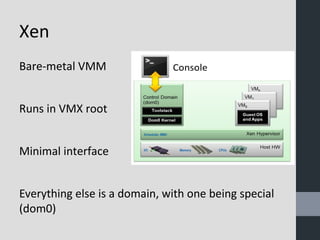
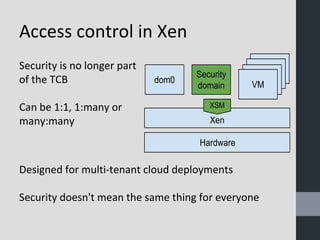
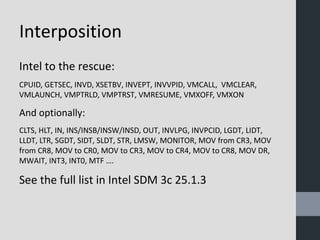
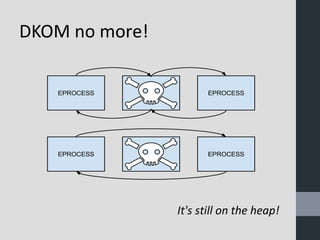
Virtual machine introspection (VMI) allows security tools to be run externally to virtual machines for improved isolation, visibility, and control. VMI provides full interpretation of the virtual hardware and memory to detect malware. It can actively monitor VM events and memory through techniques like EPT trap interposition. The speaker demonstrated these capabilities using open source tools like LibVMI and DRAKVUF for dynamic malware analysis. VMI is presented as an important approach for cloud and mobile security going forward.