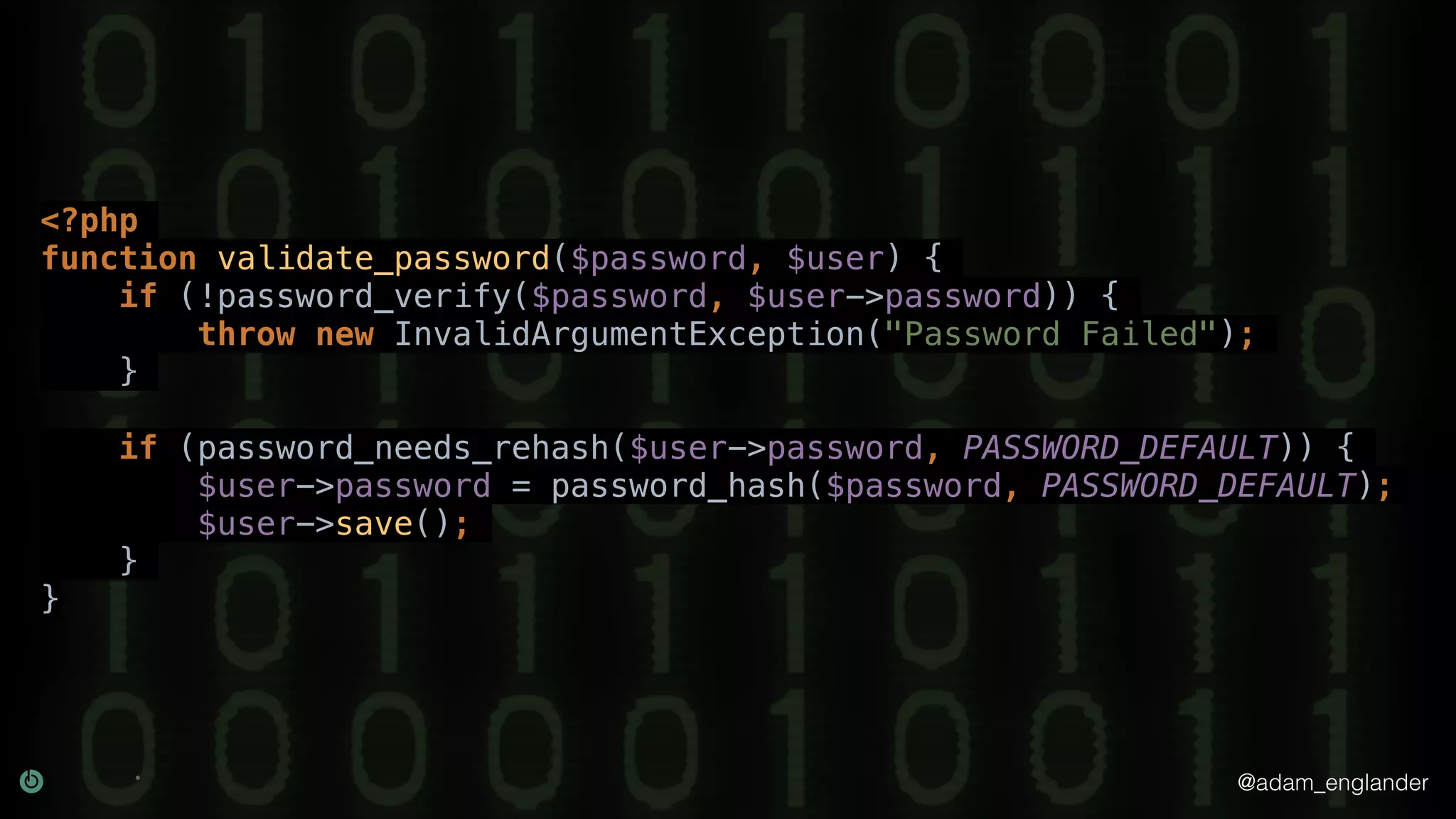
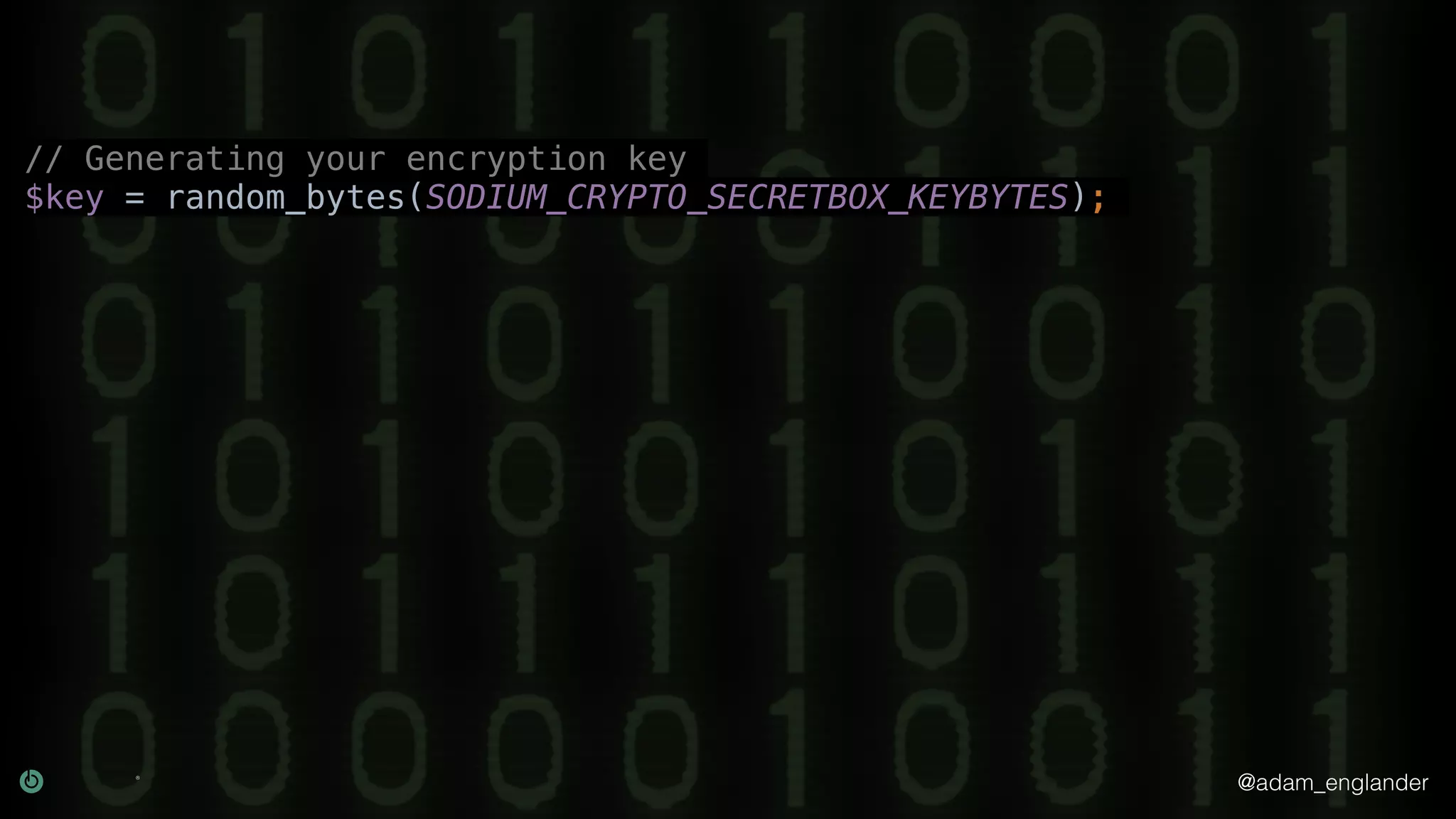
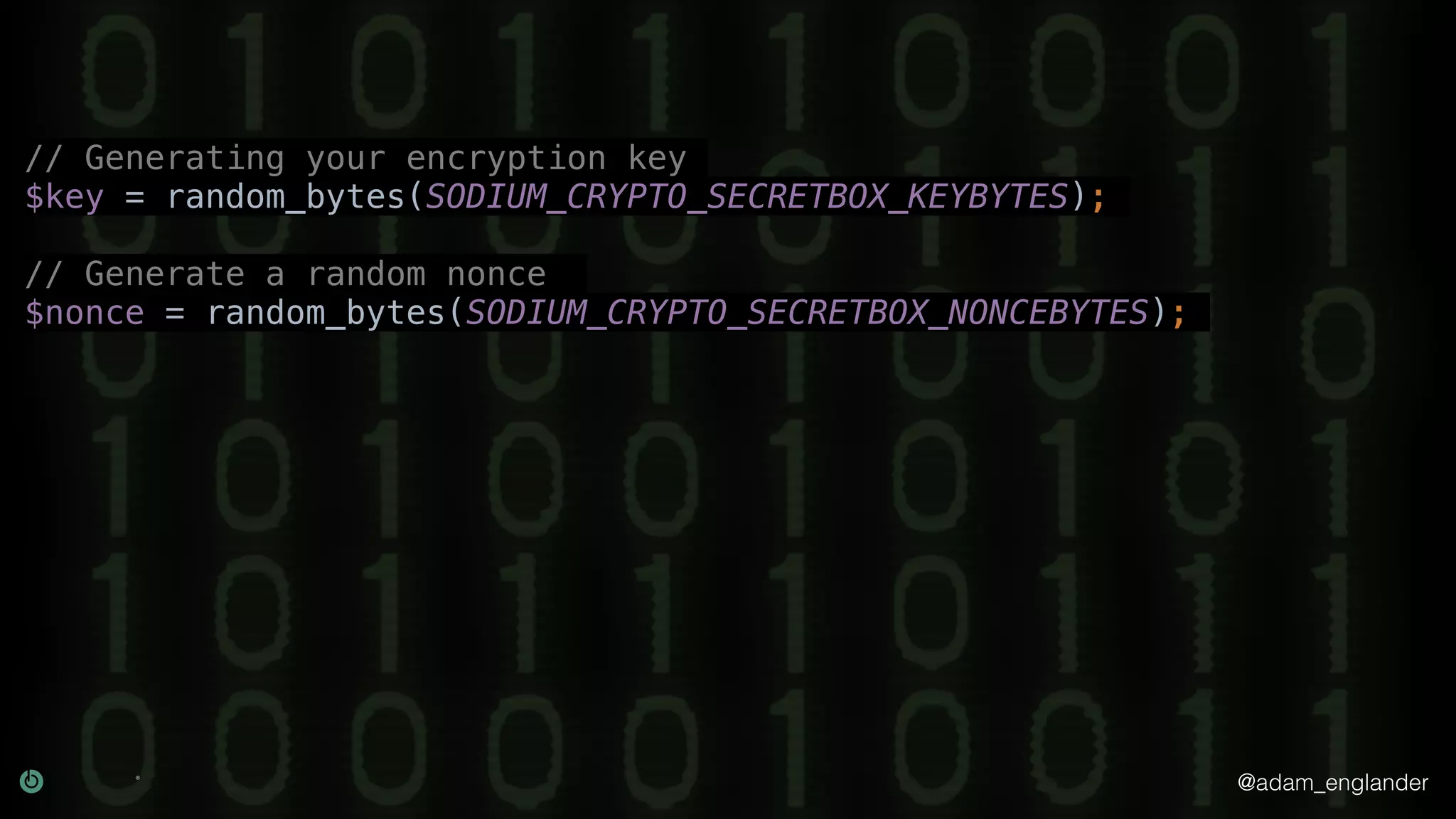
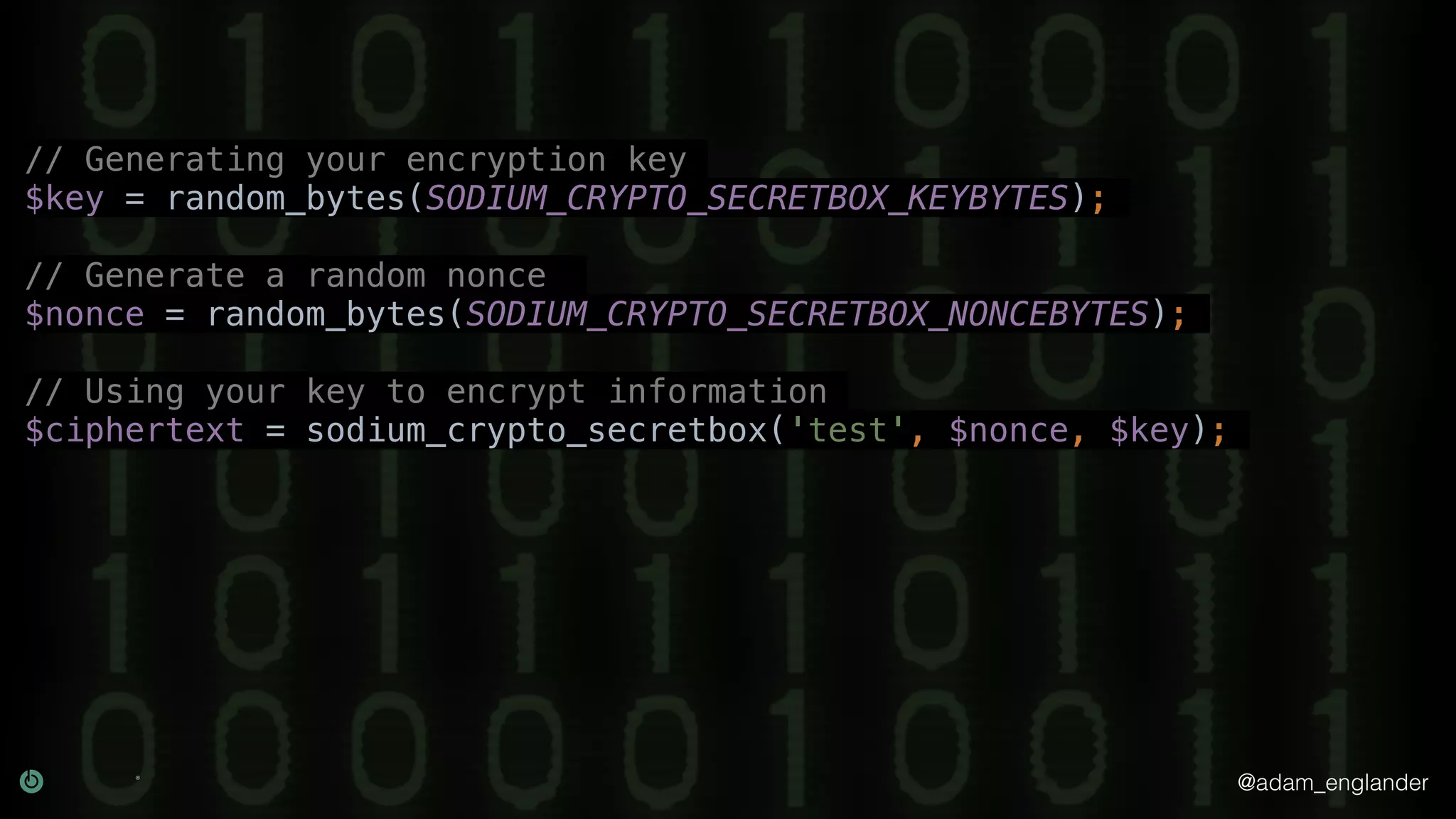
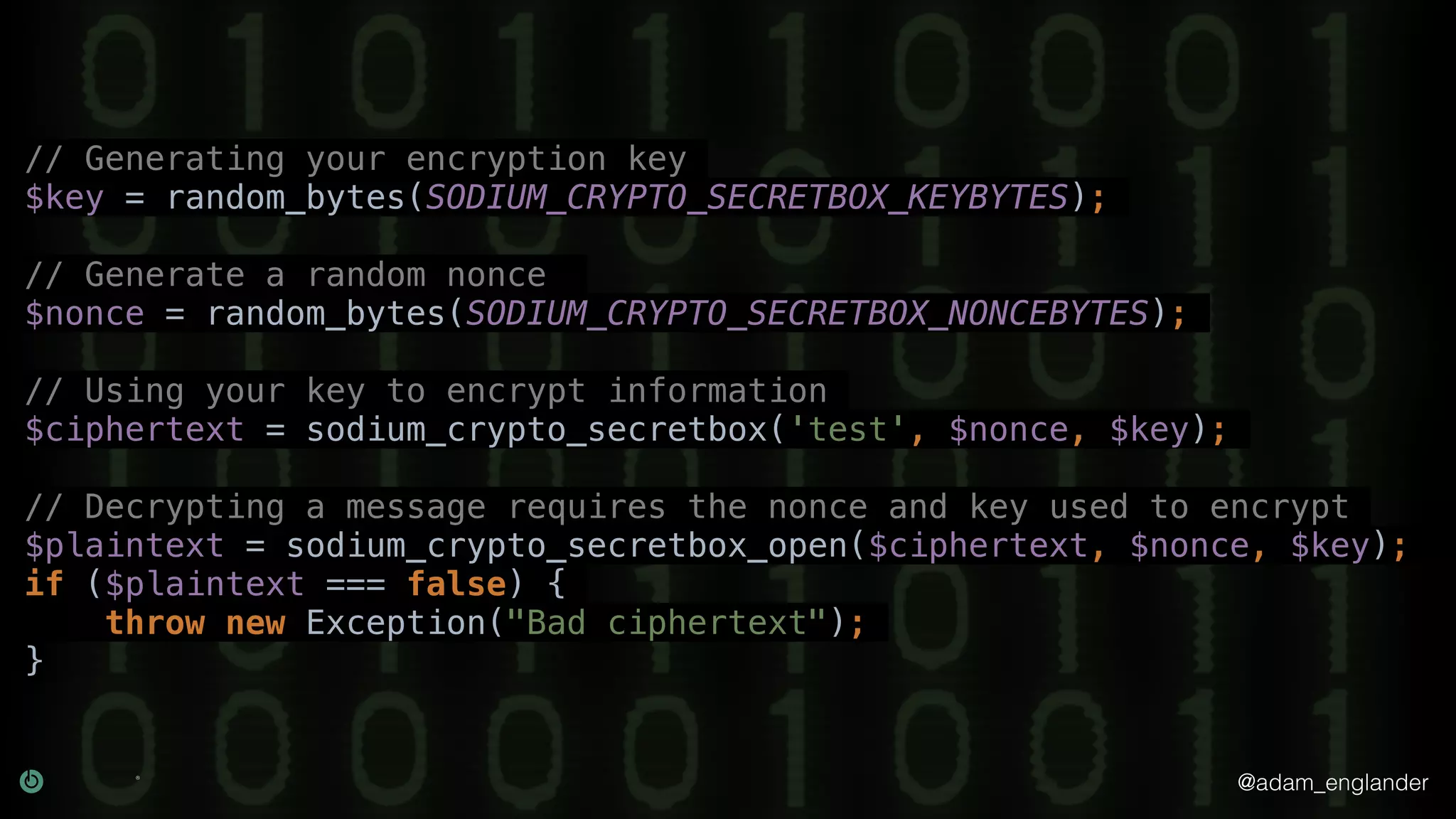
The document provides an overview of cryptography, explaining its purpose as a method for secure communication against adversaries, and details several cryptographic techniques such as encryption, hashing, and key derivation. It emphasizes the importance of good cryptography in obscuring data to prevent duplication or reverse engineering, and highlights common issues like password predictability and the use of random salts to enhance security. Additionally, it includes practical examples and resources for further understanding cryptographic methods.