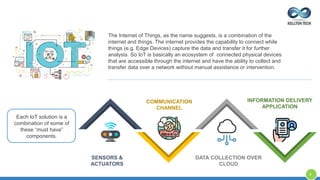
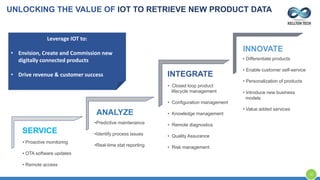
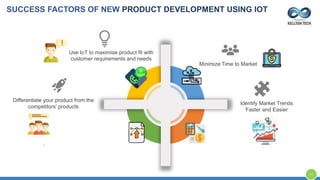
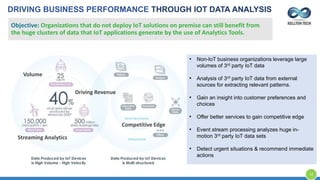
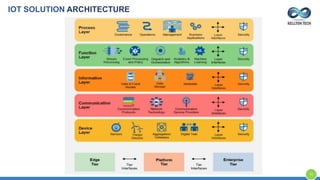
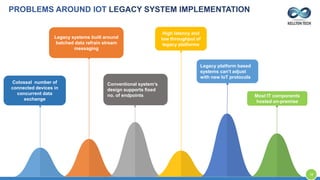
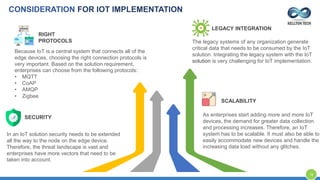
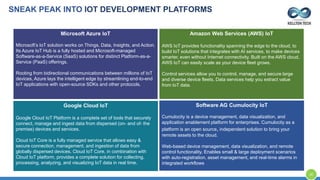
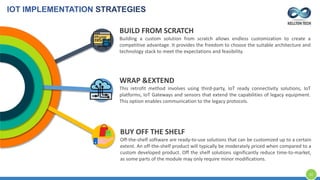
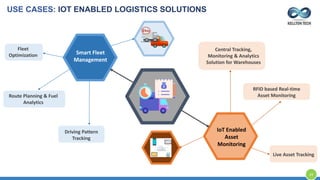
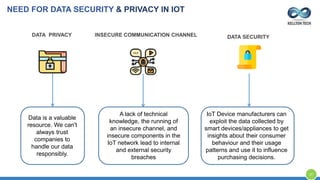
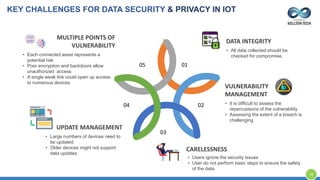
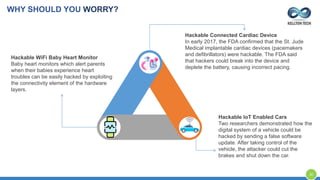
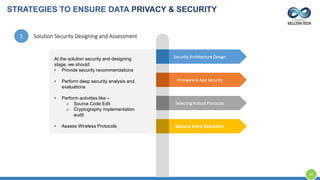
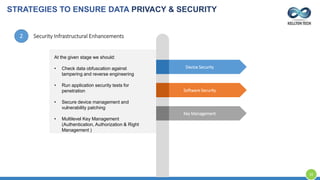
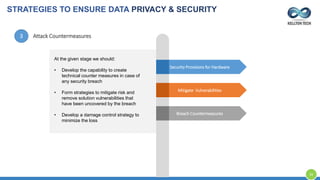
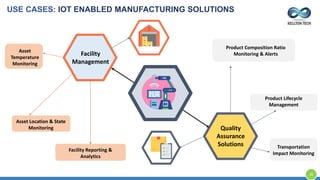
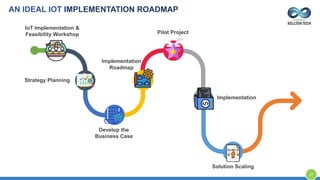
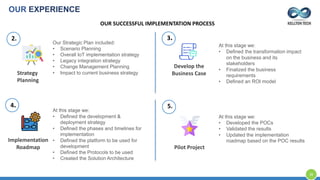
The document provides an overview of Kellton Tech's approach to Internet of Things (IoT) solutions, focusing on mitigating data security risks, simplifying IoT adoption, and integrating legacy systems. It discusses various industry applications and strategies for implementing IoT, along with the challenges posed by legacy systems, data security, and privacy concerns. Additionally, it highlights the importance of using modern development platforms and outlines a structured implementation roadmap for successful IoT integration.