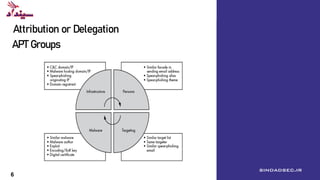
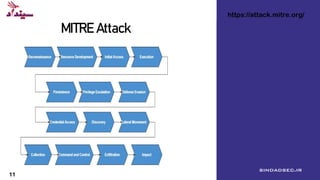
The document discusses adversary emulation and red teaming. It defines red teaming as emulating advanced persistent threat (APT) attacks. It describes APT groups and their goals of espionage and sabotage. Common APT groups and their targeted industries are listed. Methodologies for red teaming like MITRE ATT&CK and the cyber kill chain are explained. The differences between penetration testing and red teaming are outlined. Tools and platforms for adversary emulation like Cobalt Strike and Atomic Red Team are provided. The average costs of data breaches are cited from an IBM report. Defeating APT attacks is discussed as understanding enemies, continuous practice, and implementing security in depth.










![۱۰ sindadsec.ir
Penetration Testing
Penetration Testing VS Red Teaming
Red Teaming
• Offensive Security : Penetration Testing, Red Teaming,
Bug Bounty Hunting
• Penetration Testing Steps [Scope, Type (Black, White,
Gray BOX), Social Engineering not Allowed]
Red Teaming Steps ( Whole Business are SCOPE, Type
Black box, Social Engineering allowed, Any kind of
Offensive is allowed, Physical Initial Access)
13](https://image.slidesharecdn.com/redteamp1-220825101101-fcfd5f50/85/Red-Team-P1-pdf-14-320.jpg)






![sindadsec.ir
Defeat APT Attack
First Step You Should Know Your Enemies [APT Groups, Ransomware Gangs] = CTI
You Should Have Continues Practice for Evaluating your The level of preparedness to face
the threats. After Extracting TTP Assign Emulation to red Team = Purple Teaming
Security In Depth It requires proper network design. You should know using security
equipment on right place = Security is process not product.
20](https://image.slidesharecdn.com/redteamp1-220825101101-fcfd5f50/85/Red-Team-P1-pdf-21-320.jpg)
